当前位置:网站首页>[translation] Why do you need an API gateway to manage access to your API?
[translation] Why do you need an API gateway to manage access to your API?
2022-07-26 18:10:00 【programmer_ ada】
The original for Armand Sultantono stay Snapt The blog of Guest articles published on
More and more organizations are moving towards API Driven architectural transformation . This powerful method can help them innovate quickly , Integrate with the best external services , And provide new services faster than before .
However , With API It is more and more important for business operation , Provide reliable and consistent services , At the same time protect API It is essential not to be abused or used .API The gateway provides a security and control layer , To protect your data and keep your API High availability is critical . In this post , We will explore these benefits .
API The status quo of
Every organization's API The number is amazing , This is because of dependency API To support applications 、 The ever-increasing number of connections between services and Networks , And the need for real-time data . Even as early as 2018 year ,Akamai The report said ,"API Call the account of network traffic 83%".
Enterprises are bringing their IT attention -- And investment -- Focused on the API On , To achieve this growth of interconnected applications , And extract the maximum value from the data .
Google's 《2021 year API Economic status report 》 say ." Looking forward to the future , Our research shows that , The enterprise plans to increase its investment in API Project investment . The enterprise reports , They are 2021 The main priorities for the year include attention to API Security and Governance (50%),API Adopted growth and management (41%), Invest in building a developer community (38%), adopt API Monetization generates income (31%), Publicly provide more services and data (31%), And add to API Investment in operation and monitoring (20%).
Every industry has endless opportunities API The application case , But the financial and payment industries are API The best example of diffusion . for example , In this industry Open bank It is a global phenomenon , Driven by regulatory movements and changing consumer behavior . Opening up banking can help banks and other financial institutions reduce costs , And provide customers with more choices by providing them with real-time access to bank data . Open banking often leads to improved user experience , Including providing consumers with more choices and lower prices , And provide rich data for financial service providers , In order to quickly approve the loan according to the borrower's risk level . The backbone of open banking is the safe and reliable connection between third-party services and consumer applications API Interface .
API Value chain
API The value chain is " Digital value chain " A synonym for -- A series of transformations , Like an endless digital assembly line of factories .API It's a new way to connect different systems , Realize digital value chain , Unleash innovation and monetization .
One API Value chain , In its simplest form , It can be described as having two aspects .API supplier and API consumer .
Let's look at the characters in the figure below , It describes how to connect different systems API, Unleash innovation and monetization .
Move from left to right .
- End user And User experience Interaction . Now , This is usually a web browser or mobile application .
- Application Developer yes API consumer , They will API Products are transformed into customer-oriented applications . In this case , These are " partners " Application Developer , They consume external services provided by another organization API, And by API Providers' data is transformed into their products and services to create value .
- API product It is elaborately planned for consumption API. They are well documented , And may provide money for consumption .
- API The team yes API owner 、API Developers and wider engineering teams , Responsible for the original internal API Render from the back-end system as renderable API product . They are responsible for designing and maintaining reliable 、 High performance and safe API.
- Background system It is a digital asset composed of data on the server , It can be mined out at any time .
API The challenge of
although API More and more popular in sharing data and services , But they are also getting more and more complex , For these API Access management will soon become API Provider's nightmare .
Security and access control
API It is the channel to the most valuable digital assets of the enterprise . With the API The number is increasing , expect 2022 year API Will surpass web applications , Become the number one attack medium , That's not surprising ( source :apisecurity.io). For you API Providing comprehensive protection is more important than ever .
Most critical API Security risks revolve around access control that exposes valuable data .API, In terms of its nature , Exposed valuable data , Including sensitive information , Such as personal identity information (PII).
Applied logic may also be inadvertently exposed , And create vulnerability carriers for your organization . Unauthorized or excessive access may lead to data disclosure to unauthorized parties , And enter the data utilization of malicious actors 、 Data manipulation or complete takeover of accounts .
