当前位置:网站首页>MySQL 45 lecture learning notes (VI) global lock
MySQL 45 lecture learning notes (VI) global lock
2022-07-04 06:37:00 【Tom Kong】
One . Global lock : Lock the entire database instance
Mysql It provides a way to add global read lock The order is
Flush tables with read lock(FTWRL) When you need to make the whole library Read only status , You can use this command , Statements from other threads will Blocked
data to update sentence ( Data Additions and deletions ),
data Definition sentence ( Include Build table , Modify table structure etc. )
Update transaction Submit sentence
Typical use scenario of global lock -- Make a full library logical backup
That is the The whole database, every table select Come out and save it as text During the backup process The entire library is read-only , But let The whole library is read-only, which is dangerous
- Main database backup , Update cannot be performed during backup , Business basically stopped
- Backup from the library , During the backup, the slave database cannot synchronize with the master database binlog, It can lead to Master-slave delay
- No locks Words , The library that the backup system backs up is not a logical point in time , This view is logically inconsistent .
The official logic backup tool is mysqldump
When mysqldump, Using parameter -single-transaction When , A transaction will be started before importing data , To ensure a consistent view
because MVCC This data can be updated normally .
Table lock MySql There are two types of lock at the inner table level :
- One is watch lock ,
- One is metadata lock (meta data lock,MDL)
The syntax of table lock is lock tables ...read/write. And FTWRL similar . It can be used unlock tables Active release lock . It can also be released automatically when the client is disconnected .
We need to pay attention to lock tables grammar In addition to restricting the reading and writing of other threads Also limited The next operation object of this thread .
- For example , If in a thread A perform lock tables t1 t2 write This statement , Other threads write t1, Reading and writing t2 All of the statements will be blocked
- meanwhile , Threads A In execution unlock tables Previously, you could only read t1, Reading and writing t2 The operation of . Linking t1 Not allowed , Naturally, you can't access other tables .
When there is no finer grained lock , Table locking is the most common way to handle concurrency .
Two . The watch lock is MDL(metadata lock)
- MDL You don't need to explicitly use , When accessing a table, it will be automatically added
- MDL The role of is , Ensure the correctness of reading and writing
- If a query is traversing data in a table , Another thread changes the table structure during execution , Delete a list , Then the result obtained by the query thread does not match the table structure , Definitely not .
- therefore , stay MySQL5.5 Version to introduce MDL, When a table is adding, deleting, modifying, and querying , add MDL Read the lock , When it comes to watch When making structural changes , add MDL Write lock
- Read locks are not mutually exclusive , So you can have multiple threads to add, delete, modify and query a table at the same time
- Read and write locks are mutually exclusive , Write locks are mutually exclusive , To ensure the security of the operation to change the structure of the table . therefore , If two threads want to add fields to a table at the same time , One of them has to wait for the other to finish executing .
Add fields to a small table , Cause the whole library to hang
- In the transaction MDL lock . Apply at the beginning of statement execution , But it will not be released immediately after the statement ends , Instead, it will be released after the whole transaction is committed .
- First of all, we have to deal with long affairs , The transaction does not commit , Will always occupy MDL lock . stay MySQL Of information_schema Library innoDB_trx In the table , You can find the current transaction in progress 、
- You have to DDL The changed table happens to have a long transaction running , Consider suspending DDL perhaps kill Long Affairs
Special scenes
If the table you want to change is a hotspot table , Although the amount of data is small , But the requests are frequent , And you have to add a field , What should you do
- stay alert table Statement to set the waiting time , If the specified waiting time can be obtained MDL It's better to write lock , Don't block the following business statements if you can't get them , Give up first , Then the developer or DBA Repeat the process by retrying the command .
