当前位置:网站首页>Tar source code analysis 4
Tar source code analysis 4
2022-07-04 06:37:00 【Tao song remains the same】
Basics buffer The implementation of the , It's also very simple. , Take a general look at :
#include "util/tc_buffer.h"
#include <iostream>
#include <algorithm>
#include <limits>
#include <cassert>
inline static std::size_t RoundUp2Power(std::size_t size)
{
if (size == 0)
return 0;
std::size_t roundUp = 1;
while (roundUp < size)
roundUp *= 2;
return roundUp;
}
namespace tars
{
const std::size_t TC_Buffer::kMaxBufferSize = std::numeric_limits<std::size_t>::max() / 2;
const std::size_t TC_Buffer::kDefaultSize = 128;
std::size_t TC_Buffer::PushData(const void* data, std::size_t size)
{
if (!data || size == 0)
return 0;
if (ReadableSize() + size >= kMaxBufferSize)
return 0; // overflow
AssureSpace(size);
::memcpy(&_buffer[_writePos], data, size);
Produce(size);
return size;
}
std::size_t TC_Buffer::PopData(void* buf, std::size_t size)
{
const std::size_t dataSize = ReadableSize();
if (!buf ||
size == 0 ||
dataSize == 0)
return 0;
if (size > dataSize)
size = dataSize; // truncate
::memcpy(buf, &_buffer[_readPos], size);
Consume(size);
return size;
}
void TC_Buffer::PeekData(void*& buf, std::size_t& size)
{
buf = ReadAddr();
size = ReadableSize();
}
void TC_Buffer::Consume(std::size_t bytes)
{
assert (_readPos + bytes <= _writePos);
_readPos += bytes;
if (IsEmpty())
Clear();
}
void TC_Buffer::AssureSpace(std::size_t needsize)
{
if (WritableSize() >= needsize)
return;
const size_t dataSize = ReadableSize();
const size_t oldCap = _capacity;
while (WritableSize() + _readPos < needsize)
{
if (_capacity < kDefaultSize)
{
_capacity = kDefaultSize;
}
else if (_capacity <= kMaxBufferSize)
{
const size_t newCapcity = RoundUp2Power(_capacity);
