当前位置:网站首页>【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
2022-07-04 06:40:00 【fpga和matlab】
1.软件版本
vivado2019.2
2.系统原理
先将电脑的IP地址设置为: 192.168.0.3。如下所示:
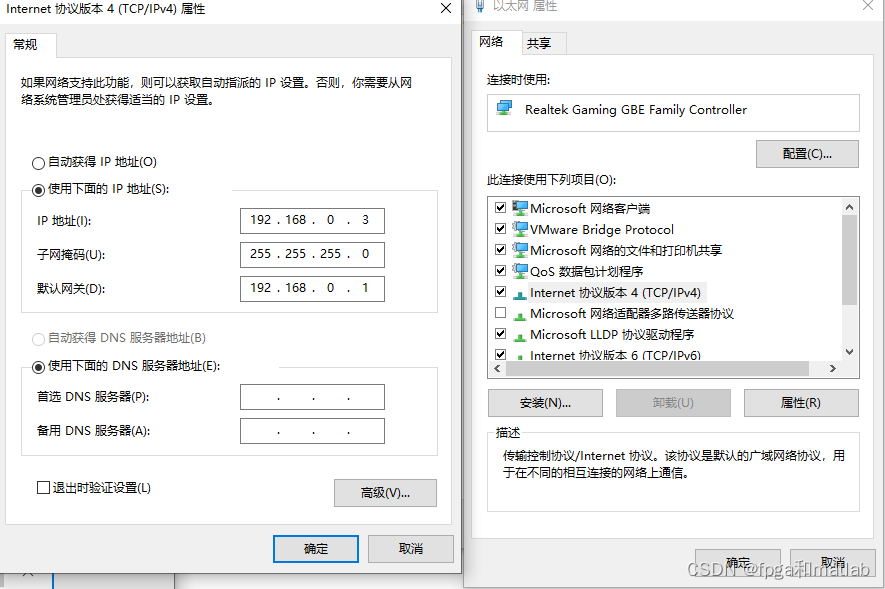
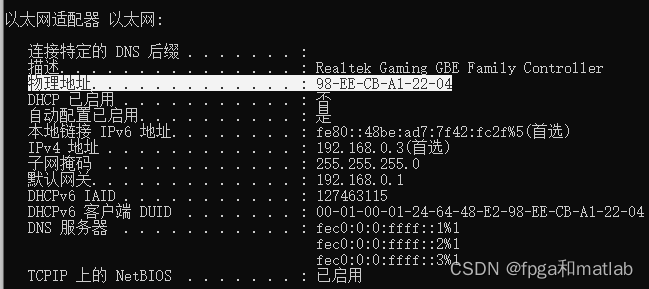
修改后,cmd中运行如下指令

可以查看PC的IP和MAC
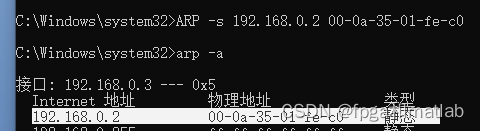
然后到windows>system32>cmd.exe,右击,以管理员进行运行,然后进行PC和FPGA的mac地址的绑定:
边栏推荐
- 11. Dimitt's law
- Mysql 45讲学习笔记(七)行锁
- [problem record] 03 connect to MySQL database prompt: 1040 too many connections
- InputStream/OutputStream(文件的输入输出)
- MySQL 45 lecture learning notes (XIII) delete half of the table data, and the table file size remains the same
- Redis面试题集
- How to help others effectively
- 颈椎、脚气
- 2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
- Arcpy 利用updatelayer函数改变图层的符号系统
猜你喜欢
Cloud native - SSH article that must be read on the cloud (commonly used for remote login to ECS)

