当前位置:网站首页>Three layer switching ①
Three layer switching ①
2022-07-04 01:24:00 【BA Bo'er Ben, BA Bo'er Ben】

Park concept :
Campus network : factory , The government authority , Office buildings , The network built by these public places such as parks to realize data exchange can be called Park Network , Different campus networks have different priorities .
Wireless network :
The connection of wireless network depends on wireless devices that can transmit and receive wireless signals , These devices also need to be connected to the network through wired access . And one of AP It is a wireless access point ,WLAN For WLAN ( Broadly speaking, it refers to radio waves , laser , Infrared, etc. to replace part or all of the transmission media of the wired LAN )
Wireless network defects :
① Poor penetration of wireless signals
Wireless uses Ethernet Technology ( Frequency division ), The civil wireless network uses low-frequency network segment for data transmission , Low frequency data network segment has congenital defects, poor penetration and other problems .
② Wireless network transmission rate is related to signal strength , And the transmission rate refers to the bidirectional rate
Limited network signal transmission rate =( bandwidth /8)*86.66%, The transmission rate of wireless network is bidirectional transmission rate ( Including upload and download rates ), Information transmission rate =[( bandwidth /8)/2]*86.66%
③ Wireless network transmission efficiency is low , Less efficient
At this time, the physical devices in the limited network are introduced : A hub , The reason why hubs are not popular is that hubs will generate conflict domains , The hub's solution to the conflict domain :CSMA/CD( Carrier sense multiple access / Conflict detection technology ), To put it simply, check the conflict query and timer wait ( Finding a signal conflict will set a waiting timer for this signal , After waiting for the timer to reset , Reprocess information ), however CSMA/CD The flaw is the delay of the signal ( Unable to quickly handle the exchange of information ).
And WLAN is also equivalent to being in the same conflict domain ( When connecting the interface ), Wireless technology is used to solve conflicts CSMA/CA( Carrier sense multiple access / Conflict avoidance techniques ),CA Compared with CD A lower .
The wireless device cannot check the cause of the conflict : Because the dynamic range of wireless signal strength is very large , Often the received signal strength may be much less than the sent signal strength , It makes it difficult to check conflicts ( It can enhance hardware performance and improve strength )
CA Technology to avoid conflict :
① When no message is sent within the listening range , It doesn't send signals directly , Instead, I will first set myself a random timer
②CSMA/CA The technology adopts stop flow control ( After a message is sent, it must be received from the opposite end ACK After the confirmation , Will continue to send messages )
Three layer switch level concept :
Access layer : The main purpose is to connect all terminal devices to the network , And provide access port ( Generally, layer-2 switches are used , rely on mac Address table realizes two layer forwarding )
Convergence layer : The main purpose is Gather the traffic collected by the access layer , Generally, three-tier switches are used ( The layer-3 switch has a layer-2 interface similar to that used by ordinary layer-2 switches, and also has a layer-3 interface similar to that used by routers or computers . The biggest difference between layer 2 interface and layer 3 interface is whether there is ip Address . The layer-3 switch can pass through MAC Address table realizes two layer forwarding , Three layer forwarding can also be realized through routing table )
Core layer : The main function is to complete the rapid forwarding of data between public and private networks
redundancy ( Backup ):
The core of the three-tier architecture of enterprise network is redundancy ( Backup ), A real three-tier architecture must have redundancy , The redundancy of the three-tier architecture is mainly divided into four types :
① Line redundancy ,② Equipment redundancy ,③ Gateway redundancy ,④UPS redundancy (UPS: Uninterruptible power supply , Ensure that the power supply of enterprise equipment reaches 99.9999% The usability of )
Generally, what we can do is line redundancy , Equipment redundancy and gateway redundancy
VLAN label
introduce :

