当前位置:网站首页>[Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
[Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
2022-07-04 06:21:00 【Programmer community】
List of articles
- One 、CPU Cache mechanism
- Two 、CPU Cache mechanism Lead to Function interception failed
One 、CPU Cache mechanism
CPU In the architecture model , Instructions At the beginning , Store in memory , Such as : /proc/pid/maps Each of the .so Dynamic libraries have an address in memory , Instructions are stored in the dynamic library ;
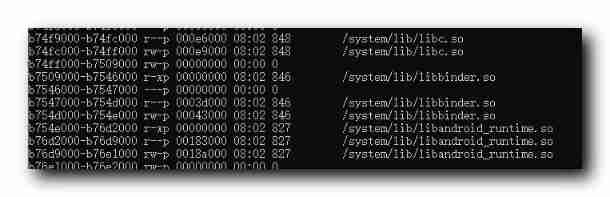
CPU And The access rate between memories is relatively low , The low here is with CPU Access register comparison , CPU The speed at which registers are accessed > CPU Speed of accessing memory > CPU The speed at which the disk is accessed ;
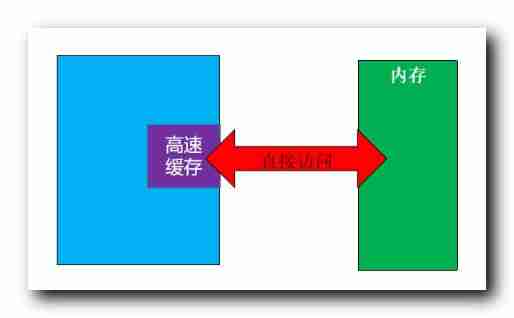
In order to improve CPU visit Memory The speed of , stay CPU A piece is prepared inside Cache , Instructions in memory are not put directly into CPU , Instead, put it in the cache first , Then read from the cache to the register for instruction operation ;
If CPU The instruction to be accessed is just in the cache , Then you can execute at high speed Code instructions , At the same time of execution , The subsequent instructions are continuously loaded into the cache , So that's a guarantee CPU Efficient execution of instructions ;
Two 、CPU Cache mechanism Lead to Function interception failed
In the last blog 【Android reverse 】 Function interception principle ( By modifying the GOT Global offset table interception function | Function interception is realized by adding jump code to the actually called function ) Reliable function interception scheme in , Recommended " Add jump code to the actually called function to realize function interception " The scheme implements function interception ;
The above scheme needs to be implemented in The function actually called in , Write a jump instruction , The function of the write instruction is stored in memory , It can only be written in memory , CPU The cache of is entirely composed of CPU Internal hardware call , External code cannot access the cache ;
Here is a question , stay Insert jump code into the intercepted function , If the function has been loaded into CPU In the cache of , that Modify memory , Can't make CPU Execute the modified code instruction ;
CPU Medium The cache is Sort by command rate , The more frequently used functions , The higher the priority , The less likely it is to be removed ;
If the function to be intercepted , Call frequency is very high , Maybe the modified function will always reside in CPU In cache , Just The function has been unable to be intercepted ;
And that leads to this Function interception , unable 100% success ;
边栏推荐
- 《ClickHouse原理解析与应用实践》读书笔记(4)
- APScheduler如何设置任务不并发(即第一个任务执行完再执行下一个)?
- Invalid revision: 3.18.1-g262b901-dirty
- Which water in the environment needs water quality monitoring
- Stc8h development (XII): I2C drive AT24C08, at24c32 series EEPROM storage
- FRP intranet penetration, reverse proxy
- How to get the parent node of all nodes in El tree
- AWT常用组件、FileDialog文件选择框
- gslb(global server load balance)技术的一点理解
- 对List进行排序工具类,可以对字符串排序
猜你喜欢
Configure cross compilation tool chain and environment variables

How does apscheduler set tasks not to be concurrent (that is, execute the next task after the first one)?
JSON Web Token----JWT和传统session登录认证对比
AWT common components, FileDialog file selection box
Native Cloud - SSH articles must be read on Cloud (used for Remote Login to Cloud Server)
How to use multithreading to export excel under massive data? Source code attached!
