当前位置:网站首页>Deep profile data leakage prevention scheme
Deep profile data leakage prevention scheme
2022-07-04 06:50:00 【CNSINDA_ HK】
One 、 Preface
• Various embedded R & D and platform software R & D industries , Each has its own core data and core documents , User data and other sensitive information , These information data have the following commonalities :
– It belongs to the core confidential information , In case of leakage, it will have a bad impact on
– There are many types of core data , Source code data , Employees have high computer skills
– A lot of data is in the business system , It's not a document
• If you don't control , Designers and users can easily copy the data through various ways , Cause leakage .
Two 、 Common ways of disclosure
• Because R & D personnel are more proficient in computers than ordinary office personnel , In addition to the common network , mail ,U disc ,QQ And other data diffusion methods , There are many other methods that are very easy for developers ( Not listed completely ):
• Physical method :
– Network cable direct connection , Unplug the network cable from the wall , Then connect directly to an uncontrolled computer ;
–winPE start-up , Via CD or U Discoid winPE start-up , Even directly ISO The image starts .
– virtual machine , Through installation VMWare virtual machine , Use peripherals in the virtual machine U disc , The Internet .
– Other uncontrolled computers , That is, copy the data to other uncontrolled computers in the network , transit
– Upload online , By building an upload server on the public network , Bypass Internet Behavior Management
• Data distortion :
– Write a console program , Print the code to DOS On the console, and then save the screen information as ;
– Write the code to Log Log file , Or write code to shared memory , Then another program reads away .
– Write interprocess communication program , Pass the code through socket, news ,LPC,COM,mutex, Shear plate , Pipeline and other interprocess communication methods , Transfer to send the data ;
– adopt IIS/Tomcat etc. web The parser transfers , Publish the code data as a web page , Then browse the browser and save as , Or just write txt box , Copy all the code during initialization ;
• Peripheral transfer
– For embedded development scenarios , You can use the serial port ,U mouth , The network port burns the code to the equipment and leaks the secret
3、 ... and 、SDC Sandbox data anti disclosure system
• Shenxinda SDC Sandbox data anti disclosure system , It is a system specially for anti disclosure protection of sensitive data , Realize code level protection of data , Will not affect work efficiency , Does not affect normal use . All sensitive information and files are automatically encrypted , So as to obtain effective range control , Prevent leaks .
Sandbox data anti disclosure system , The system architecture is as follows :
• The management end : System control center , Strategic management
• Confidential end : Source code and design document version management server , There can be multiple sets
• Outgoing audit server ( Optional ): Sending out classified documents , Email review
• client : Leak proof terminal , There can be multiple sets . All terminal source code , All documents are encrypted transparently
3、 ... and 、SDC Introduction to the main functions of sandbox data anti disclosure system
• All confidential data of the client is automatically encrypted
– The client from SVN Wait for the server to download the code , Documents, etc. can only be carried out in the sandbox , All file formats in the sandbox , All files read and written by software are automatically encrypted , Do not distinguish between file formats , It does not affect the normal development and debugging .
– The confidential data of the terminal cannot pass U disc , mail , Network communication , Chat tool , Disc burning , Hard disk extraction and other disclosure methods .
– Data can be source code 、 file 、 Drawing 、 Database etc. ..
• Safely isolate the Internet
– This function module is provided for customers who need to go to the Internet to find information in secret related status .
– In a classified state , Through this module , You can find information on the Internet normally ,QQ,GoogleTalk Etc. available ,Web Mail available . But because it is isolated from the secret related state , Can't get in , therefore
• You can't copy and paste the contents of confidential documents
• You can't put classified documents QQ Or email or website upload .
• Unable to get QQ Screenshots, etc. send the secret related screen .
•anywork Zero trust
•anywork The zero trust function is SDC Internal and external network access control module of sandbox anti disclosure system . It's through anywork gateway , Control Internet access , In the absence of VPN Under the circumstances , The Internet client can use anywork The gateway accesses the intranet confidential server .

Edit switch to center
Add picture comments , No more than 140 word ( Optional )
• Smart port
• The intelligent port filtering function is SDC Peripheral control module of sandbox anti leak system . The way is through software , Control peripheral access , Filter outgoing data files , And the server records and traces the passed data .

