当前位置:网站首页>What is industrial computer encryption and how to do it
What is industrial computer encryption and how to do it
2022-07-04 06:50:00 【CNSINDA_ HK】
One 、 Overview of industrial control safety
Want to know about industrial control safety , First, understand the asset object itself , That is, industrial control system .
1、 What is industrial control
About the definition of industrial control system , There are many on the Internet , I won't go back to , The following picture is from csdn Found , I think it's pretty good . Refer to the definition of industrial control , Can help you have a better understanding .
2、 The impact of industrial control safety
There are many cases about industrial control safety , Recent examples are 2019 year 3 month , Most parts of Venezuela are without power , The national transportation system is paralyzed , The subway system is shut down , Mass disruption of communication .2019 year 7 month , The Iranian information Corps broke into the United States 30 Control centers for multiple substations , It led to a massive blackout in New York 4 Hours , Cause large-scale chaos, etc . One of the most famous 、 The most influential is 2010 year 6 month , The Iranian nuclear power plant suffered “ Seismic net ” Virus attack . There was once a film in China “ Seismic net ” A movie based on events , named 《 Hackers fight 》, Starring Wang Leehom and Tang Wei , Those who are interested can go and have a look , You can have a more intuitive understanding of industrial control safety .
Two 、 Overview of the development of industrial control safety industry in China
In recent years , China's industrial control safety industrial policy environment continues to improve , With the help of industry and local acceleration , The industrial scale has grown rapidly , The technical system is also improving day by day , However, it is still difficult to realize the independent control of industrial control system .
1、 Industrial control information security policy 、 statute 、 The system is constantly improving
2014~2019 In, safety policies and standards have been issued 、 Gradually improve 、 Increasingly rich 5 year . The national policy on industrial control safety is gradually increased , Accelerated standard landing , It provides a good industrial environment for the development of industrial control safety in China .
2、 China's industrial information security industry has increased investment
In recent years , At the national level, policies related to industrial information security have been intensively introduced , It has attracted high attention from local governments and relevant industries , Safety investment continues to increase .
、 The scale of China's industrial control industry continues to grow at a high speed
2010 In, the domestic industrial control safety market was about 2.3 One hundred million yuan ,2018 In, the industry of industrial control safety broke out , The domestic industrial control safety market has reached 18.9 element . The future growth rate of China's industrial control safety market is optimistic , Due in 2020 year , The industrial control safety market will exceed 40 One hundred million yuan , The development prospect of the industry continues to be promising .
4、 The industrial control safety technology system is becoming more and more perfect
Information security manufacturers began to establish a sound system of security products and solutions . Domestic scientific research institutes 、 Industrial control system manufacturer 、 Information security manufacturers and some emerging enterprises focusing on industrial control security have invested a certain amount of research and development strength in the field of industrial control security research and product development , The safety product line is increasingly enriched , Form a differentiated competitive situation .
5、 The core technology of China's industrial control system is non autonomous and controllable
Throughout the construction process of industrial control system in China's industrial enterprises , The old 、 Foreign manufacturers and brands are involved in the new system , And the integration and construction of key components and systems are still implemented by foreign manufacturers , Non autonomous controllability of core system , Its security situation is very serious .
3、 ... and 、 China's industrial control safety industry Development challenges
at present , China has entered the rapid development period of industrial transformation , Intelligent manufacturing promotes the continuous integration of informatization and industrialization , The problem of information security of industrial control system is more prominent . Especially in the weak foundation of industrial enterprises 、 Weak safety awareness and lack of professionals in the field of industrial control safety .
1、 The foundation of industrial control system in China is weak
