当前位置:网站首页>The 31st --- the 52nd
The 31st --- the 52nd
2022-07-27 16:31:00 【andrewhxc】
The first 31 return


The ordinary iterator in the following figure ivec.begin() and Reverse Iterators ivec.rend() Is the corresponding

The first 32 return

adjacent_find() Find continuous 2 Data that conforms to predicate rules
All the algorithms in the following figure are applicable to any container , In the first red box is the exact search algorithm , The second red box is to find a piece of data that matches continuously , The third red box is to find the first data that appears , The first 4 The red box is to find continuous 2 Data that conforms to predicate rules

The first 33 return

The first 34 return

The search algorithms in the above figure are Ordered interval Search algorithm of
The first 35 return

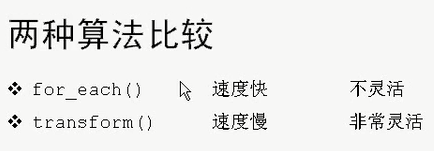
for_each() There is a return value , The return value is for_each() Function objects in , As shown in the figure below

The first 36 return

The first 37 return
The first 38 return

The first 39 return
The first 40 return

The first 41 return

fill() The algorithm can only fill in fixed values ( Constant values )
generate() Algorithms can fill functions or function objects
The first 42 return

The first 43 return

That is to say, after the deletion algorithm runs , The number of data elements in the container has not decreased
And member functions erase() Is the real deletion
The first 44 return

The first 45 return

unique() The deletion algorithm is to delete continuity Elements of repetition , Only one element is left
The first 46 return

The first 47 return

The first 48 return

The first 49 return

Be careful :sort Algorithms cannot be used for list Linked list , because sort The algorithm requires the use of random access iterators
The first 50 return

The first 51 return

The first 52 return

边栏推荐
- 4-digit random data
- training on multiple GPUs pytorch
- Leetcode234 question - simple method to judge palindrome linked list
- For enterprise operation and maintenance security, use the cloud housekeeper fortress machine!
- C语言逆序输出字符串
- Yys mouse connector
- JSP Foundation
- DRF learning notes (V): viewset
- C language programming (Third Edition)
- Common Oracle statements
猜你喜欢

: 0xc0000005: an access conflict occurs when writing position 0x01458000 - to be solved

JMeter5.3 及以后的版本jmeter函数助手生成的字符在置灰无法复制

MapReduce instance (II): Average

Find active SQL connections in SQL Server

DRF use: get request to get data (small example)

Test novice learning classic (with ideas)
DEX and AMMS of DFI security

插入word中的图片保持高dpi方法

DRF learning notes (II): Data deserialization

Implementation of ByteDance service grid based on Hertz framework
随机推荐
Introduction and use of redis
OpenCV(五)——运动目标识别
减小PDF文档大小(转载)
【论文阅读】Single- and Cross-Modality Near Duplicate Image PairsDetection via Spatial Transformer Compar
Exe program encryption lock
Script file ‘D:\programs\anaconda3\Scripts\pip-script.py‘ is not present.
The difference and use between get request and post request
爬取常见英文名
Mazak handwheel maintenance Mazak little giant CNC machine tool handle operator maintenance av-eahs-382-1
Google Chrome reversecaptcha ad blocking
指针总结
将IAR工程文件夹转移目录后无法进入函数定义解决
201403-1
solidwork装配体导入到Adams中出现多个Part重名和Part丢失的情况处理
Axure install Icon Font Catalog
word中插入度的方法
2021-03-09
The 4.3 billion euro cash acquisition of OSRAM failed! AMS said it would continue to acquire
第21回---第30回
Product axure9 English version, using repeater repeater to realize drop-down multi selection box