当前位置:网站首页>Log4j vulnerability elk platform processing method (logstah5.5.1)
Log4j vulnerability elk platform processing method (logstah5.5.1)
2022-07-28 22:31:00 【5xp_ two thousand and one】
End of network closure , Start to deal with log4j Loophole :
Method one replaces jar file
Method 2 Delete jar The class in the package
1. Application vulnerability Replace log4j-core xxx .jar
2.es Vulnerabilities need to be replaced core and api Otherwise, the report will be wrong :NoSuchFieldError: EMPTY_BYTE_ARRAY
3.logstah5.5.1 Loophole Take the second way
zip -q -d log4j-core-2.6.2.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Refer to official documentation :Logstash 5.0.0-6.8.20 and 7.0.0-7.16.0: Log4j CVE-2021-44228, CVE-2021-45046 remediation - Security Announcements - Discuss the Elastic Stack
边栏推荐
猜你喜欢
![[LiteratureReview]Object Detection and Mapping with Bounding Box Constraints](/img/37/7cb5fa3a9078a5f5947485147c819d.png)
[LiteratureReview]Object Detection and Mapping with Bounding Box Constraints

If you want to grow rapidly, you must first experience a major blow!
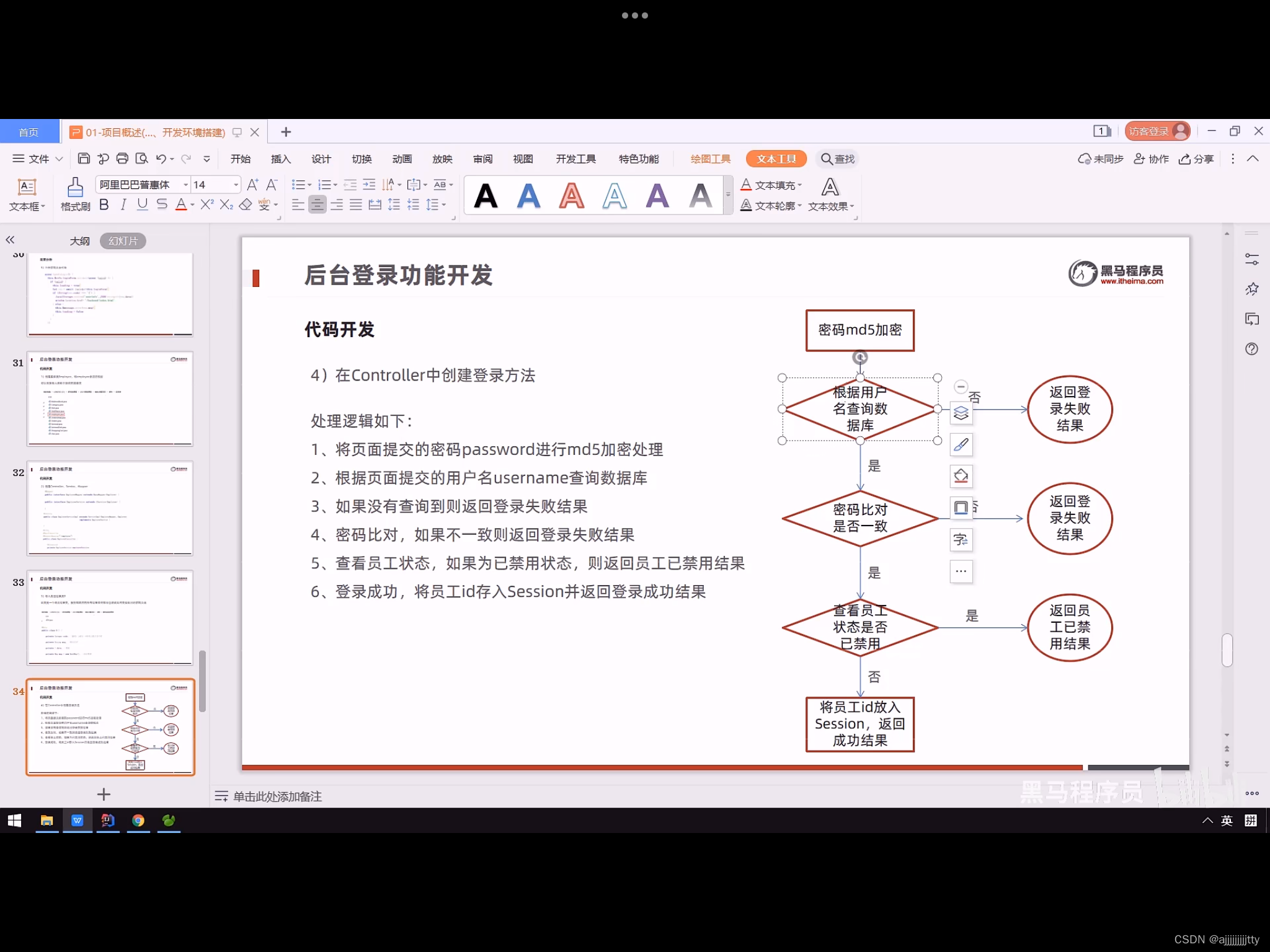
Ruiji takeout - background login function development

6K6w5LiA5qyh5pS75Ye75YiG5p6Q

CDN working principle

JMeter installs third-party plug-ins plugins Manager

Att & CK preliminary understanding

SQL注入 Less42(POST型堆叠注入)

How about the actual use effect of common source oscilloscope

What is time complexity
随机推荐
Less than a year after its establishment! MIT derivative quantum computing company completed financing of US $9million
Lotus 1.16.0 extend sector expiration time
Bugku, Web: all filtered
MySQL command (add, delete, check and modify)
Ruiji takeout - background login function development
Can the MySQL create statement be used to create a table structure and append new records
LeetCode刷题系列之-多数之和类型
Use webworker to perform background tasks
HCIP(9)
SQL injection less42 (post stack injection)
想要快速成长,先要经历重大打击!
[Ruiji takeout project]day4 - dish management
gprs网络指的是什么
ATT&CK初步了解
Sword finger offer II 055. Binary search tree iterator (medium binary search tree iterator)
【二叉树】二叉树中的伪回文路径
The function of wechat applet to cut pictures
普源示波器实际的使用效果怎么样
Solve Jupiter: the term 'Jupiter' is not recognized as the name of a cmdlet, function, script file
flask之蓝图 补充openpyxl