The safety level and intelligence level of China's industrial enterprises are uneven . A large number of old industrial control systems have been put into operation for many years , The state of safety protection is very fragile , Safety transformation is very difficult .
2、 The safety awareness of China's industrial enterprises is still in its infancy
Most of the information security construction of industrial enterprises in China is still based on the basic security needs of enterprises , It is still in the primary stage of equipment procurement , Lack of willingness to continue learning in the configuration and operation and maintenance of industrial information security products .
3、 There is a shortage of industrial control safety practitioners in China
There is an obvious gap in the number of information security practitioners in China , Security management and operation and maintenance talents who can enter the enterprise are very scarce , Knowledge of industrial control system information security talents 、 Skill levels vary .
Solution
Mainframe reinforcement
Recently, the concept of host reinforcement has been heated , The function of host reinforcement is also being concerned by those who are committed to server security .
So what is host reinforcement ?
Host reinforcement is actually a security mark for the system 、 Access control and other multi-layer and three-dimensional protective measures , Make up for operating system defects .
It can be understood as putting a lock on the main machine , Redefine the functions of each module of the operating system , Build an independent identity authentication system , When anti-virus software 、 When the firewall doesn't work , The host can still be protected , Prevent viruses and Trojans from invading , Prevent core data from being peeped 、 Be destroyed 、 Be tampered with 、 Stolen ! By guarding against external attacks , Prevent internal active disclosure , Solve abnormal behaviors such as unauthorized access , Make up for the security shortcomings of traditional information security solutions in the host layer , Improve the overall security protection ability of the operating system .
To make a long story short , Host reinforcement and anti-virus software are two completely different concepts , They are complementary , Not a substitute relationship .
The core points of host reinforcement :
1、 System reinforcement
Lock the debugged system , Become a trusted system .
In a trusted system , Illegal procedure 、 Scripts can't run . And it will not affect data access .
Even if the system has vulnerabilities , Even administrator privileges are lost , This trusted system is secure .
2、 Program reinforcement
The executable program is signed by trusted signature 、 Start the script in real time hash Value verification , If the verification fails, the startup is rejected , And trusted programs cannot be disguised .
3、 Document reinforcement
Protect files of the specified type from tampering .
4、 Disk encryption
Create a safe sandbox , The sandbox is isolated from the outside , Encrypt the data in the sandbox , Ensure that the data can only be used under the premise of effective authorization management , To be decrypted . If there is no authorization , Even administrators cannot copy and use this data , Even system cloning does not work .
5、 Database hardening ( Structured data )
first floor : Database files are forbidden to be accessed and tampered with by unfamiliar programs . Ensure database file level security .
The second floor : Database port access trusted filtering , Only business programs are allowed to connect to the database port , At the end of the connection string IP+ port + In the account password , Append process identification .
The third level : Database connection SQL Intelligent filtering of text , Prevent critical data from being retrieved and accessed , Prevent the data in the database from being accessed illegally , Prevent dangerous operations of database forms .
Host reinforcement application scenario :
1、 Protect enterprise server security . Server anti blackmail virus 、 Trojan horse 、 mill 、 Data tampering, etc .
2、 Host data anti disclosure protection . Without affecting the normal operation and maintenance of the host , Encrypt and protect sensitive data , Prevent core data from being stolen or tampered with .
3、 Business system host ( Including professional operating system embedded in the equipment ) Best state locking , Reduce viruses through process whitelist control 、 Number of illegal programs running , Greatly reduce the operation and maintenance of the host .
4、 Disk encryption , Even if the server is stolen , The hard disk was removed , The protected data is still encrypted .
Which host reinforcement brands are worth recommending :
At present, several brands that have done well in the field of host reinforcement are known in the market :
1、 Xinda's MCK Mainframe reinforcement .
2、 Wisteria cloud security .
3、 Luoan Technology .
4、 wave .
5、 Anheng .
6、 Convinced .
7、 Tian Rong Xin .