802.1Q Standard design VLAN The label of is composed of four bytes , It includes 12 Bit VID, Used to distinguish the different VLAN Traffic , And add this tag to the Ethernet two frame source MAC Address fields and TYPE Between fields
IEEE802.1Q The standard stipulates , Frames with labels are called raggedd frame /802.1Q frame , Frames without labels are called untagged frame
According to this feature , The link between the switch and the computer is called ACCESS link , also ACCESS The interface in the switch in the link is ACCESS Interface .ACCESS The link can only pass through untagged frame , And these frames can only belong to the same vlan, Computers can only recognize untagged frame
The link between switches is called TRUNK Interface ,TRUNK The interfaces at both ends of the link are called TRUNK Interface .TRUNK The link is allowed to pass through tagged frame , And these frames can belong to multiple vlan
Huawei's VLAN surface :

Link Type ( Interface type ):
①trunk Interface ,②access Interface ,③hybrid Hybrid interface
Huawei equipment , All interfaces default to hybrid type
PVID( Interface VID):
Each interface of Huawei needs to be configured with one PVID, That is, the interface belongs to VID. All interfaces PVID The default is 1,
PVID The range is from 0~2^20
VLAN List( VLAN allow list ):
VLAN List: Allow the interface to pass through vlan list , If PVID The same information will follow list Forward , and PVID Different information will be discarded .
VLAN List There are two pass types in the :U Means no label untagged adopt ,T For labeled tagged adopt
All data enters the Huawei switch through the Huawei interface , All interfaces must be marked PVID The label of , That is to say All data inside the switch is labeled
ACCESS label :
① When ACCESS The interface received a message from the link untagged After the frame , Swap opportunities add... To this frame VID Interface for PVID by tag, Then judge the frame label VID Whether it is in the Allow list , If you're here, you'll get tagged Forward frames , If it is not in the Allow list, it will be directly discarded
② When tagged Frames arrive from other ports of the switch ACCESS After a mouth , The exchange opportunity checks the... In this frame tagged Of VID Whether it is in the Allow list , If it is in the Allow list, it will split tagged The tag is then forwarded from the link , If it is not in the list, it will be discarded directly
③ If ACCESS The interface received a message from the link tagged After the frame , will Directly view the tag of this data VID Whether in your own list , If so, forward , If not, discard
TRUNK label :
① When TURNK The interface received a message from the link untagged frame , The switch first adds a... To the data frame VID by PVID Of tagged, And then based on VID View the Allow List , If so, forward , If not, discard
② When taggged Frames arrive from other ports of the switch TRUNK After a mouth , be The exchange opportunity checks the... In this frame tag Of VID Whether it is in the Allow list , If it is, it will be stripped tag Then forward from the link , If not in the list, discard
If VID and TRUNK Interface PVID Phase at the same time , The label needs to be stripped when transferring out , If PVID inequality , Then directly transfer out
③ If TRUNK The interface received a message from the link tagged After the frame , The tag of this data will be directly viewed VID Whether you are in your allow list , If so, forward , If not, discard
HYBIRD label :
Huawei's HYBIRD The label can be modified PVID,VID,VLAN list To decide whether to forward , And whether to carry the tag when forwarding
The permissions of three tags :
ACCESS/TRUNK/HYBRID These three types of interfaces are in the custom forwarding table (vlan list) The modification permissions are different .
ACCESS Modify permission of interface :
ACCESS type You can modify PVID, You can also modify the permission list , The export mode can only be non encapsulation
stay VLAN list In the Allow List ,access An interface can only have one VLAN ID, And it has to be with PVID identical
TRUNK Modify permission of interface :
TRUNK type You can modify PVID, You can also modify the permission list , The Allow list can be set to multiple VID, The export mode can be encapsulated / No encapsulation
TRUNK Allow list for There can only be one VID, And this VID It's not fixed ( Not necessarily with PVID identical ), also In the Allow list, this VID For fixing without labels ( In addition to this VID, Other VID All need to be labeled for transmission )
HYBRID Modify permission of interface :
HYBRID type You can modify PVID, You can also modify the permission list , The Allow list can be set to multiple VID, The export method can also be modified
HYBRID It can be modified by PVID,VID And export methods to modify vlan list
To configure :
① establish VLAN:
[Huawei]vlan 2
# establish VLAN 2
[Huawei]vlan batch 4 to 100
# Batch creation VLAN
[Huawei]undo vlan batch 4 to 10
# Batch deletion VLAN② Put the interface into VLAN:
① Single interface partition VLAN
[sw1-GigabitEthernet0/0/1]port default vlan 2
② The interface group is divided into the same VLAN
[sw1]port-group group-member GigabitEthernet 0/0/3 GigabitEthernet 0/0/4
[sw1-port-group]
# Create an interface group
[sw1-port-group] port default vlan 2
# Define the interface group VLAN③ Configure interfaces and trunk roads :
① Single interface defines the type of trunk road
[sw1-GigabitEthernet0/0/1]port link-type access
② Trunk road type of Interface Group
[sw1-port-group] port link-type access ④ Configure the router VLAN Routing between
// A subinterface , A virtual interface ( Logically, a physical interface is divided into multiple virtual sub interfaces )
[r1-GigabitEthernet0/0/2.1]ip address 192.168.1.1 24
[r1-GigabitEthernet0/0/2.1]dot1q termination vid 2
[r1-GigabitEthernet0/0/2.1]arp broadcast enable
// Open the sub connection ARP Broadcast request response 边栏推荐
- A little understanding of GSLB (global server load balance) technology
- AI helps make new breakthroughs in art design plagiarism retrieval! Professor Liu Fang's team paper was employed by ACM mm, a multimedia top-level conference
- Force deduction solution summary 1189- maximum number of "balloons"
- 2-redis architecture design to use scenarios - four deployment and operation modes (Part 2)
- Introduction to superresolution
- Function: write function fun to find s=1^k+2^k +3^k ++ The value of n^k, (the cumulative sum of the K power of 1 to the K power of n).
- Introduction to unity shader essentials reading notes Chapter III unity shader Foundation
- The first training of wechat applet
- Gauss elimination method and template code
- Windos10 reinstallation system tutorial
猜你喜欢
C import Xls data method summary II (save the uploaded file to the DataTable instance object)
HackTheBox-baby breaking grad