Layoutmanager layout manager: flowlayout, borderlayout, GridLayout, gridbaglayout, CardLayout, BoxLayout

AWT常用组件、FileDialog文件选择框
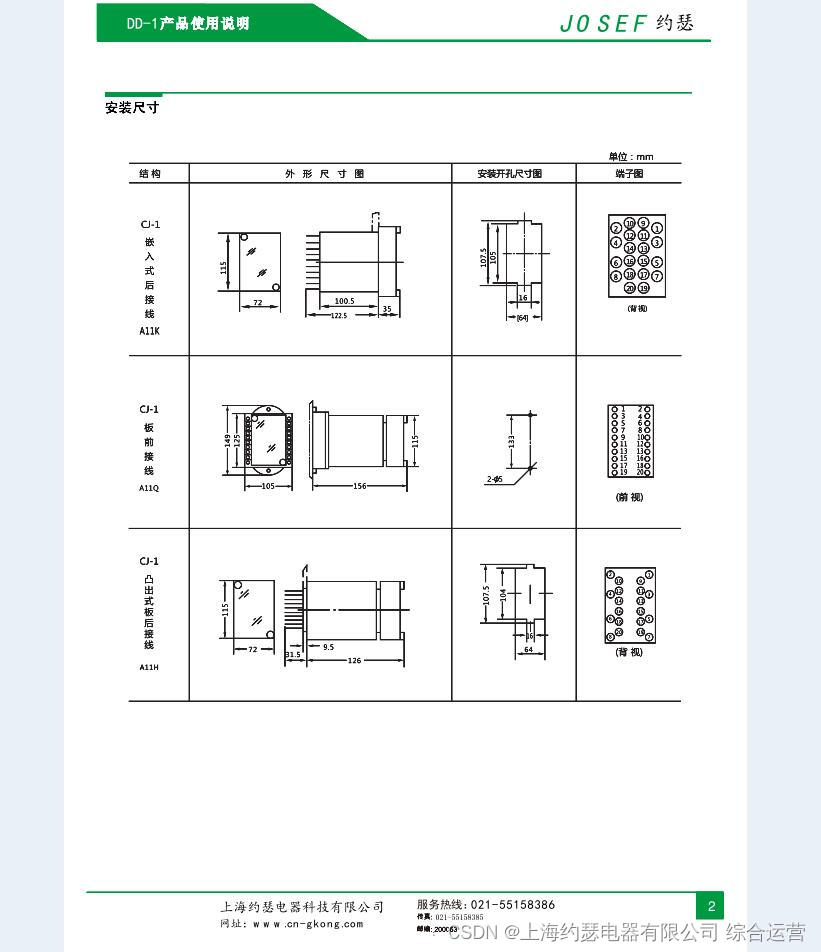
Grounding relay dd-1/60
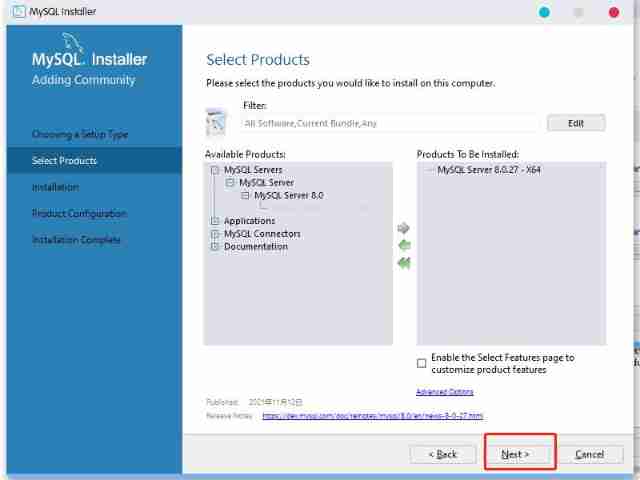
MySQL installation and configuration
随机推荐
After the festival, a large number of people change careers. Is it still time to be 30? Listen to the experience of the past people
C實現貪吃蛇小遊戲
Lightroom import picture gray / Black rectangular multi display
Abap:ooalv realizes the function of adding, deleting, modifying and checking
配置交叉编译工具链和环境变量
C language - Blue Bridge Cup - Snake filling
webrtc 快速搭建 视频通话 视频会议
Reading notes of Clickhouse principle analysis and Application Practice (4)
Arcpy uses the updatelayer function to change the symbol system of the layer
复合非线性反馈控制(二)
MySQL information_ Schema database
实用的小工具指令
How to implement lazy loading in El select (with search function)
[Chongqing Guangdong education] electronic circuit homework question bank of RTVU secondary school
Tsinghua University product: penalty gradient norm improves generalization of deep learning model
报错cvc-complex-type.2.4.a: 发现了以元素 ‘base-extension‘ 开头的无效内容。应以 ‘{layoutlib}‘ 之一开头。
509. 斐波那契数、爬楼梯所有路径、爬楼梯最小花费
740. Delete and get points
AWT introduction
Experience weekly report no. 102 (July 4, 2022)