当前位置:网站首页>Hong Kong Polytechnic University | data efficient reinforcement learning and adaptive optimal perimeter control of network traffic dynamics
Hong Kong Polytechnic University | data efficient reinforcement learning and adaptive optimal perimeter control of network traffic dynamics
2022-07-03 16:27:00 【Zhiyuan community】
【 title 】Data efficient reinforcement learning and adaptive optimal perimeter control of network traffic dynamics
【 The author team 】C. Chen, Y.P. Huang, W.H.K. Lam, T.L. Pan, S.C. Hsu, A. Sumalee, R.X. Zhong
【 Date of publication 】2022.6.28
【 Thesis link 】https://www.sciencedirect.com/sdfe/reader/pii/S0968090X22001929/pdf
【 Recommended reasons 】 The existing data-driven and feedback flow control strategies do not consider the heterogeneity of real-time data measurement . Besides , Traditional traffic control reinforcement learning (RL) Due to the lack of data efficiency , Usually slow convergence . Moreover, the traditional optimal perimeter control scheme needs to accurately understand the system dynamics , Therefore, they are vulnerable to endogenous uncertainty . In this paper, we propose a holistic reinforcement learning (IRL) To learn macro traffic dynamics , To achieve adaptive optimal perimeter control . The main contribution of this paper is :(a) Continuous time control with discrete gain update is developed , To adapt to discrete-time sensor data .(b) In order to reduce sampling complexity and use available data more effectively , Replay experience (ER) Technology introduction IRL Algorithm .(c) The proposed method is based on “ No model ” The method relaxes the requirements for model calibration , Through data-driven RL The algorithm achieves robustness to modeling uncertainty and improves real-time performance .(d) be based on IRL The convergence of the algorithm and the stability of the controlled traffic dynamics are proved theoretically . The optimal control law is parameterized , Then through neural network (NN) Approaching , This reduces the computational complexity .
边栏推荐
- 特征多项式与常系数齐次线性递推
- Q2 encryption market investment and financing report in 2022: gamefi becomes an investment keyword
- 远程文件包含实操
- How to use AAB to APK and APK to AAB of Google play apps on the shelves
- [web security] - [SQL injection] - error detection injection
- The mixlab editing team is recruiting teammates~~
- [combinatorics] combinatorial identities (sum of variable terms 3 combinatorial identities | sum of variable terms 4 combinatorial identities | binomial theorem + derivation to prove combinatorial ide
- NFT新的契机,多媒体NFT聚合平台OKALEIDO即将上线
- 中南大学|通过探索理解: 发现具有深度强化学习的可解释特征
- AcWing 第58 场周赛
猜你喜欢

Q2 encryption market investment and financing report in 2022: gamefi becomes an investment keyword

Unreal_DataTable 实现Id自增与设置RowName
![[web security] - [SQL injection] - error detection injection](/img/18/5c511871dab0e5c684b6b4c081c061.jpg)
[web security] - [SQL injection] - error detection injection
![[solved] access denied for user 'root' @ 'localhost' (using password: yes)](/img/71/1ff8ed1d773da99054310f96dca3f8.jpg)
[solved] access denied for user 'root' @ 'localhost' (using password: yes)
![[proteus simulation] 8 × 8LED dot matrix screen imitates elevator digital scrolling display](/img/46/c7f566f8fd46d383b055582d680bb7.png)
[proteus simulation] 8 × 8LED dot matrix screen imitates elevator digital scrolling display
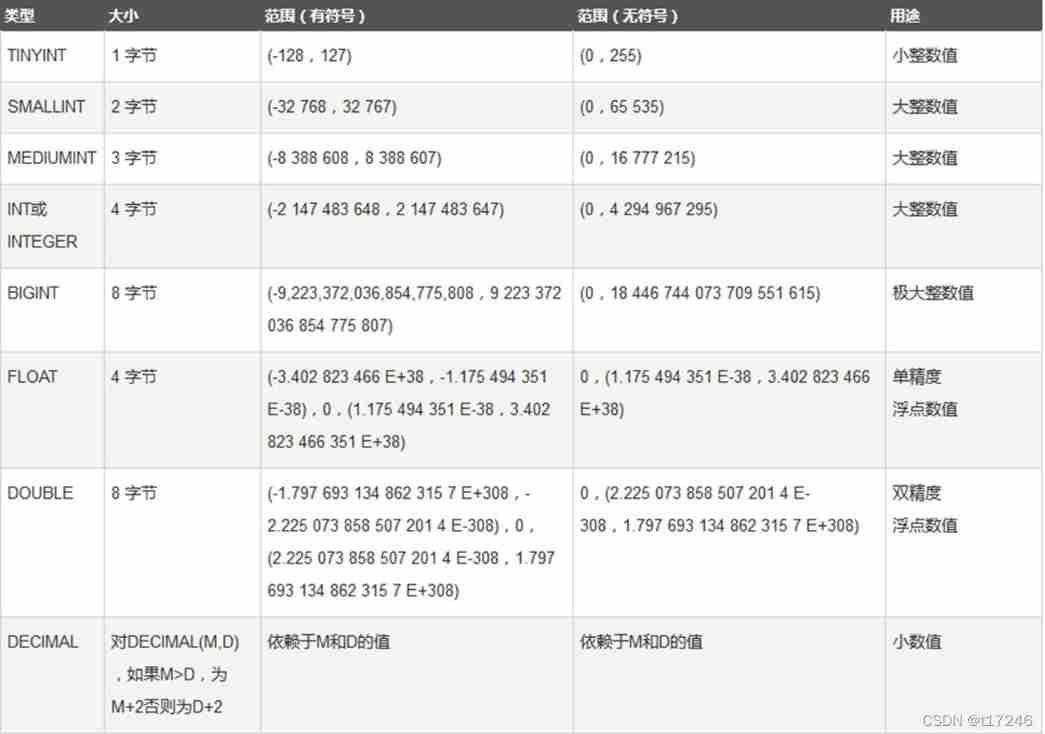
First knowledge of database
(补)双指针专题

NSQ source code installation and operation process

One article takes you to understand machine learning

2022爱分析· 国央企数字化厂商全景报告
随机推荐
Svn usage specification
Interviewer: how does the JVM allocate and recycle off heap memory
QT serial port UI design and solution to display Chinese garbled code
PHP中register_globals参数设置
TCP擁塞控制詳解 | 3. 設計空間
The mixlab editing team is recruiting teammates~~
June to - -------
[proteus simulation] 8 × 8LED dot matrix screen imitates elevator digital scrolling display
Batch files: list all files in a directory with relative paths - batch files: list all files in a directory with relative paths
Embedded development: seven reasons to avoid open source software
How to thicken the brush in the graphical interface
[redis foundation] understand redis master-slave architecture, sentinel mode and cluster together (Demo detailed explanation)
EditText request focus - EditText request focus
How programming apes grow rapidly
Qt插件之自定义插件构建和使用
pycharm错Error updating package list: connect timed out
pyinstaller不是内部或外部命令,也不是可运行的程序 或批处理文件
用同花顺炒股开户安全吗?
疫情常态化大背景下,关于远程办公的思考|社区征文
Golang 匿名函数使用