Network layer - routing

Unity Shader入门精要读书笔记 第三章 Unity Shader基础
长文综述:大脑中的熵、自由能、对称性和动力学

Meta metauniverse female safety problems occur frequently, how to solve the relevant problems in the metauniverse?
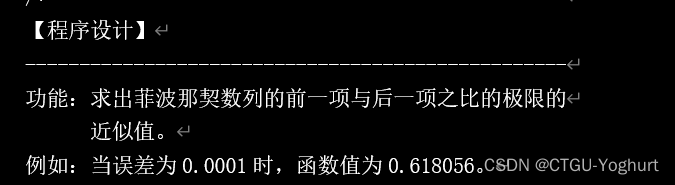
功能:求出菲波那契数列的前一项与后一项之比的极限的 近似值。例如:当误差为0.0001时,函数值为0.618056。

Employees' turnover intention is under the control of the company. After the dispute, the monitoring system developer quietly removed the relevant services

Make drop-down menu
How to delete MySQL components using xshell7?
随机推荐
Oracle database knowledge points that cannot be learned (II)
Oracle database knowledge points (I)
功能:编写函数fun求s=1^k+2^k +3^k + ......+N^k的值, (1的K次方到N的K次方的累加和)。
Ka! Why does the seat belt suddenly fail to pull? After reading these pictures, I can't stop wearing them
Print diamond pattern
PMP 考试常见工具与技术点总结
Gauss elimination method and template code
Function: write function fun to find s=1^k+2^k +3^k ++ The value of n^k, (the cumulative sum of the K power of 1 to the K power of n).
C import Xls data method summary III (processing data in datatable)
C import Xls data method summary II (save the uploaded file to the DataTable instance object)
Trading software programming
The first training of wechat applet
MySQL uses the view to report an error, explain/show can not be issued; lacking privileges for underlying table
Leetcode 121 best time to buy and sell stock (simple)
The super fully automated test learning materials sorted out after a long talk with a Tencent eight year old test all night! (full of dry goods
C import Xls data method summary I (upload files and create Workbooks)
Typescript basic knowledge sorting
技术实践|线上故障分析及解决方法(上)
Day05 表格
It's OK to have hands-on 8 - project construction details 3-jenkins' parametric construction