当前位置:网站首页>Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
2022-07-04 06:50:00 【CNSINDA_ HK】
This is the largest source code leak ever . Microsoft 、Adobe、 lenovo 、AMD、 qualcomm 、 mediatek 、 Ge 、 nintendo 、 Disney 、 Huawei 、 Heisi et al 50 Technology companies have been involved in the recent disclosure of source code leaks .
For company products , Source code is the embodiment of life , Master the writing method , You can copy the same program , Or find the vulnerability of the program by reading the source code and carry out arbitrary attacks . Once the source code is leaked , The potential harm is huge . therefore , When enterprises face source code leakage , Whether we should reflect on whether our current source code protection is not perfect ?
The cause is suspected to be improper use of configuration Devops Tools
This large-scale source code leak was caused by Bank Security The security researchers found that , The leaked source code was released in GitLab In the last public repository , And marked as “exconfidential” ( Top secret ), as well as “Confidential & Proprietary”( A secret & proper ), The repository contains approximately more than 50 Source code of Companies .

edit
Add picture comments , No more than 140 word ( Optional )
A Swiss software development engineer uploaded these repositories , And then in their own Twitter The access link is posted on the account . Although he has tried to delete the code , And contact the relevant companies involved , But because these source codes are made public , Anyone can visit , This finds vulnerabilities for network attackers 、 Stealing confidential information of enterprises has buried hidden dangers .
Why did it cause such a large-scale source code leak ?
The cause is suspected to be the use of misconfigured Devops The tool exposes the source code . There are not a few security incidents caused by improper configuration . Amazon AWS S3 The improper configuration of storage barrels caused a large-scale data leakage event, which must be remembered by everyone . Of course, there are other reasons for source code leakage , For example, hacker attack 、 Staff operation errors, etc . For example, Nintendo was recently exposed to be hacked, resulting in source code leakage .

edit
Add picture comments , No more than 140 word ( Optional )
Besides , Events caused by employees' operational errors , For example, the source code of Dajiang is leaked .2019 year , The former employee of Dajiang disclosed the company's source code , The Shenzhen court sentenced the former employee of Dajiang to six months' imprisonment for the crime of infringing trade secrets , Impose a fine 20 Thousands of yuan . And the leaked code , Has been used in the company's agricultural UAV products , Practical . Although the company has taken reasonable confidentiality measures , But the incident still caused economic losses to Xinjiang 116.4 RMB 10,000 yuan .
The game field is the hardest hit area of source code leakage . Except for Nintendo's source code leak ,2019 year Valve There was a major leak , Someone leaked it 《CS:GO》 and 《 Team Fortress 2》 Source code , And provide a download link . Responsible for 《 Team Fortress 2》 The player community for volunteer maintenance has been closed indefinitely .

edit
Add picture comments , No more than 140 word ( Optional )
2019 year 4 month ,B Station entire website backstage project source code divulges , also “ Many user passwords are hard coded in the code , Anyone can use .” On the day B The stock price of the station fell 3.27%. Although soon banned ,B The station has also given an alarm , But many netizens have cloned the code base , The hidden danger has been buried .

edit
Add picture comments , No more than 140 word ( Optional )
How should enterprises protect source code ?
The importance of source code to enterprises is self-evident , Therefore, it is very important to strengthen source code protection . From the source code itself 、 The authority of internal enterprise personnel and good monitoring and auditing , Further strengthen the security of important source code of the enterprise .

