当前位置:网站首页>How does the recv of TCP socket receive messages of specified length?
How does the recv of TCP socket receive messages of specified length?
2022-07-04 06:37:00 【Tao song remains the same】
occasionally ,tcp socket You must receive the specified number of bytes to meet the expectation , Then how to achieve ?
It is introduced in many books of network programming , Let's see ( Always accept , Up to standard ):
int recvLength(char *sRecvBuffer, size_t iRecvLen)
{
int iRet = checkSocket();
if(iRet < 0)
{
return iRet;
}
size_t iRecvLeft = iRecvLen;
iRecvLen = 0;
TC_Epoller epoller(false);
epoller.create(1);
epoller.add(_socket.getfd(), 0, EPOLLIN);
while(iRecvLeft != 0)
{
int iRetCode = epoller.wait(_timeout);
if (iRetCode < 0)
{
_socket.close();
return EM_SELECT;
}
else if (iRetCode == 0)
{
_socket.close();
return EM_TIMEOUT;
}
epoll_event ev = epoller.get(0);
if(ev.events & EPOLLIN)
{
int len = _socket.recv((void*)(sRecvBuffer + iRecvLen), iRecvLeft);
if (len < 0)
{
_socket.close();
return EM_RECV;
}
else if (len == 0)
{
_socket.close();
return EM_CLOSE;
}
iRecvLeft -= len;
iRecvLen += len;
}
else
{
_socket.close();
return EM_SELECT;
}
}
return EM_SUCCESS;
}边栏推荐
- SQL injection SQL lab 11~22
- Vant --- detailed explanation and use of list component in vant
- ADC voltage calculation of STM32 single chip microcomputer
- buuctf-pwn write-ups (8)
- leetcode 310. Minimum Height Trees
- R统计绘图-随机森林分类分析及物种丰度差异检验组合图
- CORS is not intended to protect API endpoints - nikofischer
- Mysql 45讲学习笔记(十四)count(*)
- Explain in one sentence what social proof is
- [MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)
猜你喜欢

