当前位置:网站首页>Bottom problem of figure
Bottom problem of figure
2022-07-04 06:47:00 【chengqiuming】
One Link to original question
The Bottom of a Graph - POJ 2553 - Virtual Judge https://vjudge.net/problem/POJ-2553
https://vjudge.net/problem/POJ-2553
Two Input and output
1 Input
The input contains several test cases , Each test case corresponds to a directed graph G, Each test case is expressed as an integer v Start , Diagram G Of nodes , Node number is 1~v. Next, nonnegative integers e, And then there was e To number v1、w1、......ve、we, among (vi,wi) To represent an edge . The last test case is followed by 0.
2 Output
Output all at the bottom of the diagram in a single line sink node . without , Then output a blank line .
3、 ... and Input and output examples
1 sample input
3 3
1 3 2 3 3 1
2 1
1 2
0
2 sample output
1 3
2
Four Problem analysis
sample input 1, The constructed figure is as follows , In the figure sink The node is 1 and 3.
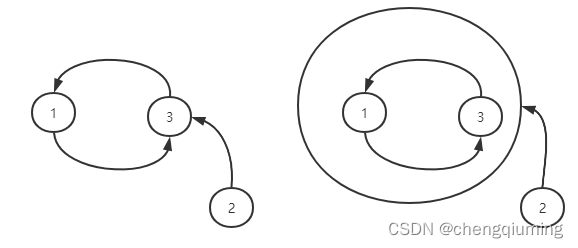
Ideas : Find the strongly connected component , And shrink points for strongly connected components , Calculate the output of the shrink point , The degree of 0 All nodes in the strongly connected component of are sink node .
5、 ... and Algorithm design
1 First use Targan The algorithm solves the strongly connected components of a directed graph , Mark the strongly connected component number .
2 Check each node u Every adjacent point of v, If the strongly connected components are different , Will u The output of the connected component number of plus 1.
3 Check each node u, If the degree of its connected component number is 0, Then output the node .
6、 ... and Code
package graph.poj553;
import java.util.Scanner;
import java.util.Stack;
public class POJ2553 {
static final int maxn = 1000 + 5;
static int n;
static int m;
static int head[];
static int belong[];
static int out[];
static int cnt;
static int id;
static int low[];
static int dfn[];
static int num;
static Edge e[] = new Edge[maxn << 1];
static Stack<Integer> s = new Stack<>();
static boolean ins[] = new boolean[maxn];
static {
for (int i = 0; i < e.length; i++) {
e[i] = new Edge();
}
}
static void add(int u, int v) { // Add an edge u--v
e[++cnt].next = head[u];
e[cnt].to = v;
head[u] = cnt;
}
static void tarjan(int u) { // Find the strongly connected component
low[u] = dfn[u] = ++num;
ins[u] = true;
s.push(u);
for (int i = head[u]; i != 0; i = e[i].next) {
int v = e[i].to;
if (dfn[v] == 0) {
tarjan(v);
low[u] = Math.min(low[u], low[v]);
} else if (ins[v]) {
low[u] = Math.min(low[u], dfn[v]);
}
}
if (low[u] == dfn[u]) {
int v;
do {
v = s.peek();
s.pop();
belong[v] = id;
ins[v] = false;
} while (v != u);
id++;
}
}
static void init() {
head = new int[maxn];
low = new int[maxn];
dfn = new int[maxn];
ins = new boolean[maxn];
belong = new int[maxn];
out = new int[maxn];
cnt = num = 0;
id = 1;
}
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
while (true) {
n = scanner.nextInt();
if (n == 0) {
return;
}
m = scanner.nextInt();
init();
while (m-- != 0) {
int u, v;
u = scanner.nextInt();
v = scanner.nextInt();
add(u, v);
}
for (int i = 1; i <= n; i++)
if (dfn[i] == 0)
tarjan(i);
for (int u = 1; u <= n; u++)
for (int i = head[u]; i > 0; i = e[i].next) {
int v = e[i].to;
if (belong[u] != belong[v])
out[belong[u]]++;
}
int flag = 1;
System.out.println();
for (int i = 1; i <= n; i++)
if (out[belong[i]] == 0) {
if (flag == 1)
flag = 0;
else
System.out.print(" ");
System.out.print(i);
}
}
}
}
class Edge {
int to;
int next;
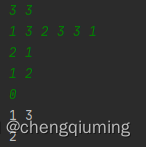
}7、 ... and test
Green is the input , White is the output
边栏推荐
- Overview of convolutional neural network structure optimization
- tars源码分析之2
- STM32 单片机ADC 电压计算
- Realize IIC data / instruction interaction with micro batg135
- Responsive mobile web test questions
- Download address of the official website of national economic industry classification gb/t 4754-2017
- 【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
- Appium foundation - appium installation (II)
- Summary of June 2022
- Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
猜你喜欢
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0

ORICO ORICO outdoor power experience, lightweight and portable, the most convenient office charging station
Uniapp custom environment variables
树形dp
期末周,我裂开
R统计绘图-随机森林分类分析及物种丰度差异检验组合图
leetcode 310. Minimum Height Trees
MySQL learning notes 3 - JDBC
![[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph](/img/5e/7ce21dd544aacf23b4ceef1ec547fd.png)
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
Arcpy uses the updatelayer function to change the symbol system of the layer
随机推荐
js 常用时间处理函数
Cervical vertebra, beriberi
Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)
uniapp 自定義環境變量
selenium IDE插件下载安装使用教程
【GF(q)+LDPC】基于二值图GF(q)域的规则LDPC编译码设计与matlab仿真
MySQL learning notes 3 - JDBC
How does the inner roll break?
Mysql 45讲学习笔记(六)全局锁
tars源码分析之4
JS common time processing functions
STM32 单片机ADC 电压计算
Uniapp custom environment variables
抽奖系统测试报告
How does the recv of TCP socket receive messages of specified length?
Overview of convolutional neural network structure optimization
Mobile adaptation: vw/vh
移动适配:vw/vh
Tar source code analysis 6
Appium基础 — APPium安装(二)