当前位置:网站首页>Analysis of tars source code 1
Analysis of tars source code 1
2022-07-04 06:36:00 【Tao song remains the same】
base64 Is a reversible transformation algorithm , Not encryption , Nor is it a hash , Let's take a look at the implementation . I have written before :
#include "util/tc_base64.h"
namespace tars
{
// Base64 Encoding table : Fetch the input data stream every time 6 bit, Use this 6 bit Value (0-63) Look up the table as an index , Output corresponding characters . such , Every time 3 Bytes will be encoded as 4 Characters (3×8 → 4×6); discontent 4 A character with '=' fill .
const char TC_Base64::EnBase64Tab[] = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";
// Base64 Decoding table : take 64 The value of printable characters is used as the index , The value obtained by looking up the table ( The scope is 0-63) Connect them in turn to get the decoding result .
// Decoding table size by 256, Illegal characters will be decoded into ASCII 0
const char TC_Base64::DeBase64Tab[] =
{
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
62, // '+'
0, 0, 0,
63, // '/'
52, 53, 54, 55, 56, 57, 58, 59, 60, 61, // '0'-'9'
0, 0, 0, 0, 0, 0, 0,
0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12,
13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, // 'A'-'Z'
0, 0, 0, 0, 0, 0,
26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36, 37, 38,
39, 40, 41, 42, 43, 44, 45, 46, 47, 48, 49, 50, 51, // 'a'-'z'
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
};
string TC_Base64::encode(const string &data, bool bChangeLine/* = false*/)
{
if(data.empty())
return "";
// Let the original string length be a, The results include carriage return, line feed and '/0', The final length is (a/3+1)*4+(a/3+1)*4*2/76+1, about 1.369*a+6
char *pDst = NULL;
int iBufSize = (int)(data.size()*1.4) + 6;
pDst = new char[iBufSize];
if(pDst == NULL)
return "";
int iDstLen = encode((unsigned char*)data.c_str(), data.size(), pDst, bChangeLine);
string ret(pDst,iDstLen);
delete [] pDst;
return ret;
}
string TC_Base64::decode(const string &data)
{
if(data.empty())
return "";
unsigned char *pDst = NULL;
pDst = new unsigned char[data.size()];
if(pDst == NULL)
return "";
int iDstLen = decode(data.c_str(), data.size(), pDst);
string ret((char*)pDst,iDstLen);
delete [] pDst;
return ret;
}
int TC_Base64::encode(const unsigned char* pSrc, int nSrcLen, char* pDst, bool bChangeLine/* = false*/)
{
unsigned char c1, c2, c3;
int nDstLen = 0;
int nLineLen = 0;
int nDiv = nSrcLen / 3;
int nMod = nSrcLen % 3;
// Every time 3 Bytes , Code as 4 Characters
for (int i = 0; i < nDiv; i ++)
{
c1 = *pSrc++;
c2 = *pSrc++;
c3 = *pSrc++;
*pDst++ = EnBase64Tab[c1 >> 2];
*pDst++ = EnBase64Tab[((c1 << 4) | (c2 >> 4)) & 0x3f];
*pDst++ = EnBase64Tab[((c2 << 2) | (c3 >> 6)) & 0x3f];
*pDst++ = EnBase64Tab[c3 & 0x3f];
nLineLen += 4;
nDstLen += 4;
// relevant RFC More than per line in 76 You need to add carriage return line feed
if (bChangeLine && nLineLen > 72)
{
*pDst++ = '\r';
*pDst++ = '\n';
nLineLen = 0;
nDstLen += 2;
}
}
// Encode the remaining bytes
if (nMod == 1)
{
c1 = *pSrc++;
*pDst++ = EnBase64Tab[(c1 & 0xfc) >> 2];
*pDst++ = EnBase64Tab[((c1 & 0x03) << 4)];
*pDst++ = '=';
*pDst++ = '=';
nLineLen += 4;
nDstLen += 4;
}
else if (nMod == 2)
{
c1 = *pSrc++;
c2 = *pSrc++;
*pDst++ = EnBase64Tab[(c1 & 0xfc) >> 2];
*pDst++ = EnBase64Tab[((c1 & 0x03) << 4) | ((c2 & 0xf0) >> 4)];
*pDst++ = EnBase64Tab[((c2 & 0x0f) << 2)];
*pDst++ = '=';
nDstLen += 4;
}
// Output with a terminator
*pDst = '\0';
return nDstLen;
}
int TC_Base64::decode(const char* pSrc, int nSrcLen, unsigned char* pDst)
{
int nDstLen; // Output character count
int nValue; // Integer used for decoding
int i;
i = 0;
nDstLen = 0;
// take 4 Characters , Decode to a long integer , Then through the shift, we get 3 Bytes
while (i < nSrcLen)
{
// Skip carriage return and line feed
if (*pSrc != '\r' && *pSrc!='\n')
{
if(i + 4 > nSrcLen) // The string to be decoded is illegal , Stop decoding immediately and return
break;
nValue = DeBase64Tab[int(*pSrc++)] << 18;
nValue += DeBase64Tab[int(*pSrc++)] << 12;
*pDst++ = (nValue & 0x00ff0000) >> 16;
nDstLen++;
if (*pSrc != '=')
{
nValue += DeBase64Tab[int(*pSrc++)] << 6;
*pDst++ = (nValue & 0x0000ff00) >> 8;
nDstLen++;
if (*pSrc != '=')
{
nValue += DeBase64Tab[int(*pSrc++)];
*pDst++ =nValue & 0x000000ff;
nDstLen++;
}
}
i += 4;
}
else
{
pSrc++;
i++;
}
}
// Output with a terminator
*pDst = '\0';
return nDstLen;
}
}边栏推荐
- Arcpy uses the updatelayer function to change the symbol system of the layer
- Bicolor case
- Practical gadget instructions
- 7. Agency mode
- Mysql 45讲学习笔记(十一)字符串字段怎么加索引
- Fundamentals of SQL database operation
- Mysql 45讲学习笔记(十)force index
- [Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
- MySQL learning notes 3 - JDBC
- Sleep quality today 78 points
猜你喜欢
![Yiwen unlocks Huawei's new cloud skills - the whole process of aiot development [device access - ESP end-to-side data collection [mqtt]- real time data analysis] (step-by-step screenshot is more detai](/img/a5/be967170a18cb2de097f01a6d4e039.jpg)
Yiwen unlocks Huawei's new cloud skills - the whole process of aiot development [device access - ESP end-to-side data collection [mqtt]- real time data analysis] (step-by-step screenshot is more detai

