当前位置:网站首页>Cross Site Request Forgery (CSRF)
Cross Site Request Forgery (CSRF)
2022-07-26 17:47:00 【Leisurely summer】
CSRF The full name of the attack is cross site request forgery ( cross site request forgery ): Is a malicious use of the site , Although it sounds like XSS Cross site scripting attacks are a bit similar , But in fact CSRF And XSS The difference is very big ,XSS Use the trusted users in the site , and CSRF It is to use the trusted website by masquerading the request from the trusted user .

Simple understanding : A vulnerability that can be used by an attacker to send a forged request to the server through the user browser pretending to be a user and successfully executed by the target server is called CSRF Loophole .
characteristic :
- User browser : Represents a trusted user for
- Impersonation : Malicious programs impersonate trusted users ( browser ) identity
- Falsify a request : Access initiated by a trusted user's browser
1、CSRF Attack principle
CSRF The attack principle and process are as follows :
1. The user opens the browser , Visit trusted sites A, Enter the user name and password to log in to the website A;
2. After the user authenticates the information , Website A produce Cookie Information and return it to the browser , At this time, the user logs into the website A success , Can send request to website normally A;
3. The user did not exit the website A Before , In the same browser , Open one TAB Page visit website B;
4. Website B After receiving the user's request , Return some offensive code , And send a request to visit a third-party site A;
5. After the browser receives the attack code , According to the website B Request , Carry... Without the user's knowledge Cookie Information , To the website A Request . Website A I don't know that the request was actually made by B Sponsored , So according to the user C Of Cookie Information to C Permission to process the request , Lead from website B The malicious code was executed .

2、CSRF Analysis of the causes of loopholes
get request :
<img src="http://www.study.com/admin/resetPassword?id=1" />
<iframe src="http://www.study.com/admin/resetPassword?id=1"style='display:none'></iframe>post request :
<!-- Hide form 、 Automatic submission , Pass the function iframe Introduce a new page -->
<iframe src="form.html" style='display:none'></iframe>3、CSRF Vulnerability hazard analysis
CSRF Attack characteristics :
- Attack timing : Website cookie There is no expiration in the browser , Don't close the browser or log out
- Attack premise : Have a certain understanding of the target website interface
- Attack difficulty : The attack is more difficult than XSS
- And XSS Compared to attack ,CSRF Attacks are often unpopular ( So there are few resources to guard against it ) And hard to prevent , So it's considered a ratio XSS More dangerous .
harm :

