当前位置:网站首页>User login function: simple but difficult
User login function: simple but difficult
2022-07-04 08:29:00 【Huawei cloud developer community】
This article is shared from Huawei cloud community 《 User login of performance analysis TPS Low and CPU Filled with problem analysis 》, author :zuozewei .
User login is just a common function , But its logic is not simple at all . Because the login process needs to compare and verify personal information , During the verification process, the corresponding encryption algorithm must be called , Encryption algorithm is a function that requires high performance . The complex encryption algorithm has high security , But the performance is poor ; Uncomplicated encryption algorithm has good performance , But it's safe , This is a question of trade-offs .
Follow the design steps of the benchmark scenario of the test scheme , First, test the benchmark scenario of this interface .
Problem phenomenon

As shown in the figure above , This phenomenon is becoming more and more obvious .
In the pressure measurement results TPS The average is 25 The average response time reached 993 ms.
The analysis process
In terms of performance analysis logic , For the problem of long response time , The first thing to do is to split the time . Since this system has been deployed SkyWalking, Use it to see where time is mainly spent .

Look at the picture ,Tomcat Of SelfDuration The most. , In other words, time is almost consumed in the service itself .
Global monitoring
First, check the resource level of the application server :

You can see 4C Of CPU Resources have been exhausted .
The container deployed here , Let's take a look at the resource usage of each container :
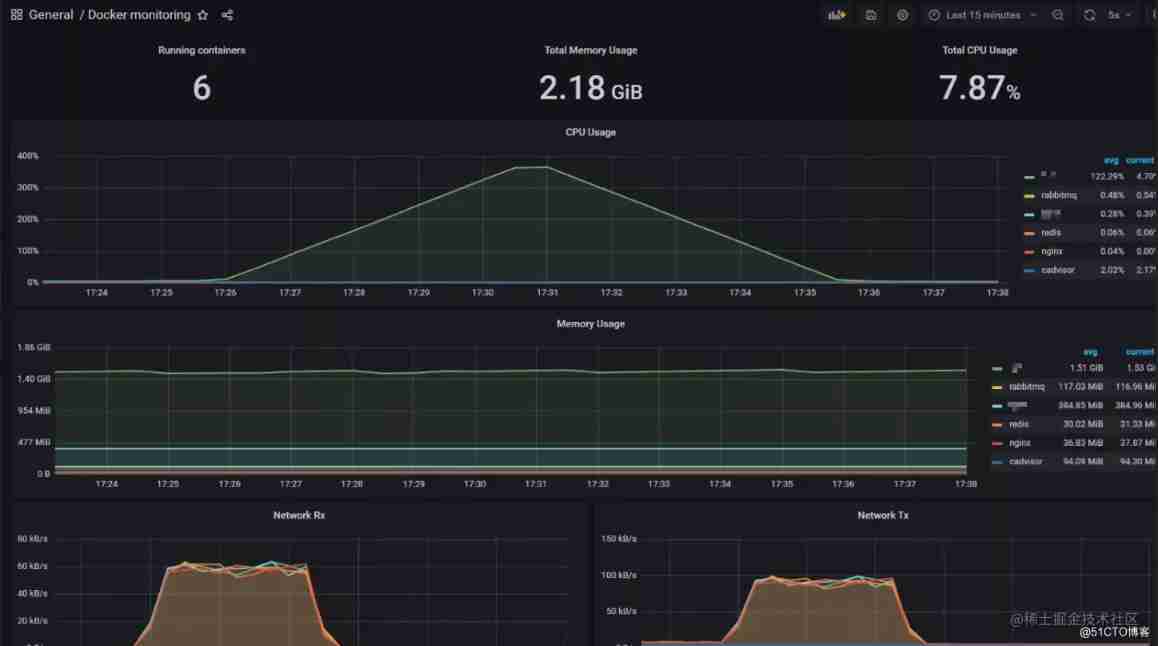
You can see that resources are mainly consumed by the service container .
Service orientation analysis
First, enter the service container to view the resource consumption :

stay SkyWaking You can't see the complete call stack in , Consider connecting directly to the service Java The time consumption of the method in the process . Here we use Arthas Follow up .
Check out the busiest previous N Thread and print stack :
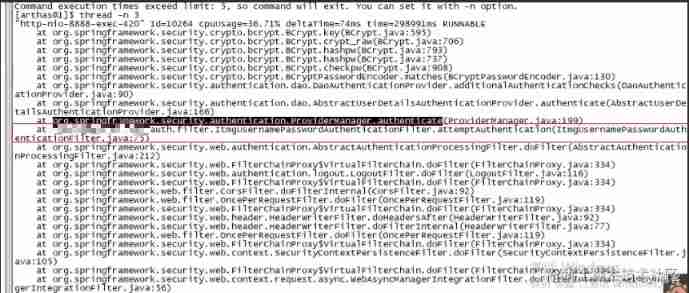
Here is the business code of the program .
therefore trace attemptAuthentication This method .

next trace authenticate This method .