Reliability and performance
In order to meet the needs of consumers for real-time data , Need high-performance applications , And supported by a scalable and highly reliable infrastructure . This means that API Meet your... In the context of the value chain API Consumer service level agreements (SLA).
for example , In order to provide the best service level and API The interview of , Availability must be 、 throughput 、 Service level objectives for response time or quality (SLO) Keep at the highest level .
Visibility and governance
It is said that :" What you can't see , You can't guarantee safety ".API It's a new visibility challenge , Because they connect services and data so universally , Not surprisingly , Most organizations don't realize their whole API Assets or " Spread ".
Other factors leading to the spread are cloud native and micro service architecture , Continuous software development drives new API edition , And typical isolated island development challenges .
Many organizations add new ones every week API And eliminate the old API, It is often carried out by multiple teams or sources , Therefore, it may not meet the governance standards . therefore ,API It's a moving target , Manage your API Assets need full visibility and vigilance .
What is? API gateway ?
In its most basic form ,API Gateway receives API Request and return the answer , stay API Consumers and one or more API Act as an intermediary between services or " middleware ".API The gateway handles the whole API Common tasks of service system , Such as user authentication 、 Rate limit 、 Real time indicators, etc .
API The purpose of gateway is to provide a consumer facing facade , To hide many back-end applications in your internal network , These applications can often be a mixture of application code and platform : Traditional monolithic applications on virtual machines , Or containerized or serverless microservices .
essentially ,API Gateway is to manage large-scale access to you API Main control points .
Why do I need a API gateway ?
API Gateways are important for overcoming security and access problems 、 Reliability and performance 、 And visibility and governance API Challenges are crucial .
without API gateway , You will need to build complex routing rules and write custom code , To deal with consumers and third-party systems that may access your API All the different ways .API Gateway enables access to your API Become simple , At the same time, it also ensures that they are safe in all consumption patterns 、 Reliable and consistent .
Besides , A platform independent API The gateway will support API visit , No matter where or how your service is hosted on your transformation .
One API The gateway will .
- To resist Common and specific API Loophole .API Protection is usually based on network applications and API Protect (WAAP) In the form of firewall , This is designed to protect network applications and API And highly specialized tools designed .
- Prevent unauthorized access , At the same time, only authorized users are allowed to access the information they need , Measurement and fair use can also be implemented when necessary .
- Ensure the quality of service (QoS) And service level agreements (SLA). the Hierarchical consumers ( Such as " bronze " and " Platinum ") Must be achieved by maintaining the highest level of reliability and performance , Get acceptable SLA.API The gateway needs dynamic routing 、 Service health check 、 Circuit interruption of poor performance or failed Services , And more .
- Manage multiple API Version access . along with With the expansion of your application , new API Will appear , The existing API Will retire , However , Consumers still want to find all your services in one place , Learn how to use the newer version API, And transition to this version at your own pace .
- Regardless of the number or composition of internal microservices , For external consumers Provide a single entry point . A microservice based architecture may consist of dozens or hundreds of heterogeneous services .
- Through real-time analysis and monitoring , Provide How consumers use your API Of insight .
- Access quotas and billing to management API Monetization strategy .
- promote Between microservices in the service mesh Secure internal communication .
summary
because API It is more and more important for the operation of enterprises , therefore , Protect and access these API It's very important .
If one API The gateway sounds like something you need , To keep up with changing technological trends , We will help here !
Contact us today , understand Snapt Nova How to help your enterprise be more successful than ever in rapid innovation and providing new services - All these will not affect the protection of your most valuable assets .
边栏推荐
- 如何组装一个注册中心?
- ICML 2022 (Part 4) | | graph hierarchical alignment graph kernel to realize graph matching
- How to switch nodejs versions at will?
- JS recursive Fibonacci sequence deep cloning
- 【欧米读书会】谈谈元宇宙中的创作者经济:无限次元
- 带你熟悉云网络的“电话簿”:DNS
- Cross Site Request Forgery (CSRF)
- AI zhetianchuan ml unsupervised learning
- LeetCode50天刷题计划(Day 5—— 最长回文子串 10.50-13:00)
- 菜鸟 CPaaS 平台微服务治理实践
猜你喜欢
![[unity3d] rocker](/img/b7/40643a2676b251c185ce58840f7581.png)
[unity3d] rocker