4、CSRF Safety protection
- Distinguish whether it is a forged request
- Secondary verification
referer check :
HTTP Referer yes header Part of , When the browser to web When the server sends the request , Usually with Referer, Tell the server which page is linked from , The server can therefore obtain some information for processing .
- Verify in the gateway filter
- Define interceptors in the corresponding microservices
- Specific business code
Exceptions : Sign in
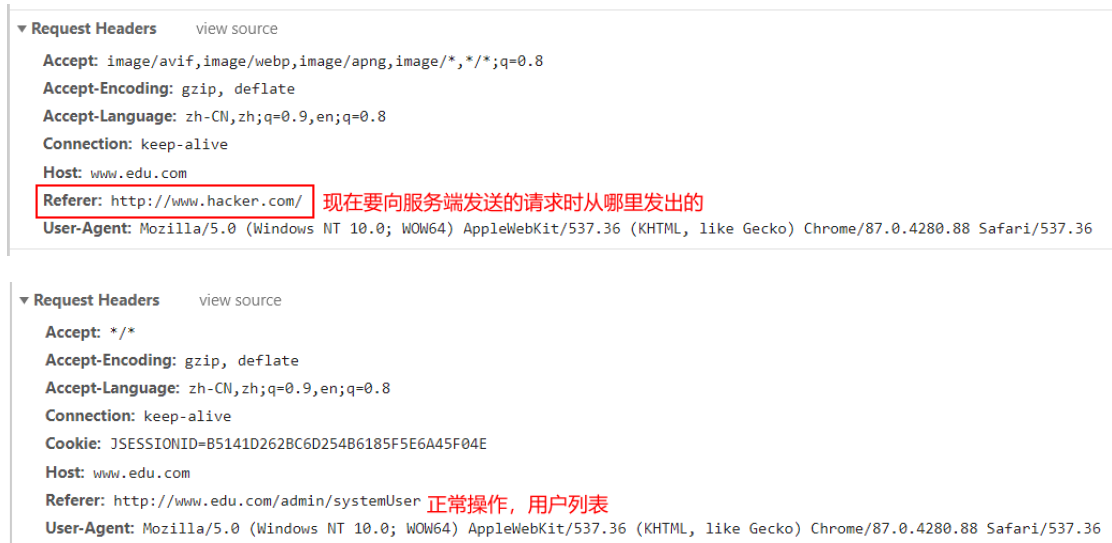
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws
Exception {
logger.debug(" The interceptor intercepted the right :{} The interview of ", request.getRequestURI());
String referer = request.getHeader("referer");
logger.debug("referer:{}", referer);
StringBuilder sb = new StringBuilder();
sb.append(request.getScheme()).append("://").append(request.getServerName());
logger.debug("basePath:{}", sb.toString());
if (referer == null || referer == "" || !referer.startsWith(sb.toString())) {
response.setContentType("text/plain; charset=utf-8");
response.getWriter().write(" Illegal access , Please ask normally through the page !");
return false;
}
return true;
}Business secondary verification :
- Change Password , You need to enter the original password
- The transaction system sets the transaction password
- Add graphic verification code verification
- Online banking transfer SMS verification code
5、CSRFTester
CSRFTester Is a CSRF Vulnerability testing tools , The test principle of this tool is as follows : It uses a proxy to grab the accessed connections and forms in the browser , By means of CSRFTester Modify the corresponding forms and other information , To resubmit , It's equivalent to a fake client request , If the tested request is successfully accepted by the website server , It means that there is CSRF Loophole , Otherwise, it doesn't exist . This tool can also be used for CSRF attack .
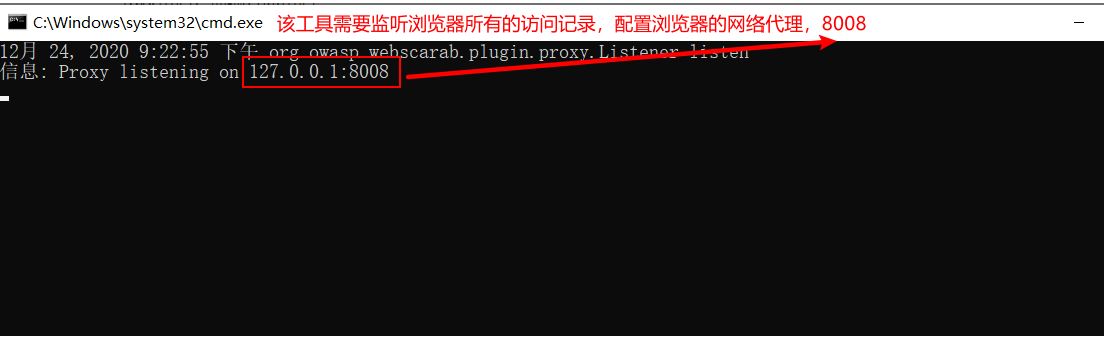


After accessing the browser manually , Will be in CSRF tester Record the access path , To generate CSRF attack html

边栏推荐
- 就这一次!详细聊聊分布式系统的那些技术方案
- 股票公司开户万一免五这是真的安全靠谱的吗
- 重磅公布!ICML2022奖项:15篇杰出论文,复旦、厦大、上交大研究入选
- JS 递归 斐波那契数列 深克隆
- ASEMI整流桥KBPC3510,KBPC3510封装,KBPC3510应用
- Tupu 3D visual national style design | collision between technology and culture "cool" spark“
- 深度学习实验:Softmax实现手写数字识别
- Tree DP problem
- The latest interface of Taobao / tmall keyword search
- 兆骑科创海外高层次人才引进平台,创业赛事活动路演
猜你喜欢

树形dp问题
机器视觉在服务机器人中的应用
【OpenCV 例程 300篇】240. OpenCV 中的 Shi-Tomas 角点检测

6-19 vulnerability exploitation -nsf to obtain the target password file

RedisDesktopManager去除升级提示
带你熟悉云网络的“电话簿”:DNS

Gan (generative adversarial network, GaN) generative countermeasure network

ASEMI整流桥KBPC2510,KBPC2510参数,KBPC2510规格书
重磅!《2022中国开源发展蓝皮书》正式发布

天翼云Web应用防火墙(边缘云版)支持检测和拦截Apache Spark shell命令注入漏洞
随机推荐
2019 popularization group summary
Leetcode:1206. design jump table [jump table board]
The diagram of user login verification process is well written!
一文详解吞吐量、QPS、TPS、并发数等高并发指标
【欧米读书会】谈谈元宇宙中的创作者经济:无限次元
Common super easy to use regular expressions!
6-19 vulnerability exploitation -nsf to obtain the target password file
【集训Day2】cinema ticket
Environment setup mongodb
带你熟悉云网络的“电话簿”:DNS
云渲染-体积云【理论基础与实现方案】
Pytest(思维导图)
【集训Day1】Spy dispatch
【模板】线段树 1
CCS TM4C123新建工程
AI遮天传 ML-集成学习
性能调优bug层出不穷?这3份文档轻松搞定JVM调优
Spark数据格式UnsafeRow
[300 opencv routines] 240. Shi Tomas corner detection in opencv
常用超好用正则表达式!