当前位置:网站首页>1、 Relevant theories and tools of network security penetration testing
1、 Relevant theories and tools of network security penetration testing
2022-07-04 06:19:00 【Dear, Ting】
One 、 What is network security penetration testing ?
Famous movies in America 《 do a quick change 》 in , Thunder · Breslin is one of the strongest prison break masters in the world , He's in the past 8 Successfully from 14 Escaped from the heavily guarded prison . even so , Thunder · Breslin is not a criminal , His real identity is a prison security expert of the national security agency . Thunder · Breslin went to prison as a criminal , Look for loopholes in the prison . And every time he successfully escaped from prison , It means that he has found the loophole in the prison security . Of course, ray · Breslin's purpose is not to destroy , But to ensure that every prisoner in prison cannot escape . Every time he successfully escaped from prison , Will make the prison stronger , So he is a legal jailbreak .
1、 Four major aspects
1. The concept of network security penetration testing .
2. The executive standard of network security penetration test .
3. Common tools for network security penetration testing .
4. Preparation of network security penetration test report .2、 The concept of network security penetration testing
1. Black box testing is also called external testing
2. White box testing is also called internal testing
3. Use white box test and black box test together , It's the gray box test 3、 The goal of network security penetration testing
1. Network devices
2. Physical security
3. operating system
4. Applications
5. Management system 4、 Characteristics of network security penetration test
1. Network security penetration testing is a business behavior , The customer should take the initiative , And give authorization permission before .
2. The goal of network security penetration testing must be evaluated as a whole , Analyze as comprehensively as possible .
3. The purpose of network security penetration test is to improve users' network security mechanism .Two 、 The executive standard of network security penetration test
There is 7 Stages :
1. The communication stage with customers
2. Intelligence gathering stage
3. Threat modeling phase
4. Vulnerability analysis stage
5. Vulnerability exploitation stage
6. Post penetration attack stage
7. Reporting stage 1、 Communication phase
1. The goal of penetration testing
2. The method used in the penetration test process
3. Conditions required for conducting penetration tests
4. Limitations during penetration testing
5. Duration of penetration test process
6. The cost of penetration testing
7. The expected goal of the penetration test process 2、 Collection phase
1. Passive scanning
2. Active scanning 3、 Threat modeling
At this stage, the following issues are mainly considered :
1、 Which assets are important in the target .
2、 The technology and means used in the attack .
3、 Which groups may cause damage to the target system .
4、 What methods will these groups use to destroy .
4、 Vulnerability analysis
This stage is the process of discovering vulnerabilities from the target . The vulnerability may be located anywhere in the target , From server to switch , From the operating system used to Web Applications are the objects we want to check . At this stage, we will find the target operating system according to the previous intelligence collection 、 Open ports and service programs , Find and analyze vulnerabilities in the target system .
5、 Exploit
After finding the vulnerability on the target , You can use the vulnerability penetration program to test the target system . At this stage , Our focus is on , How to bypass the security mechanism of the target to control the target system or access the target resources . If we successfully completed the task in the last stage , Then this stage can be carried out accurately and smoothly . The penetration test at this stage should have an accurate range . The main goal of vulnerability exploitation is to obtain the important assets we previously evaluated . Finally, the probability of success and the greatest possible impact on the target should also be considered when carrying out infiltration .
6、 Post penetration
This stage is closely connected with the previous stage , As a penetration tester , We must try our best to simulate the possible consequences after the target is infiltrated .
The tasks that may be completed at this stage include the following :
Control permission promotion .
Theft of login credentials .
Access to important information .
Use goals as a springboard .
Establish long-term control channels .
7、 Reporting stage
This stage is the last stage of the whole penetration test stage , At the same time, it is also a stage that can best reflect the results of our work , We will submit all the previous findings to the customer in writing . actually , This report is also the only demand of customers . We must report the problems in the test objectives to the customers in the form of simple and direct and try to avoid a large number of professional terms , And possible risks . This report should point out the most important threats to the target system 、 Tables and icons generated using penetration data , And the repair plan for the problems of the target system 、 Suggestions for improving the current security mechanism .