Edit switch to center
Add picture comments , No more than 140 word ( Optional )
In no particular order . Personal recommendations MCK Strengthen the host , Because what our company buys is MCK Mainframe reinforcement . It is said that their sandbox encryption is also an old brand in the industry , You can rely on .
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption

Edit switch to center
Add picture comments , No more than 140 word ( Optional )
边栏推荐
- Summary of June 2022
- Selection (022) - what is the output of the following code?
- [FPGA tutorial case 8] design and implementation of frequency divider based on Verilog
- Tree DP
- [GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
- The final week, I split
- notepad++如何统计单词数量
- 【FPGA教程案例8】基于verilog的分频器设计与实现
- Analysis of tars source code 5
- 请问旧版的的常用SQL怎么迁移到新版本里来?
猜你喜欢
centos8安装mysql.7 无法开机启动

2022 where to find enterprise e-mail and which is the security of enterprise e-mail system?
uniapp 自定義環境變量

颈椎、脚气
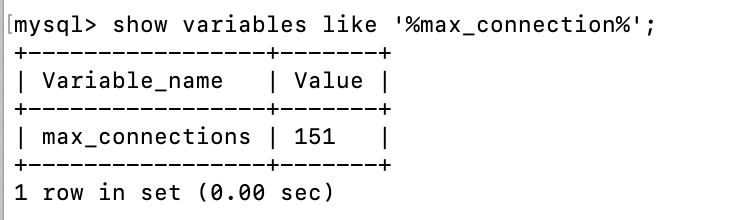
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
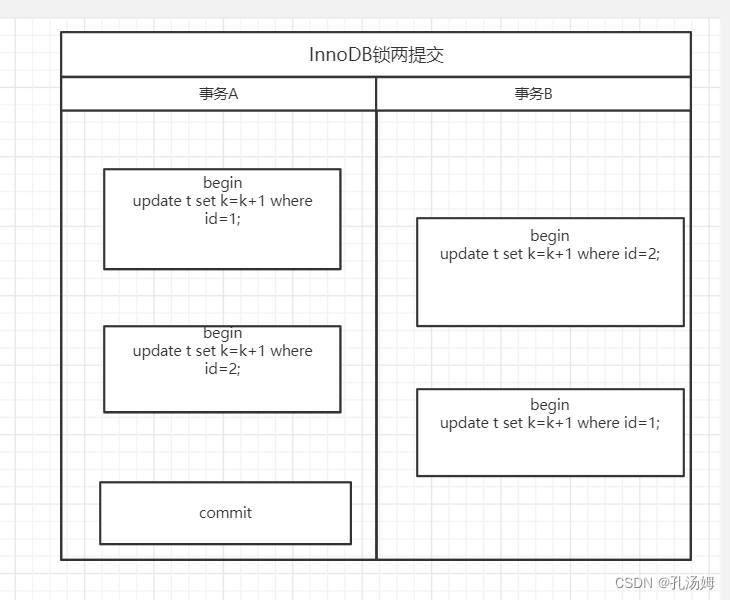
Mysql 45讲学习笔记(七)行锁
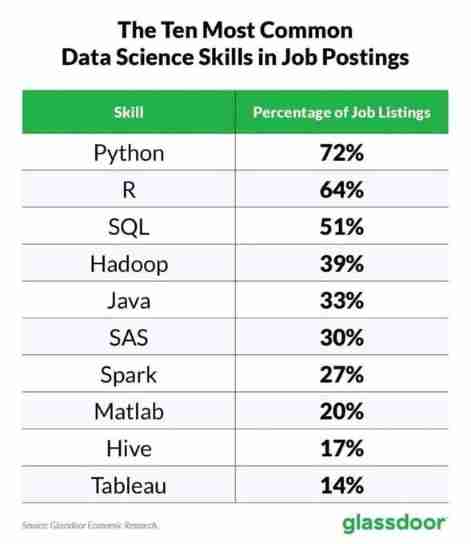
List of top ten professional skills required for data science work

C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing

【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)

Download kicad on Alibaba cloud image station
随机推荐
Tar source code analysis Part 7
tars源码分析之2
【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
Arcpy uses the updatelayer function to change the symbol system of the layer
[problem record] 03 connect to MySQL database prompt: 1040 too many connections
17-18. Dependency scope and life cycle plug-ins
Lottery system test report
【FPGA教程案例8】基于verilog的分频器设计与实现
响应式——媒体查询
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Analysis of tars source code 5
Google Chrome Portable Google Chrome browser portable version official website download method
[FPGA tutorial case 8] design and implementation of frequency divider based on Verilog
ABCD four sequential execution methods, extended application
27-31. Dependency transitivity, principle
Common usage of time library
Tar source code analysis Part 2
R statistical mapping - random forest classification analysis and species abundance difference test combination diagram
Fundamentals of SQL database operation