当前位置:网站首页>Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)
Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)
2022-07-04 06:13:00 【Shiba ya】
“ The article is written in an easy to understand way , It introduces SSH Related basic concepts , Help readers quickly understand SSH.”
Disadvantages of traditional network service program
- Traditional network service program (ftp/pop/telnet) Use on the network Plaintext delivery password and data , Hackers are easy to intercept .
- The security verification method of traditional network service program is vulnerable to A middleman (man-in-the-middle) Way of attack .
- “ A middleman ” Way of attack
- “ A middleman ” Impersonate the real server to receive the data you sent to the server , And then pass the data to the real server .
SSH brief introduction
- SSH(Secure Shell): Secure Shell Protocol ( Application layer protocol )
- A protocol that provides security for network services such as remote login sessions , It can effectively prevent security problems in the process of remote management .
- SSH Adopt connection oriented TCP Protocol transfer , The port number is 22.
SSH Application
- Use SSH, All data transmitted can be encrypted 、 Compress ( Faster transmission ), Put an end to middleman attacks , It can also prevent DNS Deception and IP cheating .
- SSH It can replace Telnet, It can also be FTP、PoP、PPP Provide a safe tunnel .
- Log in to ECS remotely for data transmission for security verification .
SSH How to implement
- OpenSSH
- PuTTY
SSH edition
- SSH By Client and server software composition Of , There are two incompatible versions of :1.x and 2.x.
- SSH 2.x The client program of cannot connect to SSH 1.x Service procedures .
- OpenSSH 2.x Support at the same time SSH 1.x and 2.x.
SSH encryption
- SSH The data transfer —— Use symmetric keys to encrypt
- SSH Create connection + Authentication handshake stage —— Use asymmetric encryption
- Symmetric encryption , The sender and receiver use a shared key for encryption 、 Decrypt .
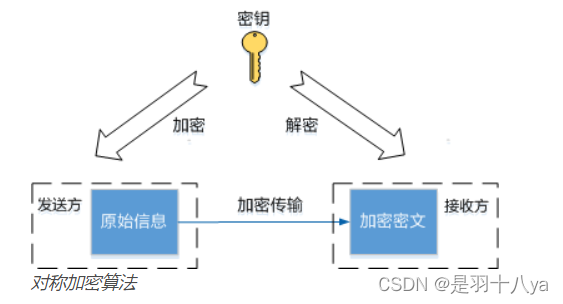
- Asymmetric encryption , Send a message Encryption uses Public key , Receiving information Decryption use Private key .
- The public key can be sent to anyone else who requests communication , The private key is kept by the generated party ,.
- The mathematical characteristics between public key and private key ensure that the information encrypted by public key can only be decrypted by private key , The information encrypted by the private key cannot be decrypted by the public key .
- The private key of asymmetric encryption does not need to be exposed in the network , High security , But the speed of encryption and decryption is much slower than that of symmetric key .

SSH verification —— From the client side
- Password verification
- Log in to the remote host with an account and password . All transmitted data is encrypted , But there is no guarantee that the server you are connecting to is the server you want to connect to . There may be other servers posing as real servers .
- Public private key verification
- Create a pair of keys for yourself , And put the public key on the server to be accessed .
- When you want to connect to SSH On the server , The client software will make a request to the server , Request security verification with your own key .
- After the server receives the request , First look for your public key in your home directory on this server , Then compare it with the public key you sent . If the two keys are the same , The server is encrypted with a public key “ inquiry ” And send it to the client software .
- Client software received “ inquiry ” Then you can decrypt it with your private key and send it to the server .
SSH Tunnel
SSH Tunnel (SSH Port forwarding ): Communication technology that allows users to connect a specific port between a local host and a remote host .
SSH Port forwarding redirects network traffic to a specific port /IP Address , So that the application on the local host can directly access the remote host .
The target may be located remotely SSH Server , Or the server may be configured to forward to another remote host , Enhance security at the expense of transmission efficiency .
SSH The tunnel is IT Powerful tools for administrators and malicious actors , Because they can bypass the enterprise firewall transmission without being discovered . therefore , There are some tools that can be used to prevent unauthorized use through the enterprise firewall SSH Tunnel .
Reference material
- https://baike.baidu.com/item/SSH/10407
- https://info.support.huawei.com/info-finder/encyclopedia/zh/SSH.html
- https://zhuanlan.zhihu.com/p/46235721
- https://www.techtarget.com/searchsecurity/definition/Secure-Shell
“ I want to ride the wind and waves 、 All over the yellow sand sea , Just for no regrets , Don't be brave to .”
