当前位置:网站首页>Save Private Ryan - map building + voltage dp+deque+ shortest circuit
Save Private Ryan - map building + voltage dp+deque+ shortest circuit
2022-07-04 01:58:00 【Wawa source】
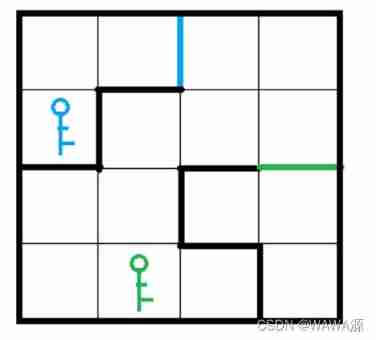
Topic link
#include <iostream>
#include <cstring>
#include <algorithm>
#include <set>
#include <deque>
#include <vector>
using namespace std;
#define x first
#define y second
typedef pair<int,int>PII;
const int N = 110,M = 1<<10;
vector<PII>g[N];
set<PII>edges; // Judge whether the edge has been built in the figure
int n,m,p,k;
int dist[N][M]; // The first dimension is coordinates , The second dimension is the key state
bool st[N][M]; // Judge whether it has been updated , If it is updated, it will be the minimum , There is no need to change
int id[12][12]; // Map two dimensions to one dimension , Easy to write
int key[N]; // Record the key of each position , In binary
void build()
{
int dx[4]={
1,0,-1,0},dy[4]={
0,1,0,-1};
for(int i=1;i<=n;i++)
{
for(int j=1;j<=m;j++)
{
for(int u=0;u<4;u++)
{
int x=i+dx[u],y=j+dy[u];
if(x<1||x>n||y<1||y>m)continue;
int a=id[i][j],b=id[x][y];
// Build a map while walking that is not built in the map
if(!edges.count({
a,b}))
g[a].push_back({
b,0});
}
}
}
}
int bfs()
{
// deque ,
memset(dist,0x3f,sizeof dist);
deque<PII>q;
q.push_back({
1,0});
dist[1][0]=0;
while(q.size())
{
auto t=q.front();
q.pop_front();
if(st[t.x][t.y])continue;
st[t.x][t.y]=true;
if(t.x==n*m)return dist[t.x][t.y];
// Pick up the key in this position
if(key[t.x])
{
int state=t.y|key[t.x];
if(dist[t.x][state]>dist[t.x][t.y])
{
dist[t.x][state]=dist[t.x][t.y];
q.push_front({
t.x,state});
}
}
for(auto [v,w] : g[t.x])
{
// If you need a key for the next position , But the last point is updated, and you can skip directly without this key
if(w&&!(t.y>>w-1&1))continue;
if(dist[v][t.y]>dist[t.x][t.y]+1)
{
dist[v][t.y]=dist[t.x][t.y]+1;
q.push_back({
v,t.y});
}
}
}
return -1;
}
signed main()
{
cin>>n>>m>>p>>k;
for(int i=1,t=1;i<=n;i++)
for(int j=1;j<=m;j++)
id[i][j]=t++;
for(int i=1;i<=k;i++)
{
int x1,y1,x2,y2,c;
cin>>x1>>y1>>x2>>y2>>c;
int a=id[x1][y1],b=id[x2][y2];
edges.insert({
a,b});
edges.insert({
b,a});
if(c)g[a].push_back({
b,c}),g[b].push_back({
a,c});
}
build();
int s;
cin>>s;
while(s--)
{
int x1,y1,c;
cin>>x1>>y1>>c;
key[id[x1][y1]]|=1<<c-1;
}
cout<<bfs()<<endl;
}
边栏推荐
- 51 MCU external interrupt
- Iclr2022 | ontoprotein: protein pre training integrated with gene ontology knowledge
- Introduction to graphics: graphic painting (I)
- What are the advantages and disadvantages of data center agents?
- C import Xls data method summary IV (upload file de duplication and database data De duplication)
- What are the main investment products of bond funds and what are they
- Why is the operation unsuccessful (unresolved) uncaught syntaxerror: invalid or unexpected token (resolved)
- The contact data on Jerry's management device supports reading and updating operations [articles]
- Jerry's modification setting status [chapter]
- Is Shengang securities company as safe as other securities companies
猜你喜欢

Final consistency of MESI cache in CPU -- why does CPU need cache
LeetCode 168. Detailed explanation of Excel list name

Override and virtual of classes in C #

MySQL advanced (Advanced) SQL statement (I)

Remember another interview trip to Ali, which ends on three sides
![Jerry's modification setting status [chapter]](/img/23/d6eb521943b35e543a9681a98ad3be.jpg)
Jerry's modification setting status [chapter]
Use classname to modify style properties

Yyds dry goods inventory it's not easy to say I love you | use the minimum web API to upload files

Small program graduation project based on wechat reservation small program graduation project opening report reference
String & memory function (detailed explanation)
随机推荐
All metal crowns - current market situation and future development trend
Small program graduation project based on wechat examination small program graduation project opening report function reference
2022 R2 mobile pressure vessel filling certificate examination and R2 mobile pressure vessel filling simulation examination questions
Jerry's synchronous weather information to equipment [chapter]
Chapter 3.4: starrocks data import - Flink connector and CDC second level data synchronization
Neo4j learning notes
Solution of cursor thickening
Ceramic metal crowns - current market situation and future development trend
Should enterprises start building progressive web applications?
Push technology practice | master these two tuning skills to speed up tidb performance a thousand times!
Basic editing specifications and variables of shell script
Portapack application development tutorial (XVII) nRF24L01 launch C
What are the main investment products of bond funds and what are they
Summary of JWT related knowledge
2022 new examination questions for safety management personnel of hazardous chemical business units and certificate examination for safety management personnel of hazardous chemical business units
Remember another interview trip to Ali, which ends on three sides
Software product download collection
Learn these super practical Google browser skills, girls casually flirt
Applet graduation project based on wechat selection voting applet graduation project opening report function reference
Hunan University | robust Multi-Agent Reinforcement Learning in noisy environment