edit
Add picture comments , No more than 140 word ( Optional )
One 、 Grade the source code , Ensure and clarify the protection measures of important source code
The internal source code of the enterprise has priority , Identify which core code needs to be protected . After clarifying the importance classification of source code , You can encrypt important source code , Build a core data management platform . At present, there are two ways to encrypt the source code : One is physical “ Source code encryption ”, One is software source code encryption .
Physical property “ Source code encryption ” It means cutting off the Internet , Seal off U Or lock the chassis , Let developers in a closed state . This method can achieve results , The drawback is that if it is sealed U mouth , It will have a great impact on the work use of employees , Greatly reduce the efficiency of work .
Software source code encryption refers to the protection of source code through software . At present, the most popular source code encryption software mechanism on the market is a kind of software that encrypts the operating environment of developers , There is no need to modify any hardware , The source code of developers can only be stored in the company , Unable to take out the encrypted space . If you want to take out the documents, you need to go through the approval process .
Two 、 Fine grained access control , Restrict the authority of employees
Although the company does a good job of source code encryption , However, it is still unable to prevent the safety risks caused by internal employees . For example, the former employee of Dajiang who leaked the source code and was sentenced is a case .
For external threats , Technology can indeed be used to defend . But for internal “ people ” On the one hand, we need to restrict employees' access rights or virtual access , On the other hand, improve the safety awareness and property right awareness of employees .
Data management from security technology , Such as data encryption 、 Data leakage prevention 、 Data traceability 、 Access control . meanwhile , Carry out decentralized management , Divide data levels and encrypt storage , Different levels of employees , Access rights are different , General employees cannot access core data , Minimize the risk of core data leakage .
When employees are on the job , Confidentiality agreement and non compete agreement should be signed . This includes the company's existing 、 And all product technology development information including source code under development or conception , Employees are not allowed to disclose .
Strengthen employees' awareness of confidentiality and relevant laws , Clear responsibilities , Let employees know the legal responsibility they need to bear once a leak occurs . Or through corporate culture education , Let employees understand the importance of source code data to enterprise development , At the same time, improve the awareness of safety protection .
3、 ... and 、 Do a good job of monitoring and safety audit
Enterprises should cooperate with the management system 、 Confidentiality agreement 、 The audit log , Make sure it's well documented 、 According to the can depend on . At present, most customers' safety concerns about software products are basically concentrated on the late stage of development , Introduce in the testing phase . Commonly used software risk assessment 、 Vulnerability scanning 、 Penetration testing is carried out after the completion of software development .
Usually, very little time is reserved at this stage , Not only is it difficult to repair , Repair 、 The cost of testing is extremely high , And there are a lot of false positives and false positives . When problems are found through post test , Manual code review to find the location of the vulnerability code , Often inefficient 、 Low accuracy 、 Unable to locate the specific problem code line .
therefore , Enterprises should intervene in safety from the early stage of development , Do a good job of safety audit , Locate the problem code line quickly and accurately , Manage vulnerabilities in real time , Security protection at the source level , Prevent improper configuration 、 Software writing exists bug And other problems caused by source code leakage .
Four 、 Introduce compulsory specifications for source code anti disclosure software
SDC Sandbox leak proof products , Adopt kernel defense in depth , It is a driver level anti disclosure Software . Do not encrypt files , A sandbox is like a container , The container contains our confidential information . The documents we work on are all in sandboxes . The sandbox is completely isolated from ordinary computers . You might ask , What if I want to access the Internet , All programs to access the Internet are launched from the tray , Such as browser , Chat software, etc .SDC The sandbox is divided into the following parts : The management end , Confidential end , Documents are sent out , client .
The management end : Sandbox Control Center , Control all clients . The control of the client covers all aspects . Let me give you a few control functions : Reverse screenshot When someone wants to view some confidential information of the company remotely to the employee's computer ,SDC The client will control the remote software , Remote people see a black screen . But the computers on the staff side are in normal use . If you can control, you can let go . clipboard In sandbox mode, employees want to copy and paste company data such as files to the Internet through the clipboard ,SDC Sandbox is controlled , You can control the maximum number of clipping words .
Confidential end : Escort the server , Ordinary computers do not have access to confidential servers . Only sandbox computers can access , Do not encrypt the company's data , Protect data to the greatest extent .
client : Normal mode and sandbox mode . All software installation should be in sandbox mode . Work must be in sandbox mode , Because all the working data are on the encrypted disk , Sandbox can only be accessed in encrypted mode . In sandbox mode, it is isolated from the outside world . To access the Internet, only programs launched from the tray can , And follow the principle of only getting in and not getting out , Can get files from the Internet to the sandbox computer , However, to send documents from this machine to the Internet, you have to go through document approval .
Documents are sent out : A file distribution system is installed on a computer . The of this computer ip That is, the address where the document is sent out . Each sandbox employee matches an account number for sending out files . The specific approval method is not cumbersome here .

Edit switch to center
Add picture comments , No more than 140 word ( Optional )
边栏推荐
- Tar source code analysis 9
- tars源码分析之8
- [GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
- Data analysis notes 09
- Mysql 45讲学习笔记(六)全局锁
- Check and display one column in the known table column
- 移动适配:vw/vh
- Selection (021) - what is the output of the following code?
- What is the sheji principle?
- How can the old version of commonly used SQL be migrated to the new version?
猜你喜欢

Matlab remainder
The solution of win11 taskbar right click without Task Manager - add win11 taskbar right click function

云Redis 有什么用? 云redis怎么用?
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Variables d'environnement personnalisées uniapp
selenium驱动IE常见问题解决Message: Currently focused window has been closed.
![[network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA](/img/71/1d6179921ae84b1ba61ed094e592ff.png)
[network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
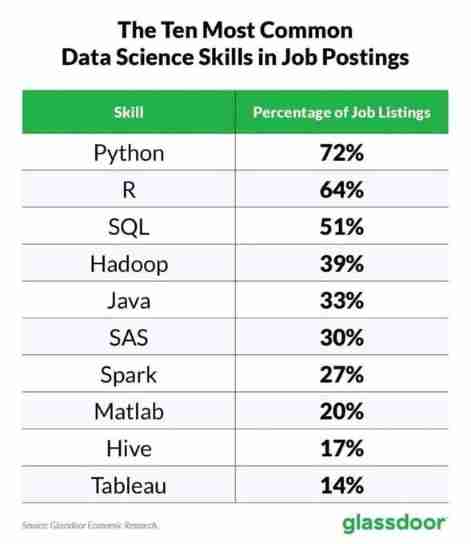
List of top ten professional skills required for data science work
【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
随机推荐
leetcode 310. Minimum Height Trees
About how idea sets up shortcut key sets
27-31. Dependency transitivity, principle
Boast about Devops
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Check and display one column in the known table column
Common usage of time library
[FPGA tutorial case 7] design and implementation of counter based on Verilog
Tar source code analysis 8
How does the recv of TCP socket receive messages of specified length?
Overview of convolutional neural network structure optimization
Bottom problem of figure
Redis interview question set
Tree DP
[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)
tars源码分析之8
Mysql 45讲学习笔记(十四)count(*)
Software keywords and process information intercepted by Golden Shield video player
【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
Which water in the environment needs water quality monitoring