当前位置:网站首页>tars源码分析之2
tars源码分析之2
2022-07-04 06:33:00 【涛歌依旧】
bitmap就是位图,在处理大数据时必不可少,来看下实现:
#include "util/tc_bitmap.h"
#include "util/tc_common.h"
#include <cassert>
#include <string.h>
#include <iostream>
namespace tars
{
const int TC_BitMap::BitMap::_magic_bits[8]={0x80,0x40,0x20,0x10,0x8,0x4,0x2,0x1};
size_t TC_BitMap::BitMap::calcMemSize(size_t iElementCount)
{
assert(iElementCount > 0);
iElementCount--;
size_t iMemSize = iElementCount/8+1;
iMemSize += sizeof(tagBitMapHead);
return iMemSize;
}
void TC_BitMap::BitMap::create(void *pAddr, size_t iSize)
{
memset((char*)pAddr, 0, iSize);
_pHead = static_cast<tagBitMapHead*>(pAddr);
_pHead->_cVersion = BM_VERSION;
_pHead->_iMemSize = iSize;
_pData = (unsigned char*)pAddr + sizeof(tagBitMapHead);
}
int TC_BitMap::BitMap::connect(void *pAddr, size_t iSize)
{
_pHead = static_cast<tagBitMapHead*>(pAddr);
if(_pHead->_cVersion != BM_VERSION)
{
return -1;
}
if(iSize != _pHead->_iMemSize)
{
return -2;
}
_pData = (unsigned char*)pAddr + sizeof(tagBitMapHead);
return 0;
}
int TC_BitMap::BitMap::get(size_t i)
{
if(i/8 >= (_pHead->_iMemSize-sizeof(tagBitMapHead)))
{
return -1;
}
unsigned char* p =_pData + i/8;
return _get_bit(*p, i%8)>0?1:0;
}
int TC_BitMap::BitMap::set(size_t i)
{
if(i/8 >= (_pHead->_iMemSize-sizeof(tagBitMapHead)))
{
return -1;
}
unsigned char* p=(unsigned char*)_pData + i/8;
*p = _set_bit(*p, i%8);
return (int)(*p)>0?1:0;
}
int TC_BitMap::BitMap::clear(size_t i)
{
if(i/8 >= (_pHead->_iMemSize-sizeof(tagBitMapHead)))
{
return -1;
}
unsigned char* p = (unsigned char*)_pData + i/8;
*p = _clear_bit(*p, i%8);
return (int)(*p)>0?1:0;
}
int TC_BitMap::BitMap::clear4all()
{
memset(_pData, 0, _pHead->_iMemSize-sizeof(tagBitMapHead));
return 0;
}
int TC_BitMap::BitMap::dump2file(const string &sFile)
{
FILE *fp = fopen(sFile.c_str(), "wb");
if(fp == NULL)
{
return -1;
}
size_t ret = fwrite((void*)_pHead, 1, _pHead->_iMemSize, fp);
fclose(fp);
if(ret == _pHead->_iMemSize)
{
return 0;
}
return -1;
}
int TC_BitMap::BitMap::load5file(const string &sFile)
{
FILE *fp = fopen(sFile.c_str(), "rb");
if(fp == NULL)
{
return -1;
}
fseek(fp, 0L, SEEK_END);
size_t fs = ftell(fp);
if(fs != _pHead->_iMemSize)
{
fclose(fp);
return -2;
}
fseek(fp, 0L, SEEK_SET);
size_t iSize = 1024*1024*10;
size_t iLen = 0;
char *pBuffer = new char[iSize];
while(true)
{
int ret = fread(pBuffer, 1, iSize, fp);
if(ret == 0)
{
break;
}
//检查版本
if(iLen == 0)
{
tagBitMapHead *tmp = (tagBitMapHead*)pBuffer;
if(tmp->_cVersion != BM_VERSION)
{
fclose(fp);
delete[] pBuffer;
return -3;
}
if(tmp->_iMemSize != _pHead->_iMemSize)
{
fclose(fp);
delete[] pBuffer;
return -2;
}
}
memcpy((char*)_pHead + iLen, pBuffer, ret);
iLen += ret;
}
fclose(fp);
delete[] pBuffer;
if(iLen != _pHead->_iMemSize)
{
return -2;
}
return 0;
}
边栏推荐
- Mysql 45讲学习笔记(十四)count(*)
- GoogleChromePortable 谷歌chrome浏览器便携版官网下载方式
- [Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
- What is a spotlight effect?
