当前位置:网站首页>L1-025 positive integer a+b (15 points)
L1-025 positive integer a+b (15 points)
2022-07-04 07:29:00 【Inter personal liabilities^】
L1-025 Positive integer A+B (15 branch )
The goal of the question is very simple , It's two positive integers A and B And , among A and B It's all in the range [1,1000]. A little bit of a hassle , The input is not guaranteed to be two positive integers .
Input format :
Type in on a line to give A and B, They are separated by spaces . The problem is A and B It doesn't have to be a positive integer , Sometimes it can be out of range numbers 、 negative 、 A real number with a decimal point 、 It's even a mess of code .
Be careful : Let's put... In the input 1 A space is taken as A and B Separation of . Make sure that there is at least one space for the question , also B It's not an empty string .
Output format :
If the input is really two positive integers , According to the format A + B = and Output . If an input is not satisfactory , Output at corresponding position ?, Obviously at this time and also ?.
sample input 1:
123 456
sample output 1:
123 + 456 = 579
sample input 2:
22. 18
sample output 2:
? + 18 = ?
sample input 3:
-100 blabla bla...33
sample output 3:
? + ? = ?
test 3: Similar to the third example , There may be more than two data entered , When the input data exceeds two data , You should directly output the results that are all question marks
test 5: The upper limit of the number is 1000, There are requirements for the topic , But when typing , I didn't input as required, so I need to judge
test 6: The lower limit of the number is 1, And testing 5 identical
AC Code
#include<iostream>
#include<algorithm>
#include<cstring>
#include<cmath>
#include<vector>
#include<stack>
#include<queue>
#include<sstream>
using namespace std;
typedef long long ll;
const int N=100010;
int main()
{
string a;
getline(cin, a);
bool flaga = false, flagb = false;
int aa = 0, bb = 0;
int flag = 0;
for(int i = 0; i < a.size(); i ++ )
{
if(a[i] == ' ') flag = i;
if(flag > 0) break;
}
for(int i = 0; i < flag; i ++ )
{
aa = aa * 10 + (a[i] - '0');
if(a[i] < '0' || a[i] > '9')
{
flaga = true;
break;
}
}
int flag1 = 0;
for(int i = flag + 1; i < a.size(); i ++ )
{
bb = bb * 10 + (a[i] - '0');
if(a[i] < '0' || a[i] > '9')
{
flagb = true;
break;
}
}
if(aa > 1000 || aa < 1) flaga = true;
if(bb > 1000 || bb < 1) flagb = true;
if(flaga) cout << '?' << ' ';
else cout << aa << ' ';
cout << '+' << ' ';
if(flagb) cout << '?' << ' ';
else cout << bb << ' ';
cout << '=' << ' ';
if(flaga || flagb) cout << '?';
else cout << aa + bb;
return 0;
}
边栏推荐
- 大厂技术专家:架构设计中常用的思维模型
- 2022-021ARTS:下半年开始
- What is the use of cloud redis? How to use cloud redis?
- Technical experts from large factories: common thinking models in architecture design
- User login function: simple but difficult
- Solution of running crash caused by node error
- BibTex中参考文献种类
- Recursive Fusion and Deformable Spatiotemporal Attention for Video Compression Artifact Reduction
- A new understanding of how to encrypt industrial computers: host reinforcement application
- Comparison between applet framework and platform compilation
猜你喜欢
How to send mail with Jianmu Ci
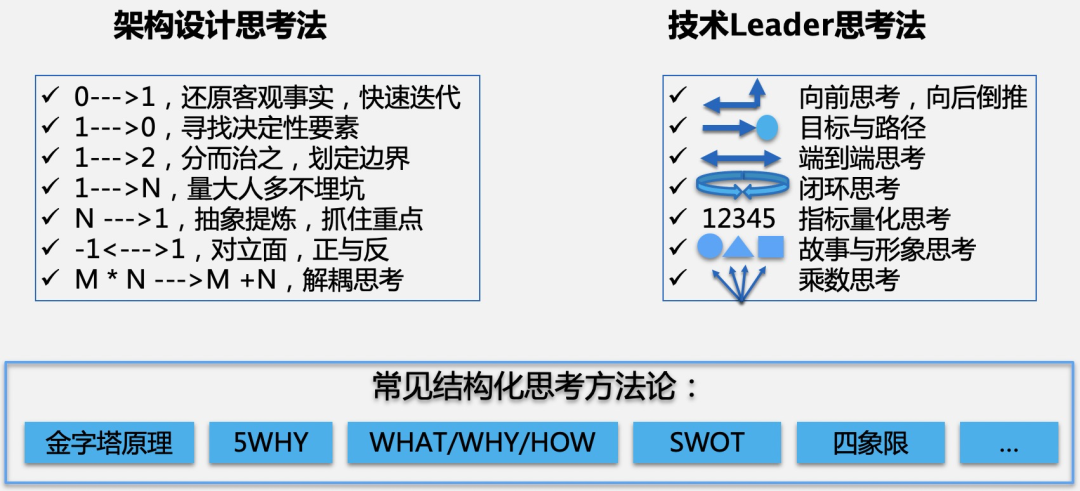
Technical experts from large factories: common thinking models in architecture design

A new understanding of how to encrypt industrial computers: host reinforcement application
Pangu open source: multi support and promotion, the wave of chip industry
Introduction to sap commerce cloud B2B organization function

Book list | as the technical support Party of the Winter Olympics, Alibaba cloud's technology is written in these books!

Handwritten easy version flexible JS and source code analysis

A real penetration test
Xcode 14之大变化详细介绍

Master-slave replication principle of MySQL database
随机推荐
[Flink] temporal semantics and watermark
Zabbix agent主动模式的实现
BasicVSR++: Improving Video Super-Resolutionwith Enhanced Propagation and Alignment
Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
电子协会 C语言 1级 35 、银行利息
Unity opens the explorer from the inspector interface, selects and records the file path
What is the use of cloud redis? How to use cloud redis?
神经网络入门(下)
BUUCTF(3)
MySQL中的文本處理函數整理,收藏速查
电脑通过Putty远程连接树莓派
Label management of kubernetes cluster
Types of references in BibTex
One of the general document service practice series
Node connection MySQL access denied for user 'root' @ 'localhost' (using password: yes
Rapidjson reading and writing JSON files
Zhanrui tankbang | jointly build, cooperate and win-win zhanrui core ecology
Directory of tornado
Enter the year, month, and determine the number of days
Chapter 1 programming problems