if (_capacity < newCapcity)
_capacity = newCapcity;
else
_capacity = 2 * newCapcity;
}
else
{
assert(false);
}
}
if (oldCap < _capacity)
{
char* tmp(new char[_capacity]);
if (dataSize != 0)
memcpy(&tmp[0], &_buffer[_readPos], dataSize);
ResetBuffer(tmp);
}
else
{
assert (_readPos > 0);
::memmove(&_buffer[0], &_buffer[_readPos], dataSize);
}
_readPos = 0;
_writePos = dataSize;
assert (needsize <= WritableSize());
}
void TC_Buffer::Shrink()
{
if (IsEmpty())
{
Clear();
_capacity = 0;
ResetBuffer();
return;
}
if (_capacity <= kDefaultSize)
return;
std::size_t oldCap = _capacity;
std::size_t dataSize = ReadableSize();
if (dataSize * 100 > oldCap * _highWaterPercent)
return;
std::size_t newCap = RoundUp2Power(dataSize);
char* tmp(new char[newCap]);
memcpy(&tmp[0], &_buffer[_readPos], dataSize);
ResetBuffer(tmp);
_capacity = newCap;
_readPos = 0;
_writePos = dataSize;
}
void TC_Buffer::Clear()
{
_readPos = _writePos = 0;
}
void TC_Buffer::Swap(TC_Buffer& buf)
{
std::swap(_readPos, buf._readPos);
std::swap(_writePos, buf._writePos);
std::swap(_capacity, buf._capacity);
std::swap(_buffer, buf._buffer);
}
void TC_Buffer::ResetBuffer(void* ptr)
{
delete[] _buffer;
_buffer = reinterpret_cast<char*>(ptr);
}
void TC_Buffer::SetHighWaterPercent(size_t percents)
{
if (percents < 10 || percents >= 100)
return;
_highWaterPercent = percents;
}
} // end namespace tars边栏推荐
- Mysql 45讲学习笔记(十三)表数据删掉一半,表文件大小不变
- Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
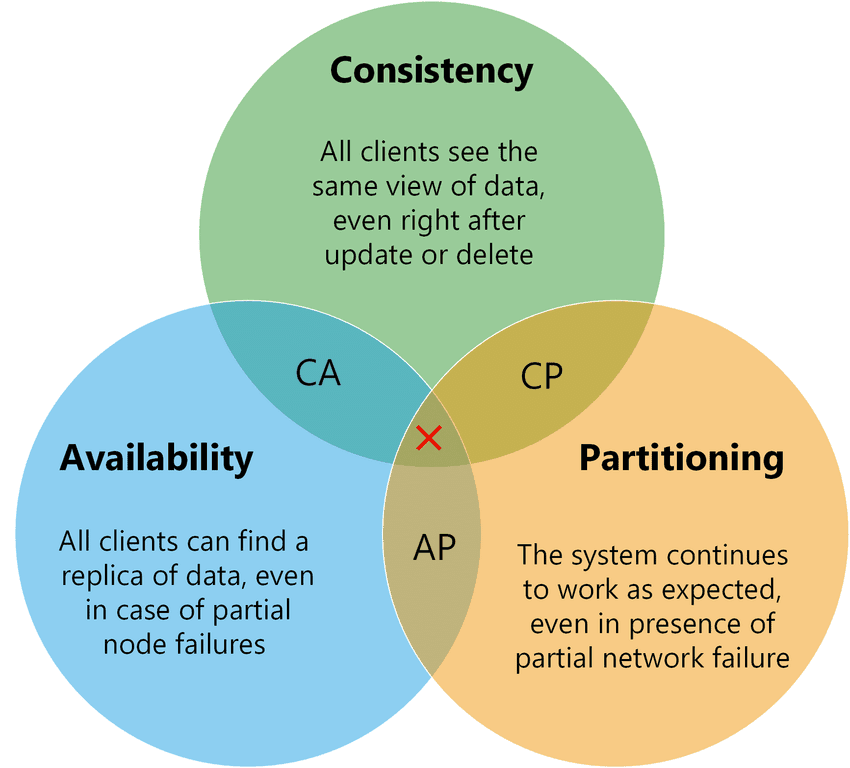
- 分布式CAP理论
- Another company raised the price of SAIC Roewe new energy products from March 1
- JSON web token -- comparison between JWT and traditional session login authentication
- How to choose the middle-aged crisis of the testing post? Stick to it or find another way out? See below
