当前位置:网站首页>Summary of JWT related knowledge
Summary of JWT related knowledge
2022-07-04 01:04:00 【-*Xiao Kai】
JWT(json web token)
Definition
Json web token (JWT), Is a kind of implementation based on the JSON Open standards for ((RFC 7519). The token Designed to be compact and safe , Especially for single sign in of distributed sites (SSO) scene .JWT The declaration of is generally used to pass the authenticated user identity information between the identity provider and the service provider , To get resources from the resource server , You can also add some additional declaration information that other business logic requires , The token It can also be used directly for authentication , It can also be encrypted .
session Authentication and token Differences in certification
session:
We know ,http Protocol itself is a stateless protocol , This means that if the user provides a user name and password to our application for user authentication , So the next time you ask , The user has to do user authentication again , Because according to http agreement , We don't know which user made the request , So in order for our application to recognize which user made the request , We can only store one copy of user login information on the server , This login information will be passed to the browser in response , Tell it to save as cookie, So that the next request can be sent to our app , So our application can identify which user the request came from , This is the basis of tradition session authentication
token:
be based on token The authentication mechanism of is similar to http The agreement is also stateless , It doesn't need to keep the user's authentication information or session information in the server . That means based on token The application of authentication mechanism does not need to consider which server the user logs in , This facilitates the expansion of the application .
##session Disadvantages of Authentication
Session: After each user has passed our application authentication , All of our applications should be recorded on the server , In order to facilitate the identification of the user's next request , generally session It's all stored in memory , And with the increase of authenticated users , The cost of the server will increase obviously .
Extensibility : After user authentication , The server makes authentication records , If the authentication record is stored in memory , This means that the next time a user requests it, he must request it on this server , In this way, we can get the authorized resources , So in distributed applications , Accordingly, the capacity of load balancer is limited . This also means that the expansion ability of the application is limited .
CSRF: Because it's based on cookie For user identification , cookie If intercepted , Users will be vulnerable to cross site request forgery attacks .
token Action process
- The user uses the user name and password to request the server
- The server verifies the user's information
- The server is sent to the user by authentication token
- Client storage token, And attach this to every request token value
- Server side validation token value , And return the data
This token It has to be passed to the server on every request , It should be kept in the request header , in addition , The server should support CORS( Cross source resource sharing ) Strategy , Generally, we can do this on the server side Access-Control-Allow-Origin: *.
JWT The composition of the
jWT It consists of three pieces of information (), These three pieces of information together form a paragraph jwt character string , Between each part . Connect
header
header It contains two parts of information :
Declaration type
Declare the encryption algorithm Usually used directly HMAC SH256
Such as :
{ 'typ': 'JWT', 'alg': 'HS256' }Then perform base64 encryption ( This encryption can constitute symmetric decryption ), Constitute the JWT The first part of
###payloadThe load is where the payload is stored . The name seems to refer to the goods carried on the plane , The valid information consists of three parts
- A statement registered in the standard
- Public statement
- Private statement
A statement registered in the standard
iss: jwt Issuer
sub: jwt Target users
aud: receive jwt On the side of
exp: jwt The expiration time of , The expiration time must be greater than the issuing time
nbf: Define before what time , The jwt They're not available .
iat: jwt Issued on
jti: jwt Unique identity of , Mainly used as a one-off token, To avoid replay attacks .
Public statement
Public statements can add any information , Generally, add relevant information of users or other necessary information required by business , But it's not recommended to add sensitive information , Because this part can be decrypted on the client
Private statement
A private statement is a statement defined by both the provider and the consumer , It is generally not recommended to store sensitive information , because base64 It's symmetric decryption , It means that this part of information can be classified as clear text information .
payload Example :
{
"sub": "1234567890",
"name": "John Doe",
"admin": true
}
### Visa information (signature)
Visa information consists of three parts :
header (base64 After )
payload (base64 After )
secret
This part needs base64 Encrypted header and base64 Encrypted payload Use
.String of connections , And then through header Adding salt in the encryption method stated insecretCombination encryption , And then it forms jwt Part three .
Be careful :secret It's stored on the server side ,jwt The signature generation of is also on the server side ,secret It's used to do jwt And jwt Validation of the , therefore , It is the private key of your server , It should not be revealed in any scene . Once the client knows this secret, That means that the client can issue itself jwt 了 .
## advantage
because json The generality of , therefore JWT Cross language support is available , image JAVA,JavaScript,NodeJS,PHP And many other languages can be used .
Because of the payload part , therefore JWT It can store some non sensitive information necessary for other business logic in itself .
Easy to transmit ,jwt It's very simple , Bytes are very small , So it's very easy to transmit .
It doesn't need to save session information on the server , So it's easy to apply extensions
Safety related
- Should not be in jwt Of payload Some store sensitive information , Because this part is the decryptable part of the client .
- Well protected secret Private key , The private key is very important .
- If possible , Please use https agreement
Tools
jwt.io decode ( Online parsing and decoding jwt token Tools )
base64
jwt.py
边栏推荐
- CLP information - how does the digital transformation of credit business change from star to finger?
- Avoid playing with super high conversion rate in material minefields
- 【.NET+MQTT】.NET6 环境下实现MQTT通信,以及服务端、客户端的双边消息订阅与发布的代码演示
- How to be a professional software testing engineer? Listen to the byte five year old test
- Release and visualization of related data
- PMP 考试常见工具与技术点总结
- 求esp32C3板子连接mssql方法
- 查询效率提升10倍!3种优化方案,帮你解决MySQL深分页问题
- Flutter local database sqflite
- Regular expression of shell script value
猜你喜欢
基于.NetCore开发博客项目 StarBlog - (14) 实现主题切换功能
Avoid playing with super high conversion rate in material minefields