How to choose the middle-aged crisis of the testing post? Stick to it or find another way out? See below
![[March 3, 2019] MAC starts redis](/img/ff/88638fcdc8d24dc268781c224e8195.jpg)
[March 3, 2019] MAC starts redis
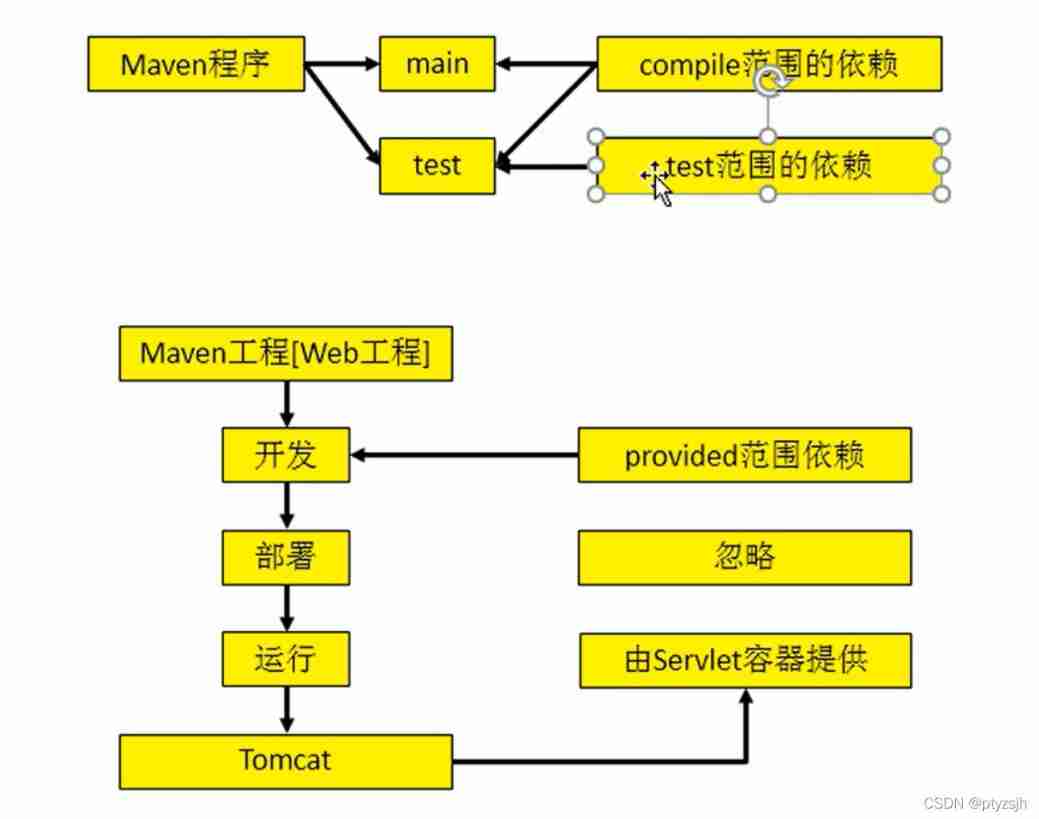
17-18. Dependency scope and life cycle plug-ins
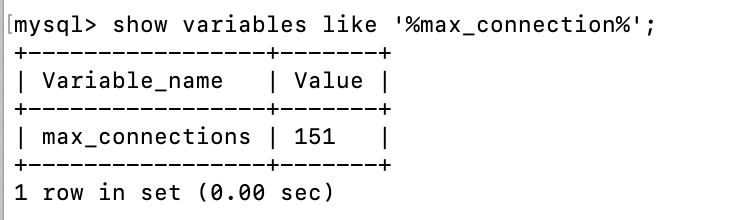
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
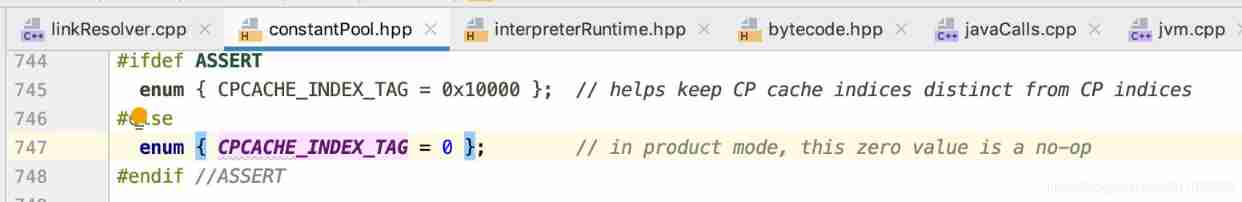
24 magicaccessorimpl can access the debugging of all methods
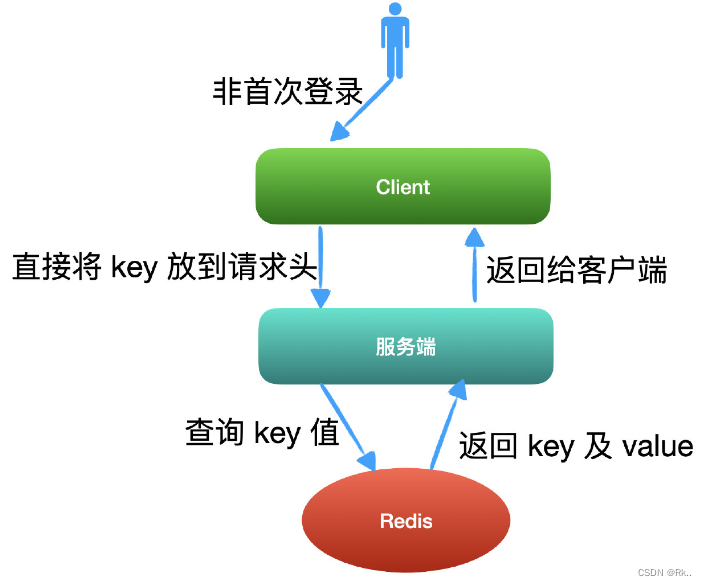
JSON Web Token----JWT和传统session登录认证对比
Uniapp custom environment variables
SQL injection SQL lab 11~22

2022 where to find enterprise e-mail and which is the security of enterprise e-mail system?

Variables d'environnement personnalisées uniapp
随机推荐
Is the insurance annuity product worth buying? Is there a hole?
Arcpy uses the updatelayer function to change the symbol system of the layer
1、 Relevant theories and tools of network security penetration testing
【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
实用的小工具指令
[backpack DP] backpack problem
Mysql 45讲学习笔记(六)全局锁
金盾视频播放器拦截的软件关键词和进程信息
C语言中的排序,实现从小到大的数字排序法
ABAP:OOALV实现增删改查功能
C réaliser des jeux de serpents gourmands
Uniapp custom environment variables
Sort list tool class, which can sort strings
tars源码分析之5
How to help others effectively
双色球案例
MySQL installation and configuration
Mysql 45讲学习笔记(十)force index
Operator < <> > fool test case
Inputstream/outputstream (input and output of file)