Follow it layer by layer , Finally came here :
Since the crypt_raw The method takes a long time , Then decompile the source code to see what this paragraph is .
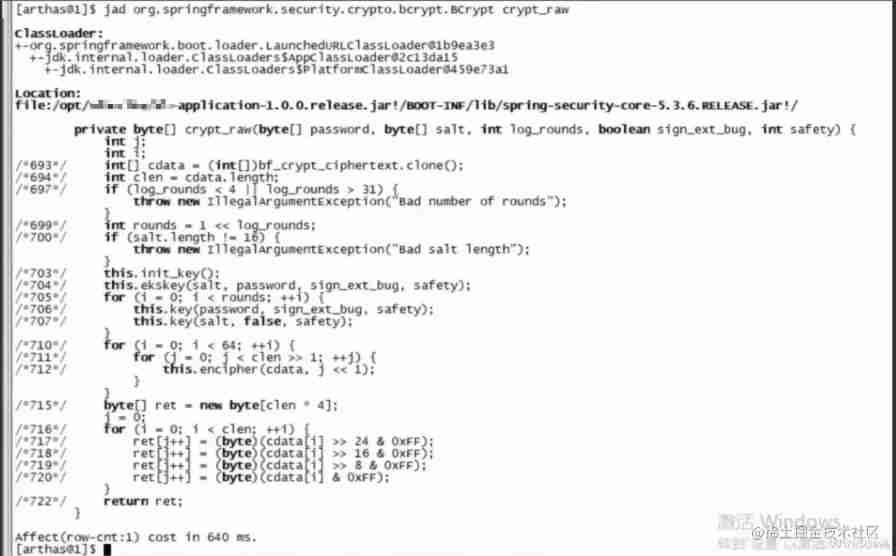
As you can see, here is an encryption algorithm BCrypt, So the conclusion is obvious BCrypt Although the encryption algorithm has high security , But the performance is poor .
demo verification
Use here SpringBoot Realization MD5 Encryption and BCrypt Encrypted instance .

JMeter Concurrent 20 MD5 Encryption result :

JMeter Concurrent 20 BCrypt Encryption result :
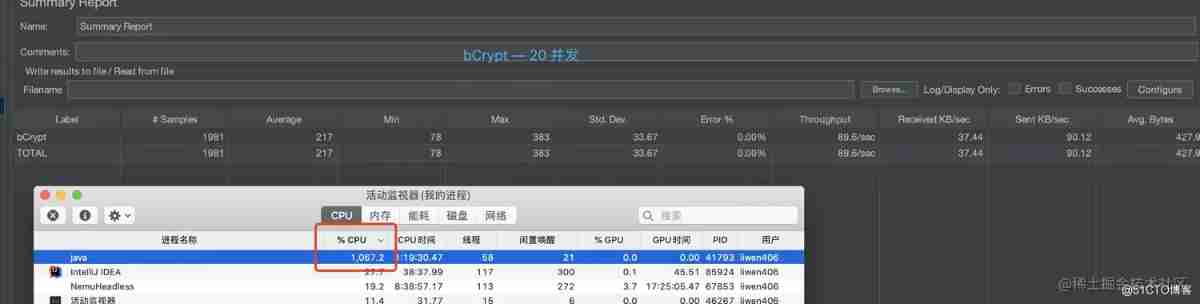
Suggested optimization direction
Here's an explanation ,Bcrypt When encrypting , every time HASH The values are different , So it's very slow !
What exactly is Bcrypt Algorithm , You can refer to this article : www.jianshu.com/p/2b131bfc2…
So that's the analysis , The optimization scheme is actually clear , That is to use faster encryption , Or remove the encryption algorithm .
Click to follow , The first time to learn about Huawei's new cloud technology ~
边栏推荐
- Scanf read in data type symbol table
- 弈柯莱生物冲刺科创板:年营收3.3亿 弘晖基金与淡马锡是股东
- Technology sharing | MySQL parallel DDL
- R language ggplot2 visualization: ggplot2 visualization grouping box diagram, place the legend and title of the visualization image on the top left of the image and align them to the left, in which th
- Wechat has new functions, and the test is started again
- Flutter 集成 amap_flutter_location
- deno debugger
- string. Format without decimal places will generate unexpected rounding - C #
- Leetcode 146. LRU 缓存
- Leetcode (215) -- the kth largest element in the array
猜你喜欢
How to use MOS tube to realize the anti reverse connection circuit of power supply
Sqli labs download, installation and reset of SQL injection test tool one of the solutions to the database error (# 0{main}throw in d:\software\phpstudy_pro\www\sqli labs-...)
ctfshow web255 web 256 web257
ES6 summary
Redis 哨兵机制
A method for detecting outliers of data
Openfeign service interface call
MySQL relearn 1-centos install mysql5.7

Linear algebra 1.1
DM8 command line installation and database creation
随机推荐
Set and modify the page address bar icon favicon ico
What sparks can applet container technology collide with IOT
[go basics] 1 - go go
Example analysis of C # read / write lock
Group programming ladder race - exercise set l1-006 continuity factor
1. Qt入门
Unity-写入Word
Use preg_ Match extracts the string into the array between: & | people PHP
Linear algebra 1.1
Flutter integrated amap_ flutter_ location
ctfshow web255 web 256 web257
【Go基础】2 - Go基本语句
Leetcode 23. Merge K ascending linked lists
How to get bytes containing null terminators from a string- c#
Unity text superscript square representation +text judge whether the text is empty
Convert datetime string to datetime - C in the original time zone
Basic operations of databases and tables ----- view data tables
Developers really review CSDN question and answer function, and there are many improvements~
Question 49: how to quickly determine the impact of IO latency on MySQL performance
[go basics] 2 - go basic sentences