- R统计绘图-随机森林分类分析及物种丰度差异检验组合图
- 8. Factory method
- Distributed cap theory
- Arcpy uses the updatelayer function to change the symbol system of the layer
- MySQL information_ Schema database
- JSON Web Token----JWT和傳統session登錄認證對比
猜你喜欢
buuctf-pwn write-ups (8)
27-31. Dependency transitivity, principle
AWT introduction
C language - Blue Bridge Cup - Snake filling
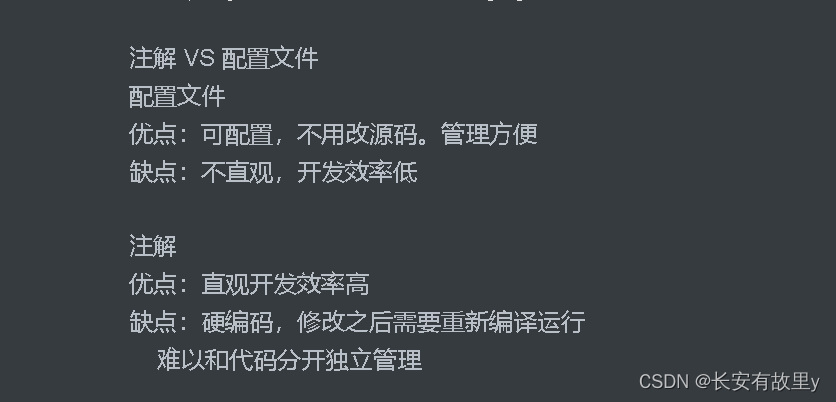
Notes and notes
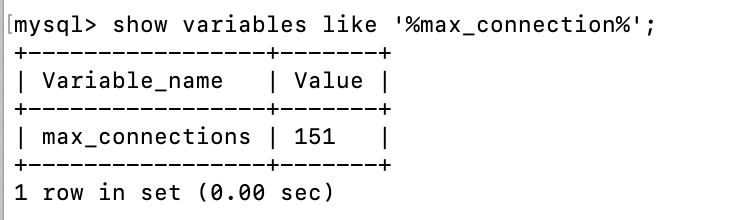
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
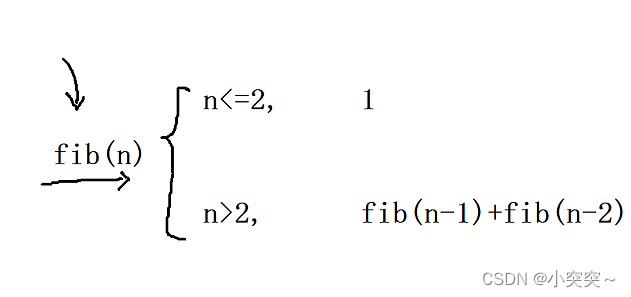
C语言练习题(递归)

2022 where to find enterprise e-mail and which is the security of enterprise e-mail system?
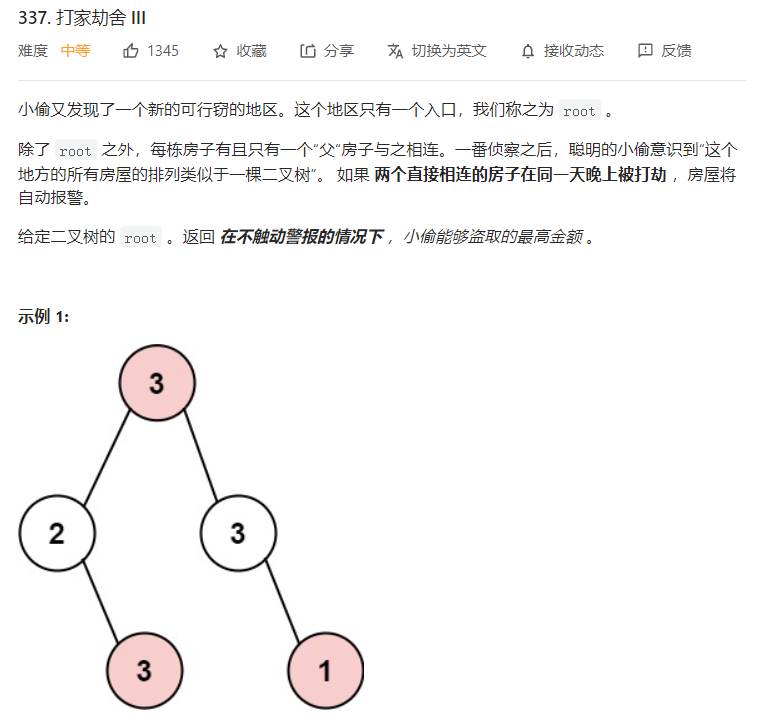
树形dp

【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
随机推荐
Matlab remainder
Tree DP
Detectron: train your own data set -- convert your own data format to coco format
Explain in one sentence what social proof is
Considerations for testing a website
Notes and notes
Detailed explanation of common APIs for component and container containers: frame, panel, scrollpane
Which water in the environment needs water quality monitoring
Fundamentals of SQL database operation
Data analysis notes 09
17-18. Dependency scope and life cycle plug-ins
《ClickHouse原理解析与应用实践》读书笔记(4)
Abap:ooalv realizes the function of adding, deleting, modifying and checking
MySQL learning notes 3 - JDBC
27-31. Dependency transitivity, principle
Sword finger offer II 038 Daily temperature
ORICO ORICO outdoor power experience, lightweight and portable, the most convenient office charging station
Mysql 45讲学习笔记(十)force index
Redis面试题集
InputStream/OutputStream(文件的输入输出)