当前位置:网站首页>C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
2022-07-04 06:21:00 【Brother Lei talks about programming】
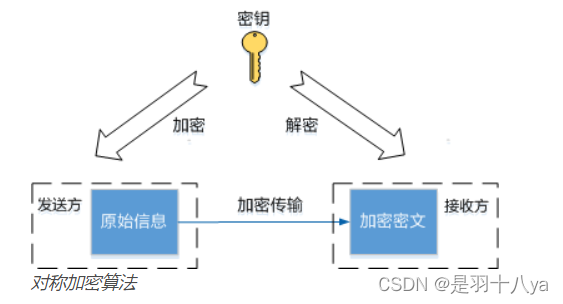
Ideas : Use random vectors , Put the random vector into the ciphertext , Before intercepting from the ciphertext each time decryption 16 position , In fact, it is the random vector we encrypted before .
Code
public static string Encrypt(string plainText, string AESKey)
{
RijndaelManaged rijndaelCipher = new RijndaelManaged();
byte[] inputByteArray = Encoding.UTF8.GetBytes(plainText);// Get the byte array to be encrypted
rijndaelCipher.Key = Convert.FromBase64String(AESKey);// The encryption and decryption parties agree on the key :AESKey
rijndaelCipher.GenerateIV();
byte[] keyIv = rijndaelCipher.IV;
byte[] cipherBytes = null;
using (MemoryStream ms = new MemoryStream())
{
using (CryptoStream cs = new CryptoStream(ms, rijndaelCipher.CreateEncryptor(), CryptoStreamMode.Write))
{
cs.Write(inputByteArray, 0, inputByteArray.Length);
cs.FlushFinalBlock();
cipherBytes = ms.ToArray();// Get the encrypted byte array
cs.Close();
ms.Close();
}
}
var allEncrypt = new byte[keyIv.Length + cipherBytes.Length];
Buffer.BlockCopy(keyIv, 0, allEncrypt, 0, keyIv.Length);
Buffer.BlockCopy(cipherBytes, 0, allEncrypt, keyIv.Length * sizeof(byte), cipherBytes.Length);
return Convert.ToBase64String(allEncrypt);
}
public static string Decrypt(string showText, string AESKey)
{
string result = string.Empty;
try
{
byte[] cipherText = Convert.FromBase64String(showText);
int length = cipherText.Length;
SymmetricAlgorithm rijndaelCipher = Rijndael.Create();
rijndaelCipher.Key = Convert.FromBase64String(AESKey);// The encryption and decryption key agreed by both parties
byte[] iv = new byte[16];
Buffer.BlockCopy(cipherText, 0, iv, 0, 16);
rijndaelCipher.IV = iv;
byte[] decryptBytes = new byte[length - 16];
byte[] passwdText = new byte[length - 16];
Buffer.BlockCopy(cipherText, 16, passwdText, 0, length - 16);
using (MemoryStream ms = new MemoryStream(passwdText))
{
using (CryptoStream cs = new CryptoStream(ms, rijndaelCipher.CreateDecryptor(), CryptoStreamMode.Read))
{
cs.Read(decryptBytes, 0, decryptBytes.Length);
cs.Close();
ms.Close();
}
}
result = Encoding.UTF8.GetString(decryptBytes).Replace("\0", ""); /// End of string '\0' Get rid of
}
catch { }
return result;
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
call :
string jiaMi = MyAESTools.Encrypt(textBox1.Text, "abcdefgh12345678abcdefgh12345678");
string jieMi = MyAESTools.Decrypt(textBox3.Text, "abcdefgh12345678abcdefgh12345678");
- 1.
- 2.
- 3.
Follow the QR code below , Subscribe to more .

边栏推荐
- 运算符<< >>傻瓜式测试用例
- Practical gadget instructions
- How to help others effectively
- Learn about the Internet of things protocol WiFi ZigBee Bluetooth, etc. --- WiFi and WiFi protocols start from WiFi. What do we need to know about WiFi protocol itself?
- Sword finger offer II 038 Daily temperature
- How to avoid JVM memory leakage?
- 对List进行排序工具类,可以对字符串排序
- gslb(global server load balance)技术的一点理解
- 27-31. Dependency transitivity, principle
- Webrtc quickly set up video call and video conference
猜你喜欢
Win10 clear quick access - leave no trace
JS flattened array of number shape structure
Impact relay jc-7/11/dc110v
雲原生——上雲必讀之SSH篇(常用於遠程登錄雲服務器)
ABAP:OOALV实现增删改查功能
17-18. Dependency scope and life cycle plug-ins
如何实现视频平台会员多账号登录
Arcpy 利用updatelayer函数改变图层的符号系统
Kubernets first meeting
High performance parallel programming and optimization | lesson 02 homework at home
随机推荐
Kubernets first meeting
Weekly summary (*63): about positive energy
Impact relay jc-7/11/dc110v
AWT常用组件、FileDialog文件选择框
JS flattened array of number shape structure
Component、Container容器常用API详解:Frame、Panel、ScrollPane
Sleep quality today 78 points
QT get random color value and set label background color code
如何获取el-tree中所有节点的父节点
Luogu deep foundation part 1 Introduction to language Chapter 5 array and data batch storage
Leetcode question brushing record | 206_ Reverse linked list
ES6 modularization
Nexus 6p downgraded from 8.0 to 6.0+root
Internet of things protocol ZigBee ZigBee module uses the concept of protocol stack
"In simple language programming competition (basic)" part 1 Introduction to language Chapter 3 branch structure programming
QT QTableWidget 表格列置顶需求的思路和代码
Design and implementation of tcp/ip series overview
Bicolor case
Grounding relay dd-1/60
JS get the attribute values nested in the object