当前位置:网站首页>tars源码分析之4
tars源码分析之4
2022-07-04 06:33:00 【涛歌依旧】
基础buffer的实现,也很简单,大致看看:
#include "util/tc_buffer.h"
#include <iostream>
#include <algorithm>
#include <limits>
#include <cassert>
inline static std::size_t RoundUp2Power(std::size_t size)
{
if (size == 0)
return 0;
std::size_t roundUp = 1;
while (roundUp < size)
roundUp *= 2;
return roundUp;
}
namespace tars
{
const std::size_t TC_Buffer::kMaxBufferSize = std::numeric_limits<std::size_t>::max() / 2;
const std::size_t TC_Buffer::kDefaultSize = 128;
std::size_t TC_Buffer::PushData(const void* data, std::size_t size)
{
if (!data || size == 0)
return 0;
if (ReadableSize() + size >= kMaxBufferSize)
return 0; // overflow
AssureSpace(size);
::memcpy(&_buffer[_writePos], data, size);
Produce(size);
return size;
}
std::size_t TC_Buffer::PopData(void* buf, std::size_t size)
{
const std::size_t dataSize = ReadableSize();
if (!buf ||
size == 0 ||
dataSize == 0)
return 0;
if (size > dataSize)
size = dataSize; // truncate
::memcpy(buf, &_buffer[_readPos], size);
Consume(size);
return size;
}
void TC_Buffer::PeekData(void*& buf, std::size_t& size)
{
buf = ReadAddr();
size = ReadableSize();
}
void TC_Buffer::Consume(std::size_t bytes)
{
assert (_readPos + bytes <= _writePos);
_readPos += bytes;
if (IsEmpty())
Clear();
}
void TC_Buffer::AssureSpace(std::size_t needsize)
{
if (WritableSize() >= needsize)
return;
const size_t dataSize = ReadableSize();
const size_t oldCap = _capacity;
while (WritableSize() + _readPos < needsize)
{
if (_capacity < kDefaultSize)
{
_capacity = kDefaultSize;
}
else if (_capacity <= kMaxBufferSize)
{
const size_t newCapcity = RoundUp2Power(_capacity);
if (_capacity < newCapcity)
_capacity = newCapcity;
else
_capacity = 2 * newCapcity;
}
else
{
assert(false);
}
}
if (oldCap < _capacity)
{
char* tmp(new char[_capacity]);
if (dataSize != 0)
memcpy(&tmp[0], &_buffer[_readPos], dataSize);
ResetBuffer(tmp);
}
else
{
assert (_readPos > 0);
::memmove(&_buffer[0], &_buffer[_readPos], dataSize);
}
_readPos = 0;
_writePos = dataSize;
assert (needsize <= WritableSize());
}
void TC_Buffer::Shrink()
{
if (IsEmpty())
{
Clear();
_capacity = 0;
ResetBuffer();
return;
}
if (_capacity <= kDefaultSize)
return;
std::size_t oldCap = _capacity;
std::size_t dataSize = ReadableSize();
if (dataSize * 100 > oldCap * _highWaterPercent)
return;
std::size_t newCap = RoundUp2Power(dataSize);
char* tmp(new char[newCap]);
memcpy(&tmp[0], &_buffer[_readPos], dataSize);
ResetBuffer(tmp);
_capacity = newCap;
_readPos = 0;
_writePos = dataSize;
}
void TC_Buffer::Clear()
{
_readPos = _writePos = 0;
}
void TC_Buffer::Swap(TC_Buffer& buf)
{
std::swap(_readPos, buf._readPos);
std::swap(_writePos, buf._writePos);
std::swap(_capacity, buf._capacity);
std::swap(_buffer, buf._buffer);
}
void TC_Buffer::ResetBuffer(void* ptr)
{
delete[] _buffer;
_buffer = reinterpret_cast<char*>(ptr);
}
void TC_Buffer::SetHighWaterPercent(size_t percents)
{
if (percents < 10 || percents >= 100)
return;
_highWaterPercent = percents;
}
} // end namespace tars边栏推荐
- [MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)
- 2022.7.3-----leetcode. five hundred and fifty-six
- 1、 Relevant theories and tools of network security penetration testing
- Detectron: train your own data set -- convert your own data format to coco format
- R statistical mapping - random forest classification analysis and species abundance difference test combination diagram
- Understanding of cross domain and how to solve cross domain problems
- C language - Blue Bridge Cup - Snake filling
- Nexus 6p downgraded from 8.0 to 6.0+root
- 2022 Xinjiang's latest eight members (Safety Officer) simulated examination questions and answers
- SQL join, left join, right join usage
猜你喜欢

Which water in the environment needs water quality monitoring
Sword finger offer II 038 Daily temperature

Common usage of time library
AWT common components, FileDialog file selection box
ABAP:OOALV实现增删改查功能
Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)
Learn about the Internet of things protocol WiFi ZigBee Bluetooth, etc. --- WiFi and WiFi protocols start from WiFi. What do we need to know about WiFi protocol itself?

How does apscheduler set tasks not to be concurrent (that is, execute the next task after the first one)?
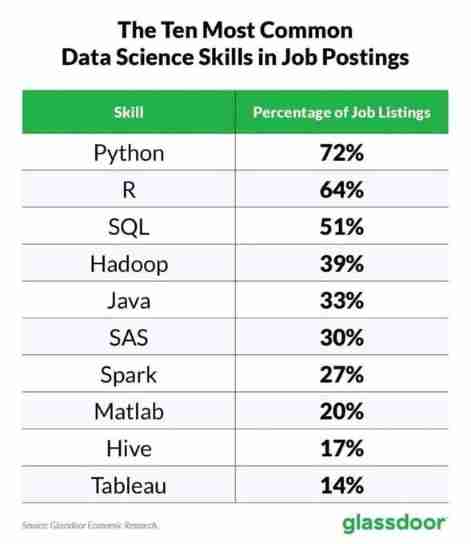
List of top ten professional skills required for data science work
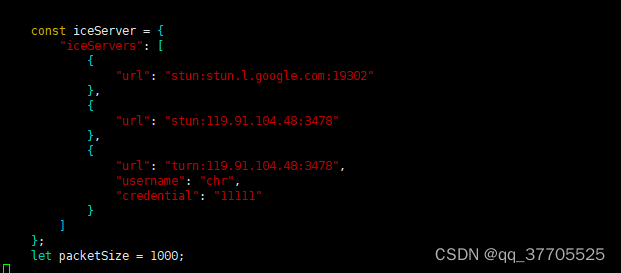
Webrtc quickly set up video call and video conference
随机推荐
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
17-18. Dependency scope and life cycle plug-ins
JS execution mechanism
C實現貪吃蛇小遊戲
lightroom 导入图片灰色/黑色矩形 多显示器
regular expression
740. Delete and get points
Mysql 45讲学习笔记(十四)count(*)
How to choose the middle-aged crisis of the testing post? Stick to it or find another way out? See below
Which water in the environment needs water quality monitoring
2022.7.2-----leetcode. eight hundred and seventy-one
24 magicaccessorimpl can access the debugging of all methods
Learning multi-level structural information for small organ segmentation
Stc8h development (XII): I2C drive AT24C08, at24c32 series EEPROM storage
Variables d'environnement personnalisées uniapp
What is tweeman's law?
C语言中的排序,实现从小到大的数字排序法
C语言中的函数(详解)
Download kicad on Alibaba cloud image station
How to implement cross domain requests