3、 ... and 、 Common tools for network security penetration testing :
1.Nmap
2.Maltego
3.Recon-NG
4.OpenVAS
5.Metasploit
6.SET
7.Ettercap
8.Burpsuite
9.Wireshark
Four 、 Preparation of network security penetration test report
The last and most important stage of penetration testing is report preparation . As a qualified penetration tester, he should have good report writing ability . The penetration tester should ensure the professionalism of the report when writing the test , However, the final readers of this report are often managers who do not have professional domain knowledge , Therefore, it is necessary to avoid using too professional terms , And easy to understand .
summary :
What is network security penetration testing , And how to carry out network security penetration testing . Mastering the standards of penetration test is of great help to our later study . If you want to have a deeper understanding of the network security penetration test standards explained in this chapter , You can visit the website pentest-standard, Here is a very detailed introduction to penetration testing 7 Stages .
边栏推荐
- Review | categories and mechanisms of action of covid-19 neutralizing antibodies and small molecule drugs
- Leakage detection relay jy82-2p
- 【无标题】
- [March 3, 2019] MAC starts redis
- AWT introduction
- FRP intranet penetration, reverse proxy
- JS扁平化数形结构的数组
- QT get random color value and set label background color code
- Weekly summary (*63): about positive energy
- SQL injection SQL lab 11~22
猜你喜欢
509. 斐波那契数、爬楼梯所有路径、爬楼梯最小花费

509. Fibonacci number, all paths of climbing stairs, minimum cost of climbing stairs
Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)
Abap:ooalv realizes the function of adding, deleting, modifying and checking
