边栏推荐
- com. alibaba. nacos. api. exception. NacosException
- The number of patent applications in China has again surpassed that of the United States and Japan, ranking first in the world for 11 consecutive years
- 2022, peut - être la meilleure année économique de la prochaine décennie, avez - vous obtenu votre diplôme en 2022? Comment est - ce prévu après la remise des diplômes?
- CORS is not intended to protect API endpoints - nikofischer
- Selection (023) - what are the three stages of event propagation?
- selenium IDE插件下载安装使用教程
- Selection (022) - what is the output of the following code?
- Cervical vertebra, beriberi
- [Valentine's day] - you can change your love and write down your lover's name
- tars源码分析之9
猜你喜欢
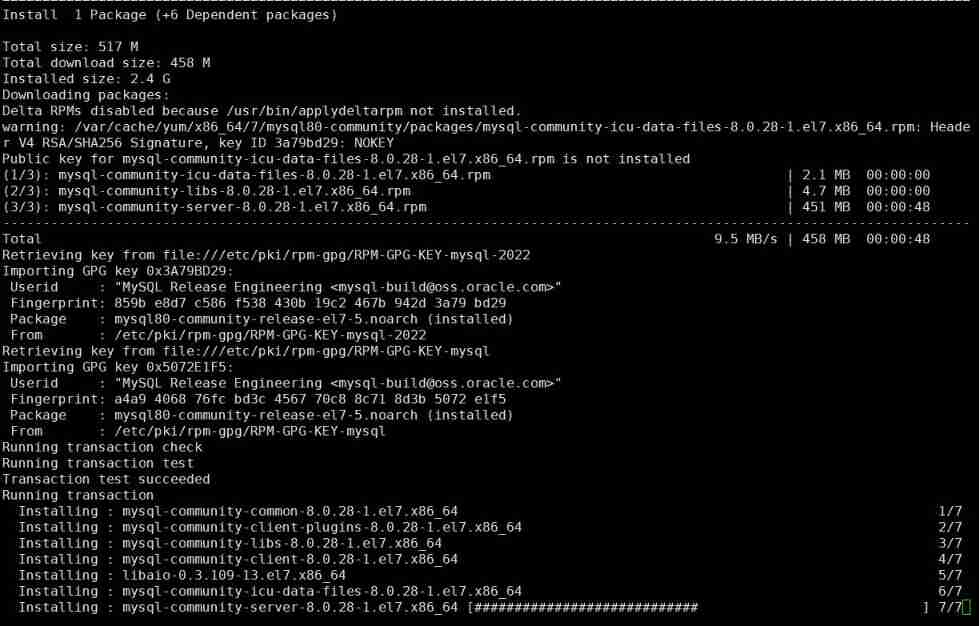
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0

Boosting the Performance of Video Compression Artifact Reduction with Reference Frame Proposals and
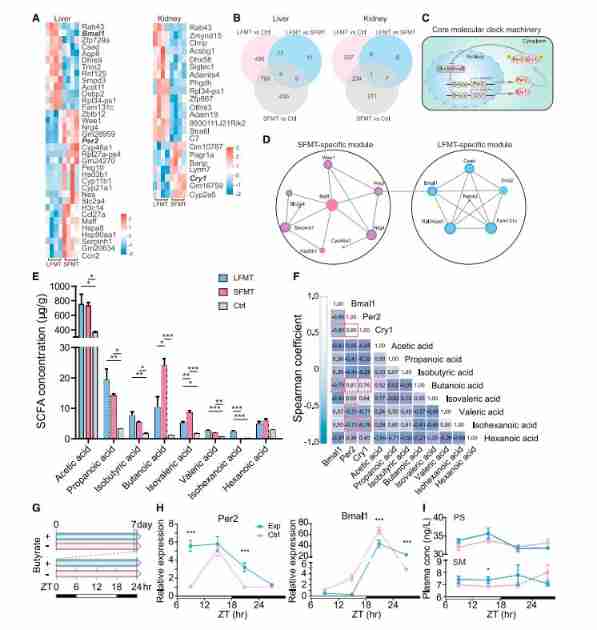
Cell reports: Wei Fuwen group of the Institute of zoology, Chinese Academy of Sciences analyzes the function of seasonal changes in the intestinal flora of giant pandas
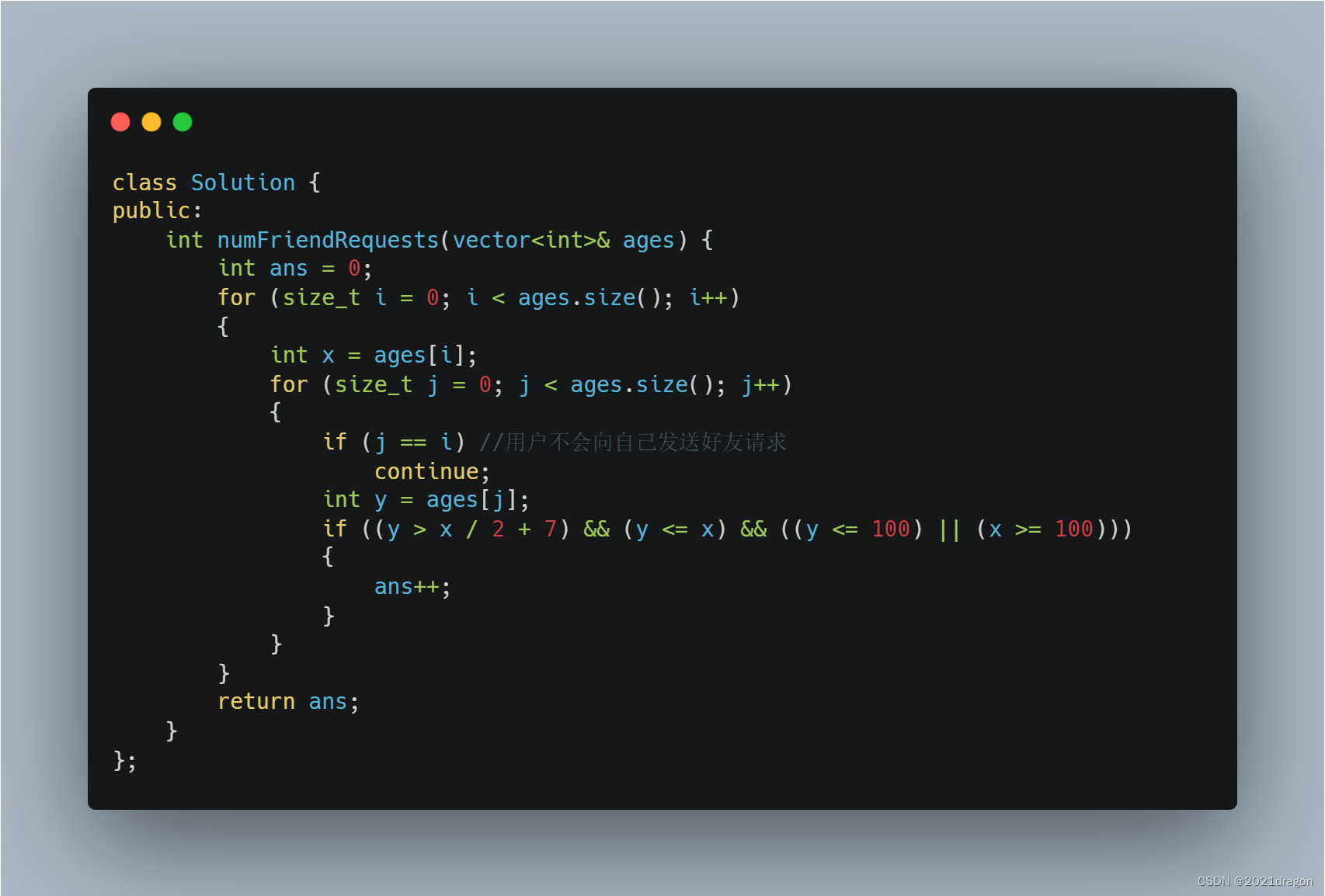
leetcode825. Age appropriate friends
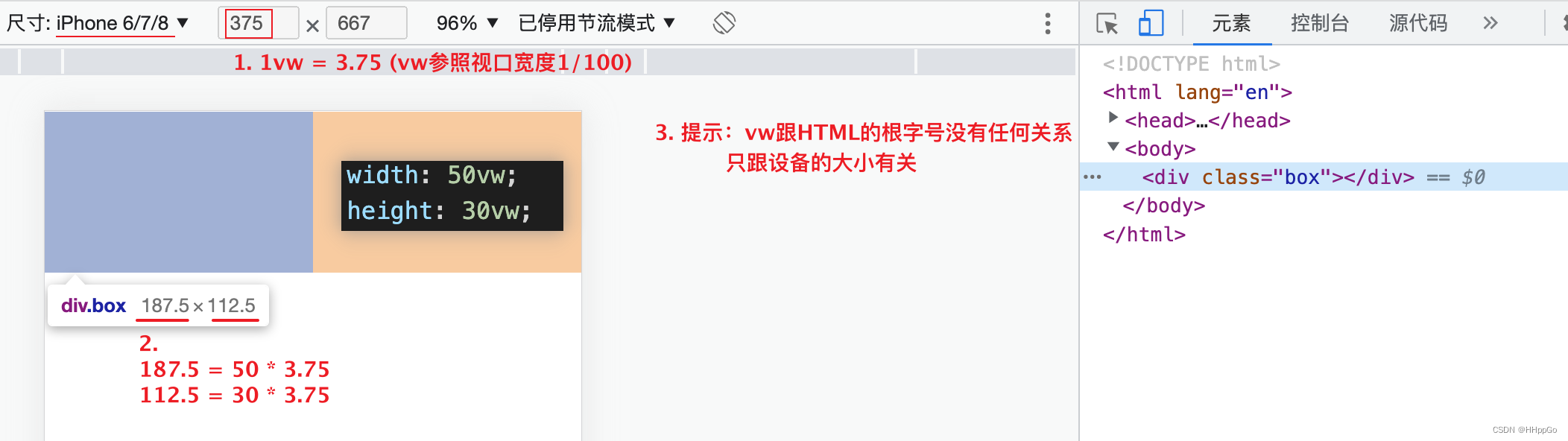
Mobile adaptation: vw/vh