——Created By It's feather 18 ya
边栏推荐
- JS arguments parameter usage and explanation
- A little understanding of GSLB (global server load balance) technology
- Tsinghua University product: penalty gradient norm improves generalization of deep learning model
- 如何展开Collapse 的所有折叠面板
- gslb(global server load balance)技术的一点理解
- C语言中的函数(详解)
- JSON Web Token----JWT和传统session登录认证对比
- Review | categories and mechanisms of action of covid-19 neutralizing antibodies and small molecule drugs
- How to expand all collapse panels
- Invalid revision: 3.18.1-g262b901-dirty
猜你喜欢
Gridview出现滚动条,组件冲突,如何解决
C realize Snake games
Experience weekly report no. 102 (July 4, 2022)
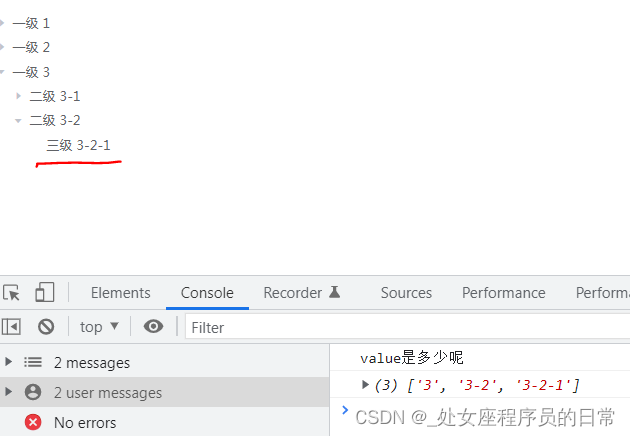
如何获取el-tree中所有节点的父节点
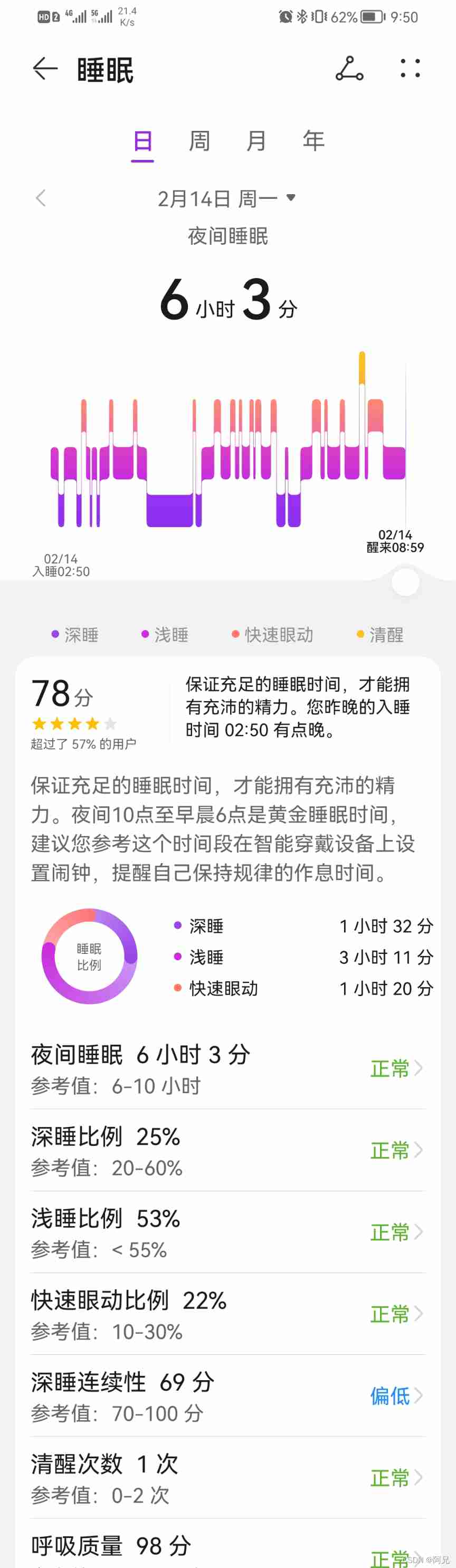
Sleep quality today 78 points
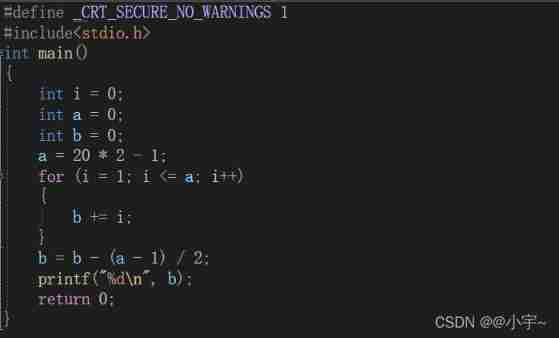
C language - Blue Bridge Cup - Snake filling
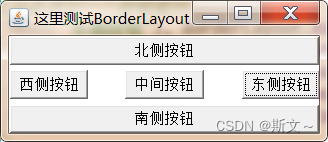
LayoutManager布局管理器:FlowLayout、BorderLayout、GridLayout、GridBagLayout、CardLayout、BoxLayout
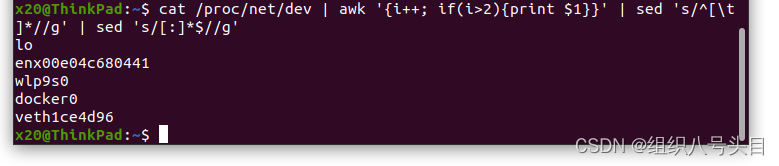