Tf/pytorch/cafe-cv/nlp/ audio - practical demonstration of full ecosystem CPU deployment - Intel openvino tool suite course summary (Part 2)
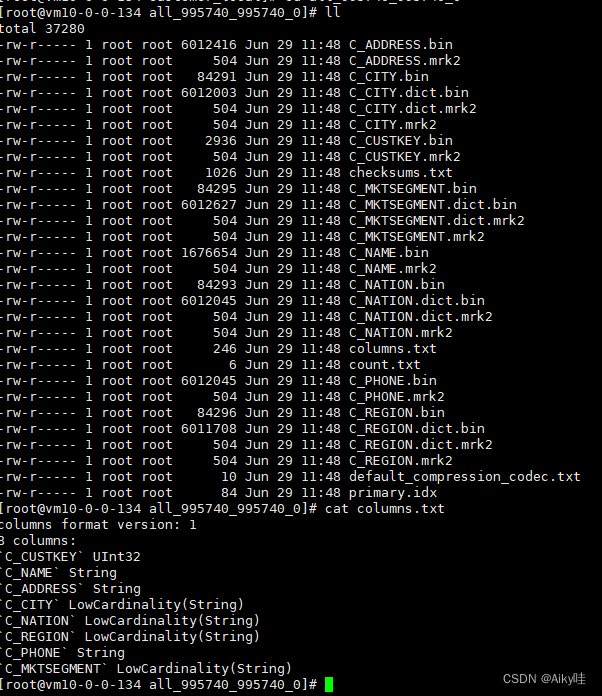
《ClickHouse原理解析与应用实践》读书笔记(4)
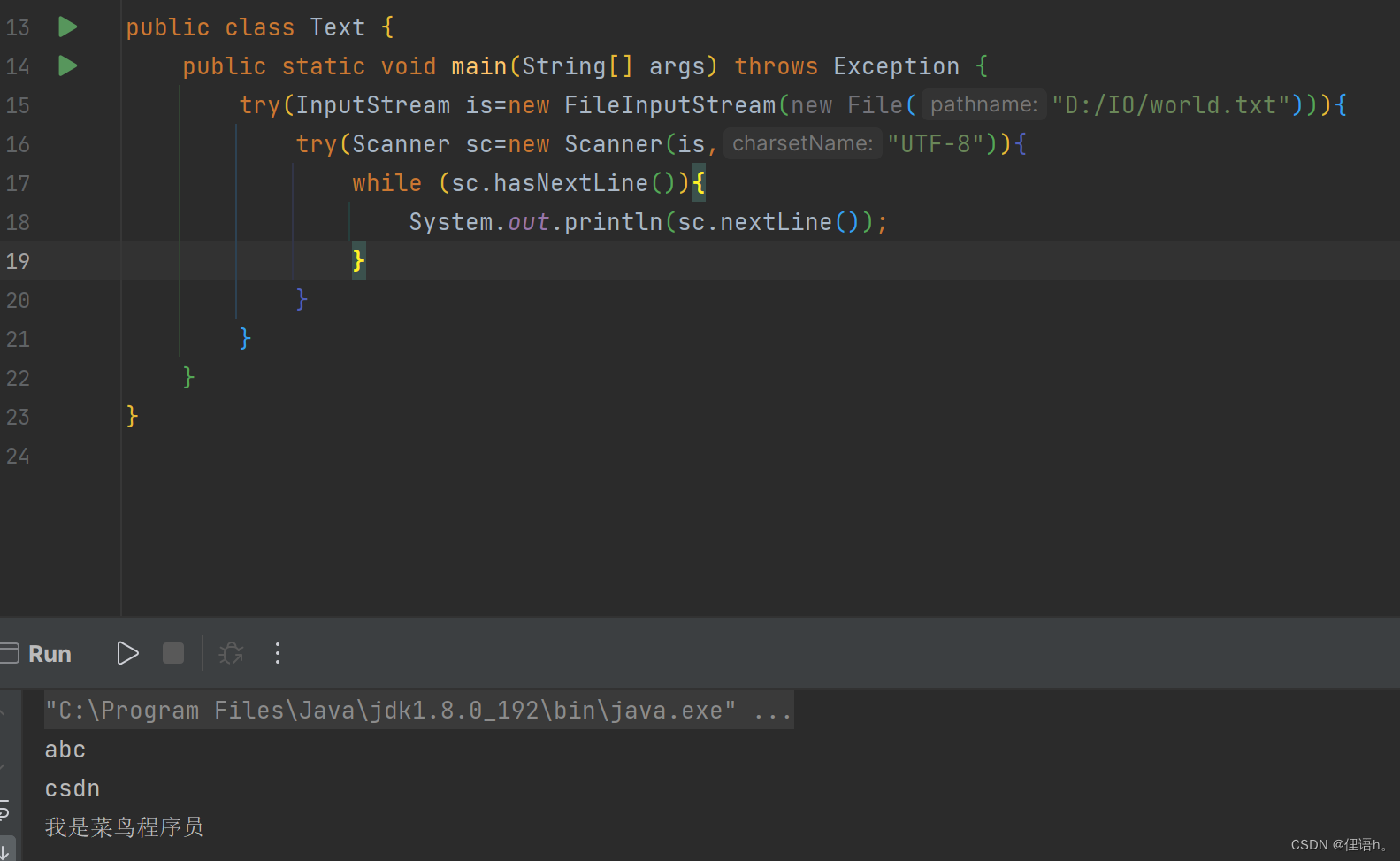
Inputstream/outputstream (input and output of file)
![Yiwen unlocks Huawei's new cloud skills - the whole process of aiot development [device access - ESP end-to-side data collection [mqtt]- real time data analysis] (step-by-step screenshot is more detai](/img/a5/be967170a18cb2de097f01a6d4e039.jpg)
Yiwen unlocks Huawei's new cloud skills - the whole process of aiot development [device access - ESP end-to-side data collection [mqtt]- real time data analysis] (step-by-step screenshot is more detai
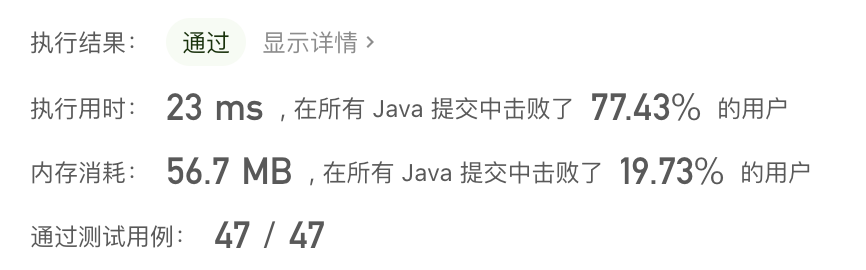
Sword finger offer II 038 Daily temperature

InputStream/OutputStream(文件的输入输出)
随机推荐
Detectron:训练自己的数据集——将自己的数据格式转换成COCO格式
win10清除快速访问-不留下痕迹
How to expand all collapse panels
746. Climb stairs with minimum cost
Invalid bound statement (not found): com. example. mapper. TblUserRecordMapper. login
Manually page the list (parameter list, current page, page size)
The solution of win11 taskbar right click without Task Manager - add win11 taskbar right click function
C realize Snake games
QT qtablewidget table column top requirements ideas and codes
Dimension and format of data
MySQL learning notes 3 - JDBC
Lightroom import picture gray / Black rectangular multi display
How does apscheduler set tasks not to be concurrent (that is, execute the next task after the first one)?
QT get random color value and set label background color code
AWT common components, FileDialog file selection box
AWT介绍
如何获取el-tree中所有节点的父节点
雲原生——上雲必讀之SSH篇(常用於遠程登錄雲服務器)
Json Web token - jwt vs. Traditional session login Authentication
198. House raiding