当前位置:网站首页>buu_ re_ crackMe
buu_ re_ crackMe
2022-07-02 02:42:00 【Child_ K1ng】
This topic mainly focuses on simple bypass anti debugging , Evaluation combined with dynamic debugging .
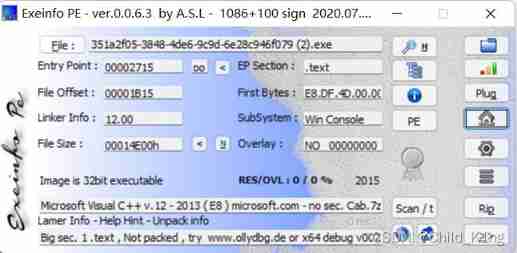
Check the shell
Shell less 32 position
ida analysis
Enter your username and password .
Find out Flower instruction , Can't decompile .
![]()

take jbe and aaa That line nop fall , These data will also be generated nop fall .

Finally get this .

Select all the addresses marked red on the left , Press p Declared as a function , Open the function and find Congratulations, And then Please try again, And back to result The value is 1, therefore v3==1.( The following picture is incomplete )
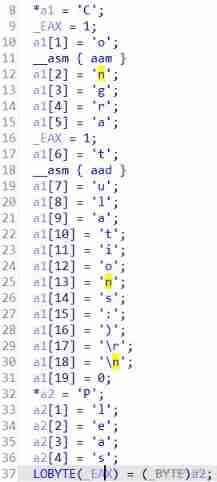
analysis sub_401830 function 
I found that there are many anti debugging things , There are probably four .
![]()
![]()
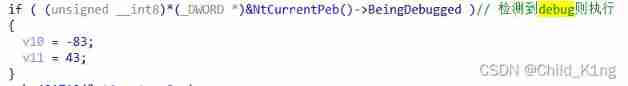

Because of these things , If we go straight debug Can't get the right result .
Bypass anti debugging
First position the cursor on the line with anti debugging pseudo code , Press Tab key , Right click after jump and select Text view, In this way, the assembly instructions can be modified , So as to remove the interference of anti debugging code .

Put... In the picture above jz The order was changed to jmp Instructions ,jmp The corresponding operation code is 0xE8. Empathy , Change the other places too . Finally, don't forget patch into file!!!

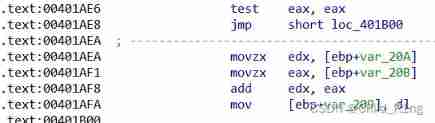
After completion, you can review the execution flow , Found that the anti debugging code disappeared , Bypass all .
Dynamic debugging byte_416050 Array
The following figure shows the lower breakpoint . The first one is the position of the array we are looking for , It is also the key code ; In Chapter 2, we find that this array is stored in ecx To carry out exclusive or , When debugging, only watch ecx The content in .

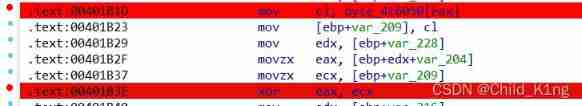
We know the user name , So type , Enter a random set of strings for the password .

then F8 Single step , observe ecx Value .
Finally get byte_416050 The value is 0x2a, 0xd7, 0x92, 0xe9, 0x53, 0xe2, 0xc4, 0xcd
EXP
byte_C26050 = [0x2a, 0xd7, 0x92, 0xe9, 0x53, 0xe2, 0xc4, 0xcd]
v17 = 'dbappsec'
flag=''
for i in range(len(byte_C26050)):
flag += hex(byte_C26050[i] ^ ord(v17[i]))[2:]
print(flag)
#4eb5f3992391a1aeCarry out the results according to the topic MD5 encryption , obtain flag.
flag{d2be2981b84f2a905669995873d6a36c}
For details, please refer to the blogger's wp, It's well written and more specific .
BUUCTF crackMe Answer key .
边栏推荐
- CVPR 2022 | Dalian Institute of technology proposes a self calibration lighting framework for low light level image enhancement of real scenes
- 【无标题】
- Calculation (computer) code of suffix expression
- What kind of good and cost-effective Bluetooth sports headset to buy
- 多线程查询,效率翻倍
- how to add one row in the dataframe?
- Stack - es - official documents - filter search results
- Pytest testing framework
- STM32__05—PWM控制直流电机
- Es interview questions
猜你喜欢

A quick understanding of digital electricity
![[liuyubobobo play with leetcode algorithm interview] [00] Course Overview](/img/1c/c8cab92c74b6658c3ef608c5255f1f.png)
[liuyubobobo play with leetcode algorithm interview] [00] Course Overview

A quick understanding of analog electricity

Soul app released the annual report on generation Z behavior: nearly 20% of young people love shopping in the vegetable market

STM32__ 05 - PWM controlled DC motor

【OpenCV】-5种图像滤波的综合示例

附加:信息脱敏;

How to turn off the LED light of Rog motherboard
![[staff] diacritical mark (ascending sign | descending sign B | double ascending sign x | double descending sign BB)](/img/96/8c4baa1dd8e35e2cab67461e7c447b.jpg)
[staff] diacritical mark (ascending sign | descending sign B | double ascending sign x | double descending sign BB)
【带你学c带你飞】1day 第2章 (练习2.2 求华氏温度 100°F 对应的摄氏温度
随机推荐
实现一个自定义布局的扫码功能
[learn C and fly] 2day Chapter 8 pointer (practice 8.1 password unlocking)
PHP notes - use Smarty to set public pages (include, if, else, variable settings)
[reading notes] programmer training manual - practical learning is the most effective (project driven)
【OpenCV】-5种图像滤波的综合示例
How to turn off the LED light of Rog motherboard
[punch in questions] integrated daily 5-question sharing (phase II)
[pit] how to understand "parameter fishing"
Special symbols in SAP ui5 data binding syntax, and detailed explanation of absolute binding and relative binding concepts
Formatting logic of SAP ui5 currency amount display
es面試題
Stack - es - official documents - filter search results
Analysis of FLV packaging format
【带你学c带你飞】day 5 第2章 用C语言编写程序(习题2)
Face++ realizes face detection in the way of flow
The number one malware in January 2022: lokibot returned to the list, and emotet returned to the top
Mongodb base de données non relationnelle
使用开源项目【Banner】实现轮播图效果(带小圆点)
[learn C and fly] 1day Chapter 2 (exercise 2.2 find the temperature of Fahrenheit corresponding to 100 ° f)
Kibana操控ES