The cloud native programming challenge ended, and Alibaba cloud launched the first white paper on application liveliness technology in the field of cloud native
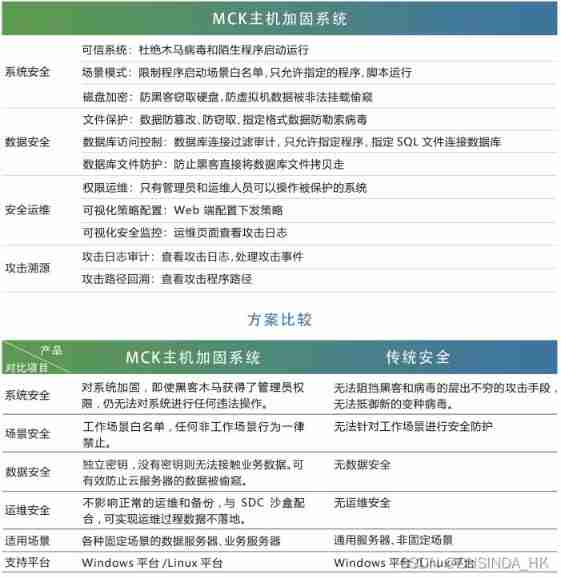
Industrial computer anti-virus
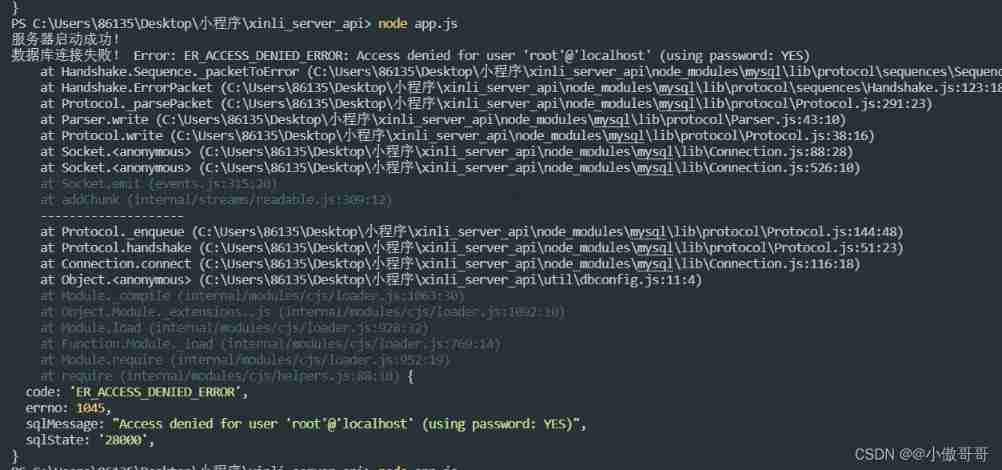
Node connection MySQL access denied for user 'root' @ 'localhost' (using password: yes
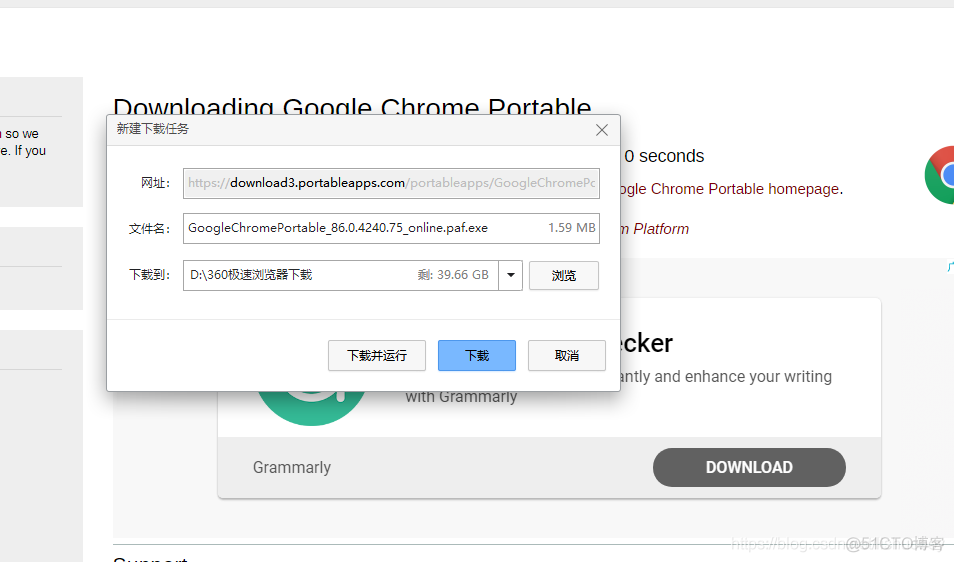
GoogleChromePortable 谷歌chrome浏览器便携版官网下载方式
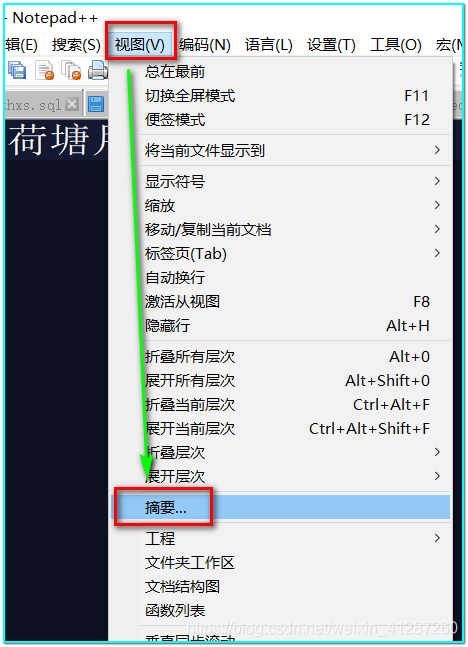
How notepad++ counts words
随机推荐
tars源码分析之7
What is tweeman's law?
How can the old version of commonly used SQL be migrated to the new version?
Boast about Devops
Set JTAG fuc invalid to normal IO port
Analysis of tars source code 1
图的底部问题
Lottery system test report
Check and display one column in the known table column
Redis - detailed explanation of cache avalanche, cache penetration and cache breakdown
Explain in one sentence what social proof is
tcp socket 的 recv 如何接收指定长度消息?
2022年6月小结
The final week, I split
Computer connects raspberry pie remotely through putty
Highly paid programmers & interview questions: how does redis of series 119 realize distributed locks?
《国民经济行业分类GB/T 4754—2017》官网下载地址
"Sword finger offer" 2nd Edition - force button brush question
【FPGA教程案例8】基于verilog的分频器设计与实现
2022年,或许是未来10年经济最好的一年,2022年你毕业了吗?毕业后是怎么计划的?