当前位置:网站首页>Super automation and the future of network security
Super automation and the future of network security
2022-06-28 16:15:00 【Software test network】

Artificial intelligence technology has been integrated into various application systems , But research institutions Gartner Think : The current application level and capability of automation technology can be further improved .Gartner Analysts predict : Super automation technology will soon become a global business technology development trend . In the field of cyber security , Hyper automation can be a powerful tool for organizations to effectively manage numerous alerts and network events .
What is super Automation ?
Super automation integrates robot process automation 、 Machine learning technology and artificial intelligence , It aims to improve and perfect the business and technical processes that previously required the participation of human decision makers . Due to low code / No code development tools and agile DevOps The process is popular , Many enterprises have automated every day task . Super automation will bring robot automation and quality to a new level , Combine machine learning / Artificial intelligence technology to replicate human decision-making process .
Imagine an intelligent system making unusually fast decisions based on an unusually complex data set , This is super automation . today , Super automation can be used to improve business process management 、iPaaS Solutions and security systems . Tomorrow, , Super automation will become more advanced .
The main advantages of super automation are as follows :
- Simplify and improve automation of work and processes .
- Improve business agility and DevOps Strategy .
- Enhanced low code / No code security .
The main disadvantages of super automation are as follows :
- Next generation technology infrastructure is required .
- Integrated emerging technologies need to be further integrated .
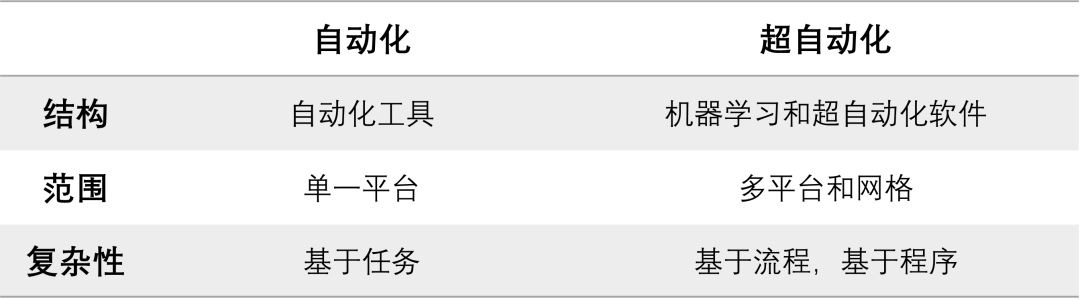
Super automation and conventional automation ( For example, robot process automation ) What's the difference between ?
Super automation is still based on automation , But super automation combines artificial intelligence with automation tools , Expanded the scope , Increased complexity .
The application of super automation in the field of network security
Nowadays, remote work is increasingly advocated 、 Internet of things devices and multi Cloud Architecture , Many organizations compete to protect their important assets . In this context , The nature of network security is also undergoing fundamental changes . Most security solutions have been combined with the next generation of artificial intelligence technology . And the super automation technology will further enhance the practicability of these systems based on artificial intelligence , Let them make humanized 、 Decisions against time .
Besides , Cyber criminals are becoming more and more aware of artificial intelligence / How machine learning network security solutions work . Advanced super automated systems can make more complex decisions faster , So as to increase the complexity of the organizational defense strategy . More advanced artificial intelligence / Machine learning solutions are inherently more difficult to predict , Therefore, it is more defensive .
Gartner Think , Organizations with ultra automation will automate their business , Reduce operating costs 30%. But in the area of security , Use super automation to deal with network security events 、 The cost savings from improving the operation and maintenance process of complex multi cloud infrastructure may be greater . For security professionals , Super automation has been integrated into many next-generation solutions supporting artificial intelligence , Understanding the technical principle of super automation as soon as possible may be as important as understanding the principle of robot process automation and testing .
Some potential uses of super automation in the security field include the following :
- Artificial intelligence systems use natural language to process review emails , To identify phishing attempts .
- The document security system uses optical character recognition technology (OCR) Read scanned documents , To identify personally identifiable information .
- Machine learning security solutions identify suspicious login contexts , Request further login information .
Gartner Organizations are encouraged to focus on projects with high feasibility and commercial value ( See the picture below ).
The details are as follows :
- Transaction fraud detection ;
- File based malware detection ;
- Process behavior analysis ;
- Abnormal system behavior detection ;
- Web Domain and reputation assessment ;
- Asset inventory and dependency mapping optimization .
Embrace automation more actively
Here's the thing to watch ,Z generation ( A generation of young people born after the rise of network technology ) More likely to embrace super Automation , They may also become the main force of adopting super automation technology in the next few years . This generation has grown up with digital technology , So today's supply chain leaders want them to be innovators , So as to accelerate the digitalization of supply chain , And pave the way for super Automation .Z A generation of technical professionals may find themselves rapidly adapting to the super automated world , So as to enhance the competitiveness in the market .
Gartner Specially pointed out , The COVID-19 has greatly accelerated the transformation of organizations to automation . The recession has raised concerns 、 Organizations cut costs and need more flexibility , These will further drive organizations to adopt automated resilient systems . In the increasingly complex network threat situation , Super automation will become the driving force behind the security industry .
Again , Security professionals may need to actively use super automation to save valuable time . As safety professionals sign contracts with large companies , Hosted security service providers (MSSP) Expand to a larger customer base , Super automation will save more working time .
Most industry professionals have realized that the application trend of automation technology is getting faster and faster . Super automation is based on automated and optimized processes , Supported by more powerful real-time decision-making , It naturally becomes the next stop of automation technology . For security professionals , Super automation enables a more resilient overall security architecture , In order to gain insight into the emerging new threats .
Reference link :https://www.esecurityplanet.com/trends/cybersecurity-hyperautomation/
边栏推荐
- Introduction to deep learning in machine learning
- leetcode:22. bracket-generating
- 如何根据多元索引查询最后一条数据,达到 sql order by desc limit 1的效果呢?
- 【高并发基础】MySQL 不同事务隔离级别下的并发隐患及解决方案
- leetcode:22. 括号生成
- LDD 知识整理
- Visual Studio 2010 compilation qt5.6.3
- 成功迁移到云端需要采取的步骤
- 机器学习之卷积神经网络使用cifar10数据集和alexnet网络模型训练分类模型,安装labelimg,以及报错ERROR
- Opengauss kernel: analysis of SQL parsing process
猜你喜欢

