当前位置:网站首页>Highly paid programmers & interview questions: how does redis of series 119 realize distributed locks?
Highly paid programmers & interview questions: how does redis of series 119 realize distributed locks?
2022-07-04 06:43:00 【One brother sun】
One . Interview questions and Analysis
1. Interview questions of the day
Redis How to implement distributed locks ?
2. Problem analysis
Yige Today, I will continue to give you an analysis Redis Relevant interview questions . This article , Yige Will give you a specific analysis Redis Practical application of , Such as the use of Redis How to implement distributed locks . Distributed locking is an important means to solve the problem of concurrent access to shared resources in distributed projects , among Redis It is a common implementation scheme for implementing distributed locks , So today's content is very important , You should read carefully .
Two . Redis Implement distributed locks
1. Problem description
In fact, the content about locks , If you have carefully read the previous articles of Yige , It should not be very strange , We know Java There are all kinds of locks in the , such as synchronize、lock etc. , The following is the previous interview question article about lock :
边栏推荐
- Displaying currency in Indian numbering format
- [Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
- 【问题记录】03 连接MySQL数据库提示:1040 Too many connections
- Realize IIC data / instruction interaction with micro batg135
- Mysql 45讲学习笔记(十一)字符串字段怎么加索引
- Analysis of tars source code 1
- [backpack DP] backpack problem
- Mysql 45讲学习笔记(六)全局锁
- Google Chrome Portable Google Chrome browser portable version official website download method
- Sleep quality today 78 points
猜你喜欢
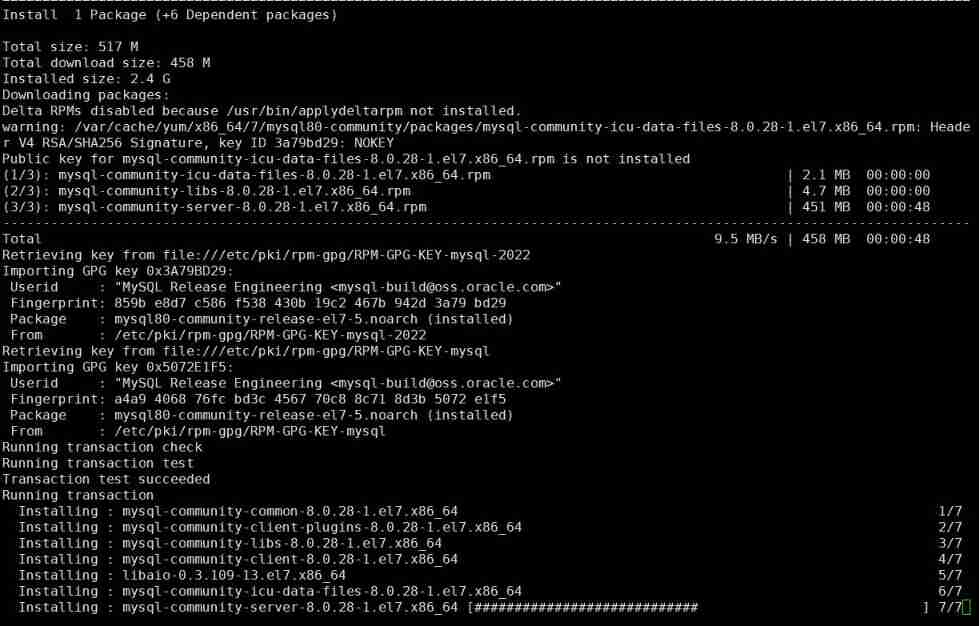
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0
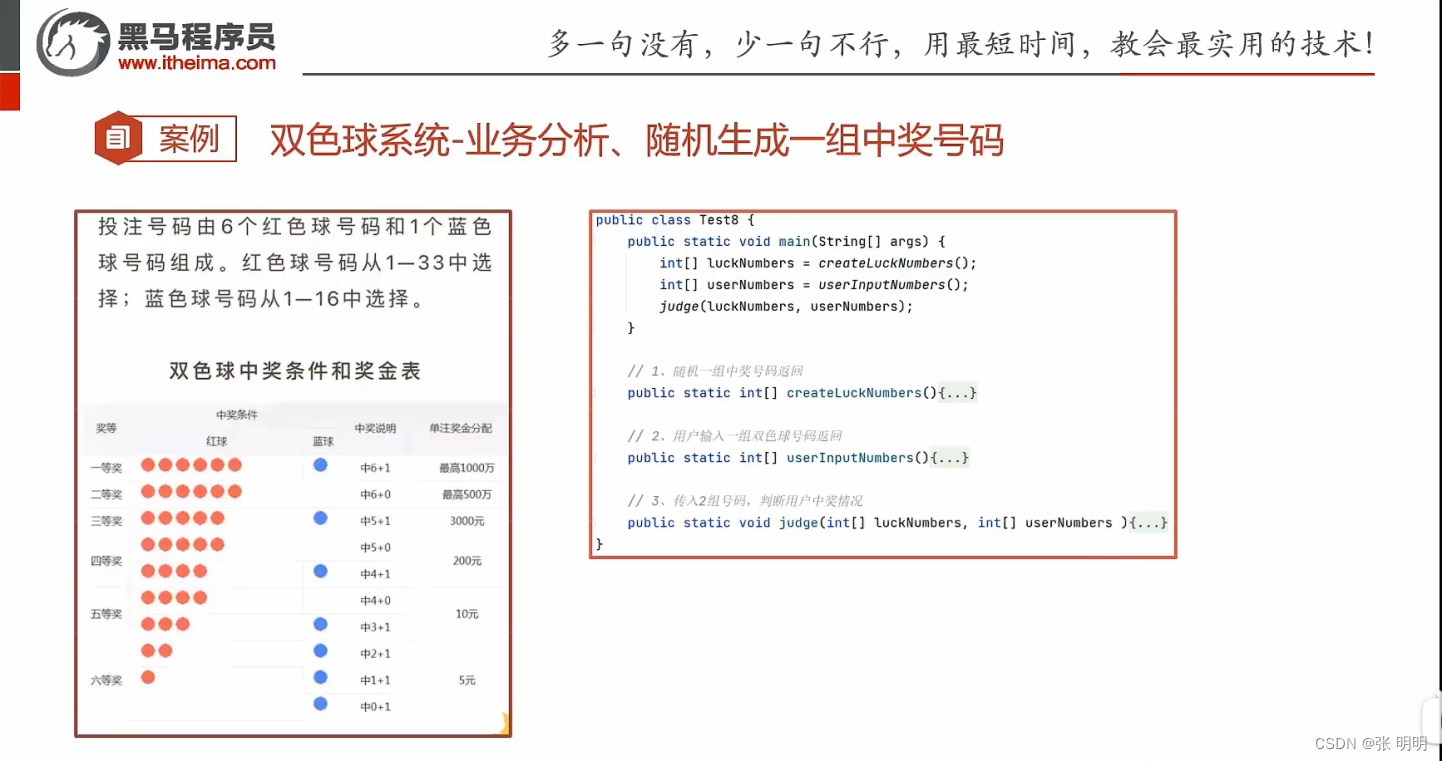
双色球案例

Which water in the environment needs water quality monitoring
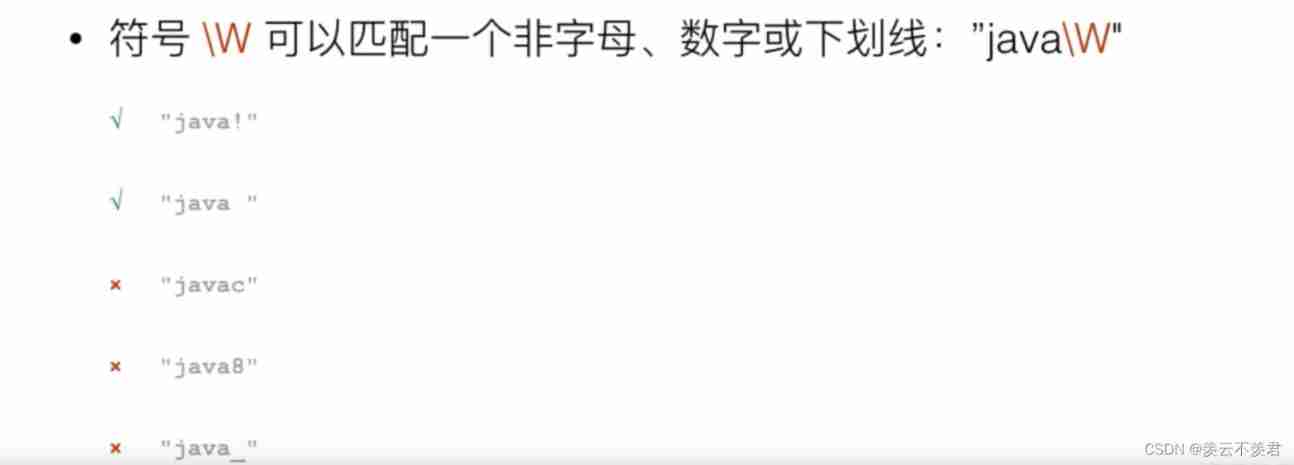
regular expression
P26-P34 third_ template
关于IDEA如何设置快捷键集
Can the out of sequence message complete TCP three handshakes
SQL injection SQL lab 11~22
Inputstream/outputstream (input and output of file)
R statistical mapping - random forest classification analysis and species abundance difference test combination diagram
随机推荐
在已經知道錶格列勾選一個顯示一列
Bicolor case
SQL injection SQL lab 11~22
Google Chrome Portable Google Chrome browser portable version official website download method
MySQL 45 learning notes (XI) how to index string fields
Considerations for testing a website
Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
tars源码分析之8
双色球案例
Tar source code analysis Part 3
同一个job有两个source就报其中一个数据库找不到,有大佬回答下吗
【FPGA教程案例7】基于verilog的计数器设计与实现
C语言中的排序,实现从小到大的数字排序法
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
在已经知道表格列勾选一个显示一列
Common JS tool Libraries
Arcpy 利用updatelayer函数改变图层的符号系统
Appium基础 — APPium安装(二)
8. Factory method
Tar source code analysis 9