ACL实验演示(Huawei路由器设备配置)

Sign up now | oar hacker marathon phase III midsummer debut, waiting for you to challenge

COSCon'22城市/学校/机构出品人征集令
![[static code quality analysis tool] Shanghai daoning brings you sonarource/sonarqube download, trial and tutorial](/img/09/209a405953d99d7d8b347c01873eba.png)
[static code quality analysis tool] Shanghai daoning brings you sonarource/sonarqube download, trial and tutorial
![[Digital IC] understand Axi Lite protocol in simple terms](/img/2b/15b3d831bba6aa772ad83f3ac91d23.png)
[Digital IC] understand Axi Lite protocol in simple terms

web项目文件简单上传和下载
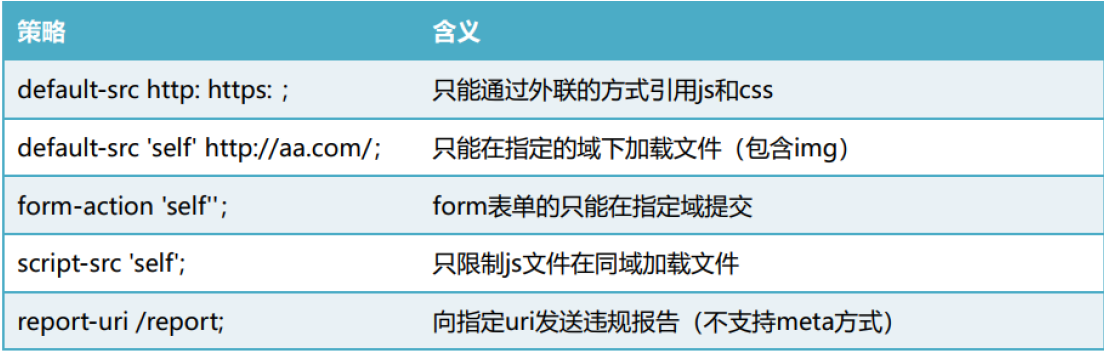
Cross site scripting attack (XSS)

Vector CANoe Menu Plugin拓展入门
![[Oumi reading club] talk about the creator economy in the meta universe: infinite dimension](/img/60/17cb0295f81dc580cc3ff8543ec253.png)
[Oumi reading club] talk about the creator economy in the meta universe: infinite dimension
随机推荐
兆骑科创海外高层次人才引进平台,创业赛事活动路演
Coscon'22 city / school / institution producer solicitation order
236. The nearest common ancestor of a binary tree
【模板】线段树 1
Week 17 free intrusion pointer exercise - output maximum
Cross Site Request Forgery (CSRF)
7、 Common commands of ROS (II): rosservice, rossrv, rosparam
相对路径与绝对路径
Diagram of seven connection modes of MySQL
Point cloud target detection Kitti dataset bin file visualization, one-stop solution
【集训Day2】Sculpture
openssl
kaggle猫狗数据集开源——用于经典CNN分类实战
DTS is equipped with a new self-developed kernel, which breaks through the key technology of the three center architecture of the two places Tencent cloud database
【集训Day2】cinema ticket
The chess robot broke the finger of a 7-year-old boy because "the chess player violated safety rules"?
【集训Day2】Torchbearer
PMP考生必读,7月30日考试防疫要求都在这里
.Net CLR GC 动态加载短暂堆阈值的计算及阈值超量的计算
COSCon'22城市/学校/机构出品人征集令