当前位置:网站首页>Computer connects raspberry pie remotely through putty
Computer connects raspberry pie remotely through putty
2022-07-04 06:59:00 【Thinking and Practice】
Make sure your computer and your raspberry pie are connected to the same hotspot
1. Connect your raspberry pie to your computer and your mobile hotspot
Raspberry pie is configured using the command line wifi Connect - Bili, Bili (bilibili.com)
Input instructions see wlan0 Of RX And TX No 0 It means that the connection to the hotspot is successful
[email protected]:~$ sudo ifconfig wlan0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.243.125 netmask 255.255.255.0 broadcast 192.168.243.255
inet6 2409:8914:244:b7f:1f05:f093:abf3:30ce prefixlen 64 scopeid 0x0<global>
inet6 fe80::ceda:dbd1:2893:9ff9 prefixlen 64 scopeid 0x20<link>
ether dc:a6:32:29:13:8d txqueuelen 1000 (Ethernet)
RX packets 866 bytes 106471 (103.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 478 bytes 71486 (69.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Determine if you can access Internet, Sure Ping www.baidu.com
[email protected]:~$ ping www.baidu.com
PING www.a.shifen.com (39.156.66.18) 56(84) bytes of data.
64 bytes from 39.156.66.18 (39.156.66.18): icmp_seq=1 ttl=50 time=44.7 ms
64 bytes from 39.156.66.18 (39.156.66.18): icmp_seq=2 ttl=50 time=58.7 ms
64 bytes from 39.156.66.18 (39.156.66.18): icmp_seq=3 ttl=50 time=59.0 ms
64 bytes from 39.156.66.18 (39.156.66.18): icmp_seq=4 ttl=50 time=41.8 ms
64 bytes from 39.156.66.18 (39.156.66.18): icmp_seq=5 ttl=50 time=42.4 ms
2. Use Putty Connect the raspberry pie
1> Download a Putty
Download PuTTY - a free SSH and telnet client for Windows
2> Check out the raspberry pie ip Address , Enter... At the raspberry pie terminal sudo ifconfig, Inside 192.168.243.125 That's what we want ip Address
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.243.125 netmask 255.255.255.0 broadcast 192.168.243.255
inet6 2409:8914:244:b7f:1f05:f093:abf3:30ce prefixlen 64 scopeid 0x0<g
3> Enter the address , Then connect
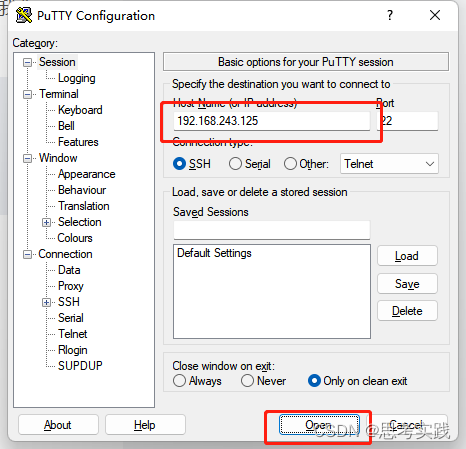
Fill in your raspberry pie user name here , It's usually pi
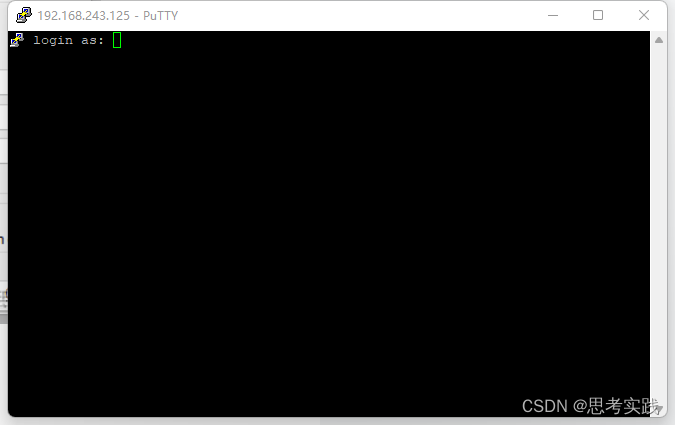
Fill in your raspberry pie password here , It's usually raspberry
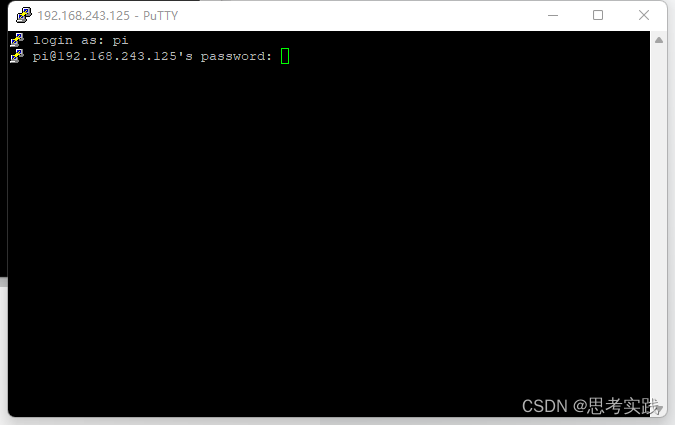
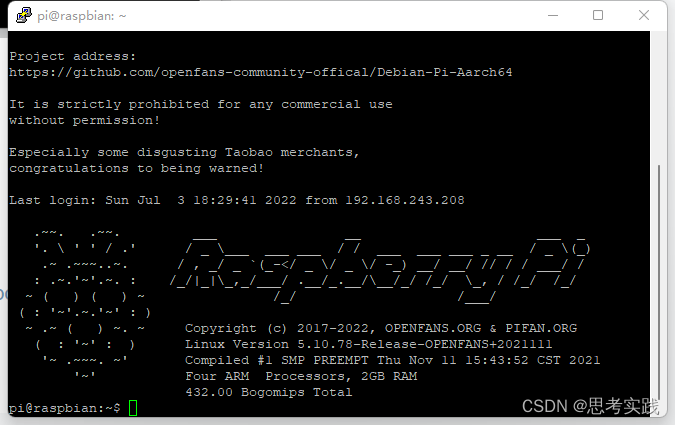
Reference material
Summary of three ways of remote connection of raspberry pie - Let's have a look (zoukankan.com)
边栏推荐
- Cervical vertebra, beriberi
- com. alibaba. nacos. api. exception. NacosException
- Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
- Vulhub vulnerability recurrence 77_ zabbix
- Analysis of tars source code 1
- Introduction to spark core components
- Chapter 1 programming problems
- Tar source code analysis Part 2
- 云Redis 有什么用? 云redis怎么用?