实用的小工具指令
QT qtablewidget table column top requirements ideas and codes
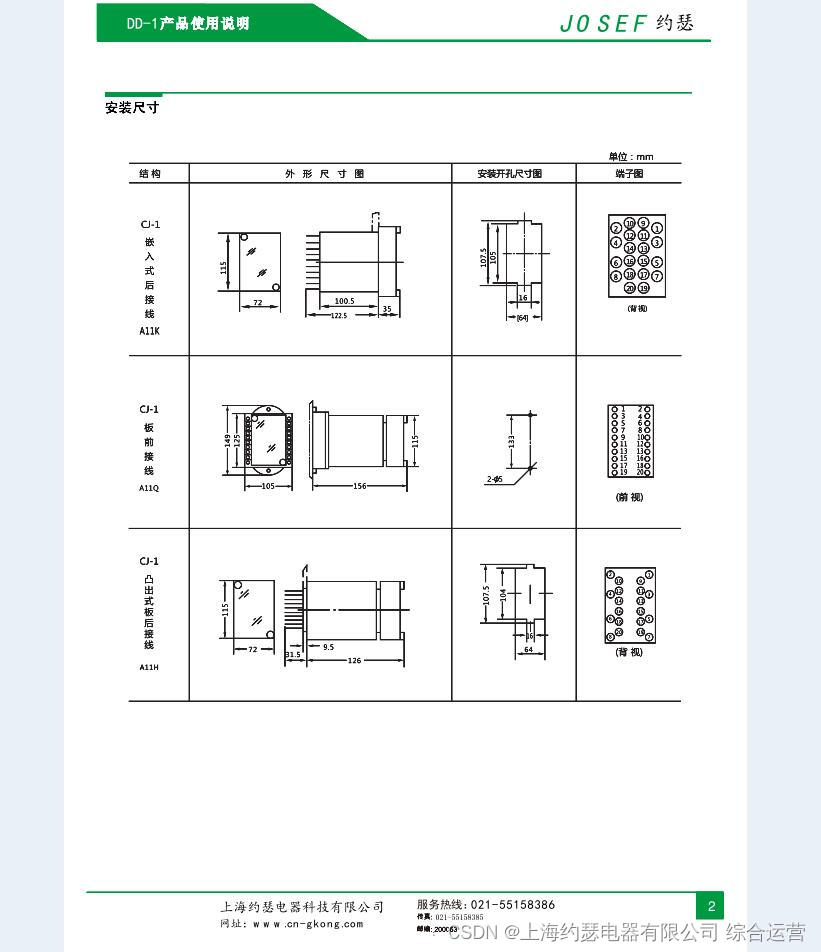
接地继电器DD-1/60
随机推荐
Luogu deep foundation part 1 Introduction to language Chapter 5 array and data batch storage
Recommended system 1 --- framework
Abap:ooalv realizes the function of adding, deleting, modifying and checking
AWT介绍
QT QTableWidget 表格列置顶需求的思路和代码
ES6 modularization
How to realize multi account login of video platform members
buuctf-pwn write-ups (8)
Grounding relay dd-1/60
509. Fibonacci number, all paths of climbing stairs, minimum cost of climbing stairs
注释与注解
Sword finger offer II 038 Daily temperature
Install pytoch geometric
STC8H开发(十二): I2C驱动AT24C08,AT24C32系列EEPROM存储
Average two numbers
[microservice] Nacos cluster building and loading file configuration
left_ and_ right_ Net normal version
Experience weekly report no. 102 (July 4, 2022)
Configure cross compilation tool chain and environment variables
Uninstall Google drive hard drive - you must exit the program to uninstall