当前位置:网站首页>Data double write consistency between redis and MySQL
Data double write consistency between redis and MySQL
2022-07-04 06:57:00 【No trace after wind 2018】
Redis And MySQL Data double write consistency
1. What is? Redis And MySQL Data double write consistency

2. Synchronous write through and asynchronous cache

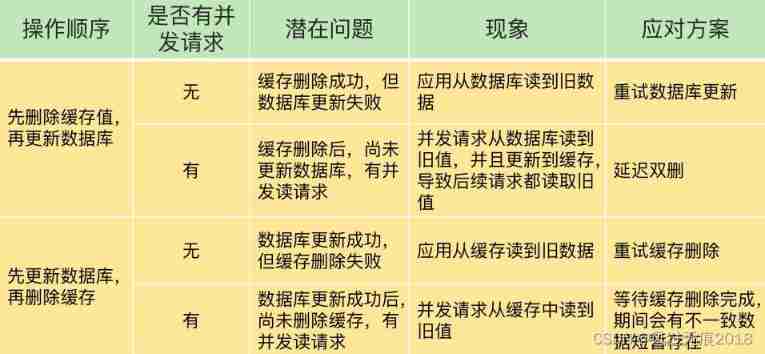
3. Several update strategies for database and cache consistency *
Don't allow : Update cache first , The strategy of updating the database
1) Update the database first , Update the cache again
Generally do not use Update the database first , Update the cache again , If Redis Something unusual happened , There will be a problem that the cache reads dirty data
1 To update mysql The inventory of a commodity , The current stock of goods is 100, Updated to 99 individual .
2 To update mysql It is amended as follows 99 success , And then update redis.
3 At this time, it is assumed that the exception appears , to update redis failed , This leads to mysql The inventory inside is 99 and redis Inside is still 100 .
4 The above happened , Will make the database and cache redis The data inside is inconsistent , Read dirty data
2) So let's delete the cache , Update the database
Low concurrent , Small plant If the database update fails , Lead to B When a thread requests to access the cache again , Find out redis There's no data in it , Cache missing , Read again mysql when , Read old value from database
Low concurrent : Write the old data to the cache
High concurrency : Cache breakdown
technological process :
(1) request A Write operation , After deleting the cache , The work is in progress …A It hasn't been completely updated yet
(2) request B starts , Inquire about redis Found cache does not exist
(3) request B continue , Go to the database and get myslq The old value in
(4) request B Write the old value to redis cache
(5) request A Write the new value to mysql database
This leads to inconsistencies .
solve : Delay double delete strategy 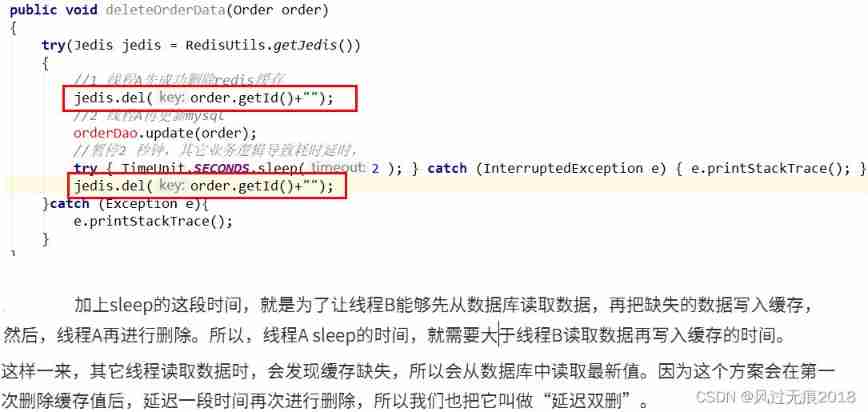
3) Update the database first , Delete the cache
If the cache deletion fails or it is too late , Cause a request to visit again redis Cache hit , What is read is the old cache value .
Enterprises often use
Solution :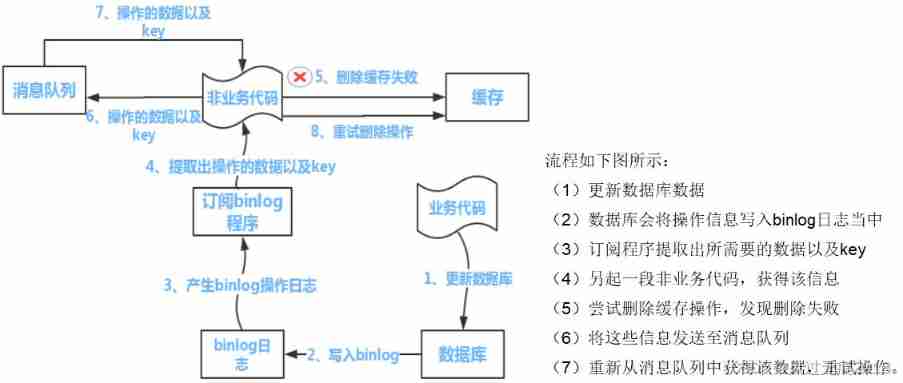
1 The cache value to be deleted or the database value to be updated can be temporarily stored in the message queue ( For example, using Kafka/RabbitMQ etc. ).
2 When the program fails to successfully delete the cache value or update the database value , These values can be re read from the message queue , Then delete or update again .
3 If you can successfully delete or update , We need to remove these values from the message queue , So as not to repeat the operation , here , We can also ensure that the database and cached data are consistent , Otherwise, you need to try again
4 If you try again more than a certain number of times and still fail , We need to send an error message to the business layer , Inform the operation and maintenance personnel .
summary
边栏推荐
- List of top ten professional skills required for data science work
- The important role of host reinforcement concept in medical industry
- 高薪程序员&面试题精讲系列119之Redis如何实现分布式锁?
- Shopping malls, storerooms, flat display, user-defined maps can also be played like this!
- The most effective futures trend strategy: futures reverse merchandising
- Latex中的单引号,双引号如何输入?
- regular expression
- thread priority
- 《国民经济行业分类GB/T 4754—2017》官网下载地址
- 响应式——媒体查询
猜你喜欢
Vulhub vulnerability recurrence 77_ zabbix
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
响应式——媒体查询
图的底部问题
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Knowledge payment applet dream vending machine V2

Another company raised the price of SAIC Roewe new energy products from March 1
校园网络问题

Responsive - media query
What is industrial computer encryption and how to do it
随机推荐
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
centos8安装mysql.7 无法开机启动
MySQL 45 learning notes (XI) how to index string fields
Cervical vertebra, beriberi
Mobile adaptation: vw/vh
what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
金盾视频播放器拦截的软件关键词和进程信息
Check and display one column in the known table column
BasicVSR++: Improving Video Super-Resolutionwith Enhanced Propagation and Alignment
Tar source code analysis 6
Flink memory model, network buffer, memory tuning, troubleshooting
Selenium driver ie common problem solving message: currently focused window has been closed
Mysql 45讲学习笔记(十一)字符串字段怎么加索引
Modify TCP timestamp to optimize transmission performance
MySQL 45 lecture learning notes (VII) line lock
Paddleocr prompt error: can not import AVX core while this file exists: xxx\paddle\fluid\core_ avx
Tar source code analysis Part 2
校园网络问题
com. alibaba. nacos. api. exception. NacosException
Su Weijie, a member of Qingyuan Association and an assistant professor at the University of Pennsylvania, won the first Siam Youth Award for data science, focusing on privacy data protection, etc