wallys/DR7915-wifi6-MT7915-MT7975-2T2R-support-OpenWRT-802.11AX-supporting-MiniPCIe-Module

leetcode:22. bracket-generating

leetcode:22. 括号生成

What is the maximum number of concurrent TCP connections for a server? 65535?

【MySQL】官网文档学习之查询语句sql注意事项
![[MySQL] official website document learning query statement SQL precautions](/img/aa/bf27b609e2fda1edaa46f134fc5626.png)
[MySQL] official website document learning query statement SQL precautions

Visual Studio 2010 configuring and using qt5.6.3

Big God explains open source buff gain strategy live lecture
![[high concurrency foundation] hidden dangers and solutions of MySQL concurrency under different transaction isolation levels](/img/35/63c9793ec7bc1c90c759504e84dc96.png)
[high concurrency foundation] hidden dangers and solutions of MySQL concurrency under different transaction isolation levels

The sadness of software testers is Their own technical ability can not meet the requirements of large manufacturers?
随机推荐
IPDK — Overview
Qt5.5.1 configuring msvc2010 compiler and WinDbg debugger
REDIS00_ Explain redis Conf configuration file
10年测试经验,在35岁的生理年龄面前,一文不值
Big God explains open source buff gain strategy live lecture
[leetcode] 13. Roman numeral to integer
Android和eclipse和MySQL上传图片并获取
岛屿类问题通用解法与DFS框架
防火墙基础之流量管理与控制
薅羊毛的机会了,点个“赚”即有机会赚取高额佣金
leetcode:22. bracket-generating
Web3.0时代来了,看天翼云存储资源盘活系统如何赋能新基建(上)
PostgreSQL异常处理
Visual Studio 2010 配置和使用Qt5.6.3
机器学习之卷积神经网络Lenet5训练模型
Navicat 15 for MySQL
24岁秃头程序员教你微服务交付下如何持续集成交付,学不会砍我
QT interface library
Classic model transformer
Qt5.5.1配置MSVC2010编绎器和windbg调试器