edit
Add picture comments , No more than 140 word ( Optional )
key word : Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption , Source code encryption , Source code anti disclosure , Source code leakage prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , The source code is confidential , Data leakage prevention , Source code security management , Enterprise data security management , Terminal data leakage prevention , Server data leakage prevention , Anti leakage of operation and maintenance data , Document encryption , Encryption of drawings , Environment encryption . Source code encryption , Operation and maintenance data security , Server data leakage prevention , How to choose encryption software , Enterprise source code encryption , Enterprise code protection , Enterprise source code leak proof , Database leak prevention , Source code encryption software , Data leakage prevention solution , Enterprise data security management , Serial port control , Burn control , Source code protection , Server security , Source code encryption system , Research and development data security
Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption , Source code encryption , Source code anti disclosure , Source code leakage prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , The source code is confidential , Data leakage prevention , Source code security management , Enterprise data security management , Terminal data leakage prevention , Server data leakage prevention , Anti leakage of operation and maintenance data , Document encryption , Encryption of drawings , Environment encryption . Source code encryption , Operation and maintenance data security , Server data leakage prevention , How to choose encryption software , Enterprise source code encryption , Enterprise code protection , Enterprise source code leak proof , Database leak prevention , Source code encryption software , Data leakage prevention solution , Enterprise data security management , Serial port control , Burn control , Source code protection , Server security , Source code encryption system , Research and development data security
Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption 、 Source code encryption , Source code encryption , Source code anti disclosure , Source code leakage prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leak prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , Source code leakage prevention , The source code is confidential , Data leakage prevention , Source code security management , Enterprise data security management , Terminal data leakage prevention , Server data leakage prevention , Anti leakage of operation and maintenance data , Document encryption , Encryption of drawings , Environment encryption . Source code encryption , Operation and maintenance data security , Server data leakage prevention , How to choose encryption software , Enterprise source code encryption , Enterprise code protection , Enterprise source code leak proof , Database leak prevention , Source code encryption software , Data leakage prevention solution , Enterprise data security management , Serial port control , Burn control , Source code protection , Server security , Source code encryption system , Research and development data security
边栏推荐
- 2022年,或許是未來10年經濟最好的一年,2022年你畢業了嗎?畢業後是怎麼計劃的?
- centos8安装mysql.7 无法开机启动
- C语言中的排序,实现从小到大的数字排序法
- Analysis of tars source code 5
- [network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
- 2022 is probably the best year for the economy in the next 10 years. Did you graduate in 2022? What is the plan after graduation?
- How to use multithreading to export excel under massive data? Source code attached!
- tcp socket 的 recv 如何接收指定长度消息?
- Can the out of sequence message complete TCP three handshakes
- Selection (022) - what is the output of the following code?
猜你喜欢

2022 where to find enterprise e-mail and which is the security of enterprise e-mail system?
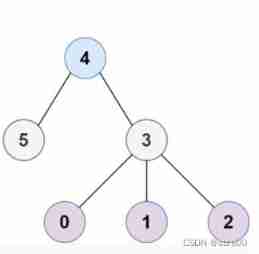
leetcode 310. Minimum Height Trees

【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
![[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)](/img/03/2b37e63d0d482d5020b7421ac974cb.jpg)
[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)

C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
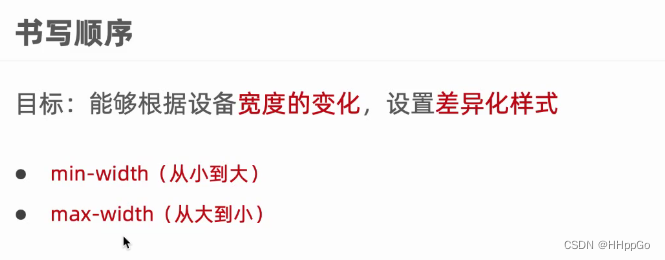
响应式——媒体查询
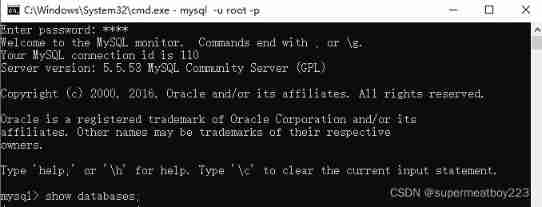
Fundamentals of SQL database operation
校园网络问题
List of top ten professional skills required for data science work
Can the out of sequence message complete TCP three handshakes
随机推荐
Selection (023) - what are the three stages of event propagation?
2022年,或许是未来10年经济最好的一年,2022年你毕业了吗?毕业后是怎么计划的?
Cervical vertebra, beriberi
Shopping malls, storerooms, flat display, user-defined maps can also be played like this!
采用中微BATG135实现IIC数据/指令交互
Mysql 45讲学习笔记(七)行锁
Arcpy uses the updatelayer function to change the symbol system of the layer
what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
移动适配:vw/vh
[number theory] fast power (Euler power)
【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
Check and display one column in the known table column
The sorting in C language realizes the number sorting method from small to large
What is tweeman's law?
Tar source code analysis Part 7
MySQL 45 lecture learning notes (VI) global lock
Redis interview question set
Download kicad on Alibaba cloud image station
高薪程序员&面试题精讲系列119之Redis如何实现分布式锁?
Analysis of tars source code 5