当前位置:网站首页>MySQL 45 learning notes (XI) how to index string fields
MySQL 45 learning notes (XI) how to index string fields
2022-07-04 06:37:00 【Tom Kong】
One . Prefix index
- MySQL Support prefix index , Sure Define part of the string Do the index
- Create an index statement Do not specify prefix length , that The index will contain the entire string
Two . How long prefix to use
Use prefix index , Define the length , Sure Save space , Don't add too many additional queries cost .
- Focus on the differentiation when building the index , The higher the discrimination, the better
- The more distinguishable , signify The fewer duplicate key values
- We can How many different values are there in the statistical index To determine how long prefix to use
Example : Count the differentiation of different fields with different lengths
select
count(distinct left(email,4))as L4,
count(distinct left(email,5))as L5,
count(distinct left(email,6))as L6,
count(distinct left(email,7))as L7,
from SUser;3、 ... and . The influence of prefix index on overlay index
- If it is a full string , If the index coverage is supported, the table will not be returned .
- If it's just a part of a string , The system still depends on id Look back at the index , Because the system is not sure whether the prefix index definition truncates the complete information .
The longer the index , The more disk space it takes up , The smaller the index value that can be placed on the same data page , The less efficient the search .
Four . ID card scenario ( The front of the field should be highly differentiated from the back )
- Use flashback storage , If you turn them upside down when storing ID number
- Use hash Field
Use Flashback storage and Use hash Field The similarities and differences between the two methods
The same thing
- Range queries are not supported
Difference
- In terms of the extra space occupied , Flashbacks are stored in the primary key index , No additional storage is consumed
- hash Field method needs to add a field
CPU Consumption :
- The flashback method needs an additional call reverse function
- hash Field requires an additional call to the hash function ,reverse Function extra consumption CPU Resources will be smaller
The query efficiency :
- hash The query performance of field mode is relatively stable . because crc32 The calculated values have the probability of conflict , But the probability is very small
- After all, the reverse storage method is still the prefix index method , In other words, it will increase the number of scanning lines
边栏推荐
- Mysql 45讲学习笔记(十二)MySQL会“抖”一下
- 颈椎、脚气
- The solution of win11 taskbar right click without Task Manager - add win11 taskbar right click function
- Tar source code analysis 9
- How to choose the middle-aged crisis of the testing post? Stick to it or find another way out? See below
- [Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
- 微信小程序使用rich-text中图片宽度超出问题
- selenium IDE插件下载安装使用教程
- 【问题记录】03 连接MySQL数据库提示:1040 Too many connections
- Learn about the Internet of things protocol WiFi ZigBee Bluetooth, etc. --- WiFi and WiFi protocols start from WiFi. What do we need to know about WiFi protocol itself?
猜你喜欢
Bicolor case
雲原生——上雲必讀之SSH篇(常用於遠程登錄雲服務器)
regular expression
QT qtablewidget table column top requirements ideas and codes
How to use multithreading to export excel under massive data? Source code attached!
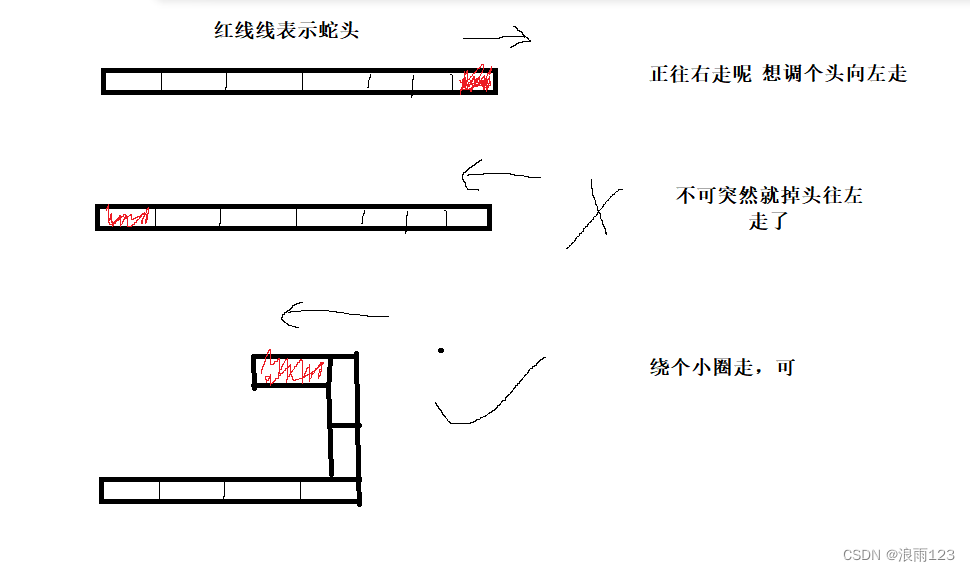
C réaliser des jeux de serpents gourmands
Mysql 45讲学习笔记(七)行锁

ORICO ORICO outdoor power experience, lightweight and portable, the most convenient office charging station
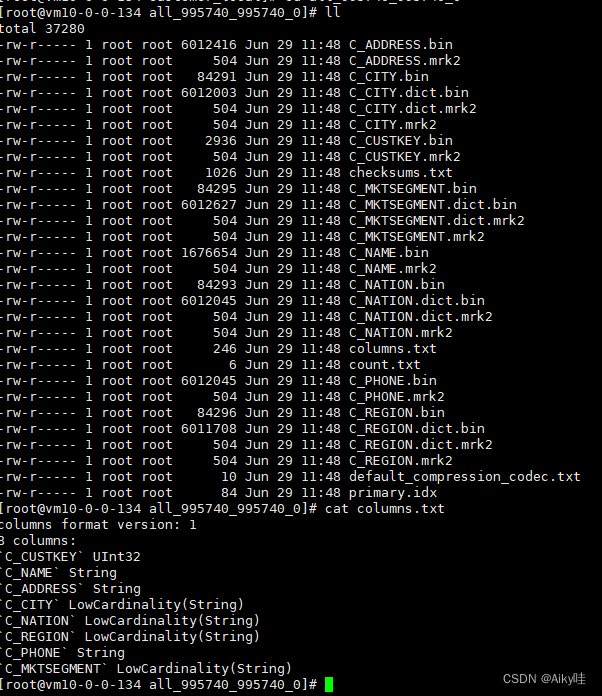
Reading notes of Clickhouse principle analysis and Application Practice (4)
How to avoid JVM memory leakage?
随机推荐
Explain in one sentence what social proof is
Variables d'environnement personnalisées uniapp
tars源码分析之2
Tar source code analysis 9
Mysql 45讲学习笔记(十一)字符串字段怎么加索引
Analysis of tars source code 1
How to use multithreading to export excel under massive data? Source code attached!
tars源码分析之7
Tar source code analysis 6
内卷怎么破?
如何实现视频平台会员多账号登录
Tar source code analysis Part 3
tcp socket 的 recv 如何接收指定长度消息?
Can the out of sequence message complete TCP three handshakes
tars源码分析之4
Dimension and format of data
8. Factory method
C language exercises (recursion)
Tree DP
Arcpy uses the updatelayer function to change the symbol system of the layer