当前位置:网站首页>IPFs of Internet Protocol
IPFs of Internet Protocol
2022-07-25 22:54:00 【InfoQ】
URLDNSIPHTTPHTTPSHypertext Transfer Protocol SecureSSLTLSwebserverHTTPSIPFS The origin of the agreement
Protocol Lab
IPFS The features of the agreement
- Content positioning is easy to access: Usually , When searching for files, you need to process data through the central server . In this case, the access efficiency is low , The central server is prone to crash when too many visits are made . However ,IPFS Use content addressing to assign a unique encrypted hash value to each file . Hash information is generated by running on IPFS Blockchain storage on . When the network needs to access it , Just look up the corresponding hash information on this chain .
- Distributed storage saves resources:IPFS Each node in the protocol is both a client and a server . When downloading data , Users can download from the nearest node at the same time , Avoid network congestion caused by a large number of access to the central server .
- Decentralization ensures data security:IPFS Agreement will data “ Fragmentation ”, Decentralized storage . therefore , When you encounter a large number of access requests , for example DDoS attack , All accesses will be distributed to different nodes , Even the attacker himself . This decentralization makes IPFS Avoid the collapse of traditional centralized servers .
- Historical data is permanently saved: When you meet 404 error , That is, when the page cannot be found , It may be caused by the deletion of data on the server or the shutdown of the server . stay IPFS in , As long as one of the nodes views specific data , Will store the data . Because these data are shared and used by the whole network , Therefore, the inaccessibility problem caused by deleting the data of one of the nodes can be avoided .
IPFS Use of protocol
边栏推荐
- Mysql数据类型
- 3 lexical analysis
- 【论文笔记】A Meta-Reinforcement Learning Algorithm for Causal Discovery
- invalid syntax
- ECMA 262 12 Lexical Grammer
- We media people must have four material websites, and don't worry about finding materials anymore
- JVM内存区域
- Two methods of printing strings in reverse order in C language
- [training Day11] Calc [mathematics]
- 栈与Stack类
猜你喜欢
![[文献阅读] - HRL -[HRL with Universal Policies for Multi-Step Robotic Manipulation]](/img/34/06d5ba3af4e6e775a335324c020161.png)
[文献阅读] - HRL -[HRL with Universal Policies for Multi-Step Robotic Manipulation]
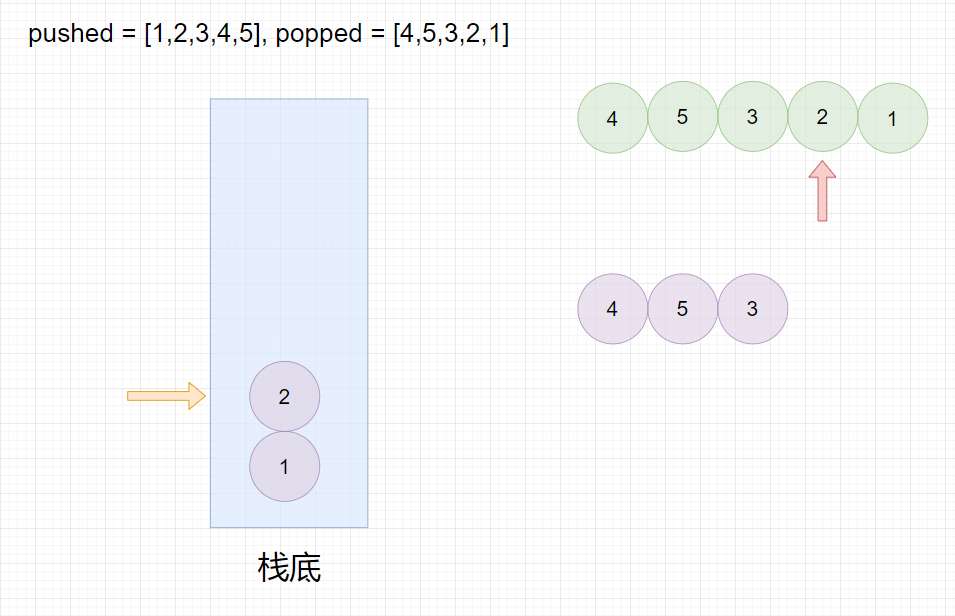
栈与Stack类

Anaconda~Upload did not complete.

新媒体运营策略(以小红书为例)帮助你快速掌握爆款创作方法
Naming rules of software test pytest pytest the pre and post confitest of use cases Py customized allure report @pytest.mark.parameter() decorator as data-driven
Binder principle

Kibana~后台启动Kibana之后无法找到进程号

JSON object
![[MySQL rights] UDF rights (with Malaysia)](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[MySQL rights] UDF rights (with Malaysia)

DHCP first static experiment
随机推荐
Review of static routing
[training day15] boring [tree DP]
[training day13] out race [mathematics] [dynamic planning]
Today, learn about the use of lists, hyperlinks, image tags, and audio and video
Binder原理
Vs2019 WinForm clr20r3 error
Analysis of Excel file
互联网协议之 IPFS
ECMA 262 12 Lexical Grammer
[MySQL rights] UDF rights (with Malaysia)
BIO、NIO、AIO的区别?
新媒体运营策略(以小红书为例)帮助你快速掌握爆款创作方法
Naming rules of software test pytest pytest the pre and post confitest of use cases Py customized allure report @pytest.mark.parameter() decorator as data-driven
SSH服务器CBC加密模式漏洞(CVE-2008-5161)
软件测试 pytest pytest的命名规则 用例的前后置 conftest.py 定制allure报告 @pytest.mark.parametrize()装饰器作数据驱动
QT Chinese programming encounters c2001 error, prompting "there is a newline character in the constant"
Solve several common problems
Network Security Learning (16)
自媒体人必备的4个素材网站,再也不用担心找不到素材
QT的Tree View Model示例