- Arcpy uses the updatelayer function to change the symbol system of the layer
- Common JS tool Libraries
- 27-31. Dependency transitivity, principle
- Variables d'environnement personnalisées uniapp
猜你喜欢
Learning multi-level structural information for small organ segmentation
Distributed cap theory
24 magicaccessorimpl can access the debugging of all methods
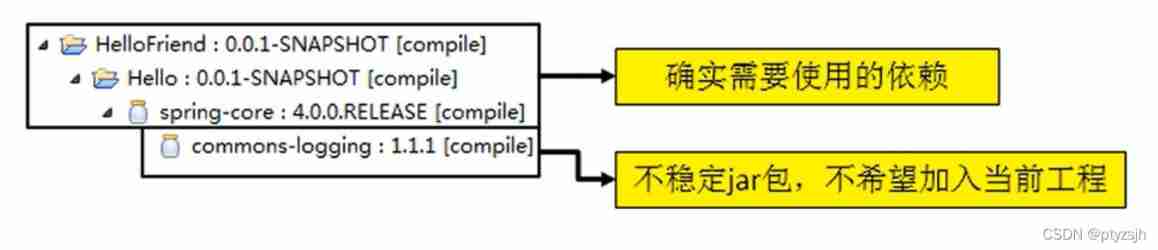
27-31. Dependency transitivity, principle
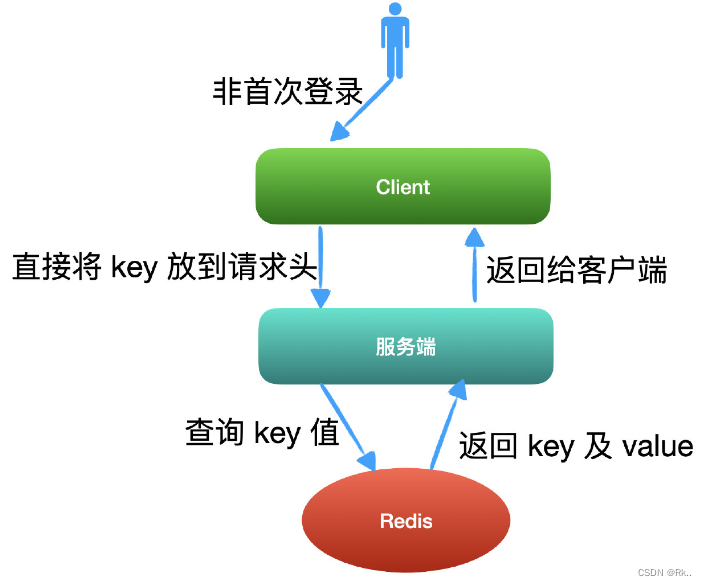
JSON Web Token----JWT和傳統session登錄認證對比
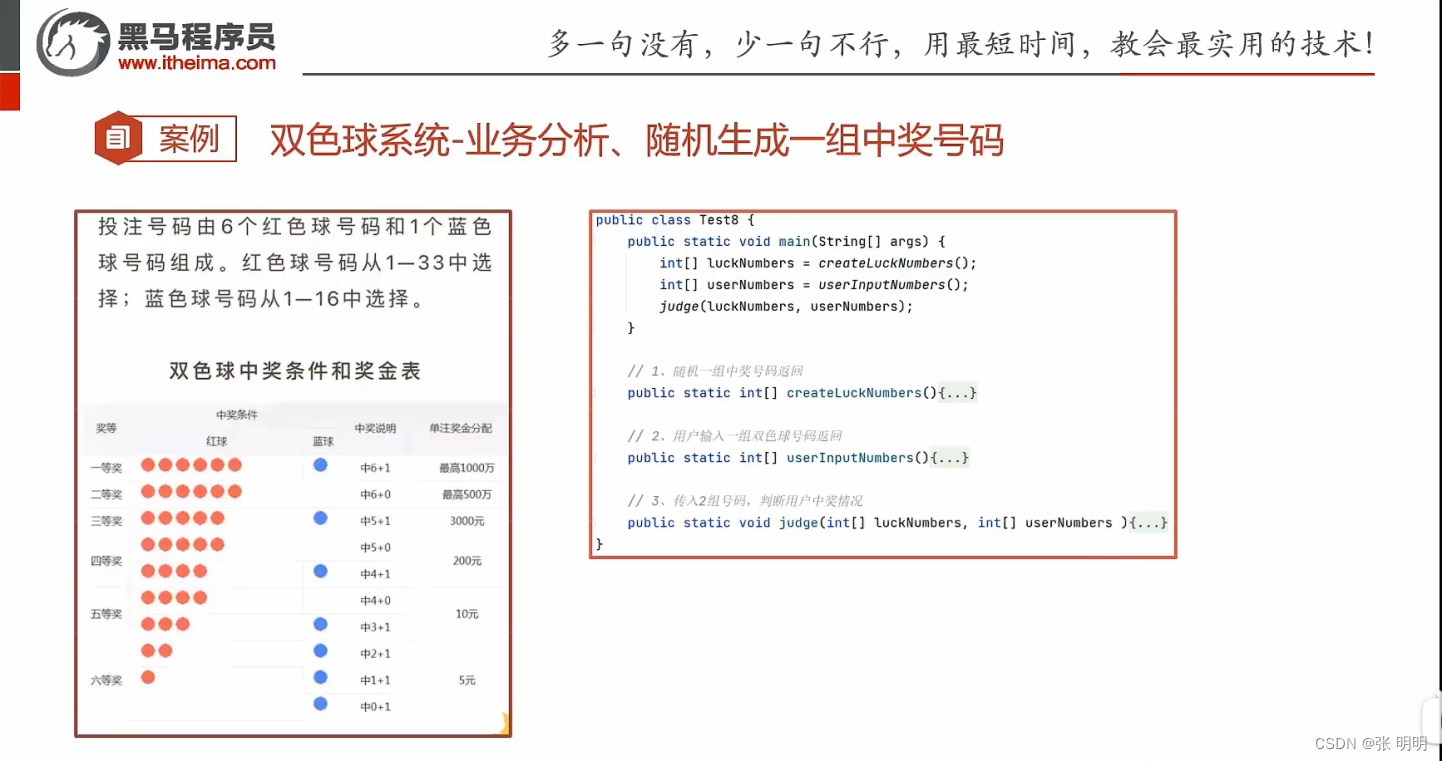
Bicolor case
QT get random color value and set label background color code
![[number theory] fast power (Euler power)](/img/1e/5d032c8f2e43f553b4543d28ea2a2d.jpg)
[number theory] fast power (Euler power)

C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
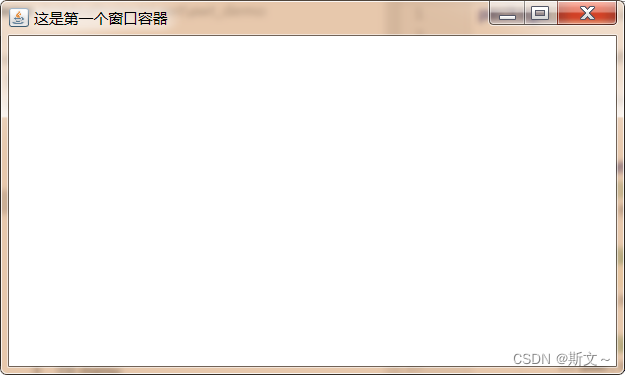
Detailed explanation of common APIs for component and container containers: frame, panel, scrollpane
随机推荐
分布式CAP理论
Invalid revision: 3.18.1-g262b901-dirty
Distributed cap theory
tars源码分析之4
Download kicad on Alibaba cloud image station
regular expression
7. Agency mode
Common JS tool Libraries
How to realize multi account login of video platform members
List of top ten professional skills required for data science work
Appium foundation - appium installation (II)
[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)
Which water in the environment needs water quality monitoring
AWT common components, FileDialog file selection box
STM32 单片机ADC 电压计算
11. Dimitt's law
17-18. Dependency scope and life cycle plug-ins
How to choose the middle-aged crisis of the testing post? Stick to it or find another way out? See below
What is a spotlight effect?
Sort list tool class, which can sort strings