- Wechat applet scroll view component scrollable view area
猜你喜欢
Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
How notepad++ counts words
Flink memory model, network buffer, memory tuning, troubleshooting
com. alibaba. nacos. api. exception. NacosException
Vulhub vulnerability recurrence 77_ zabbix
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
selenium IDE插件下载安装使用教程
响应式——媒体查询
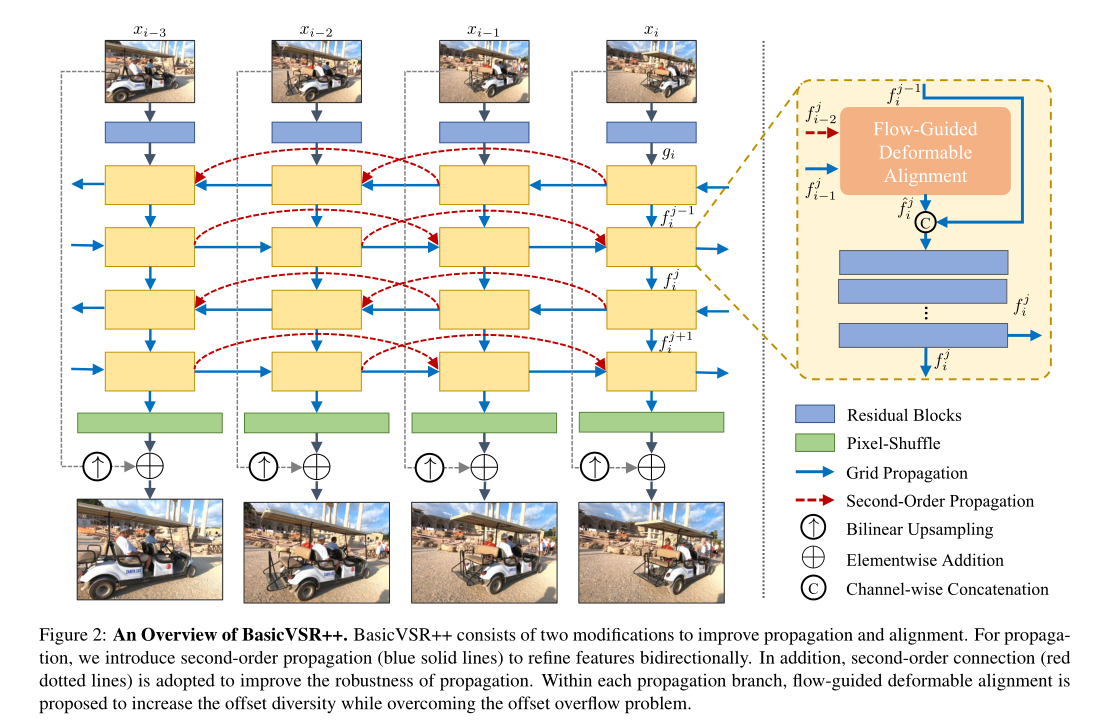
BasicVSR++: Improving Video Super-Resolutionwith Enhanced Propagation and Alignment

电脑通过Putty远程连接树莓派
随机推荐
Mysql 45讲学习笔记(十一)字符串字段怎么加索引
Analysis of tars source code 1
The most effective futures trend strategy: futures reverse merchandising
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
Summary of June 2022
tars源码分析之3
Splicing plain text into JSON strings - easy language method
Mysql 45讲学习笔记(六)全局锁
Mysql 45讲学习笔记(十二)MySQL会“抖”一下
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
Highly paid programmers & interview questions: how does redis of series 119 realize distributed locks?
ABCD four sequential execution methods, extended application
Data double write consistency between redis and MySQL
Campus network problems
Mysql 45讲学习笔记(十)force index
[thread pool]
selenium驱动IE常见问题解决Message: Currently focused window has been closed.
Redis - detailed explanation of cache avalanche, cache penetration and cache breakdown
【FPGA教程案例7】基于verilog的计数器设计与实现
Knowledge payment applet dream vending machine V2