当前位置:网站首页>Snipaste convenient screenshot software, which can be copied on the screen
Snipaste convenient screenshot software, which can be copied on the screen
2022-07-04 08:11:00 【The mountain of ignorance, the valley of despair, the slope of 】
边栏推荐
- Take you to master the formatter of visual studio code
- Oracle stored procedures and functions
- Laravel page load problem connection reset - PHP
- yolov5 xml数据集转换为VOC数据集
- @Role of requestparam annotation
- [Gurobi] 简单模型的建立
- 21 examples of strategic goals to promote the rapid development of your company
- Difference between static method and non static method (advantages / disadvantages)
- deno debugger
- What determines vacuum permittivity and vacuum permeability? Why do these two physical quantities exist?
猜你喜欢

Book list | as the technical support Party of the Winter Olympics, Alibaba cloud's technology is written in these books!
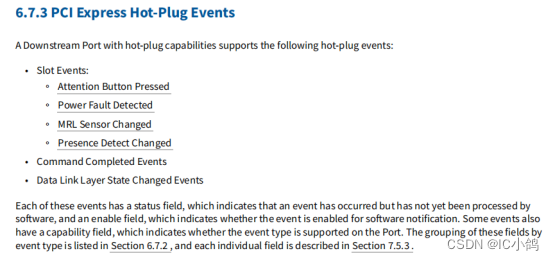
PCIe knowledge points -010: where to get PCIe hot plug data
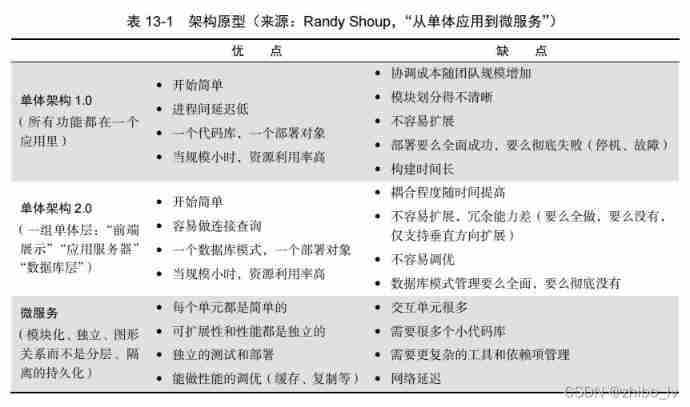
Devops Practice Guide - reading notes (long text alarm)
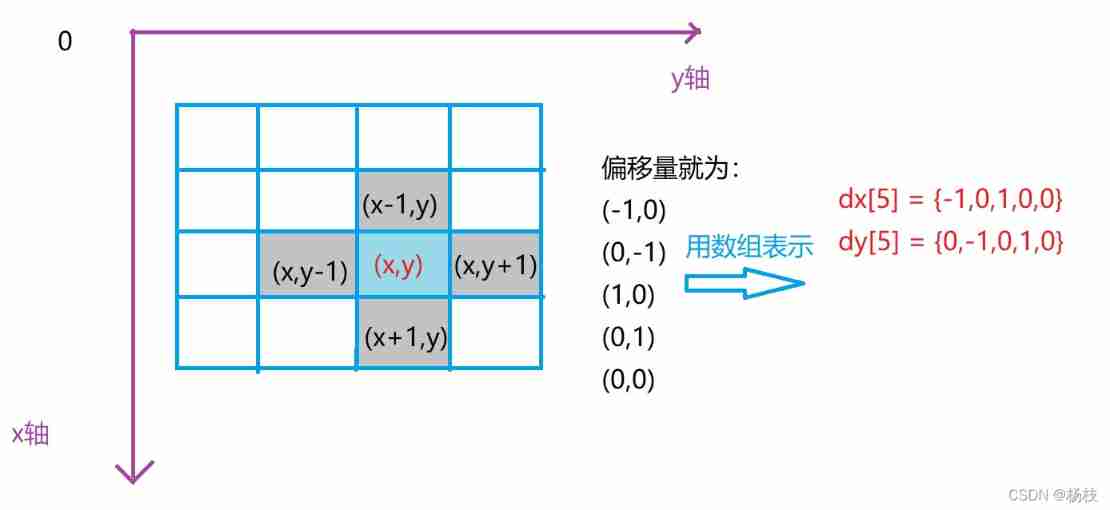
The second session of the question swiping and punching activity -- solving the switching problem with recursion as the background (I)

谷歌官方回应:我们没有放弃TensorFlow,未来与JAX并肩发展
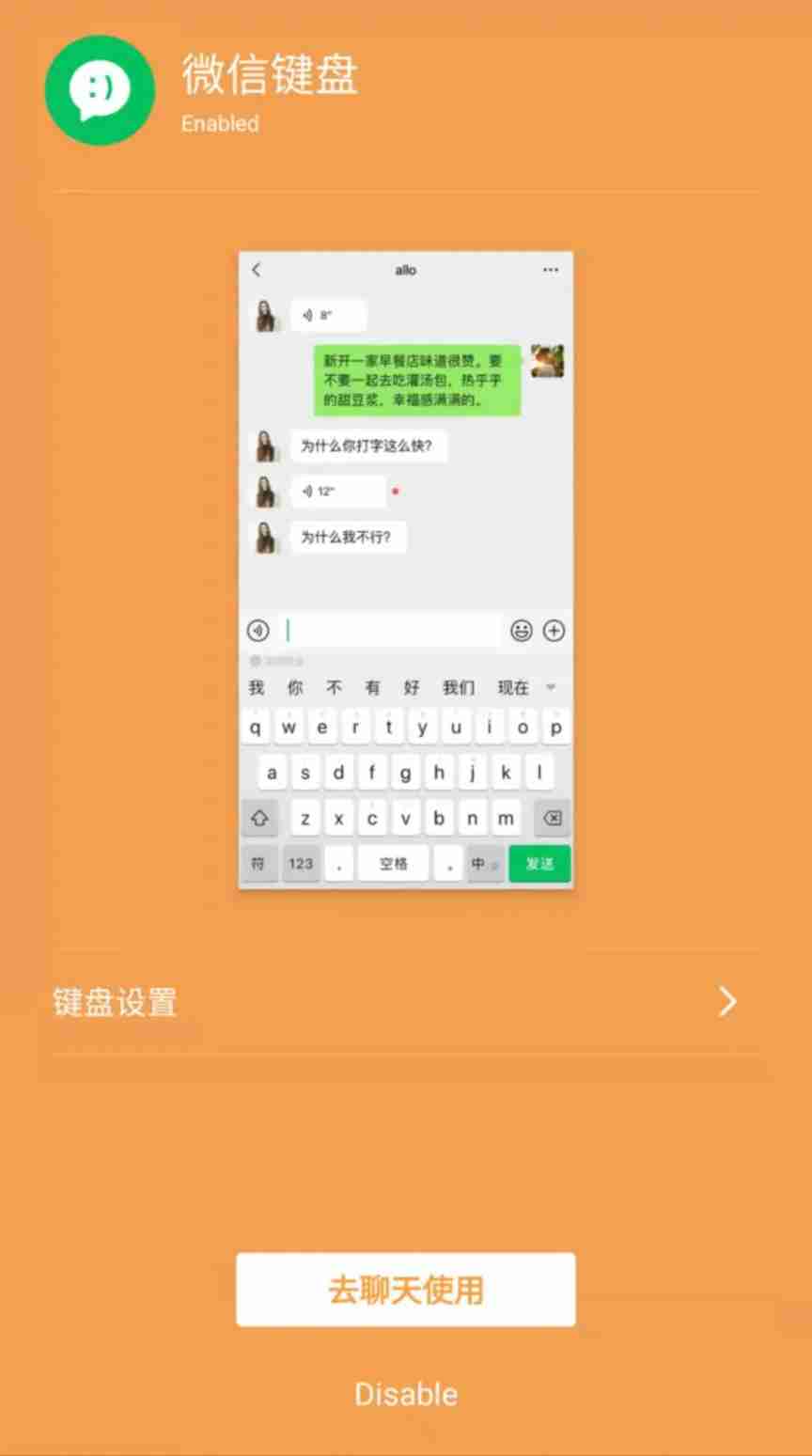
Wechat has new functions, and the test is started again
![[Gurobi] 简单模型的建立](/img/3f/d637406bca3888b939bead40b24337.png)
[Gurobi] 简单模型的建立
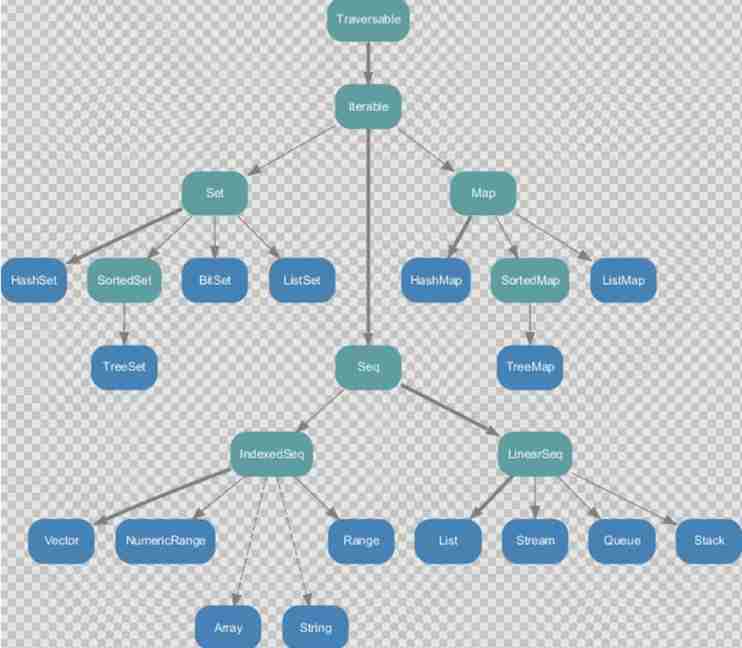
Collections in Scala
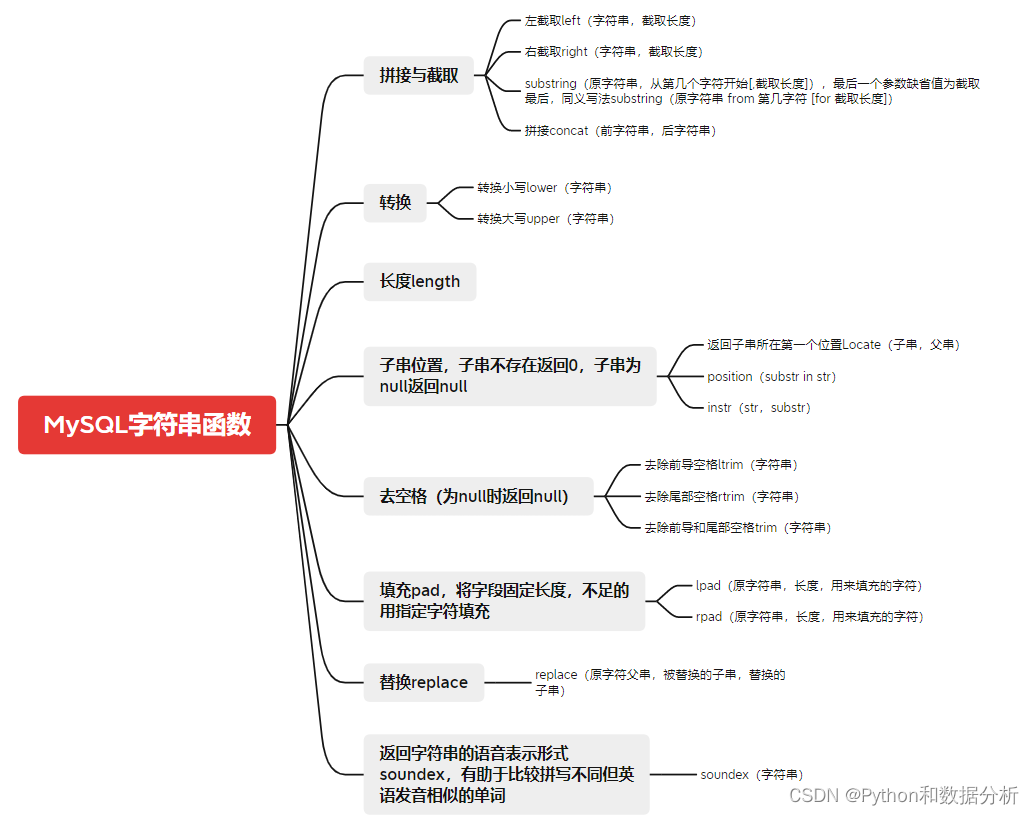
Tri des fonctions de traitement de texte dans MySQL, recherche rapide préférée
![[go basics] 1 - go go](/img/e2/d973b9fc9749e1c4755ce7d0ec11a1.png)
[go basics] 1 - go go
随机推荐
Unity write word
Parallel shift does not provide any acceleration - C #
Leetcode 23. 合并K个升序链表
SSRF vulnerability exploitation - attack redis
1. Kalman filter - the best linear filter
Moher College webmin unauthenticated remote code execution
弈柯莱生物冲刺科创板:年营收3.3亿 弘晖基金与淡马锡是股东
@Role of requestparam annotation
Leetcode 146. LRU cache
Put a lantern on the website during the Lantern Festival
Devops Practice Guide - reading notes (long text alarm)
Oracle stored procedures and functions
Activiti常見操作數據錶關系
【性能測試】一文讀懂Jmeter
Oceanbase is the leader in the magic quadrant of China's database in 2021
Heap concept in JVM
Li Kou today's question -1200 Minimum absolute difference
真空介电常数和真空磁导率究竟是由什么决定的?为何会存在这两个物理量?
zabbix监控系统邮件报警配置
Linear algebra 1.1