边栏推荐
- thread priority
- Google Chrome Portable Google Chrome browser portable version official website download method
- Operator < <> > fool test case
- Explain in one sentence what social proof is
- tars源码分析之4
- JSON web token -- comparison between JWT and traditional session login authentication
- C realize Snake games
- 对List进行排序工具类,可以对字符串排序
- Another company raised the price of SAIC Roewe new energy products from March 1
- Tree DP
猜你喜欢
C实现贪吃蛇小游戏
![[number theory] fast power (Euler power)](/img/1e/5d032c8f2e43f553b4543d28ea2a2d.jpg)
[number theory] fast power (Euler power)
27-31. Dependency transitivity, principle
![[March 3, 2019] MAC starts redis](/img/ff/88638fcdc8d24dc268781c224e8195.jpg)
[March 3, 2019] MAC starts redis
《ClickHouse原理解析与应用实践》读书笔记(4)
Bicolor case
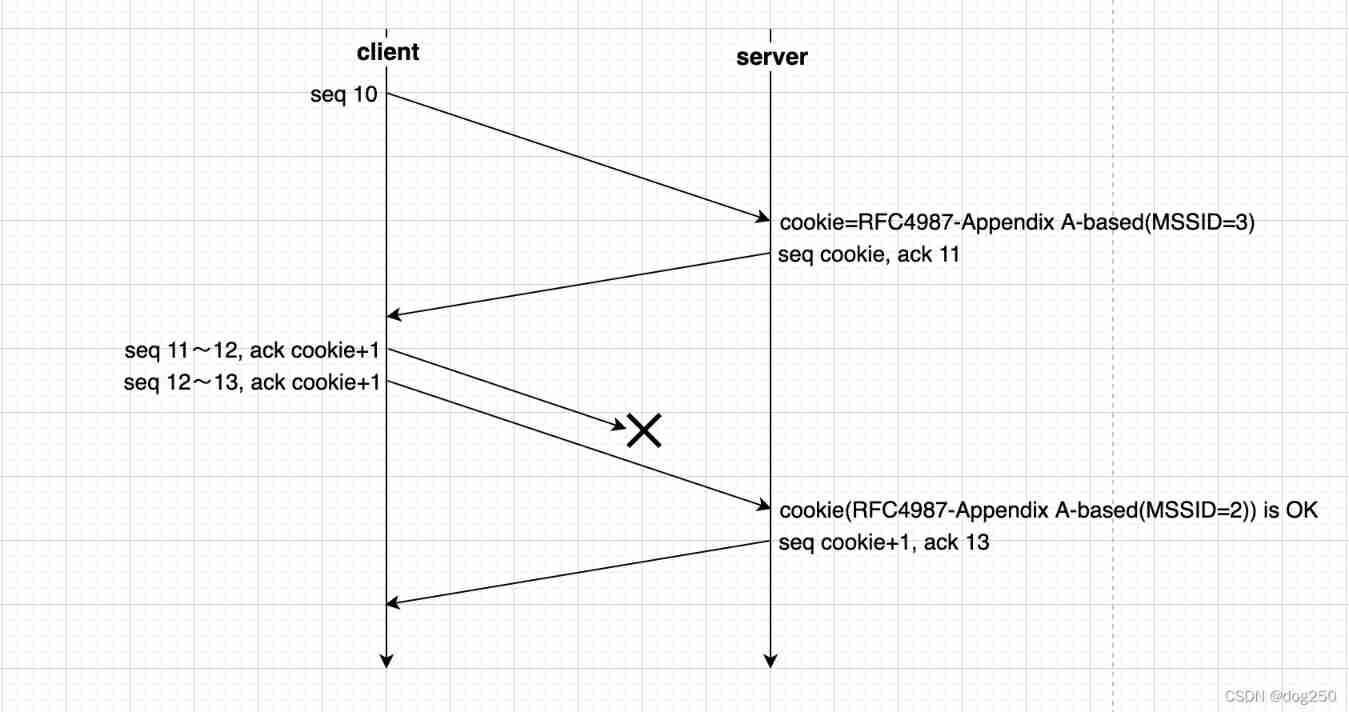
Can the out of sequence message complete TCP three handshakes

双色球案例
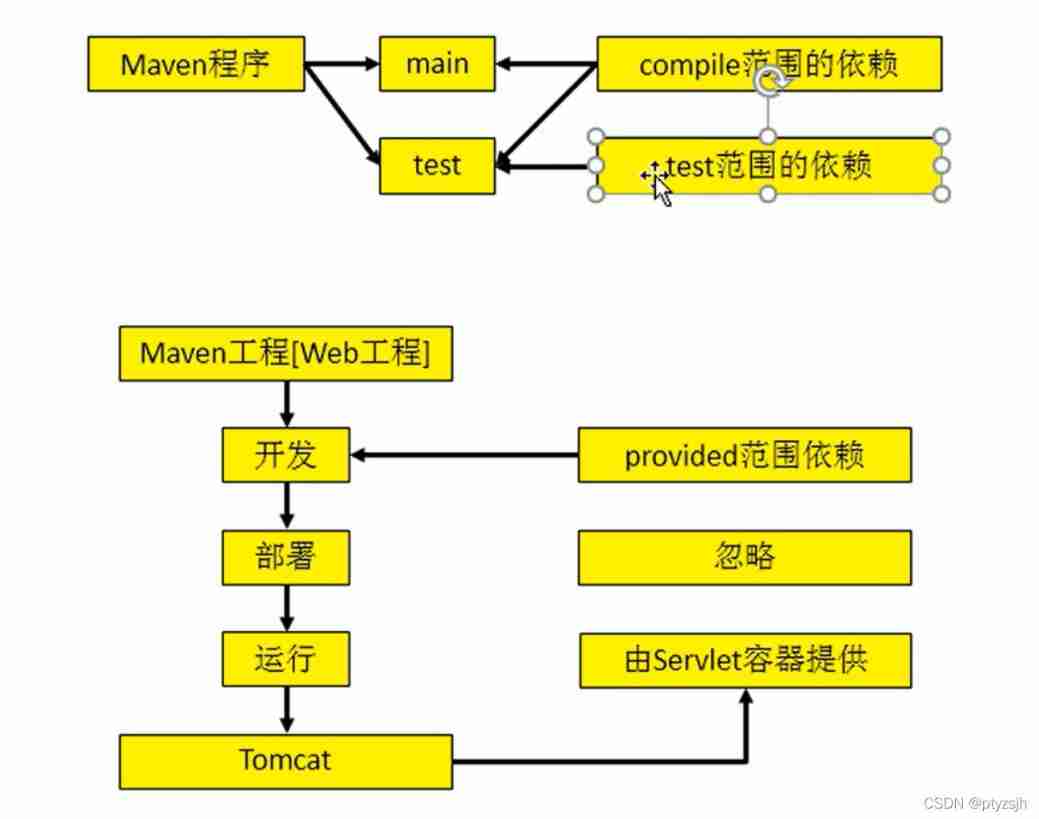