Cloud dial test helps Weidong cloud education to comprehensively improve the global user experience

Function: write function fun to find s=1^k+2^k +3^k ++ The value of n^k, (the cumulative sum of the K power of 1 to the K power of n).
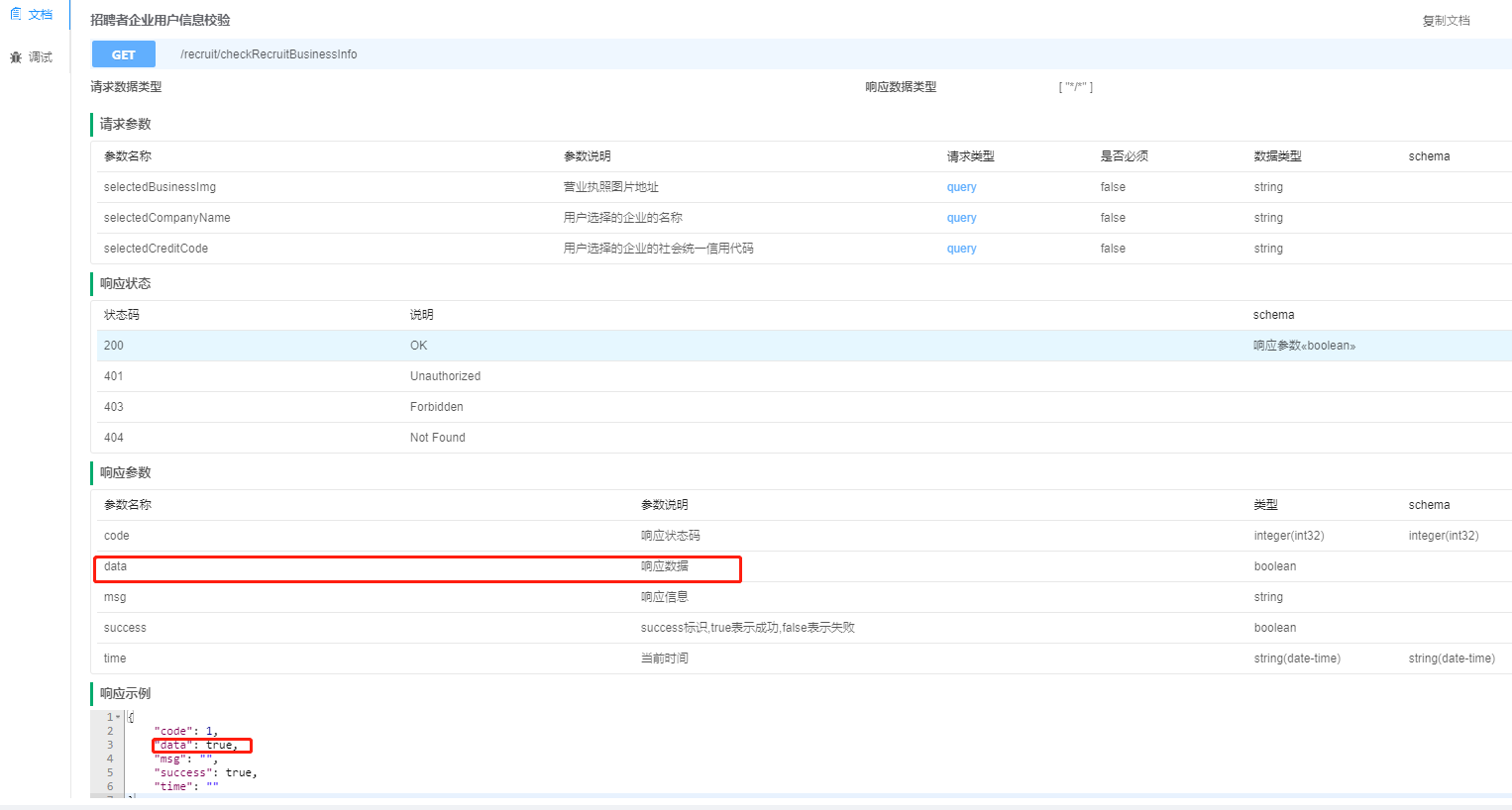
swagger中响应参数为Boolean或是integer如何设置响应描述信息

From functional testing to automated testing, how did I successfully transform my salary to 15K +?

It's OK to have hands-on 8 - project construction details 3-jenkins' parametric construction

Unity Shader入门精要读书笔记 第三章 Unity Shader基础

GUI application: socket network chat room

AI helps make new breakthroughs in art design plagiarism retrieval! Professor Liu Fang's team paper was employed by ACM mm, a multimedia top-level conference
随机推荐
Sorry, Tencent I also refused
AI helps make new breakthroughs in art design plagiarism retrieval! Professor Liu Fang's team paper was employed by ACM mm, a multimedia top-level conference
leetcode 121 Best Time to Buy and Sell Stock 买卖股票的最佳时机(简单)
MPLS experiment
What is the GPM scheduler for go?
How to set the response description information when the response parameter in swagger is Boolean or integer
Alibaba test engineer with an annual salary of 500000 shares notes: a complete set of written tests of software testing
求esp32C3板子连接mssql方法
2022 Software Test Engineer skill list, please check
The super fully automated test learning materials sorted out after a long talk with a Tencent eight year old test all night! (full of dry goods
中电资讯-信贷业务数字化转型如何从星空到指尖?
On covariance of array and wildcard of generic type
【.NET+MQTT】.NET6 环境下实现MQTT通信,以及服务端、客户端的双边消息订阅与发布的代码演示
我管你什么okr还是kpi,PPT轻松交给你
[cloud native topic -48]:kubesphere cloud Governance - operation - overview of multi tenant concept
查询效率提升10倍!3种优化方案,帮你解决MySQL深分页问题
Function: write function fun to find s=1^k+2^k +3^k ++ The value of n^k, (the cumulative sum of the K power of 1 to the K power of n).
国元证券开户是真的安全可靠吗
老姜的特点
Att & CK actual combat series - red team actual combat - V