C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing

Download kicad on Alibaba cloud image station
![[problem record] 03 connect to MySQL database prompt: 1040 too many connections](/img/bb/4d8d202cf5c6e556bc860a734e5934.png)
[problem record] 03 connect to MySQL database prompt: 1040 too many connections
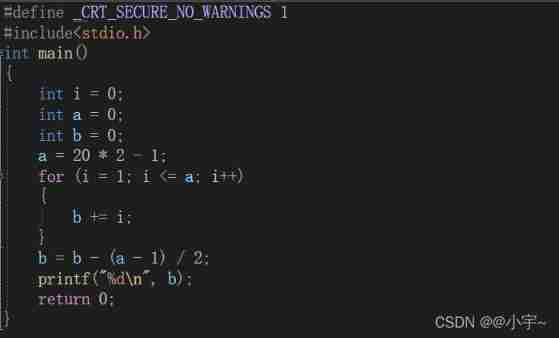
C language - Blue Bridge Cup - Snake filling

Overview of convolutional neural network structure optimization
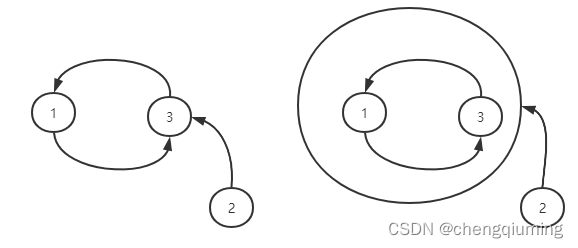
图的底部问题
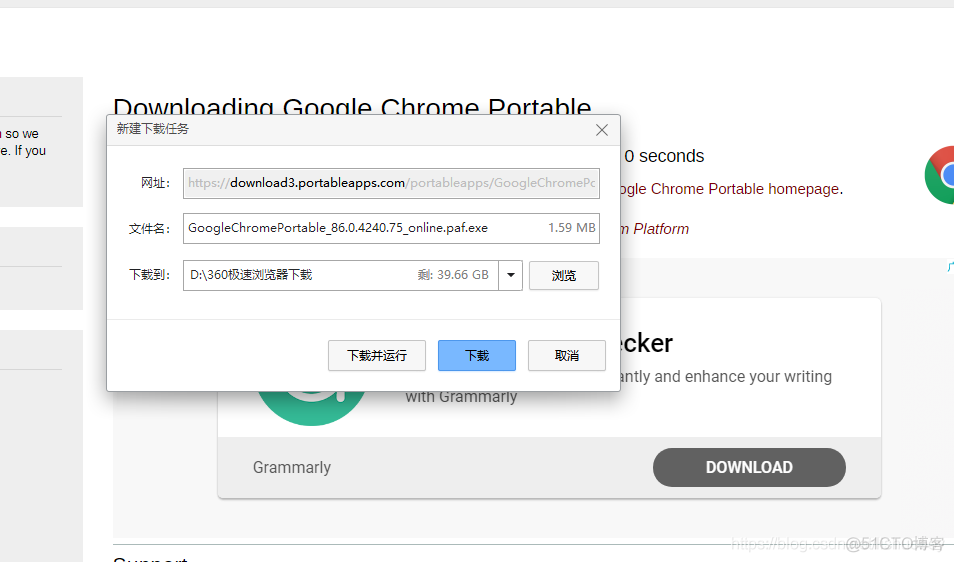
GoogleChromePortable 谷歌chrome浏览器便携版官网下载方式
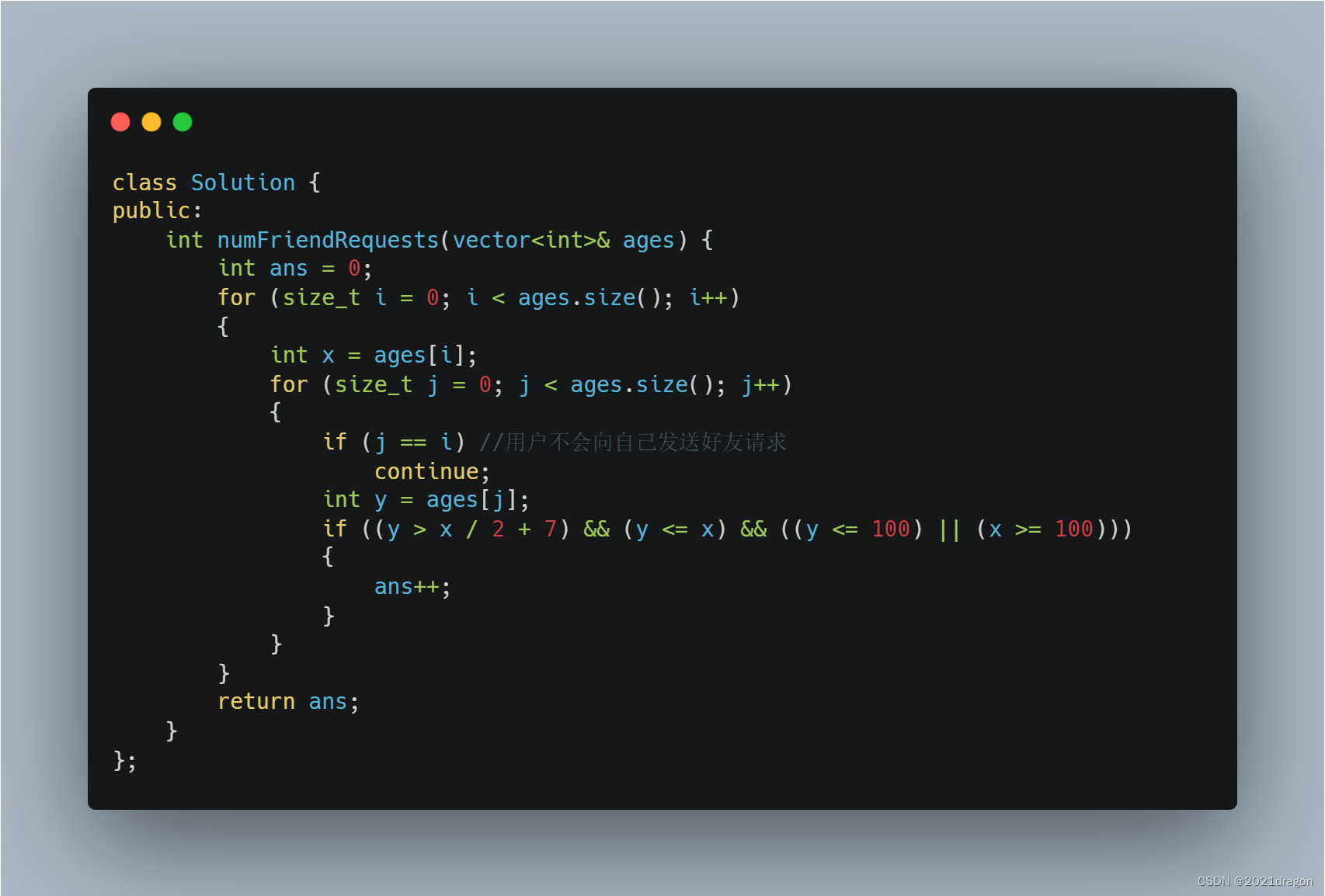
leetcode825. 适龄的朋友
![[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)](/img/03/2b37e63d0d482d5020b7421ac974cb.jpg)
[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)
随机推荐
Background and current situation of domestic CDN acceleration
2022 Xinjiang's latest eight members (Safety Officer) simulated examination questions and answers
《ClickHouse原理解析与应用实践》读书笔记(4)
Mysql 45讲学习笔记(十二)MySQL会“抖”一下
How to help others effectively
tars源码分析之7
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
STC8H开发(十二): I2C驱动AT24C08,AT24C32系列EEPROM存储
MySQL 45 lecture learning notes (12) MySQL will "shake" for a while
雲原生——上雲必讀之SSH篇(常用於遠程登錄雲服務器)
Considerations for testing a website
C language - Blue Bridge Cup - Snake filling
What is tweeman's law?
How does the inner roll break?
Mysql 45讲学习笔记(十三)表数据删掉一半,表文件大小不变
C réaliser des jeux de serpents gourmands
STC8H开发(十二): I2C驱动AT24C08,AT24C32系列EEPROM存储
Mysql 45讲学习笔记(十四)count(*)
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
Summary of leetcode BFS question brushing