Download kicad on Alibaba cloud image station
Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)

云原生——上云必读之SSH篇(常用于远程登录云服务器)
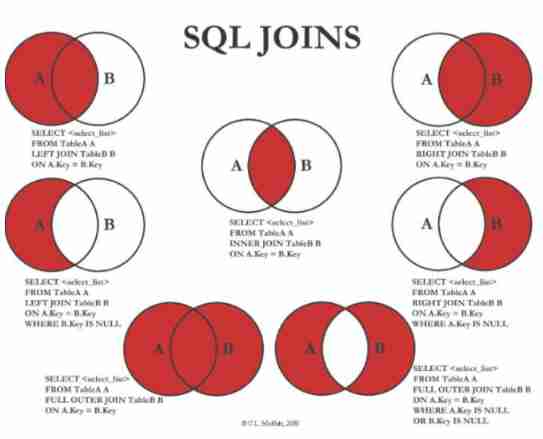
SQL join, left join, right join usage
C language - Blue Bridge Cup - Snake filling
Practical gadget instructions

746. Climb stairs with minimum cost
How to use multithreading to export excel under massive data? Source code attached!
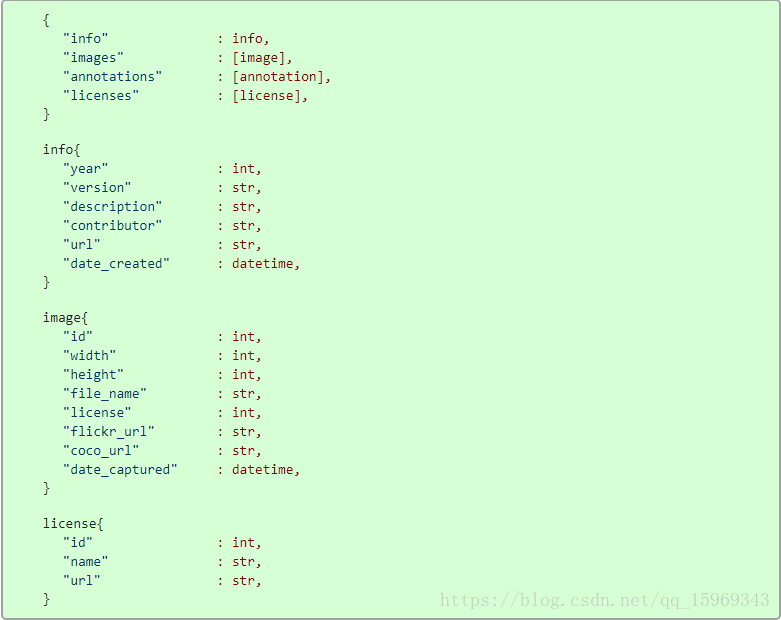
Detectron: train your own data set -- convert your own data format to coco format
随机推荐
regular expression
8. Factory method
C實現貪吃蛇小遊戲
lightroom 导入图片灰色/黑色矩形 多显示器
Fast power (template)
Average two numbers
How to implement cross domain requests
uniapp 自定义环境变量
[March 3, 2019] MAC starts redis
tars源码分析之2
Operator < <> > fool test case
How to help others effectively
Learn about the Internet of things protocol WiFi ZigBee Bluetooth, etc. --- WiFi and WiFi protocols start from WiFi. What do we need to know about WiFi protocol itself?
[backpack DP] backpack problem
JSON web token -- comparison between JWT and traditional session login authentication
Dimension and format of data
ABCD four sequential execution methods, extended application
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
金盾视频播放器拦截的软件关键词和进程信息
tcp socket 的 recv 如何接收指定长度消息?