边栏推荐
- 746. Climb stairs with minimum cost
- 《国民经济行业分类GB/T 4754—2017》官网下载地址
- Is the insurance annuity product worth buying? Is there a hole?
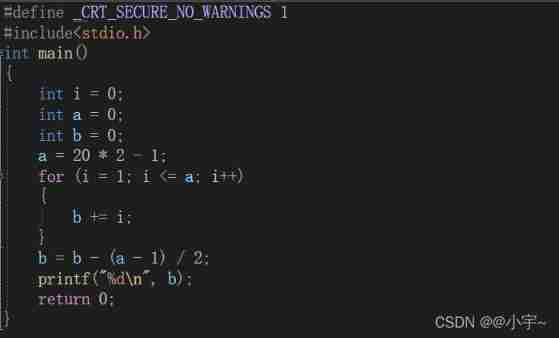
- C language - Blue Bridge Cup - Snake filling
- Common usage of time library
- Fundamentals of SQL database operation
- Selection (022) - what is the output of the following code?
- Cervical vertebra, beriberi
- 校园网络问题
- R statistical mapping - random forest classification analysis and species abundance difference test combination diagram
猜你喜欢
![[number theory] fast power (Euler power)](/img/1e/5d032c8f2e43f553b4543d28ea2a2d.jpg)
[number theory] fast power (Euler power)
云原生——上云必读之SSH篇(常用于远程登录云服务器)
C language - Blue Bridge Cup - Snake filling
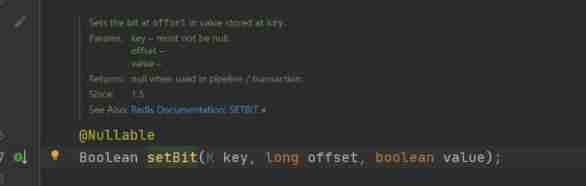
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
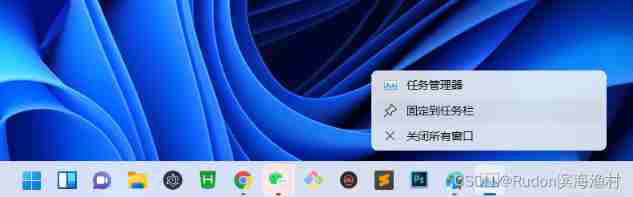
The solution of win11 taskbar right click without Task Manager - add win11 taskbar right click function
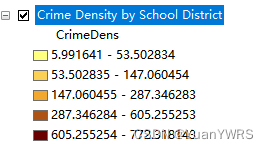
Arcpy 利用updatelayer函数改变图层的符号系统

Cervical vertebra, beriberi
![[Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)](/img/7e/02bb01480257cd56537914a7247733.jpg)
[Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
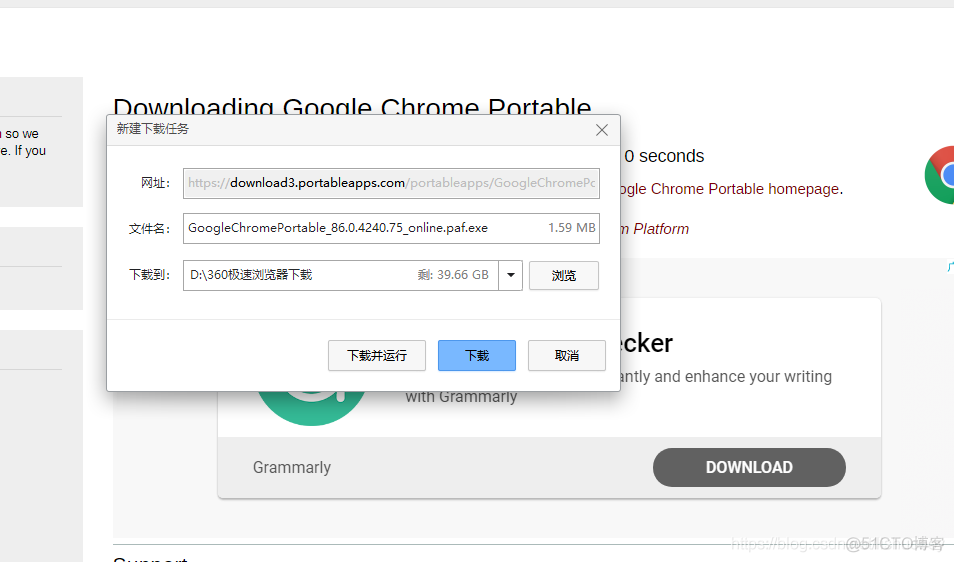
Google Chrome Portable Google Chrome browser portable version official website download method
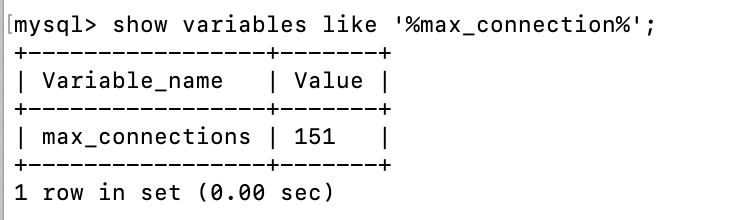
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
随机推荐
Another company raised the price of SAIC Roewe new energy products from March 1
Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
[March 3, 2019] MAC starts redis
雲原生——上雲必讀之SSH篇(常用於遠程登錄雲服務器)
tars源码分析之6
What is Gibson's law?
C language - Blue Bridge Cup - Snake filling
leetcode 310. Minimum Height Trees
1、 Relevant theories and tools of network security penetration testing
tars源码分析之1
thread priority
Tar source code analysis Part 2
Data analysis notes 09
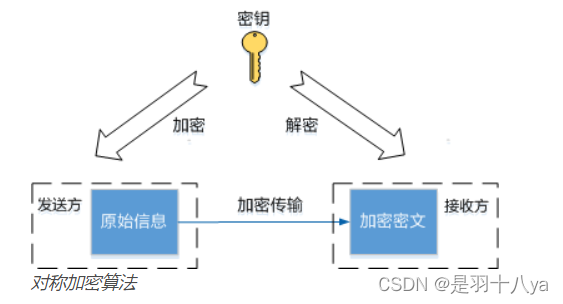
C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
请问旧版的的常用SQL怎么迁移到新版本里来?
P26-P34 third_ template
微信小程序使用rich-text中图片宽度超出问题
leetcode825. 适龄的朋友
【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
Analysis of tars source code 5