17-18. Dependency scope and life cycle plug-ins
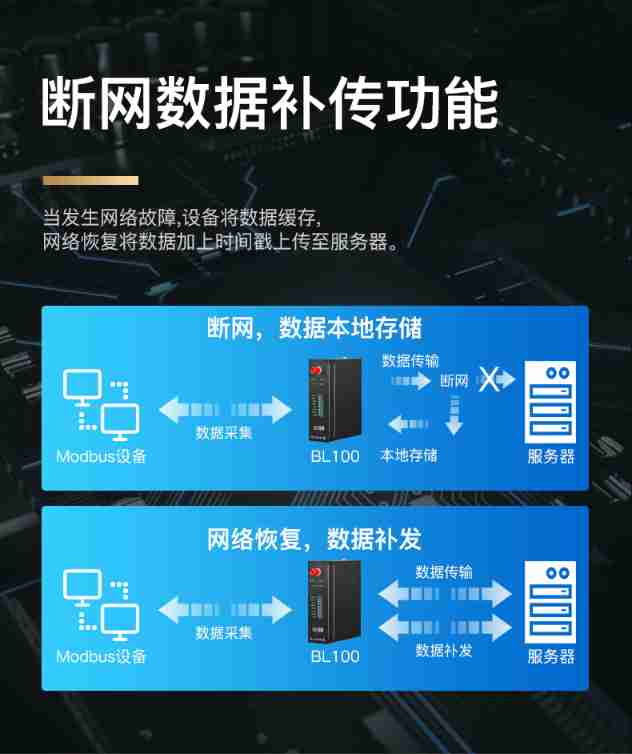
4G wireless all network solar hydrological equipment power monitoring system bms110
随机推荐
ADC voltage calculation of STM32 single chip microcomputer
《国民经济行业分类GB/T 4754—2017》官网下载地址
Tar source code analysis 6
How to implement cross domain requests
Vant --- detailed explanation and use of list component in vant
C语言中的排序,实现从小到大的数字排序法
GoogleChromePortable 谷歌chrome浏览器便携版官网下载方式
740. Delete and get points
7. Agency mode
How does the inner roll break?
STM32 单片机ADC 电压计算
P26-P34 third_ template
[number theory] fast power (Euler power)
SQL join, left join, right join usage
Explain in one sentence what social proof is
Invalid bound statement (not found): com. example. mapper. TblUserRecordMapper. login
tars源码分析之7
Notes and notes
Operator < <> > fool test case
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?